Posts
2469Following
662Followers
1486Harold Aptroot
harold@mastodon.gamedev.placeCPU bugs reached a level of yikes that speculation side channels can only dream of
screaminggoat
screaminggoat@infosec.exchangeMICROSOFT ZERO-DAYS (both CVE IDs are UNPATCHED)
As promised, Microsoft Security Response Center (MSRC) published not one but TWO security advisories in regards to a Windows Update issue allowing for software-downgrade attacks (see parent toot above):
- CVE-2024-21302 (6.7 medium) Windows Secure Kernel Mode Elevation of Privilege Vulnerability (PUBLICLY DISCLOSED)
- CVE-2024-38202 (7.3 high) Windows Update Stack Elevation of Privilege Vulnerability (PUBLICLY DISCLOSED)
Microsoft was notified that an elevation of privilege vulnerability exists in Windows based systems supporting Virtualization Based Security (VBS) including a subset of Azure Virtual Machine SKUS; enabling an attacker with administrator privileges to replace current versions of Windows system files with outdated versions. By exploiting this vulnerability, an attacker could reintroduce previously mitigated vulnerabilities, circumvent some features of VBS, and exfiltrate data protected by VBS.
A security researcher informed Microsoft of an elevation of privilege vulnerability in Windows Backup potentially enabling an attacker with basic user privileges to reintroduce previously mitigated vulnerabilities or circumvent some features of VBS. For exploitation to succeed, an attacker must trick or convince an Administrator or a user with delegated permissions into performing a system restore which inadvertently triggers the vulnerability.
Microsoft is developing a security update to mitigate this threat, but it is not yet available.
cc: @campuscodi @briankrebs @wdormann @ntkramer
#CVE_2024_21302 #CVE_2024_38202 #Microsoft #vulnerability #CVE
James Kettle
albinowax@infosec.exchangeThe whitepaper is live! Listen to the whispers: web timing attacks that actually work. Read it here ->
https://portswigger.net/research/listen-to-the-whispers-web-timing-attacks-that-actually-work
screaminggoat
screaminggoat@infosec.exchangeIvanti and Fortinet have unpatched vulnerabilities in their VPN products!
Akamai, in their blog post Living off the VPN — Exploring VPN Post-Exploitation Techniques, talk about techniques that can be used by threat actors after compromising a VPN server to further escalate their intrusion. The key takeaway is that the vulnerability disclosure was published 133 days after initial notification to Ivanti and Fortinet:
- CVE-2024-37374 (unknown CVSS score) Ivanti hard-coded key issue?
- CVE-2024-37375 (unknown CVSS score) Ivanti MDM cleartext passwords issue?
- Fortinet custom encryption key bypass issue (no CVE ID assigned)
Fortinet informed us that after additional consideration, they decided to not fix the custom encryption key bypass as it “does not cross a security boundary”
If the original Ivanti Connect Secure exploited zero-day fiasco hasn't scared you off of their products, this is your wakeup call. As @cadey would say: "No way to prevent this" say users of only VPN where this regularly happens
cc: @campuscodi (who else wants to be notified of issues like this?)
#CVE_2024_37374 #CVE_2024_37375 #Fortinet #Ivanti #ConnectSecure #FortiGate
Dominic White
singe@chaos.social“Variant analysis is the lowest effort, highest reward activity for preventing 0days” @natashenka
Piotr Bazydło
chudypb@infosec.exchangeAnother year, another Microsoft Most Valuable Researcher for me. This year, it has a bittersweet taste though.
Let’s kick off with the sweet part.
I’m quite happy with my consistency and findings. My record for 2024:
- 10x Exchange
- 2x SharePoint
- 1x .NET/VS
Multiple RCEs included.
I have also already reported several vulns for 2025, and I’m happy with the technical level of the findings. Not necessarily with the impact, but you don’t always get RCE;). I’m especially happy with the fact that I’m doing some risky deep dives, and sometimes it pays off.
I’m also happy with some recent research. I’ve been abusing unknown attack surfaces and I had some success with that (even though I was not familiar with the target). At least some of them are unknown according to my knowledge, so even if they are known, it does not count, right? :)
Now the bitter part.
Over the entire year, I had an impression that MSRC leaderboard is missing points for the majority of my submissions. I was signalizing this issue a couple of times, but with no effect. I was even not on the initial MVR list.
After my small tweet, some of my missing points were found and I eventually made it to the list (thx MSRC for this intervention). The truth is – the list is not so important to me. I like to think about vuln disclosure as some mutually respected process.
I’m not collecting bounties (reporting as ZDI) and the only thing I want in return for my submissions is a proper acknowledgment. I think that this process failed in 2024, but I hope it will eventually get better. I have impression that I should have way more points, but whatever.
Another part – several of my submissions were rejected as an expected behavior. Not a nice feeling, but it’s a part of the game. I can see a lot of tweets about dropped submissions and this part concerns everybody. From my perspective, reporting of .NET vulns is hardest.
I have a small perception that if you cannot exploit something that you consider a .NET vuln in Exchange or SharePoint, it’s probably going to be ignored (based on my experience only). Well guess what, there are different products/apps based on .NET too :D
To sum up, quite a good year. Hoping to have an even better 2025, although my Exchange run from 2023/2024 will be hard to repeat.
I hope to deliver some nice research and to see you next year during conferences or wherever. Cheers
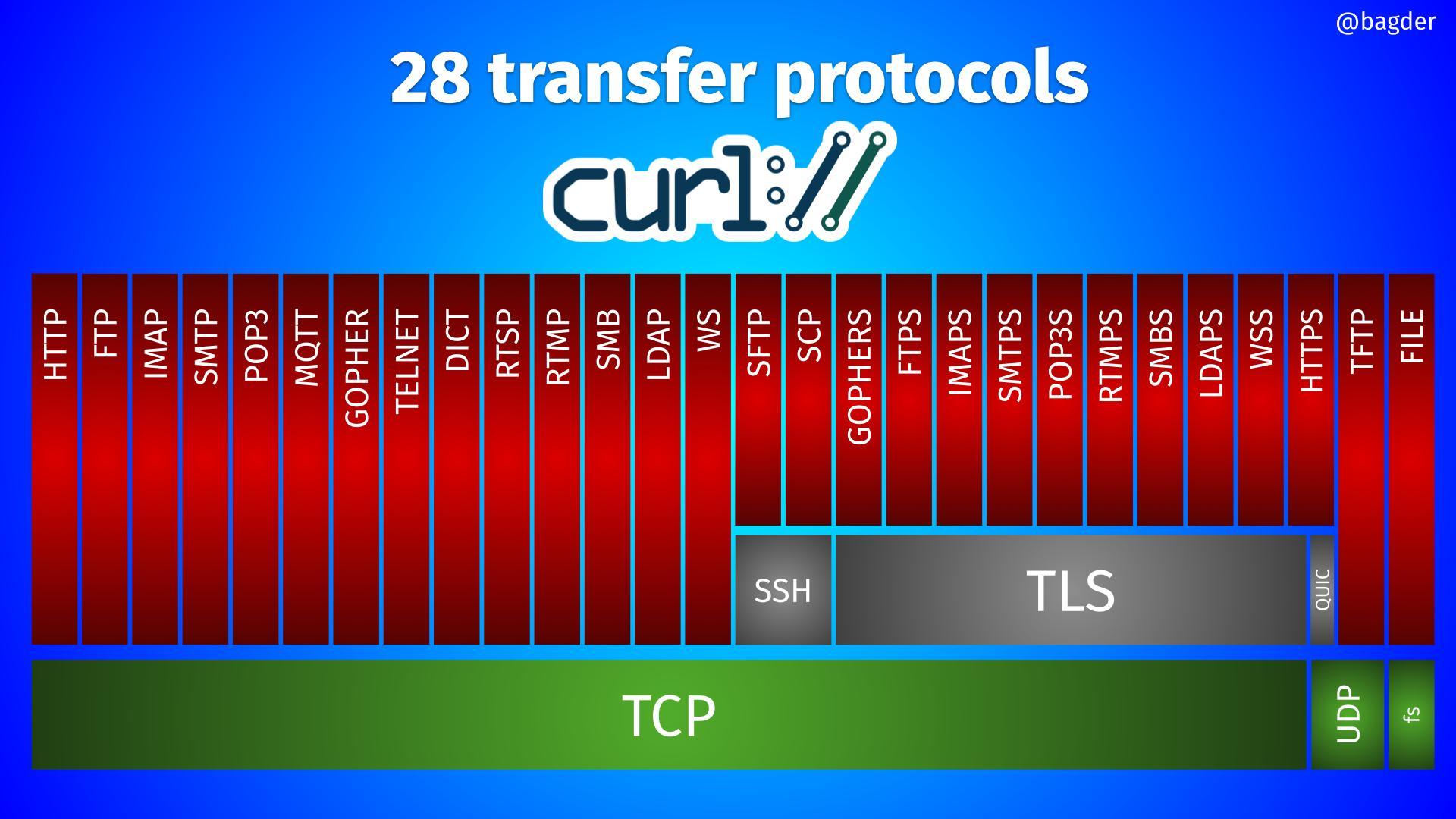
daniel:// stenberg://
bagder@mastodon.socialHere's one way to view the 28 transfer protocols #curl supports.
screaminggoat
screaminggoat@infosec.exchangeGoogle Chrome security advisory: Stable Channel Update for Desktop
Google does not know how to count past five as they state 5 security fixes but list 6 externally reported vulnerabilities:
- CVE-2024-7532 (critical) Out of bounds memory access in ANGLE
- CVE-2024-7533 (high) Use after free in Sharing.
- CVE-2024-7550 (high) Type Confusion in V8.
- CVE-2024-7534 (high) Heap buffer overflow in Layout
- CVE-2024-7535 (high): Inappropriate implementation in V8
- CVE-2024-7536 (high) Use after free in WebAudio.
No mention of exploitation.
#CVE_2024_7532 #Google #Chrome #PatchTuesday #vulnerability #CVE
Ars Technica
arstechnica@mastodon.socialParody site ClownStrike refused to bow to CrowdStrike’s bogus DMCA takedown
Parody site ClownStrike defended the "obvious" fair use.
Jason Koebler
jasonkoebler@mastodon.socialAfter months of digging and reporting, I have learned where Facebook's bizarre AI spam (like "Shrimp Jesus") comes from, who is making it, how it works, and how it is monetized.
Turns out Meta is directly paying people to spam FB with this stuff
screaminggoat
screaminggoat@infosec.exchangeMozilla Foundation security advisories:
- Security Vulnerabilities fixed in Firefox 129 14 vulnerabilities
- Security Vulnerabilities fixed in Firefox ESR 115.14 9 vulnerabilities
- Security Vulnerabilities fixed in Firefox ESR 128.1 12 vulnerabilities
- Security Vulnerabilities fixed in Firefox for iOS 129 4 vulnerabilities
No mention of exploitation
Joxean Koret (@matalaz)
joxean@mastodon.socialI have just added support in #Diaphora for #IDA 9.0 (currently in beta). I wrote the changes this weekend, but I had to test multiple things... anyway, enjoy it.
https://github.com/joxeankoret/diaphora/commit/232a2720d56d17acce809b6bf82a6a561c980d82
Molly White
molly0xfff@hachyderm.ioLast week, Public Citizen’s Rick Claypool and I filed a complaint with the Federal Election Commission based on my research into apparent campaign finance violations by the Coinbase cryptocurrency exchange.
Read the full complaint and my updated article.
Complaint: https://www.citizen.org/article/coinbase-fec-complaint/
Updated article: https://www.citationneeded.news/coinbase-campaign-finance-violation/
#crypto #cryptocurrency #Coinbase #Fairshake #USpol #USpolitics
Marcus Hutchins 
malwaretech@infosec.exchange
Resorts World Las Vegas announced they're performing periodic room checks for the duration of the blackhat / defcon hacking conference. When asked what they are looking for, one of the employees responded with "people hacking our stuff" ☠️
Reminds me of that old blog post by some dude who got pulled aside by the TSA so they could search his bag for "bitcoins".
https://www.404media.co/hotel-to-search-rooms-during-def-con-hacking-conference/
Ken Shirriff
kenshirriff@oldbytes.spaceThe original Pentium chip was introduced in 1993. It was the first "superscalar" x86 chip, able to run two instructions per clock cycle. I took this die photo of the chip yesterday. The chip has three metal layers; the thick lines you see are the top metal layer, mostly power and ground. The silicon itself is almost entirely obscured. Around the edges of the chip, tiny bond wires connect to the bond pads, providing the connections to the chip's external pins. 1/N
screaminggoat
screaminggoat@infosec.exchangeCurrently trending on the bad place (Twitter): Leaked Wallpaper
Proof of concept for CVE-2024-38100 (7.8 high, disclosed 09 July 2024 by Microsoft Windows File Explorer Elevation of Privilege Vulnerability.
This is a privilege escalation tool (fixed with CVE-2024-38100 in KB5040434) that allows us to leak a user's NetNTLM hash from any session on the computer, even if we are working from a low-privileged user.
#CVE_2024_38100 #microsoft #msrc #vulnerability #CVE #proofofconcept #PoC
Joseph Cox
josephcox@infosec.exchangeNew from 404 Media: we got a massive leak from inside Nvidia (emails, Slack chats, documents) which show how it created a yet-to-be-released AI model. The leak shows that Nvidia scraped YouTube en masse, had clearance from highest levels of the company https://www.404media.co/nvidia-ai-scraping-foundational-model-cosmos-project/