Conversation
buherator
buherator
I don't have hight expectations about security products but this one about #CrowdStrike is straight up terrifying
buherator
buherator
Alt:
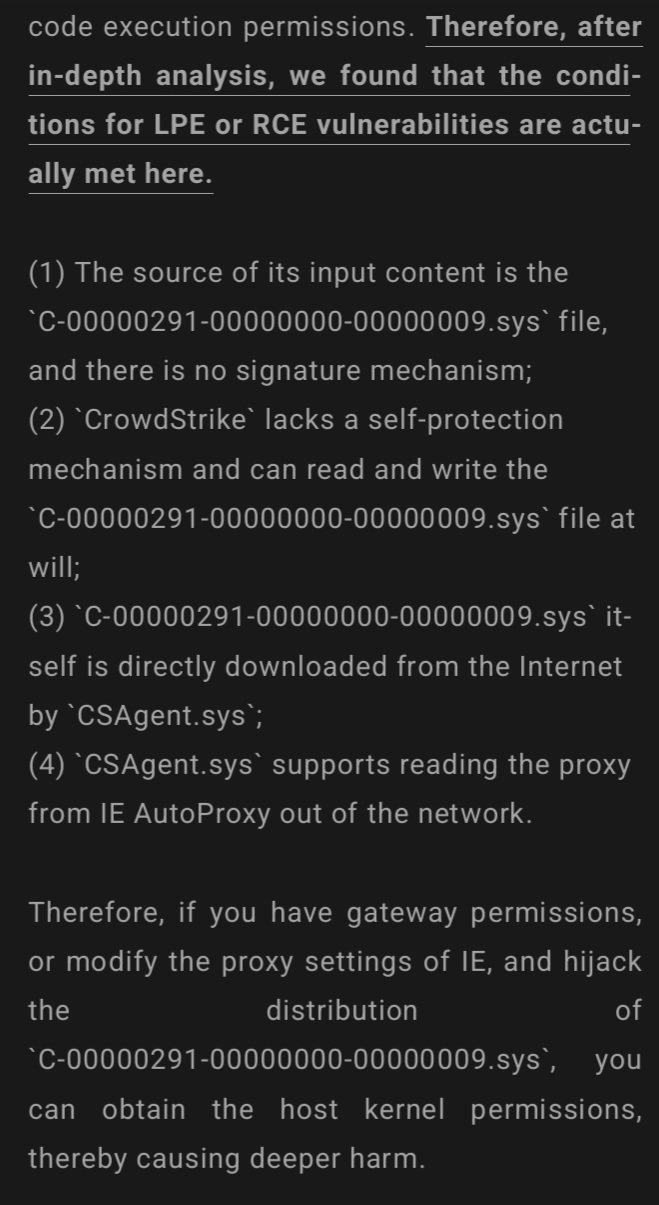
Therefore, after in-depth analysis, we found that the conditions for LPE or RCE vulnerabilities are actually met here.
(1) The source of its input content is the `C-00000291-00000000-00000009.sys` file, and there is no signature mechanism;
(2) `CrowdStrike` lacks a self-protection mechanism and can read and write the `C-00000291-00000000-00000009.sys` file at will;
(3) `C-00000291-00000000-00000009.sys` itself is directly downloaded from the Internet by `CSAgent.sys`;
(4) `CSAgent.sys` supports reading the proxy from IE AutoProxy out of the network.
Therefore, after in-depth analysis, we found that the conditions for LPE or RCE vulnerabilities are actually met here.
(1) The source of its input content is the `C-00000291-00000000-00000009.sys` file, and there is no signature mechanism;
(2) `CrowdStrike` lacks a self-protection mechanism and can read and write the `C-00000291-00000000-00000009.sys` file at will;
(3) `C-00000291-00000000-00000009.sys` itself is directly downloaded from the Internet by `CSAgent.sys`;
(4) `CSAgent.sys` supports reading the proxy from IE AutoProxy out of the network.
Viss
Viss@mastodon.social@buherator using the rce by design edr platform for addition rce sounds like a feature crowdstrike will find a way to charge extra for
buherator
buherator
@risottobias Im not familiar with TUF. Here the key would be to verify the authenticity of (bytecode)updates since you have to expect middleboxes in the network path that you shouldn't trust.
buherator
buherator
@risottobias if I interpret the translation correctly there is no need for revocation as there are no sigs :) *roll smart*
buherator
buherator
@risottobias I'm not saying revocation/key mgmt is useless, just that it's not relevant in this case as it seems there are no keys to manage