Posts
2469Following
662Followers
1486Mr. Bitterness
wdormann@infosec.exchangeThe flow is pretty straightforward:
First, the MotW is written when the from-the-internet ZIP is extracted, as any well-behaved (e.g. NOT 7-zip) archiving utility will do.
Then, as Windows parses the LNK file, it rewrites it to fix the path. In the process of doing this, the MotW is removed.
Finally, Windows checks to see if it needs to use SAC or SmartScreen. Because there is no MotW, the file is deemed "safe" and no SAC or SmartScreen comes into play. 🎉
Zeljka Zorz
zeljkazorz@infosec.exchangeCVE-2024-38856, an incorrect authorization vulnerability affecting all but the latest version of Apache OFBiz, may be exploited by remote, unauthenticated attackers to execute arbitrary code on vulnerable systems.
screaminggoat
screaminggoat@infosec.exchangeCISA: CISA Adds One Known Exploited Vulnerability to Catalog
Hot off the press! CISA adds CVE-2018-0824 (7.5 high, disclosed 08 May 2018 by Microsoft) Microsoft COM for Windows Remote Code Execution Vulnerability to the Known Exploited Vulnerabilities (KEV) Catalog! See parent toot above for evidence of exploitation.
#CVE_2018_0824 #eitw #activeexploitation #vulnerability #CVE #Microsoft #KEV #KnownExploitedVulnerabilitiesCatalog
Trail of Bits
trailofbits@infosec.exchangeWe break down the cryptography services offered within Google Cloud Platform —Cloud KMS, Secret Manager, and Confidential Computing—helping you decide which tools are right for your project. https://buff.ly/3WQB69S
screaminggoat
screaminggoat@infosec.exchangeElastic: Dismantling Smart App Control
Elastic claims that Windows Smart App Control and SmartScreen have several design weaknesses that allow attackers to gain initial access with no security warnings or popups. A bug in the handling of LNK files can also bypass these security controls. They research bypasses for reputation-based systems and develop detections to identify indicators of attack. No CVE IDs associated.
See related The Hacker News reporting: Researchers Uncover Flaws in Windows Smart App Control and SmartScreen
Haroon Meer
haroonmeer@infosec.exchange“Crowdstrike has made intentional architectural engineering and QA decisions that made this happen. They were negligent in their engineering decisions and their QA decisions.”
@alexstamos starts off strong on his latest @riskybiz episode.
Note to sec company CTOs/CISOs:
If u put in the work to engage with the community on topics that don’t directly affect what u are selling, it buys u some leeway when u have to discuss products that do..
Many would be flamed for taking this stance openly. He pulls it off.
Jack Daniel (often offline)
jack_daniel@mastodon.socialFifteen years ago today, a group of hackers and security pros got together and made a little thing happen, the first ever BSides @SecurityBSidesGlobal, @BSidesLV
Things took off from there.
The next BSides on the event calendar is BSides Las Vegas, and it will be event number 1002.
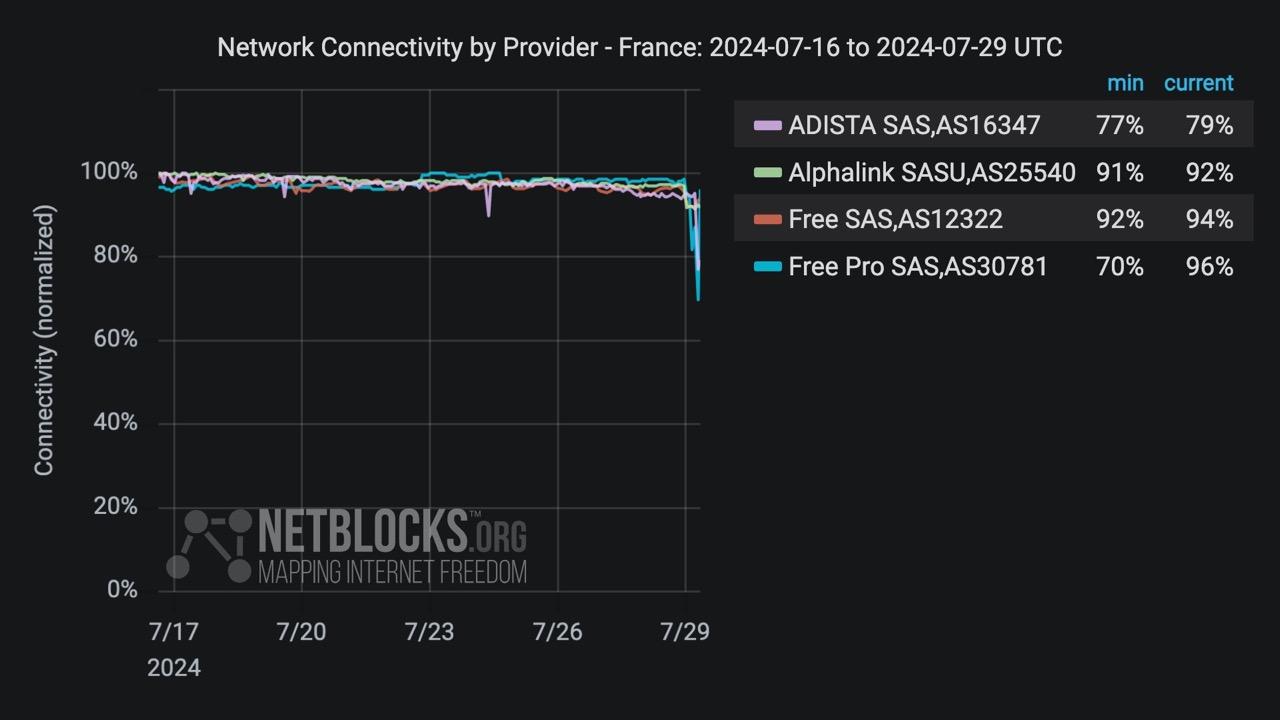
NetBlocks
netblocks@mastodon.social⚠️ Confirmed: Network data show disruptions to multiple internet providers in #France amid reports of a fibre sabotage campaign targeting telecoms infrastructure during the Paris 2024 Olympics 📉
it's missing 🔜 eth0 🎃
domi@donotsta.reprotip: when referring to your favourite programming language’s features, call them spells instead to sound more mysterious and cool.
 “memory safety feature”
“memory safety feature”
 “memory safety spell”
“memory safety spell”
Dare Obasanjo
carnage4life@mas.toA really “inspirational” Google ad about a young girl who’s inspired by an Olympic athlete so her dad asks Google’s Gemini AI to write the athlete a letter from his daughter.
It’s actually an effective anti-AI ad which plays to the fear AI drains the creativity and honesty out of human communication. 🤦🏾♂️
I found out quite a lot of stuff by now about the Ghidra stack depth mess up and still have no idea how to fix it... 😩
https://github.com/NationalSecurityAgency/ghidra/issues/6747
Simon Tesla 🏳️🌈🐭
SimonTesla@chitter.xyzsomeone just shared this picture with me and I am so mad this is a thing that somebody thought was a good idea, or even not a terrible idea
dwizzzle
dwizzzle@infosec.exchangeMy new blog - featuring: a technical overview of the CrowdStrike incident, why security products user kernel mode, and what this means for the future of Windows.
Shout outs to my non-Microsoft friends who gave me input and technical editing, appreciate you!
Ryan Townsend (old account)
ryantownsend@webperf.social👏 more 👏 developers 👏 need 👏 👏 hear 👏 this
I can count on one hand the number of my clients over the past couple of years who haven't either over-architected for scale or were unnecessarily concerned about it.
You don't need to understand Distributional Little's Law to figure this out, it's obvious with primary school level math.
Excerpt from https://tailscale.com/blog/new-internet
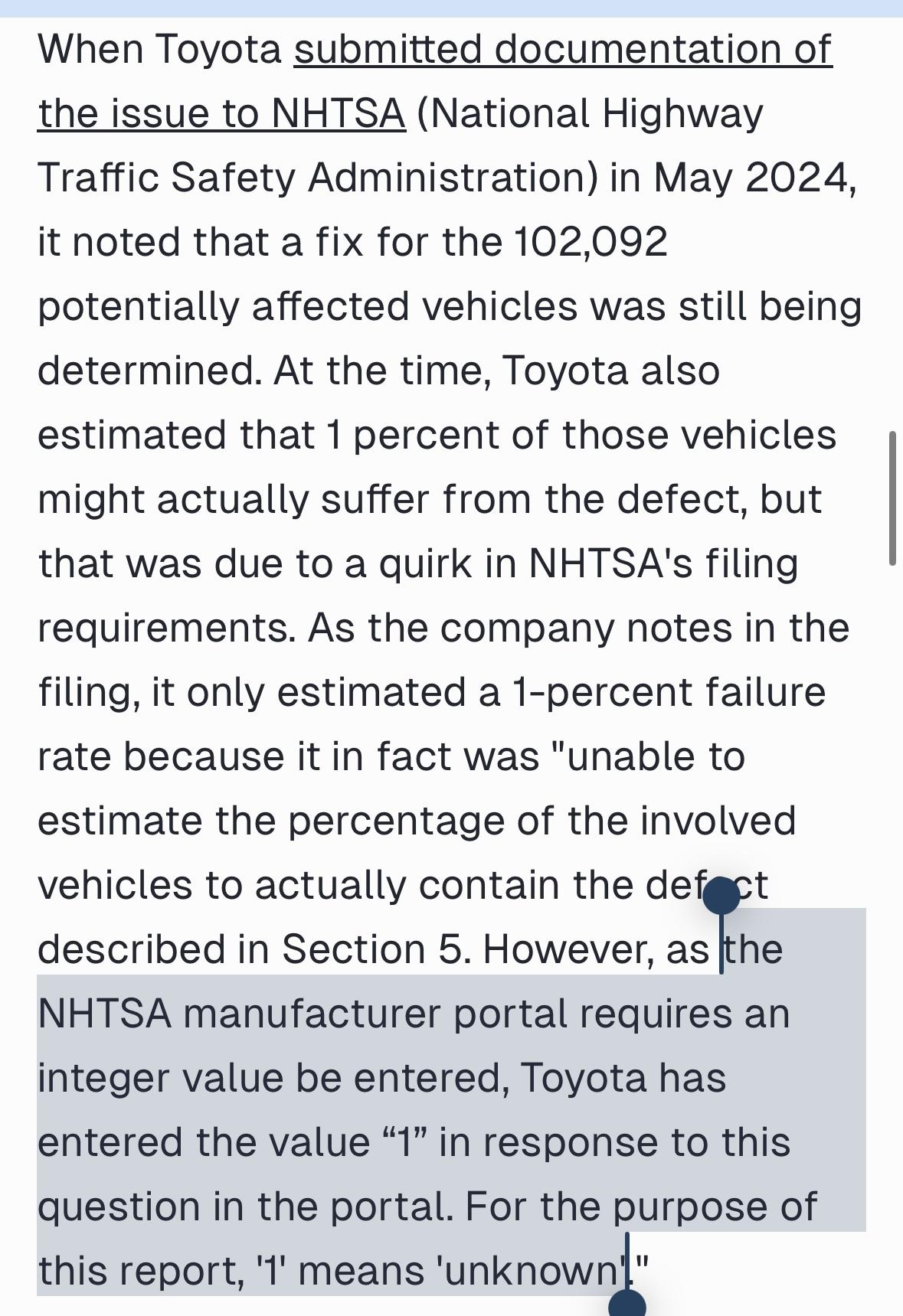
Kenn White
kennwhite@mastodon.socialInteresting nugget in this story on the historic mass recall to replace 100,000 engines in Toyota trucks & Lexus SUVs: When Toyota first reported the problem to the government, the total # of vehicles hadn't been determined, but NHTSA's website required an "integer value" in the percentage of vehicles impacted field, but "1" also meant "unknown". [insert Do You Even UX Bro gif]
https://www.motortrend.com/news/toyota-engine-recall-tundra-pickup-lexus-lx-suv/
AWS in GovcCoud US-East _accidentally_ upgrading MySQL from 5.7.X to 8.X.
DevOpsBorat was right. Error is human, automatically upgrading a database fleet to a new major MySQL version is #devops .
No opportunity goes to waste ;-)
https://www.theverge.com/2024/7/26/24206719/microsoft-windows-changes-crowdstrike-kernel-driver
Alberto Ruiz
aruiz@mastodon.socialI just wrote some initial ramblings on my attempt to write a Rust based bootloader for Open Firmware/ppc64le
https://siliconislandblog.wordpress.com/2024/07/25/booting-with-rust-chapter-1/