Posts
2469Following
662Followers
1486Dominic White
singe@chaos.socialI once had the pleasure of working with @mslaviero, and miss his smarts and wit. This blog post on how @ThinkstCanary architects for security is worth a read for many reasons - but the biting insight delivered with a chuckle is what I’m most enjoying.
https://blog.thinkst.com/2024/07/unfashionably-secure-why-we-use-isolated-vms.html
Daniel J. Bernstein
djb@cr.yp.toGave a burst of new talks over the past week, including intros to (1) patents, (2) timing variations in crypto code, (3) modern tools to avoid bugs in rewriting snippets to run in constant time, and, on the more mathematical side, (4) cola cryptography: https://cr.yp.to/talks.html
Binary Ninja
binaryninja@infosec.exchangeOur UEFI support added in 3.5 continues to improve! 4.1 released last week adds TE support, platform types for SMM, PEI, and PPI and updates to EFI Resolver.
https://binary.ninja/2024/07/17/4.1-elysium.html#uefi-enhancements
And we're not done, keep an eye out for an in-progress blog post with more details.
/r/netsec
_r_netsec@infosec.exchangeNew OpenSecurityTraining2 mini-class: "Debuggers 1102: Introductory Ghidra" https://p.ost2.fyi/courses/course-v1:OpenSecurityTraining2+Dbg1102_IntroGhidra+2024_v2/about
Mr. Bitterness
wdormann@infosec.exchangeBinarly's PKFail:
Yet another way that SecureBoot is broken. This time it's due to manufacturers like Acer, Dell, Gigabyte, Fujitsu, HP, Intel, Lenovo, and SuperMicro using test/public keys to secure the kingdom. (The Platform Key (PK))
https://www.binarly.io/blog/pkfail-untrusted-platform-keys-undermine-secure-boot-on-uefi-ecosystem
Surely my no-name (Beelink) cheapo Chinese PC does the right thing, right?
Oh...
"DO NOT TRUST - AMI Test PK"
Nobody could possibly know what that could imply.
N O B O D Y
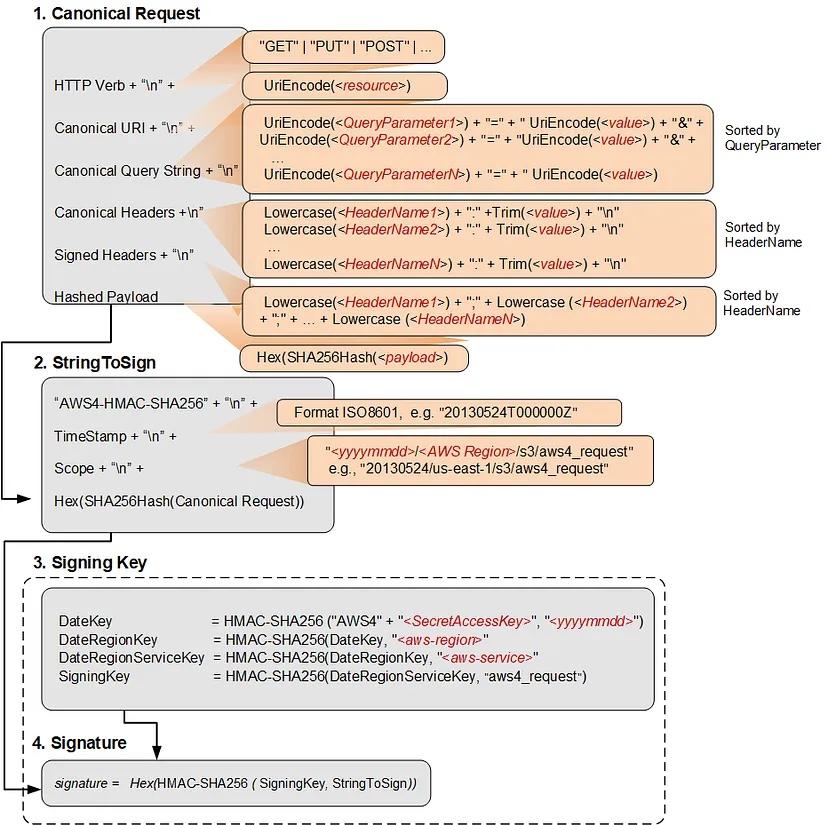
Kenn White
kennwhite@mastodon.socialCloud nerds will enjoy this. Cryptographer Tal Be'ery reverse engineered AWS session tokens and has a detailed write-up.
https://medium.com/@TalBeerySec/revealing-the-inner-structure-of-aws-session-tokens-a6c76469cba7
Trend Zero Day Initiative
thezdi@infosec.exchangeIn June, we disclosed several vulnerabilities in the Deep Sea Electronics DSE855. Today, ZDI analyst @infosecdj provides his in-depth analysis of the bugs and their root causes. He includes the timeline for disclosure. https://www.zerodayinitiative.com/blog/2024/7/25/multiple-vulnerabilities-in-the-deep-sea-electronics-dse855
Binary Ninja
binaryninja@infosec.exchangeRunning an ARM Linux machine but still want to do RE? Or maybe you're a sad apple silicon user who misses running native VMs you could use your regular tooling in. With Binary Ninja 4.1, our stable branch includes ARM Linux support!
https://binary.ninja/2024/07/17/4.1-elysium.html#linux-arm-builds
Nikoloz K.
nikolozk@infosec.exchangeIn the trenches, security and IT teams are the real heroes. The CrowdStrike incident crashed 8.5M Windows devices, and IT worked around the clock to restore systems. But did they get the recognition they deserved from leadership? Too often, their efforts go unnoticed while facing unrealistic expectations. As leaders, we must have their backs - publicly appreciate their work, ensure they have resources, and advocate for them to the C-suite. That's how we build resilient, high-performing teams.
screaminggoat
screaminggoat@infosec.exchangeProgress Telerik security advisories (edit: plural):
- Insecure Deserialization Vulnerability - CVE-2024-6327 (9.9 critical, disclosed 24 July 2024) In Progress Telerik Report Server versions prior to 2024 Q2 (10.1.24.709), a remote code execution attack is possible through an insecure deserialization vulnerability.
- Object Injection Vulnerability - CVE-2024-6096 In Progress Telerik Reporting versions prior to 18.1.24.709, a code execution attack is possible through object injection via an insecure type resolution vulnerability.
No mention of exploitation.
Why you should care about CVE-2024-6327: FIVE Telerik vulnerabilities are known exploited vulnerabilities, TWO specifically called Progress Telerik. One in particular, CVE-2019-18935, is a deserialization of untrusted data vulnerability. This is the same one exploited against the U.S. government last year as noted by CISA on 15 June 2023: Threat Actors Exploit Progress Telerik Vulnerabilities in Multiple U.S. Government IIS Servers. Patch your Teleriks.
cc: @cR0w @tas50 @campuscodi
daniel:// stenberg://
bagder@mastodon.socialCVE-2024-6197: freeing stack buffer in utf8asn1str. (severity medium) libcurl's ASN1 parser has this utf8asn1str() function used for parsing an ASN.1 UTF-8 string. It can detect an invalid field and return error. Unfortunately, when doing so it also invokes free() on a 4 byte local stack buffer.
A bit more gasoline to pour into Clownstrike's fire... ;-)
zhenech
zhenech@chaos.socialAnyone can Access Deleted and Private Repository Data on GitHub ◆ Truffle Security Co.
https://trufflesecurity.com/blog/anyone-can-access-deleted-and-private-repo-data-github
Haifei Li
haifeili@bird.makeupCongrats @nachoskrnl for being nominated @pwnieawards for his 3-episode research work on Windows paths - well deserved (yes, I nominated it:)).
https://x.com/PwnieAwards/status/1815894380789592298
Samuel Groß
saelo@chaos.socialSomething I've had on my list for quite some time and finally got around to now: updating the HowFuzzilliWorks document: https://github.com/googleprojectzero/fuzzilli/blob/main/Docs/HowFuzzilliWorks.md
Besides a number of smaller changes (e.g. new mutators), the design of the HybridEngine has changed considerably since the document was initially written.
Happy fuzzing!
Sebastian
moehrenfeld@social.karotte.org#TIL that the #IAEA uses something called a „COBRA seal“ to seal relevant objects against manipulation. One type of these seals works by using a multi-core optical cable. When the seal is locked a random number of cores are cut. This creates a unique optical pattern that can be verified simply by shining a light into the cable and can’t be recreated.
The Verge
verge@mastodon.socialThe moral bankruptcy of Marc Andreessen and Ben Horowitz https://www.theverge.com/2024/7/24/24204706/marc-andreessen-ben-horowitz-a16z-trump-donations
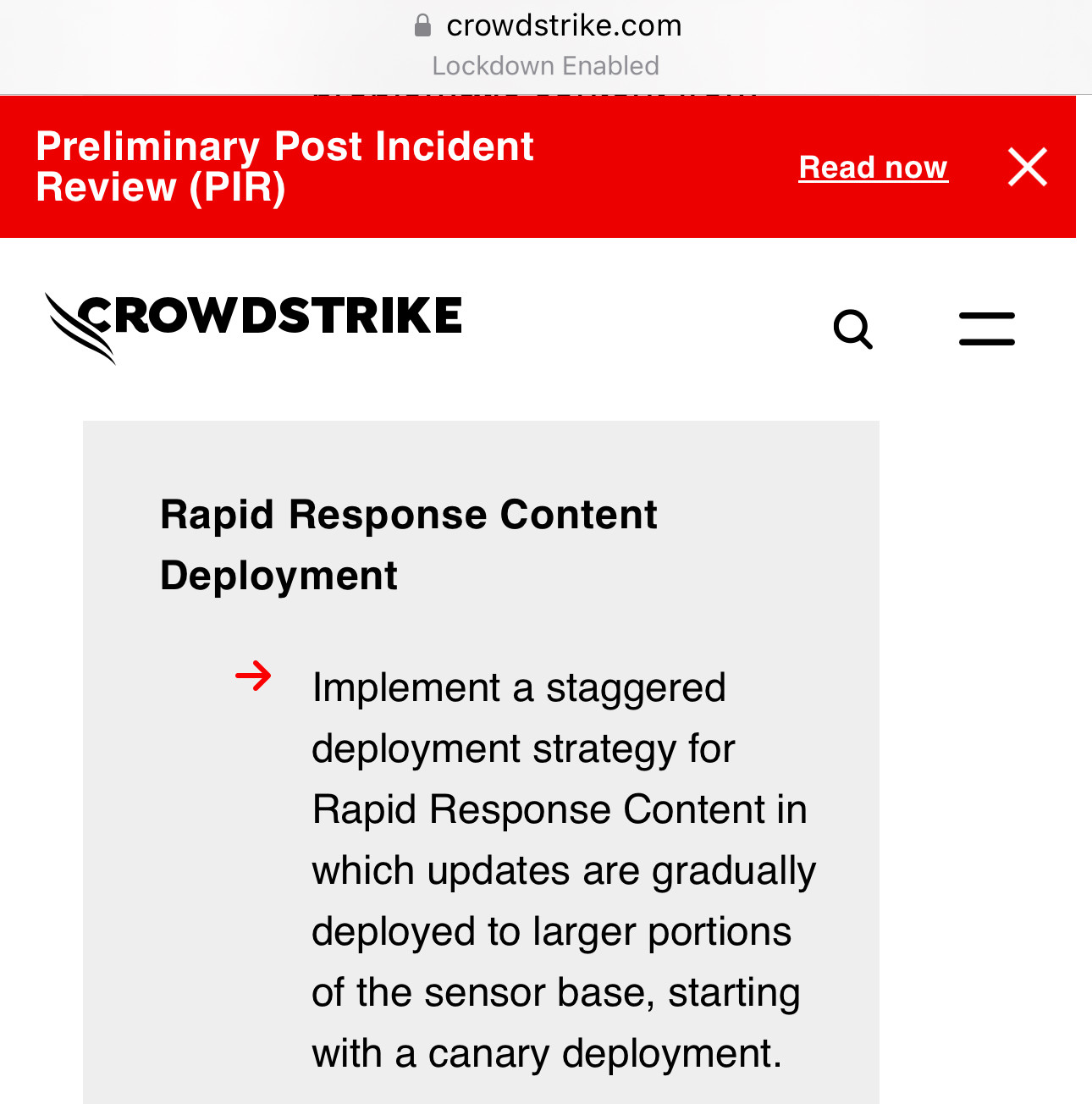
Kevin Beaumont
GossiTheDog@cyberplace.socialThe initial Post Incident Review is out from CrowdStrike. It’s good and really honest.
There’s some wordsmithing (eg channel updates aren’t code - their parameters control code).
The key take away - channel updates are currently deployed globally, instantly. They plan to change this at a later date to operate in waves. This is smart (and what Microsoft do for similar EPP updates).
https://www.crowdstrike.com/falcon-content-update-remediation-and-guidance-hub/
hanno
hanno@mastodon.socialDo I know anyone with a mail address on a mail server managed by barracuda networks who would help me with something? I'd like to test a few things (just sending you a few test mails and see if they arrive).
BrianKrebs
briankrebs@infosec.exchangeWild, true story from the security awareness and training company KnowBe4 that details how they inadvertently hired a North Korean hacker who was posing as a Western tech worker.
Kudos to them for publishing this. If it can happen to a security awareness company, it can happen to anyone (full disclosure: they've been an advertiser on my site for ages).
https://blog.knowbe4.com/how-a-north-korean-fake-it-worker-tried-to-infiltrate-us