Posts
2504Following
650Followers
1469buherator
buheratorhttps://www.thezdi.com/blog/2025/7/24/cve-2025-20281-cisco-ise-api-unauthenticated-remote-code-execution-vulnerability
James Kettle
albinowax@infosec.exchangeYou know those non-vulnerabilities that companies get forced to fix for compliance reasons? I've found a full bypass for a common patch strategy. I'm half-tempted to keep it secret for the greater good 😂
Trail of Bits
trailofbits@infosec.exchangeAt DistrictCon's inaugural Junkyard competition, we achieved full remote execution on two popular home network devices: a Netgear WGR614v9 router and BitDefender Box V1 security appliance.
Our exploitation techniques included chaining four buffer overflow vulnerabilities with authentication bypass on the router, plus a novel "bashsledding" ROP technique that sprays shell commands into NVRAM for reliable code execution.
Read the blog: https://blog.trailofbits.com/2025/07/25/exploiting-zero-days-in-abandoned-hardware/
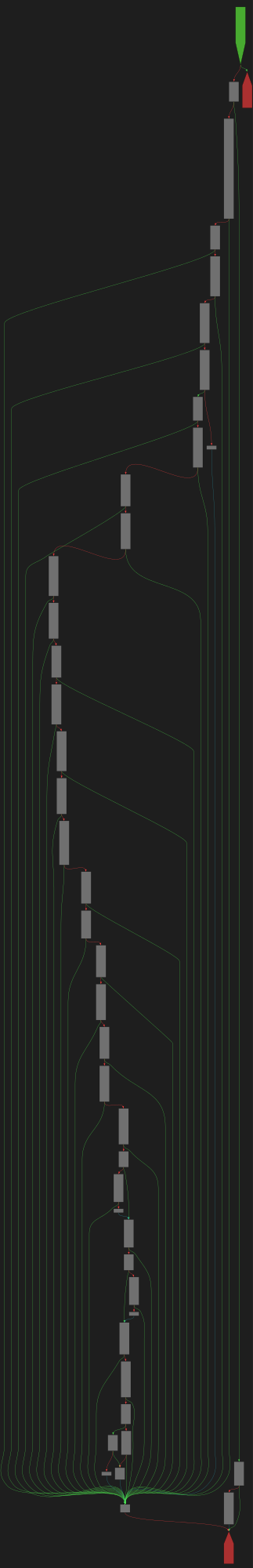
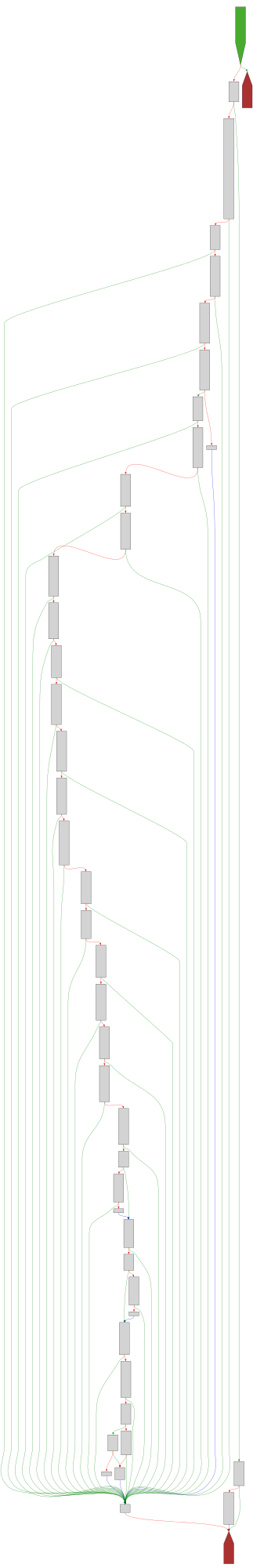
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00598f60
ossl_ec_GFp_simple_ladder_post
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00598f60.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00598f60.json&colors=light
Imagine being a welder. And every day you come to work you have to worry about whether your tools are where you left them. Or if your controls have been reversed. Or the tanks are mislabeled or rearranged. Or if your 110v equipment suddenly requires 220v. Or the trigger on your MIG welder only works after you tap on three fire hydrants. Or your visor has ads pop up in the way of your vision. Or cameras and microphones show up to record all your work and you don't know who has access to those recordings. Or that supply of rods you just purchased will no longer work with your torch because the manufacturer decided that you can only use rods purchased from them, even though that was not disclosed at the time of purchase.
Why the fuck does tech get away with it?
Kevin Beaumont
GossiTheDog@cyberplace.socialIf you're looking at this thinking 'wait, CVE-2025-6543 is a denial of service vuln?', it's not - it turns out Citrix knew orgs were getting shelled but chose to not tell the public. The implants persist after patching.
Rairii 

Rairii@labyrinth.zone
https://silliest.website:3/
buherator
buheratorbuherator
buheratorhttps://www.ibm.com/support/pages/node/7240410?myns=swgother&mynp=OCSWG60&mynp=OCSSKWKM&mynp=OCSSC5L9&mynp=OCSSTS2D&mynp=OCSS9QQS&mynp=OCSSB23CE&mync=A&cm_sp=swgother-_-OCSWG60-OCSSKWKM-OCSSC5L9-OCSSTS2D-OCSS9QQS-OCSSB23CE-_-A
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-80-itw-windows-bugs-deterministic-ios-exploits-pwn2own-firefox-vulns-and-more/
buherator
buheratorhttps://blog.0patch.com/2025/07/micropatches-for-windows-disk-cleanup.html
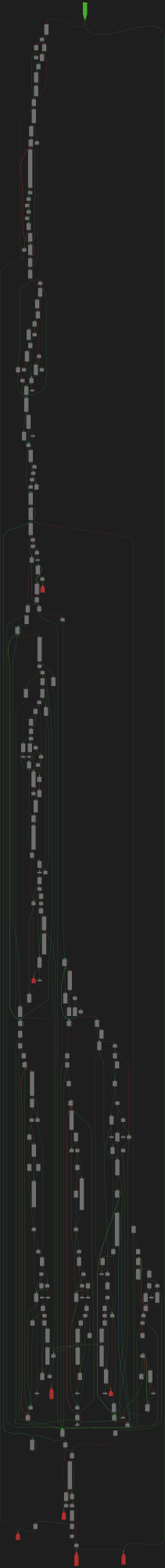
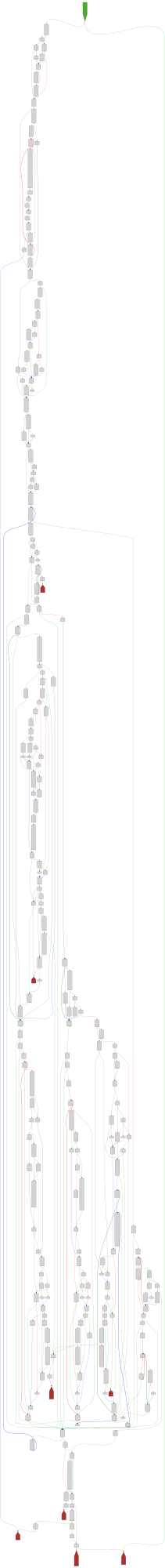
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0091ec00
_dl_relocate_object
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0091ec00.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0091ec00.json&colors=light
Andreas Klopsch
hackingump1@infosec.exchange🛠️ RIFT just got an upgrade!
Now supports FLIRT signature generation on Linux 🐧
Perfect for reverse engineering Rust malware 🦀
🔗 https://github.com/microsoft/RIFT
#DFIR #ReverseEngineering #RustLang #FLIRT #MalwareAnalysis