Posts
3352Following
711Followers
1578BTW, glitching the early UART boot path that is fuse protected gives you access to very early nvidia-only key material that is locked down pretty early during the normal boot path. Every single other key on the TX2 is either derived from the FEK1 or FEK2 depending on a fuse bit. Default seems to be FEK2.
SHA1(FEK1) = 9d00fe0637b15de7b417c740a6210d19932c7eb4
SHA1(FEK2) = 0e0fdef7a31d32aaf0fee77679e065652daecb44
I initially did all this to reverse engineer the Denver microcode, however I never could make sense of the instruction set encoding. If anyone wants to tackle this, I can decrypt both microcode stages - seemingly a loader and the final JIT and I more or less completely reverse engineered MB1 that loads the Denver microcode.
/cc @elise
Ken Shirriff
kenshirriff@oldbytes.spaceIf you're interested in obscure details of the microcode in the Intel 8087 floating-point chip, I have a new blog post...
https://www.righto.com/2025/12/8087-microcode-conditions.html
buherator
buheratorThis is the attention span vendors are expecting from you.
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20251226-00/?p=111919
pancake 
pancake@infosec.exchange
Today I saw this UNIX v4 PDP11 emulator (running simh in the browser) and decided to write an IO plugin for radare2 to load tapes. Here's the source in case you are curious about how tapes are structured and how to extend r2 with new features like IO backends. https://github.com/radareorg/radare2/commit/aeeccc1d23d3b75edcd6e0013f1372830a6af134
Gentle Reminder for Newcomers  :
:
Boosting posts keeps Mastodon alive!
Boost what you love! 💚
Boost freely!  ✨
✨
New post on my blog! Decapping with DMSO.
https://dev-zzo.github.io/blarg/2025/12/19/decapping-dmso.html
GitHub Security Lab
GitHubSecurityLab@infosec.exchangeLearn why some vulnerabilities resist to fuzzing and persist in long-enrolled OSS-Fuzz projects, and how you can find them!
Project Zero Bot
p0botSamsung: QuramDng FixBadPixelList opcode out-of-bounds read/write
https://project-zero.issues.chromium.org/issues/448241955
CVE-2025-58479
Project Zero Bot
p0botSamsung: QuramDng opcodes ignore PixelType, leading to out-of-bounds read/writes
https://project-zero.issues.chromium.org/issues/447479300
CVE-2025-58478
buherator
buheratorhttps://swarm.ptsecurity.com/blind-trust-what-is-hidden-behind-the-process-of-creating-your-pdf-file/
Gynvael Coldwind 🐈
gynvael@infosec.exchangeGlitches in games, especially used for speedrunning, are one of the most fun aspects of hacking to watch!
As an example, check out this video "How Speedrunners BEAT Hollow Knight Silksong In 10 Minutes!" by Abyssoft
LaurieWired
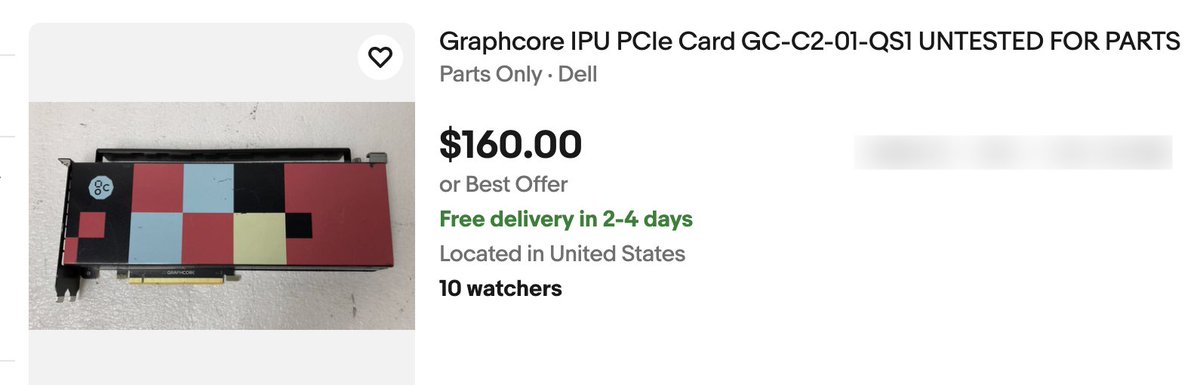
lauriewired@bird.makeupThe “opposite” of a GPU is kinda weird.
Graphcore has a strange chip (IPU) that loves tiny batches...but is also massively parallel.
It used to cost ~$100k. Now you can get one on Ebay for $160 bucks.
The catch is it's almost impossible to use.
mid_kid
mid_kid@fosstodon.orgTime to promote this one in 1h. This was an incredible research project, and having seen the talk before at WHY, it's really well explained despite how technical it is.
Spectre in the real world: Leaking your private data from the cloud with CPU vulnerabilities
dimarts, 30 de desembre del 2025 0:15 CET (Europe/Berlin), Zero
buherator
buheratorShow content
https://www.youtube.com/watch?v=50vL1uAXn7s
buherator
buheratorhttps://media.ccc.de/v/39c3-from-silicon-to-darude-sand-storm-breaking-famous-synthesizer-dsps
I love CCC talks because you get to hear "pretty easy" and things like "special microscope lenses" in the same sentence :)
buherator
buheratorhttps://video.infosec.exchange/w/7VRDzwthgrSzeAHwHvkPtt
#ReverseEngineering