Posts
3037Following
703Followers
1550Talos Vulnerability Reports
talosvulnsThe Biosig Project libbiosig MFER parsing multiple stack-based buffer overflow vulnerabilities
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2296
CVE-2025-66048,CVE-2025-66043,CVE-2025-66047,CVE-2025-66044,CVE-2025-66046,CVE-2025-66045,CVE-2025-66043,CVE-2025-66044,CVE-2025-66045,CVE-2025-66046,CVE-2025-66047,CVE-2025-66048
quarkslab
quarkslab@infosec.exchangeA modern tale of Blinkenlights, cheap Christmas shopping and curiosity, narrated by @virtualabs
Firmware extraction and reverse engineering of a smartwatch FTW!
buherator
buheratorhttps://blog.trailofbits.com/2025/12/11/introducing-mrva-a-terminal-first-approach-to-codeql-multi-repo-variant-analysis/
vim user doing God's work
RPGPGM
rpgpgm@mastodon.socialIn #IBMi 7.6 TR1 and 7.5 TR7 three new date formats have been introduced that will make solving 2040 issue easier.
💙 #IBMi #rpgpgm #IBMChampion
https://www.rpgpgm.com/2025/12/new-date-formats-for-rpg.html
daniel:// stenberg://
bagder@mastodon.socialWe currently have three pending CVEs to be announced in the next #curl release (severity low + medium x 2)
All three found with AI powered tooling.
So it is happening.
buherator
buheratorhttps://portswigger.net/research/the-fragile-lock
buherator
buheratorhttps://medium.com/@Debugger/how-citrix-fixed-an-esc1-risk-in-their-documentation-5051bf410139?source=rss-3ba65b326b28------2
❄️☃️Merry Jerry🎄🌲
jerry@infosec.exchangeRandom realization: MS Teams is the Lotus Notes of web meetings.
Damien Guard
damieng@mastodon.socialOh dear the entire https://www.lyonlabs.org site is offline *and* excluded from archive.org.
It's a massive archive of vintage and modern GEOS and C64 material a lot of it seemingly not found elsewhere.
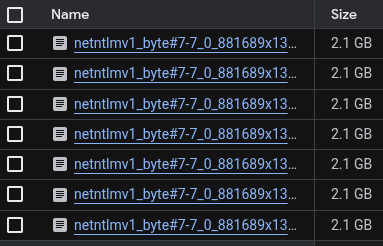
Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge.
https://research.google/resources/datasets/
Dataset is available for download at:
▪️https://console.cloud.google.com/storage/browser/net-ntlmv1-tables [Login required]
▪️gs://net-ntlmv1-tables
Trend Zero Day Initiative
thezdi@infosec.exchangeIt's the final Patch Tuesday of 2025! #Microsoft and #Adobe took it easy on us with a smaller release, but there's 1 0-day being exploited & an Exchange bug reported by the NSA. @dustin_childs fills you in on the details & where to focus your priorities. https://www.zerodayinitiative.com/blog/2025/12/9/the-december-2025-security-update-review
Julia Evans
b0rk@jvns.cai finally gave in and started using uv to manage the dependencies for my Python scripts and it’s great https://jvns.ca/til/python-inline-dependencies/
buherator
buheratorProblem is 1) there are many obvious bots 2) those who are likely not bots also seem to use LLM/templates to communicate, making them look like bots.
If you don't want to get reported, use your own voice!
#fedihire
Phrack
phrack@haunted.computerPhrack #72 PUZZLE CHALLENGE >>> WALKTHROUGH <<< is OUT.
Everyone who did not find the hidden secrets in the hardcopy release: This is your chance.
♥️ Stay curious and live forever ♥️
Samuel Groß
saelo@chaos.socialWe derestricted a number of vulnerabilities found by Big Sleep in JavaScriptCore today: https://issuetracker.google.com/issues?q=componentid:1836411%20title:JavascriptCore
All of them were fixed in the iOS 26.1 (and equivalent) update last month. Definitely some cool bugs in there!
Samuel Groß
saelo@chaos.socialV8 now has a (experimental) JS bytecode verifier!
IMO a good example for the benefits of the V8 Sandbox architecture:
- Hard: verify that bytecode is correct (no memory corruption)
- Easier: verify that it is secure (no out-of-sandbox memory corruption)
The sandbox basically separates correctness from security.
More details: https://docs.google.com/document/d/1UUooVKUvf1zDobG34VDVuLsjoKZd-CeSuhvBcLysc7U/edit?usp=sharing
Implementation: https://source.chromium.org/chromium/chromium/src/+/main:v8/src/sandbox/bytecode-verifier.cc
BleepingComputer
BleepingComputer@infosec.exchangeAmerican IT software company Ivanti warned customers today to patch a newly disclosed vulnerability in its Endpoint Manager (EPM) solution that could allow attackers to execute code remotely.