Posts
3070Following
703Followers
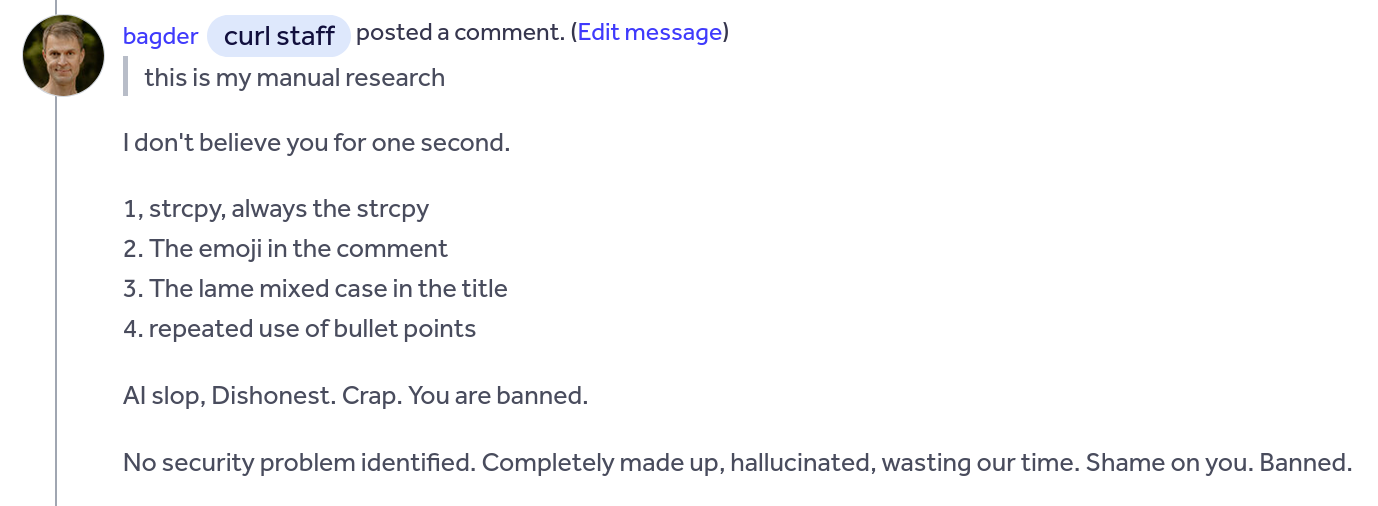
1553buherator
buheratorhttps://github.com/silentsignal/oracle_forms/pull/3#issuecomment-3434380477
#pentesting
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: The U.S. govt accused Peter Williams, ex general manager of hacking tool maker L3Harris Trenchant, of stealing trade secrets and selling them to buyer in Russia.
As we reported earlier this week, Trenchant was investigating a leak of internal tools this year. At this point, it's unclear if that investigation is related to the accusations against Williams.
/r/netsec
_r_netsec@infosec.exchangePrivescing a Laptop with BitLocker + PIN https://www.errno.fr/Bitlocker_TPM_and_PIN_privesc
CFG Bot 🤖
cfgbot@mastodon.socialProject: microsoft/typescript-go https://github.com/microsoft/typescript-go
File: testdata/baselines/reference/submodule/compiler/enumLiteralsSubtypeReduction.js:3088 https://github.com/microsoft/typescript-go/blob/cab7a0bf793f3ba0e83619798f2eb191673fe4c7/testdata/baselines/reference/submodule/compiler/enumLiteralsSubtypeReduction.js#L3088
function run(a)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2Ftypescript-go%2Fblob%2Fcab7a0bf793f3ba0e83619798f2eb191673fe4c7%2Ftestdata%2Fbaselines%2Freference%2Fsubmodule%2Fcompiler%2FenumLiteralsSubtypeReduction.js%23L3088&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2Ftypescript-go%2Fblob%2Fcab7a0bf793f3ba0e83619798f2eb191673fe4c7%2Ftestdata%2Fbaselines%2Freference%2Fsubmodule%2Fcompiler%2FenumLiteralsSubtypeReduction.js%23L3088&colors=light
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialToday is the annual memorial day of the 1956 Hungarian revolution.
Today I learned that Victor Ambrus (Ambrus Győző), the artist who worked on Time Team, was one of the freedom fighters in Budapest in '56. He was a 3rd year art student at the time. He had to flee the country after the Soviets crushed the revolution.
Trend Zero Day Initiative
thezdi@infosec.exchangeDue to travel complications and delayed flights, the live stream scheduled for 3PM Irish time has been cancelled. We apologize for the inconvenience.
highly caffeinated adorable rodent
algernon@come-from.mad-scientist.clubIf anyone has a mac capable of running OpenAI's ChatGPT Atlas "browser", and is willing to conduct a short experiment aimed at figuring out how to identify & block that thing, please let me know!
Update: I have some preliminary results, thanks! I'll conduct more research if/when there's version of Atlas I can run (likely in a Windows VM).
Neodyme
neodyme@infosec.exchangeCheck out our new blog post on a research-driven look at software-only DRM. Explore how the Qiling emulation framework can be used to analyze Widevine and how Differential Fault Analysis (DFA) and emulation aid de-obfuscation.
▶️ Read more: https://neodyme.io/en/blog/widevine_l3/
Cascading failures are fascinating :P
Trend Zero Day Initiative
thezdi@infosec.exchangeMiss anything from Day 2 of #Pwn2Own Ireland 2025? Join @TheDustinChilds as he recaps what happened and covers some of the highlights of the event.
https://youtu.be/Xz7jjz6xIic
Miguel Afonso Caetano
remixtures@tldr.nettime.orgRT @ednewtonrex
Wait… so users of OpenAI’s Atlas browser can opt-in the web pages they browse - *which belong to other people* - to AI training?
Cool cool
Claus Cramon Houmann
claushoumann@mastodon.socialIf you know who did this, or if you know how to set it back, the hotel kindly asks you to do so, respecting the fun achievement unlocked :)
https://infosec.exchange/@xme/115422139879568495
blackle mori
suricrasia@lethargic.talkative.fishevery AI generated pixel, every AI generated token I see makes me want to use the internet less. it makes me want to log off and spend the rest of my days reading books published before 2020. this must be how the paranoid creatives felt in the 2000s when cross-site tracking and the patriot act also pushed them offline. this must be how those creatives who refused to give up their own methods of distribution felt when things like facebook and twitter and youtube monopolized attention through the 2010s and turned the internet into a small collection of walled gardens. I don't know what kind of creative you'd call me, but I cannot abide by the internet being polluted by mushy, merely-probable junk data which is drowning out what had once been a place to find real testimony, real human effort and art whose maxim is to bridge the gap between us. sure there will always be oases, places where human creativity continues to thrive, but I'll forever miss when the entire land was covered in green.
this story is crazy not because someone in the exploit business got a taste of their own medicine, that part should be expected. the crazy thing is that trenchant, widely considered to be one of the “good discerning western exploit shops” was leaking chrome exploits to who knows where.
https://infosec.exchange/@lorenzofb/115412729875549507
Trend Zero Day Initiative
thezdi@infosec.exchangeBoom! Rafal Goryl of PixiePoint Security needed two attempts but was able to get his exploit of the Phillips Hue Bridge working. He heads off to the disclosure room to provide all the details. #Pwn2Own
Trend Zero Day Initiative
thezdi@infosec.exchangeYou can find all of the results from Day Two of #Pwn2Own Ireland at https://www.zerodayinitiative.com/blog/2025/10/22/pwn2own-ireland-2025-day-two-results - We'll be updating this blog throughout the day as results become available. #P2OIreland
Tom Schuster
evilpie@hachyderm.ioThe new version of the Sanitizer API is now enabled by default in @firefoxnightly!
https://developer.mozilla.org/en-US/docs/Web/API/Sanitizer
https://wicg.github.io/sanitizer-api/
Please give it a try and provide us with feedback.
buherator
buheratorhttps://blog.silentsignal.eu/2025/10/22/IBM-i-LIBL-Autopwn-Kill-the-Vulnerability-Class/
#IBMi exploits go brrr