Posts
2512Following
665Followers
1491Cure53 🏳️🌈
cure53@infosec.exchangeDOMPurify 3.2.7 has been released today, adding several fixes and improvements.
https://github.com/cure53/DOMPurify/releases/tag/3.2.7
Thanks to all folks who contributed 💕
Julia Evans
b0rk@jvns.caadded a cheat sheet to the official Git website
(with a lot of help from other folks who work on the website)
Yellow Flag
WPalant@infosec.exchangeDrew DeVault writes:
“Perhaps Google and Mozilla, leaders in JavaScript standards and implementations, will start developing a real standard library for JavaScript, which makes micro-dependencies like left-pad a thing of the past.”
There is an interesting logic flaw here. There is in fact String.prototype.padStart built into JavaScript, it has been available for at least eight years. How often did you see that used in production code? Me, having reviewed lots of codebases over the past years – almost never. Meanwhile the cumulative downloads for various string padding libraries on NPM still go into millions per week. It’s not even that many software projects directly depending on them, but way too many projects having complicated dependencies that in some corner of their wide dependency tree aren’t too up to date with these “newfangled” language features.
And if something else is an indicator: I still regularly see jQuery being used in new projects, decades after it became obsolete thanks to browsers improving. No amount of pointing out how harmful it is to sane development patterns helped here.
So I’m not sure that I can see Drew DeVault’s proposed solution to the dependency hell succeeding even if we could get the industry behind it. The inertia behind JavaScript is enormous, and in many areas the usage barely moved beyond JavaScript 1.5. Yet most projects today use a whole array of linters and build tools to aid development, and these are really complicated beasts. Maybe it’s possible to shrink their dependency trees a bit but the complexity isn’t going away.
Maybe the real question is: why does my build process have the potential to compromise my system unless I do some crazy hacks that no sane person would normally bother with? The build result will typically run in some kind of sandbox with very limited damage potential, why doesn’t the build process?
Open Source Security mailing list
oss_security@bird.makeupCVE-2025-6965: SQLite: Integer truncation in findOrCreateAggInfoColumn https://www.openwall.com/lists/oss-security/2025/09/06/1
CVE-2025-7709: SQLite: Integer Overflow in FTS5 Extension https://www.openwall.com/lists/oss-security/2025/09/06/2
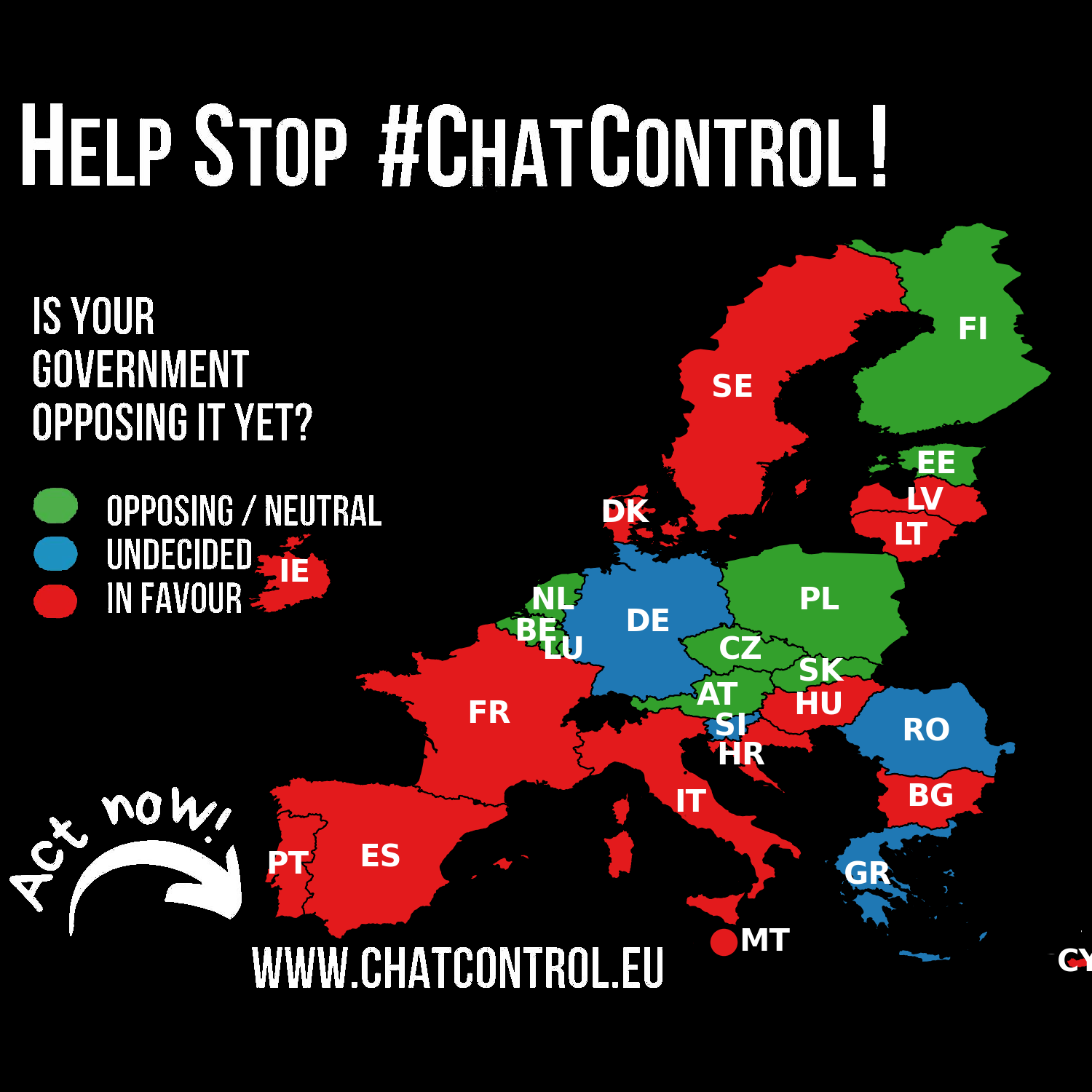
Fight Chat Control
chatcontrol@mastodon.socialGermany's position has been reverted to UNDECIDED.
Despite expressing concerns about breaking end-to-end encryption, Germany refrained from taking a definitive stance on the Chat Control proposal during the September 12th LEWP meeting. A willingness to negotiate and compromise remains.
This is an unfortunate as Germany is crucial to defeating Chat Control.
Please make your voices heard! https://fightchatcontrol.eu/
Source: https://netzpolitik.org/2025/chatkontrolle-noch-haelt-sich-widerstand/
Feoh
feoh@oldbytes.spaceThis is a Dystopian timeline: My wife was let go after 25 years working for the same bank this morning. In an apparent oops, the bank's IT department hard wiped ALL her IOS devices remotely, while she was on the road driving, relying on the GPS function.
The screw you cherry on top? Our apartment building in its infinite wisdom a couple years back switched all building locks to the Latch app.
So she was LOCKED OUT OF OUR HOUSE.
Oh, and the Latch maintained intercom at our front door is out of order.
Thanks for that. Sheesh.
buherator
buheratorhttps://hackaday.com/2025/09/16/2025-hackaday-component-abuse-challenge-let-the-games-begin/
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250916-00/?p=111602
Nothing to see here, move along!
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250916-00/?p=111602
"Nothing to see here!"
Neodyme
neodyme@infosec.exchange▶️ We built a proof-of-concept post-quantum FIDO authenticator. It's phishing- AND quantum-resistant.
✅️ Bonus: it even outperforms Google's prototype. 👀
Full write-up here: https://neodyme.io/en/blog/pqc-fido/
buherator
buheratorhttps://www.linaro.org/blog/becoming-a-kernel-developer-part1-posting-your-first-patch/
Socket
SocketSecurity@fosstodon.org🚨 Malicious update to @ctrl/tinycolor on npm is part of an active supply chain attack hitting 40+ packages across multiple maintainers. Audit & remove affected versions.
Our analysis of the malware: https://socket.dev/blog/tinycolor-supply-chain-attack-affects-40-packages
Marco Ivaldi
raptor@infosec.exchangeI've updated my #VulnerabilityResearch and #ReverseEngineering tools to use the latest version of @binarly_io award-winning #idalib #Rust bindings, which support @HexRaysSA IDA Pro 9.2 and their freshly open-sourced SDK.
#Rhabdomancer - Vulnerability research assistant that locates calls to potentially insecure API functions in a binary file.
https://github.com/0xdea/rhabdomancer
#Haruspex - Vulnerability research assistant that extracts pseudo-code from the IDA Hex-Rays decompiler.
https://github.com/0xdea/haruspex
#Augur - Reverse engineering assistant that extracts strings and related pseudo-code from a binary file.
https://github.com/0xdea/augur
For additional details:
https://security.humanativaspa.it/streamlining-vulnerability-research-with-ida-pro-and-rust/
Frederik Braun �
freddy@security.plumbing1900s: Computers allow me to do things.
Early 2000s: Computers do things for me.
Now: Computers do things to me.
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
A path traversal in LG webOS TV allows unauthenticated file downloads, leading to an authentication bypass for the secondscreen.gateway service, which could lead to a full device takeover.
This vulnerability was disclosed during our TyphoonPWN 2025 LG Category and won first place:
https://ssd-disclosure.com/lg-webos-tv-path-traversal-authentication-bypass-and-full-device-takeover/
ReynardSec
reynardsec@infosec.exchange"Abusing an 0day to steal the data that fuels macOS AI"
"In a nutshell, plugins can only access files when the Spotlight subsystem requests it and, in theory, should only return extracted information back to Spotlight—nobody else! But is Apple’s sandboxing sufficient? 🤔
Today, we’ll present a 0-day that leverages a bug from almost a decade ago(!) — one that can still be exploited from a Spotlight plugin, even on macOS Tahoe, to access TCC-protected files, including sensitive databases that log user and system behaviors that can power Apple’s AI features 😈"
 Corveon
Corveon