Posts
3368Following
712Followers
1580
Esteban Küber 
ekuber@hachyderm.io
Wanted: a #RustLang tool with 4 panes:
- desired generated code
- an in progress proc-macro being written
- input #Rust code where the proc-macro is being applied
- a live updating view of the actual generated code with diff annotations against what was desired
If you want to go fancier, tie things in the output to the input and provide suggestions on where things are missing pre-expansion for the output to march the expectation. I feel like 90% of this can be accomplished today with tmux+a file watcher+direct rustc invocations using -Zunpretty=expanded, but it'd be lovely to have an actual tool for this.
Mitch Wagner
mitch@hachyderm.io“War is war and hell is hell and of the two, war is a lot worse.” https://www.tumblr.com/jimstares/790549011146981376
TrendAI Zero Day Initiative
thezdi@infosec.exchangeWe have updated the #Pwn2Own Ireland rules to clarify scoping for WhatsApp for Windows. For WhatsApp for Windows, both “WhatsApp” and the “WhatsApp Beta” applications are in scope for the competition. #P2OIreland https://www.zerodayinitiative.com/blog/2025/7/30/pwn2own-returns-to-ireland-with-a-one-million-dollar-whatsapp-target
Fritz Adalis
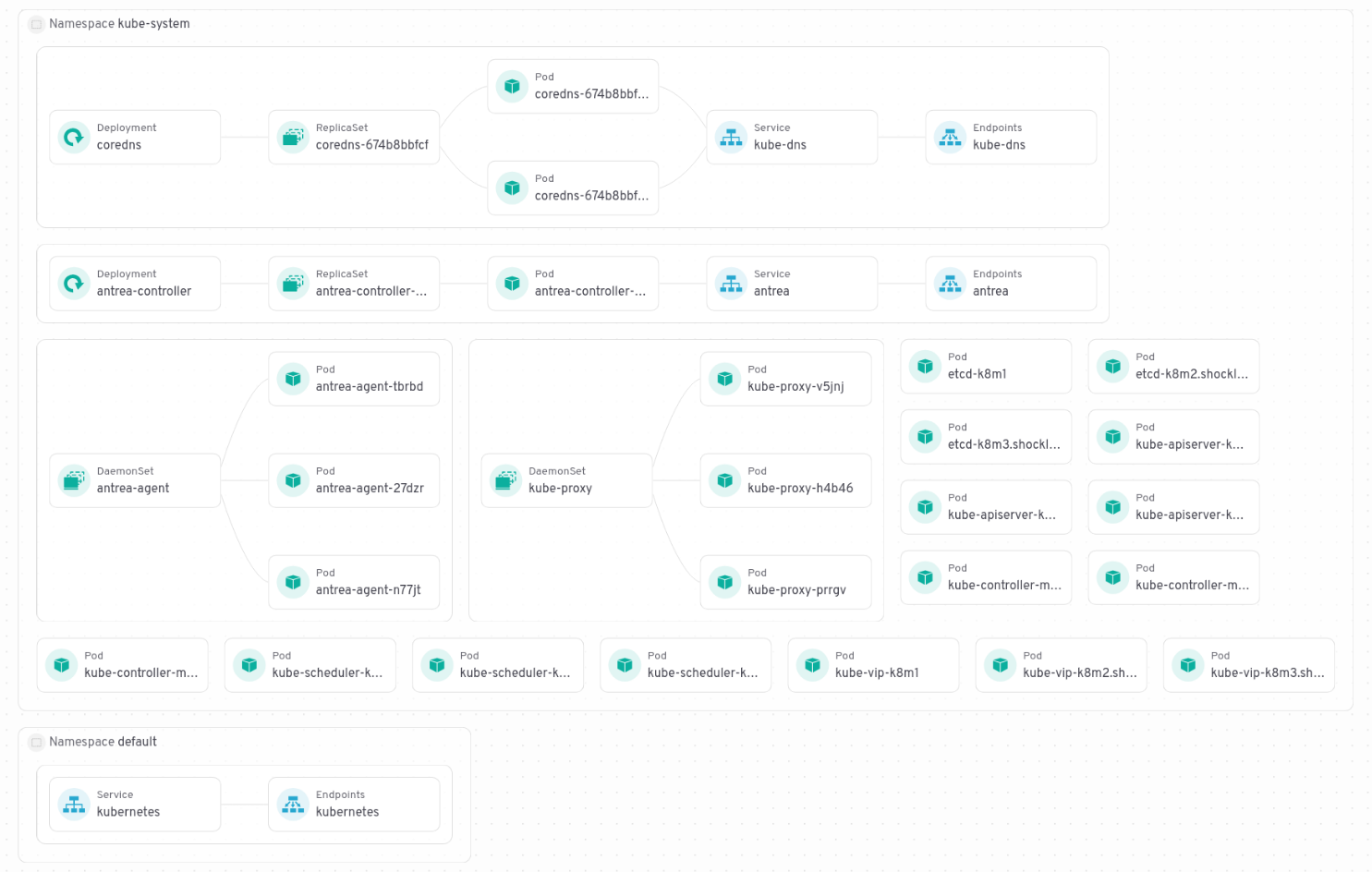
FritzAdalis@infosec.exchangeKubernetes is a lot of fun. Here's the layout of a 3-node HA cluster that's doing... absolutely nothing.
I have played me for an absolute fool!
pancake 
pancake@infosec.exchange
📣I will be reaching out all the #r2con2025 speakers next week, in order to confirm the details of every presentation and get the schedule published in September!
If you are willing to present the #CFP closes in October! Reach me out if you have questions or half-shaped proposals to show!
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://wero-wallet.eu/ - a European replacement for PayPal, Google and Apple
Threats:
* https://the-sequence.com/rustypages-malware-part-i - some nice new shiney malware for OS X
* https://www.crowdstrike.com/en-us/blog/murky-panda-trusted-relationship-threat-in-cloud/ - don't you just hate being poked with bamboo?
Detection:
* https://camel-security.github.io/ - LLM guard rails from GOOG
* https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_logging?view=powershell-5.1#enabling-script-block-logging - MSFT's protected logging feature for PS
* https://adsecurity.org/?p=4510 - mm, honey
* https://blog.pypi.org/posts/2025-08-18-preventing-domain-resurrections/ - preventing domain resurrections in PyPI
Bugs:
* https://www.heise.de/en/news/Docker-Desktop-Critical-vulnerability-allows-host-access-10560707.html - attackers may no longer be contained
https://bughunters.google.com/blog/5800341475819520/a-fuzzy-escape-a-tale-of-vulnerability-research-on-hypervisors - I hate being supervised, do you?
Exploitation:
* https://arxiv.org/abs/2507.09411 - feasibility of generating variant malware using LLMs
* https://phrack.org/issues/72/5_md#article - @phrack #72 lands and it's a goodie... aforementioned link is to @orange's work on PHP
* https://versprite.com/blog/the-shell-was-restricted-but-the-kernel-memory-was-wide-open/ - attacking Linux-based firmware for LPE via the kernel
* https://blog.anh4ckin.ch/posts/netexec-workshop2k25/ - nosing around an AD lab
Ars Technica
arstechnica@mastodon.socialSam Altman calls AI a “bubble” while seeking $500B valuation for OpenAI
"Someone will lose a phenomenal amount of money," says CEO while fundraising at record prices.
https://arstechnica.com/information-technology/2025/08/sam-altman-calls-ai-a-bubble-while-seeking-500b-valuation-for-openai/?utm_brand=arstechnica&utm_social-type=owned&utm_source=mastodon&utm_medium=social
buherator
buheratorPOML is a way to wrap your natural language prompts to XML to give them structure again:
https://github.com/microsoft/poml
Seriously.
Techokami
techokami@woof.techWell AMD just made an oopsie! They accidentally posted the complete source code to FSR4, then tried to remove it, but uhhhhh... here's the repo: https://github.com/GPUOpen-LibrariesAndSDKs/FidelityFX-SDK/tree/01446e6a74888bf349652fcf2cbf5f642d30c2bf
and here's the commit history: https://github.com/GPUOpen-LibrariesAndSDKs/FidelityFX-SDK/commit/01446e6a74888bf349652fcf2cbf5f642d30c2bf
MIT license, have fun!
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-83-windows-p20-wins-llms-codeql-mcp-takes-down-defcon-ctf-and-more/
Mari0n
pinkflawd@bird.makeup@blackhoodie_re will be back at @hexacon_fr this year, and we're currently looking for former BlackHoodies who would be willing to give a training, between Oct 6 and 9! https://blackhoodie.re/Hexacon2025/
Ivan Molodetskikh
YaLTeR@mastodon.onlinelonging for the day when computers are advanced enough to handle 65k bytes of plaintext
Zack Whittaker
zackwhittaker@mastodon.socialNEW: Earlier this month, two hackers published their findings in Phrack magazine after hacking into the computer of a North Korean government hacker. Now, in speaking with @lorenzofb, the hackers explain why they went public — even though their breach was probably illegal.
David Gerard
davidgerard@circumstances.runlol the xz backdoor lives on in docker images https://www.binarly.io/blog/persistent-risk-xz-utils-backdoor-still-lurking-in-docker-images
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
⚠️#Docker: If you are using Docker for Desktop you need to update it TODAY to v4.44.3. Critical CVE-2025-9074 #vulnerability in previous versions allows malicious containers to access host system:
👇
https://www.heise.de/en/news/Docker-Desktop-Critical-vulnerability-allows-host-access-10560707.html
hanno
hanno@mastodon.socialAnyone happens to know if there's any easy trick to bypass an Incapsula "security firewall" that thinks downloading with curl/wget is an attack to be prevented? (It's not just the user agent, I tried that.)