Posts
2471Following
660Followers
1482École des Bro-Arts
aphyr@woof.groupMade a little pornographic test case for the UK #OnlineSafetyAct, to see whether we can get Ofcom to ban AWS S3 from the United Kingdom.
daniel:// stenberg://
bagder@mastodon.socialDoing #curl command lines in powershell can be a whole adventure: https://medium.com/@shindeshreeharsh157/my-midnight-battle-with-a-curl-command-ac6b22942f01
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-xrg4-qp5w-2c3w
CVE-2025-48387
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-v2c8-vqqp-hv3g
buherator
buheratorhttps://threadreaderapp.com/thread/1956498902443827574.html
LaurieWired
lauriewired@bird.makeuplp0 is a Linux error code that means “printer on fire.”
It’s not a joke. In the 50s, computerized printing was an experimental field.
At LLNL (yes, the nuclear testing site), cathode ray tubes created a xerographic printer.
...it would occasionally catch fire.
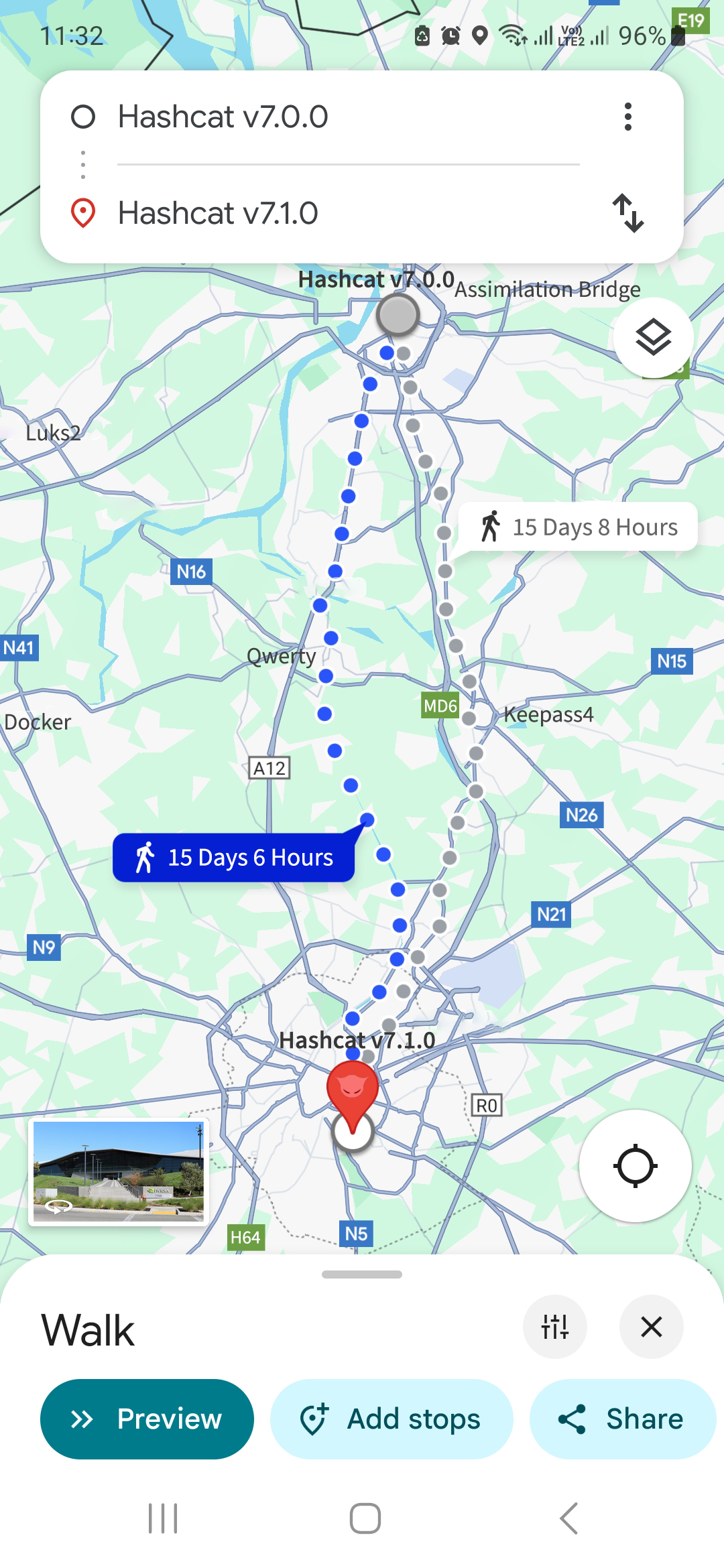
hashcat
hashcat@infosec.exchangehashcat v7.1.0 released!
This update includes important bug fixes, new features, and support for new hash-modes, including KeePass with Argon2.
Read the full write-up here: https://hashcat.net/forum/thread-13353.html
MostlyHarmless
MostlyHarmless@thecanadian.socialA sad day indeed - the original Rick Roll video has finally been taken down from YouTube from a copyright claim.
https://www.youtube.com/watch?v=dQw4w9WgXcQ
buherator
buheratorhttps://scrapco.de/dataslate/phrack/
(Will probably update when 72 comes out)
hackaday
hackaday@hackaday.socialLiberating a Collapsible Chair from a Single Piece of Wood
https://hackaday.com/2025/08/15/liberating-a-collapsible-chair-from-a-single-piece-of-wood/
faker
faker@infosec.exchangeI wish watchTwr Labs was on mastodon, their blog posts are always amazing.
Today's about a Fortinet vulnerability:
https://labs.watchtowr.com/should-security-solutions-be-secure-maybe-were-all-wrong-fortinet-fortisiem-pre-auth-command-injection-cve-2025-25256/
Viss
Viss@mastodon.socialsquirrels always act and look like its their first day being a squirrel
finally got around to writing up my windows exploit from pwn2own vancouver 2024! (plus some notes about using it on xbox) https://exploits.forsale/pwn2own-2024/
sorahed
kvashadow@bird.makeupFollowing the method demonstrated by @yarden_shafir in "Your Mitigations Are My Opportunities", this implementation automates adding a driver to the HvciDisallowedImages registry entry, ensuring it will be blocked from loading after the next reboot.
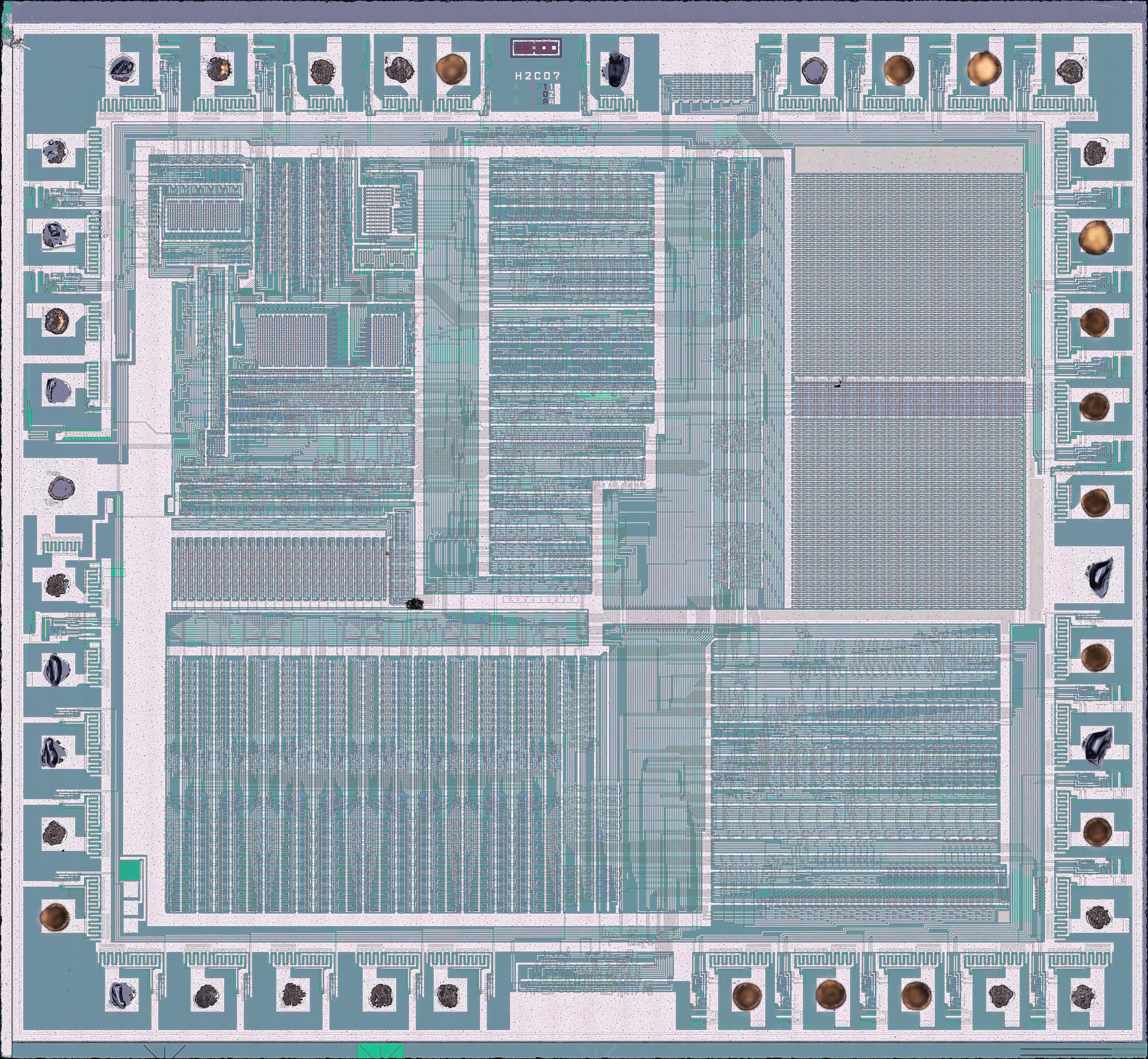
Yo all, it is Friday now where I am, so might as well get the #nakeddiefriday thing going.
Today's guest is the famous NES PPU chip, RP2C07A by Ricoh. What's interesting about this particular sample is that it's very very dead. Many thanks to @root42 for supplying it!
As always, a short thread follows. Why not give this one a boost while you're here? :D
SiPron page for those hi-res maps we all love: https://siliconpr0n.org/archive/doku.php?id=infosecdj:ricoh:rp2c07a
Note the die is oriented the same way Visual 2C02 has it: https://www.nesdev.org/wiki/Visual_2C02
Addison
addison@nothing-ever.worksNew rant about fuzzing just dropped: https://addisoncrump.info/research/consideration-of-input-shapes/