Posts
3373Following
712Followers
1579Trail of Bits
trailofbits@infosec.exchange🥈 We won second place in DARPA's AI Cyber Challenge with Buttercup!
After competing against 7 top teams to build autonomous AI systems, we're excited to announce that Buttercup, our Cyber Reasoning System that automatically discovers and patches vulnerabilities, is now open source.
Learn more about Buttercup: https://blog.trailofbits.com/2025/08/08/buttercup-is-now-open-source/
XKCD Bot
xkcd@mastodon.xyzShow content
You say no human would reply to a forum thread about Tom Bombadil by writing and editing hundreds of words of text, complete with formatting, fancy punctuation, and two separate uses of the word 'delve'. Unfortunately for both of us, you are wrong.
https://xkcd.com/3126/
3 or 4 decades of InfoSec and this kind of crap still going on :P
"The Linux kernel contributes to this issue by exposing esoteric features through the same syscalls as commonly-used core kernel functionality."
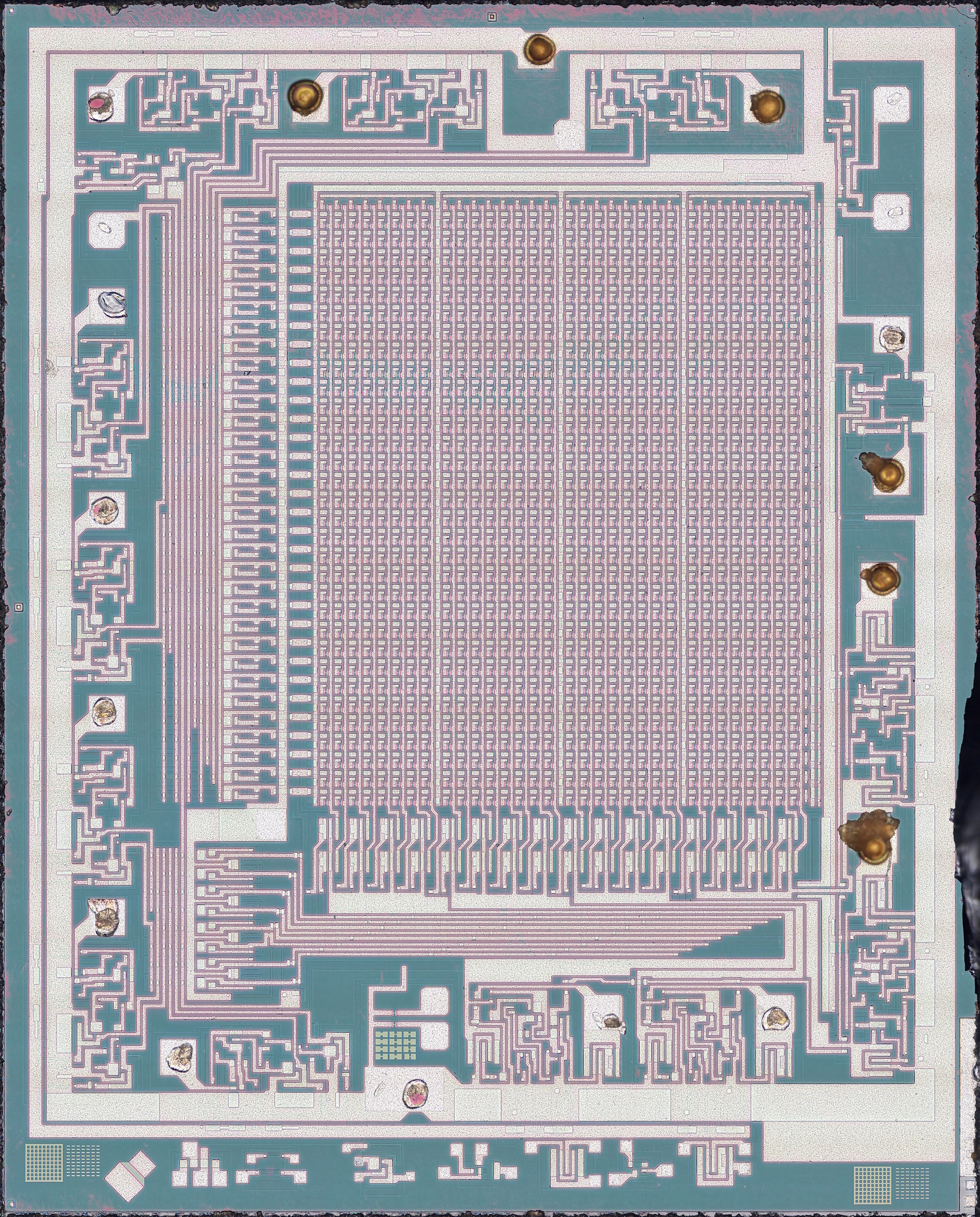
Hello and welcome to this installment of #nakeddiefriday! Today's guest of honour is one КР556РТ4, a Soviet clone of 82S126 the 256x4 TTL PROM.
A very short thread.
SiPron page: https://siliconpr0n.org/archive/doku.php?id=infosecdj:gamma:kr556rt4
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a29a8e4
sqlite3WhereCodeOneLoopStart
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a29a8e4.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a29a8e4.json&colors=light
daniel:// stenberg://
bagder@mastodon.socialI nominate https://docs.openssl.org/3.3/man3/d2i_X509/ as #OpenSSL's worst man page. And there's fierce competition for that award.
And in the end it does not even mention the weird behavior: it stores errors in an internal queue which mysteriously makes the *next* invoked function fail...
Jann Horn
jann@infosec.exchangeI found a Linux kernel security bug (in AF_UNIX) and decided to write a kernel exploit for it that can go straight from "attacker can run arbitrary native code in a seccomp-sandboxed Chrome renderer" to kernel compromise:
https://googleprojectzero.blogspot.com/2025/08/from-chrome-renderer-code-exec-to-kernel.html
This post includes fun things like:
- a nice semi-arbitrary read primitive combined with an annoying write primitive
- slowing down usercopy without FUSE or userfaultfd
CONFIG_RANDOMIZE_KSTACK_OFFSETas an exploitation aid- a rarely-used kernel feature that Chrome doesn't need but is reachable in the Chrome sandbox
sched_getcpu()usable inside Chrome renderers despitegetcpubeing blocked by seccomp (thanks to vDSO)
buherator
buheratorhttps://www.upwind.io/feed/cve-2024-12718-path-escape-via-pythons-tarfile-extraction-filters
buherator
buheratorhttps://bughunters.google.com/blog/6551590643040256/new-patch-rewards-program-for-osv-scalibr
buherator
buheratorCVE-2024-44308 writeup by Exodus Intelligence
https://blog.exodusintel.com/2025/08/04/oops-safari-i-think-you-spilled-something/
Talos Vulnerability Reports
talosvulnsPDF-XChange Editor EMF File EMR_EXTCREATEFONTINDIRECTW Facename Out-Of-Bounds Read Vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2203
CVE-2025-47152
Talos Vulnerability Reports
talosvulnsPDF-XChange Editor EMF File EMR_POLYDRAW16 PT_BEZIERTO Out-Of-Bounds Read Vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2171
CVE-2025-27931
Project Zero Bot
p0botLinux >=6.9: broken AF_UNIX MSG_OOB handling causes UAF read+write
https://project-zero.issues.chromium.org/issues/423023990
CVE-2025-38236
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-81-safari-spills-sonicwall-overflows-pixel-8-kgdb-and-more/
wyatt
wyatt@soc.megatokyo.moeWANTED: Intel Architecture Labs 1990’s CD-ROM’s. They appear to have maybe been monthly. They contained a mirror of Intel’s ‘download.intel.com’ ftp server, specifically the /ial/ subdirectory which is not in the 2014 backup of the site on archive.org.
Lots and lots of white papers and design guideline documents in there. Especially looking for ones from the late 1990’s (1998-ish onward) if they exist. I’ve seen references in mailing lists to them that lead me to believe they do.
Example gem: intel trying to cover its ass after the FDIV bug, and have some more FDIV
cpresser
cccpresser@chaos.socialI need help car jacking my own car. Left the keys inside :(
Can someone help me with that? Either with lockpicking tools or those inflatable cushions?
Its an old car, no fancy stuff.
Please #why2025 do your magic.
Edit: ANWB fixed it.
Justine Tunney
justinetunney@bird.makeup1/ The most powerful hacker in the world right now is femboy·cat who is able to control 5% of Internet hosts, making them the all-time champion of the IPv4 Games.
Rust Language
rust@social.rust-lang.orgHappy new Rust! 🎆🦀
Rust 1.89.0 has been released!
This release brings you inferred args to const generics (e.g. array length: `[false; _]`), the new mismatched_lifetime_syntaxes lint, u128/i128 in extern "C", NonZero<char>, File::{lock,unlock,etc.}, many x86 intrinsics, and much more! ✨
Check out the blog post and release notes for all the details: https://blog.rust-lang.org/2025/08/07/Rust-1.89.0/
Nspace
nspace@infosec.exchangeOur newest blog post about exploiting Retbleed, a bug in AMD CPUs, in the real world is out! Enjoy!
https://bughunters.google.com/blog/6243730100977664/exploiting-retbleed-in-the-real-world