Posts
3373Following
712Followers
1579SensePost
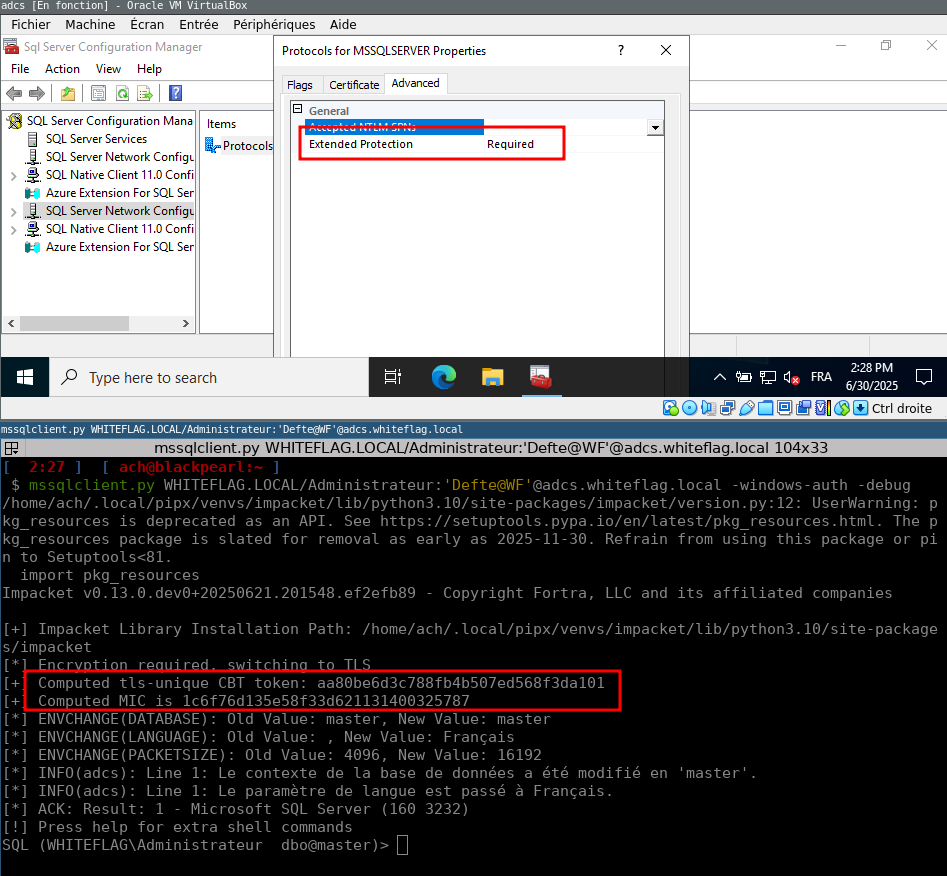
sensepost@infosec.exchangeReverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (@defte_), including instructions for reproducing the test environment yourself.
https://sensepost.com/blog/2025/a-journey-implementing-channel-binding-on-mssqlclient.py/
BobDaHacker 🏳️⚧️
bobdahacker@infosec.exchangeFound critical vulns in Lovense (the biggest sex toy company) affecting 11M+ users. They ignored researchers for 2+ years, then fixed in 2 days after public exposure. 🤦
What I found:
- Email disclosure via XMPP (username→email)
- Auth bypass (email→account takeover, no password)
History of ignoring researchers:
- 2017: First recorded case of someone reporting XMPP email leak.
- 2022: Someone else reports XMPP email leak, ignored
- Sept 2023: Krissy reports account takeover + different email leak via HTTP API, paid only $350
- 2024: Another person reports XMPP email leak AND Account Takeover vuln, offered 2 free sex toys (accepted for the meme)
- March 2025: I report account takeover + XMPP email leak, paid $3000 (after pushing for critical)
- Told me fix for email vuln needs 14 months because "legacy support" > user security (had 1-month fix ready)
- July 28: I go public
- July 30: Both fixed in 48 hours
Same bugs, different treatment. They lied to journalists saying it was fixed in June, tried to get me banned from HackerOne after giving permission to disclose.
News covered it but my blog has the full technical details:
https://bobdahacker.com/blog/lovense-still-leaking-user-emails/
#InfoSec #BugBounty #ResponsibleDisclosure #Security #Vulnerability #IoT #cybersecurity
stacksmashing
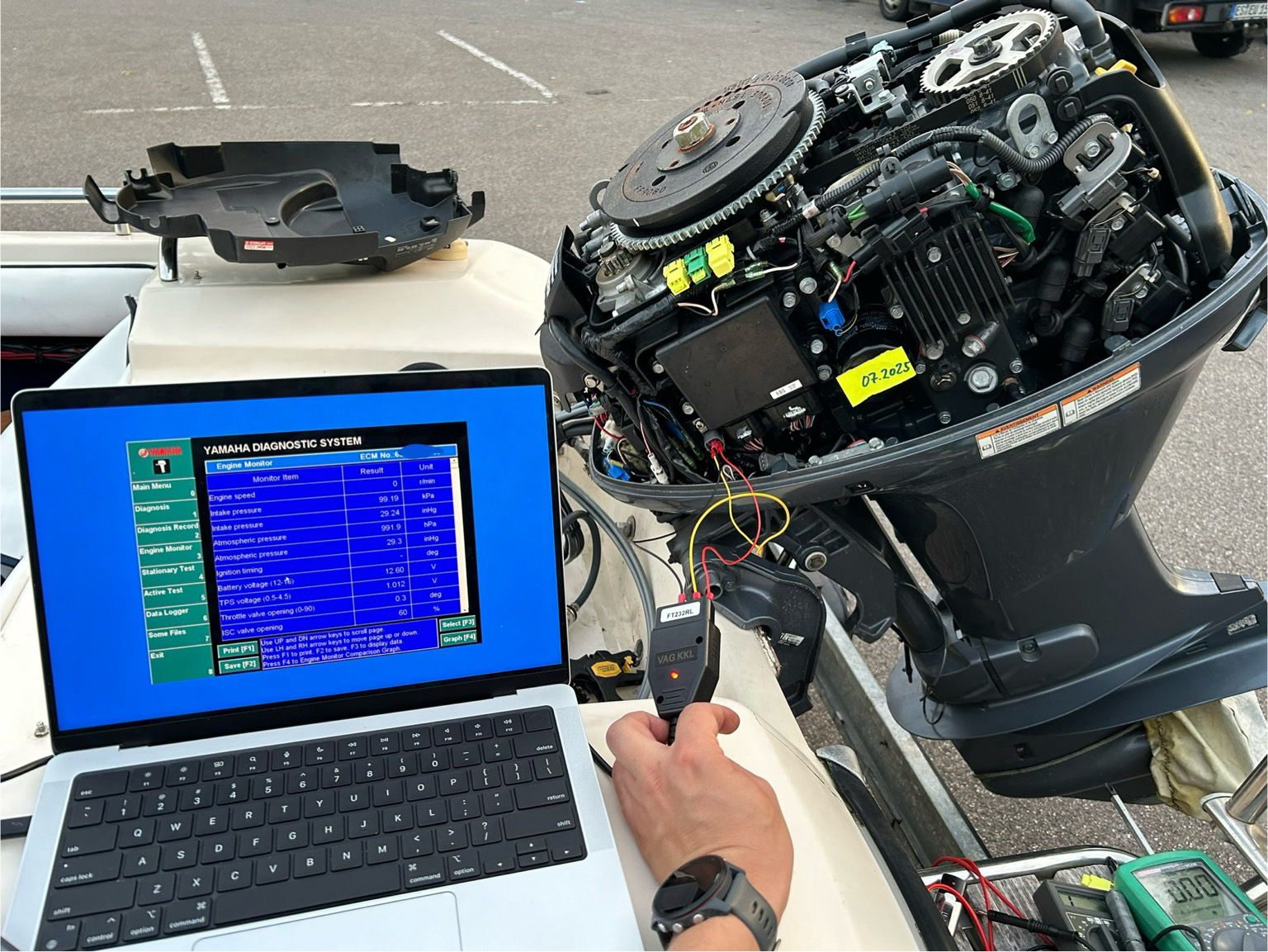
stacksmashing@infosec.exchangeWhy do so many aspects of my life involve connecting FT232s to random pins 😂
Phrack
phrack@haunted.computerHeya @why2025camp! You got 2250 copies of Phrack Magazine coming your way!!
K. Reid Wightman  🌻
🌻 

reverseics@infosec.exchange
I want to gush about the dumbest thing for a minute.
I subscribe to @molly0xfff 's newsletter thing. And while the news often is a bit concerning, the format is A++++ perfection.
The newsletter comes to my inbox in its entirety. There are references and links, and NONE OF THEM ARE TRACKING LINKS. (well okay, there are two links that are technically trackers, they are the 'more like this' and 'less like this'...it's hard to make some kind of newsletter customization without knowing who clicked the link). But all the rest of the links are just plain links. To plain URLs. Like what we used to have back in the '90s. Remember those halcyon days when readers weren't the product?
I read the whole newsletter every time one comes out, in part because I don't have to 'click here to read more'.
I'm sure it's a little concerning to run a publication this way in the modern era ("are people even reading this?" is probably a real concern. Well hey, at least I do...).
Anyway, if you're able to support her, I do recommend it. Well researched news, worth every penny for the ad-free experience.
Royce Williams
tychotithonus@infosec.exchangeOh look, another "door locks are bad because someone can crawl through the window" scare article (this time a sponsored one). Not responsible journalism, Bleeping.
I especially "appreciate" the scare quotes around "phishing-resistant" 🤬
Phrack
phrack@haunted.computerAre you going to @defcon ??
We'll have 9500 print copies of Phrack distributed around the con! Come to main stage Sunday @ noon to see phrack staffers @netspooky @richinseattle and @chompie1337 talk hacker history!
Natalie Silvanovich
natashenka@infosec.exchangeWhile most vendors ship timely patches for vulnerabilities reported by Project Zero, they don’t always reach users. Today, we’re announcing Reporting Transparency, a new policy to encourage downstream fixes
https://googleprojectzero.blogspot.com/2025/07/reporting-transparency.html
CHERI Alliance
cheri_alliance@infosec.exchangeThe CHERI Alliance has released an experimental prototype of CHERI support in seL4 and Microkit, accompanied by tutorials to help you get started. This release is now available for you to reproduce, explore, and build upon.
For those who are unfamiliar with CHERI, CHERI support in seL4 enables memory-safe C/C++ user-level projects and applications without having to (re)write code in languages like Rust. This complement's seL4's strong isolation between different components, enforced by the MMU and seL4's software capabilities.
We welcome your feedback and contributions.
Learn more: https://cheri-alliance.org/cheri-sel4-and-cheri-microkit-released/
buherator
buheratorhttps://slcyber.io/assetnote-security-research-center/struts-devmode-in-2025-critical-pre-auth-vulnerabilities-in-adobe-experience-manager-forms/
danzin
danzin@mastodon.socialOne obvious thing from fuzzing the CPython JIT with the lafleur fuzzer is that finding crashes is much lower probability than fuzzing CPython with fusil.
Whenever fusil found a crash, it would find hits for it again and again pretty quickly.
With lafleur, we only got 3 hits (2 issues) in thousands of fuzzing hours.
I'm throwing more compute at it, but maybe we'll need to improve the core ideas to get better results.
daniel:// stenberg://
bagder@mastodon.socialThe opposite of AI slop reports is a detailed, well written and qualified report that takes many hours of mind-wrestling until we know what to do about it.
Like this: https://hackerone.com/reports/3261310
buherator
buheratorhttps://labs.watchtowr.com/stack-overflows-heap-overflows-and-existential-dread-sonicwall-sma100-cve-2025-40596-cve-2025-40597-and-cve-2025-40598/
buherator
buheratorhttps://talosintelligence.com/vulnerability_reports/TALOS-2025-2177
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2176
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2156
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2154
CVE-2025-24485 CVE-2025-27724 CVE-2025-32731 CVE-2025-26469
Project Zero Bot
p0botLinux: hugetlb page table sharing races with VMA splitting, leading to page table UAF
https://project-zero.issues.chromium.org/issues/420715744
CVE-2025-38084, CVE-2025-38085
daniel:// stenberg://
bagder@mastodon.social"we observe that in most ecosystems, the average vulnerability lifespan has increased in recent years. The average lifespan of vulnerabilities across all platforms has grown from 1,056 days to 1,956 days - an increase of approximately 85%." (from 2017 to 2024)
🦊 helloyanis 
helloyanis@furries.club
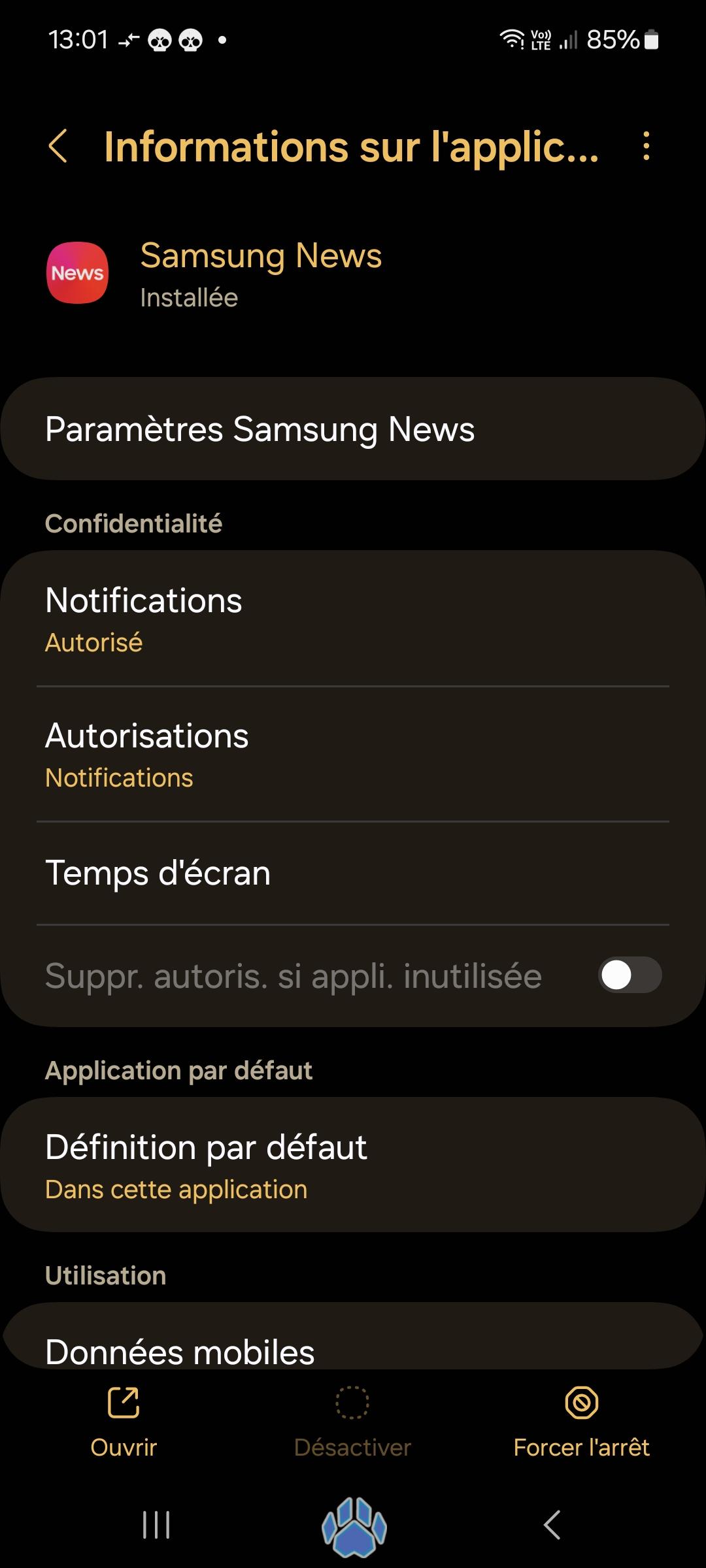
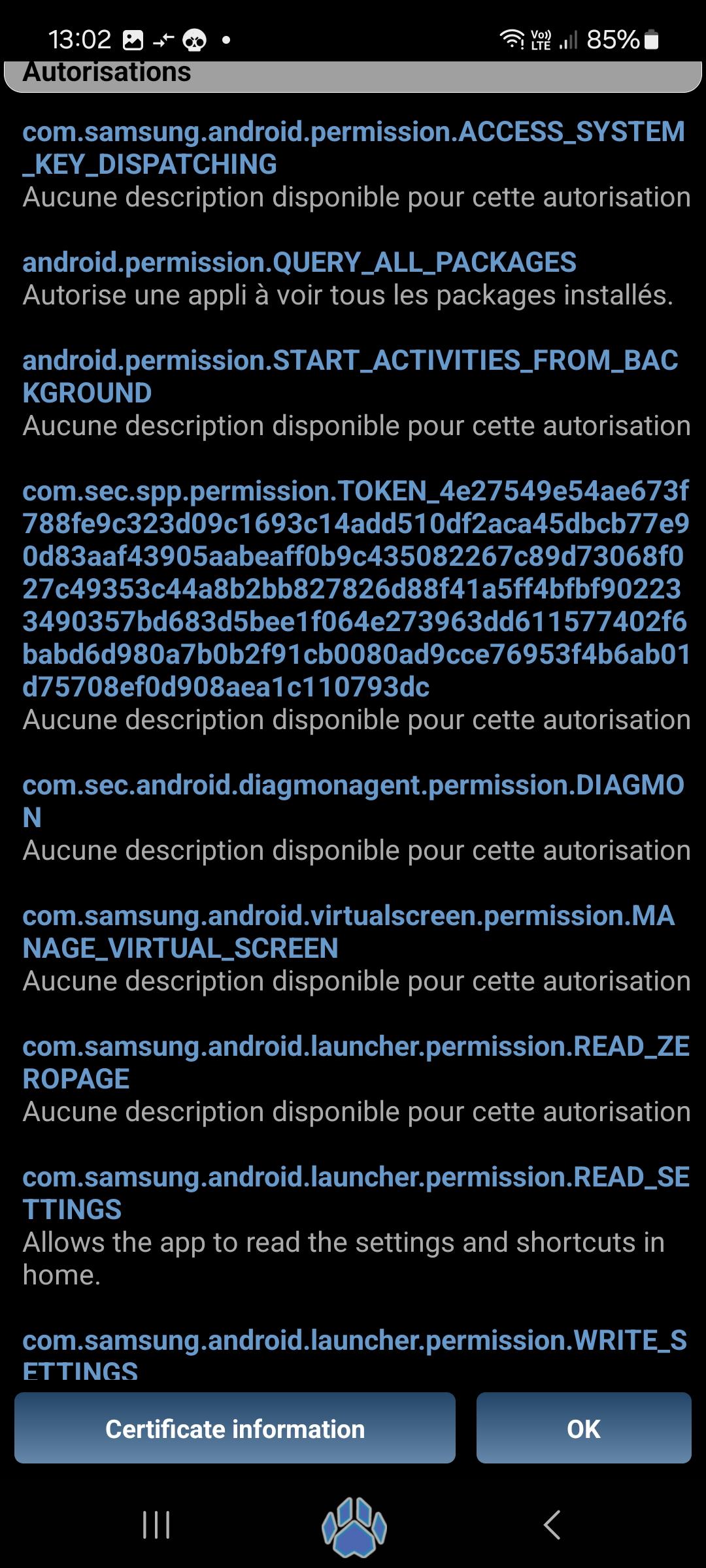
I found this great samsung spyware (I assume), I present to you : Samsung news!!
https://galaxystore.samsung.com/detail/com.samsung.android.app.spage?cId=000006738177
For an app that's just supposed to tell you the news :
- It comes bundled with the phone
- It auto connects you to your samsung account
- You can't uninstall it, or even disable it (usually only critical system apps that break your phone if disabled do this)
- In the app info the only permission it shows is notification
- However looking at the app package's info shows it also has permissions to see all installed apps, read and edit settings, run on phone startup and start stuff in the background
- Uninstalled it with root, my phone works flawlessly
Well, that's just 1 app I took a look at. There can be many more simillar ones! I really should install a custom OS
@soatok @xanthe @sebsauvage
#privacy #android #samsung
Programming Quotes
programming_quotes@mastodon.socialTo me programming is more than an important practical art. It is also a gigantic undertaking in the foundations of knowledge.
— Grace Hopper
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange💻Have you read our recent publication?
A critical double-free vulnerability has been discovered in the pipapo set module of the Linux kernel’s NFT subsystem. An unprivileged attacker can exploit this vulnerability by sending a specially crafted netlink message, triggering a double-free error with high stability. This can then be leveraged to achieve local privilege escalation: https://ssd-disclosure.com/ssd-advisory-linux-kernel-pipapo-set-double-free-lpe/