Posts
2504Following
650Followers
1469buherator
buheratorhttps://www.hoyahaxa.com/2025/06/sandbox-security-escapes-in-coldfusion.html
/r/netsec
_r_netsec@infosec.exchangeSecurity Benchmarking Authorization Policy Engines https://goteleport.com/blog/benchmarking-policy-languages/
buherator
buheratorhttps://www.youtube.com/watch?v=YAue1QljRg4
Hex-Rays SA
HexRaysSA@infosec.exchange👉🏽 Check out this in-depth video of @nmatt0 reversing the firmware decryption mechanism used in a Hanwha security camera with IDA Pro. Bonus: He's also written an accompanying blog post packed with code samples, screenshots, and more!
https://hex-rays.com/blog/reversing-hanwha-security-cameras-a-deep-dive-by-matt-brown
Jeff Atwood
codinghorror@infosec.exchangeThis is very aggressively (perhaps too aggressively) stated, but he's absolutely right. People are all worried their ideas are gonna be "stolen", and my friends, I can assure you that won't be the problem.
Rebane
rebane2001@infosec.exchangei love css 💖
also shoutout to Fastmail for rolling out fixes for both reports in <48h
https://www.fastmail.com/bug-bounty/
buherator
buheratorhttps://www.ibm.com/support/pages/node/7237732
Another one by @silentsignal !
buherator
buheratorhttps://ssd-disclosure.com/ssd-advisory-kerio-control-authentication-bypass-and-rce/
buherator
buheratorhttps://www.downtowndougbrown.com/2025/06/finding-a-27-year-old-easter-egg-in-the-power-mac-g3-rom/
buherator
buheratorhttps://www.hoyahaxa.com/2025/06/cfcamp-2025-slides-understanding-cfml.html
#coldfusion
buherator
buheratorhttps://scrapco.de/ghidra_docs/
Here's the documentation for Decompiler Taint Operations:
https://scrapco.de/ghidra_docs/Features/DecompilerDependent/DecompilerTaint/DecompilerTaint.html
buherator
buheratorhttps://github.com/NationalSecurityAgency/ghidra/releases/tag/Ghidra_11.4_build
TROOPERS Conference
WEareTROOPERS@infosec.exchange📢 @ERNW is preparing the venue for tomorrow's launch of #TROOPERS25 in #heidelberg! See you soon people! We are super excited! 🥳
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250624-00/?p=111299
#warez
Rebane
rebane2001@infosec.exchangeyay my first 2025 chrome cve!!
https://chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop_24.html
シャポコ🌵
shapoco@misskey.ioVSCode のターミナルも Sixel 対応してたのか (terminal.integrated.experimentalImageSupport を有効にすると表示される)
poptart
yeslikethefood@infosec.exchange"We will respond to you in 5 days"
3 weeks later... No response.
Anyone who gets mad at people for going full disclosure has never had to deal with the bureaucratic maze of trying to get people to fix their things.
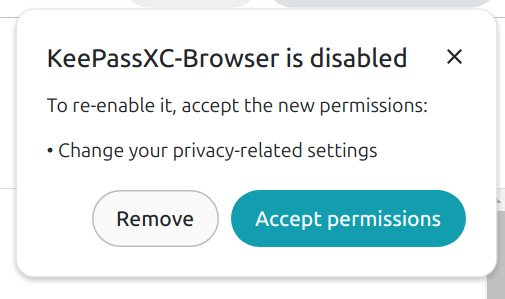
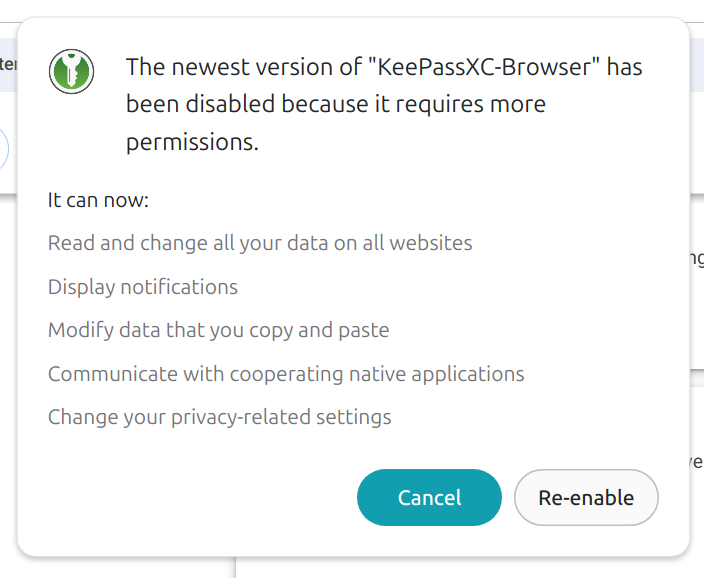
Team KeePassXC
keepassxc@fosstodon.orgPSA: The new version of our browser extension now requires additional permissions to "change your privacy-related settings".
The new permissions are required so we can set KeePassXC as your default password manager backend. Unfortunately, there isn't a better name for this permission set.
/r/netsec
_r_netsec@infosec.exchangeRemote code execution in CentOS Web Panel - CVE-2025-48703 https://fenrisk.com/rce-centos-webpanel