Posts
3368Following
712Followers
1580danzin
danzin@mastodon.socialSo, my technical report on fuzzing CPython with fusil is almost done.
I'd really appreciate some help categorizing the found issues by relevance/severity/importance or any other name for impact.
Do you have the chops to help with that? And do you have time and interest? Please get in touch if so! And please boost if you can :)
A plot, some tables, links to the report and some discussion are available in this thread:
https://discuss.python.org/t/feedback-on-the-recent-fusil-fuzzing-campaign-of-cpython/91737
buherator
buheratorhttps://scrapco.de/blog/visualizing-prefetch-infoleaks-to-defeat-kaslr.html
buherator
buheratorhttps://blog.scrt.ch/2025/06/04/sonicdoor-attacking-sonicwalls-sma-500/
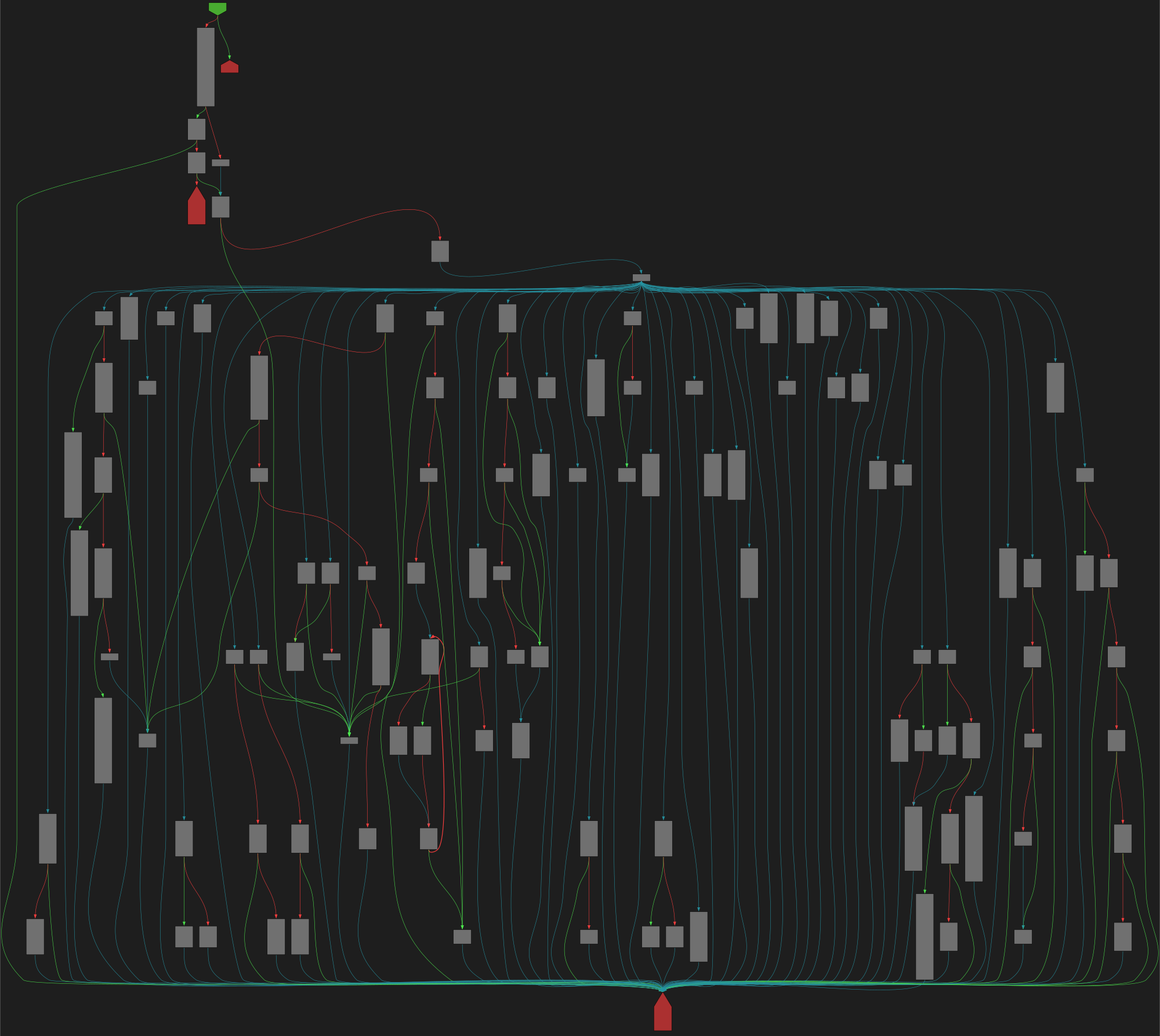
CFG Bot 🤖
cfgbot@mastodon.socialProject: microsoft/typescript https://github.com/microsoft/typescript
File: src/compiler/program.ts:3242 https://github.com/microsoft/typescript/blob/81c951894e93bdc37c6916f18adcd80de76679bc/src/compiler/program.ts#L3242
function checkModifiers(modifiers: NodeArray<ModifierLike>, isConstValid: boolean)
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2Ftypescript%2Fblob%2F81c951894e93bdc37c6916f18adcd80de76679bc%2Fsrc%2Fcompiler%2Fprogram.ts%23L3242&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2Ftypescript%2Fblob%2F81c951894e93bdc37c6916f18adcd80de76679bc%2Fsrc%2Fcompiler%2Fprogram.ts%23L3242&colors=light
FreddyB Aviation Photography
cvvhrn@sfba.socialUSMC AH-1Z Viper working the pattern at Pt. Mugu, July 2024 #USMC #choppa #rotor #Mugu #AH1Z #aviationphotography #planespotting #AvGeek #spotter #photography #Nikon #aircraft #nikonphotography
buherator
buheratorhttps://starlabs.sg/blog/2025/06-solo-a-pixel-6-pro-story-when-one-bug-is-all-you-need/
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-74/
kajer :notverified:
kajer@infosec.exchangeFucking stupid UI/UX choices.
Fortigate Firewall/Routers - All options for BGP/IPSEC are behind an "advanced options" user preference.... IT'S A FORTIFUCKINGROUTER the only people in this interface are advanced users.
PaloAlto XDR portal - Right-click for options on a line... fine... But wait, if you hold option/alt, you get even more options. I get the need to define which options are less common choices, but you should not be hiding things behind click-modifiers. The only people using the XDR interface will be advanced users. If a user doesn't have authorization for a command, then don't show it. If the option is destructive, then confirm with N number of dialogs. Also, the ENTIRE user interface is in italics.
Admin interfaces should never have hidden options.
Phrack Zine
phrack@bird.makeupThere’s still time for you to submit your article for the 40th anniversary edition of Phrack!
Jonty Wareing
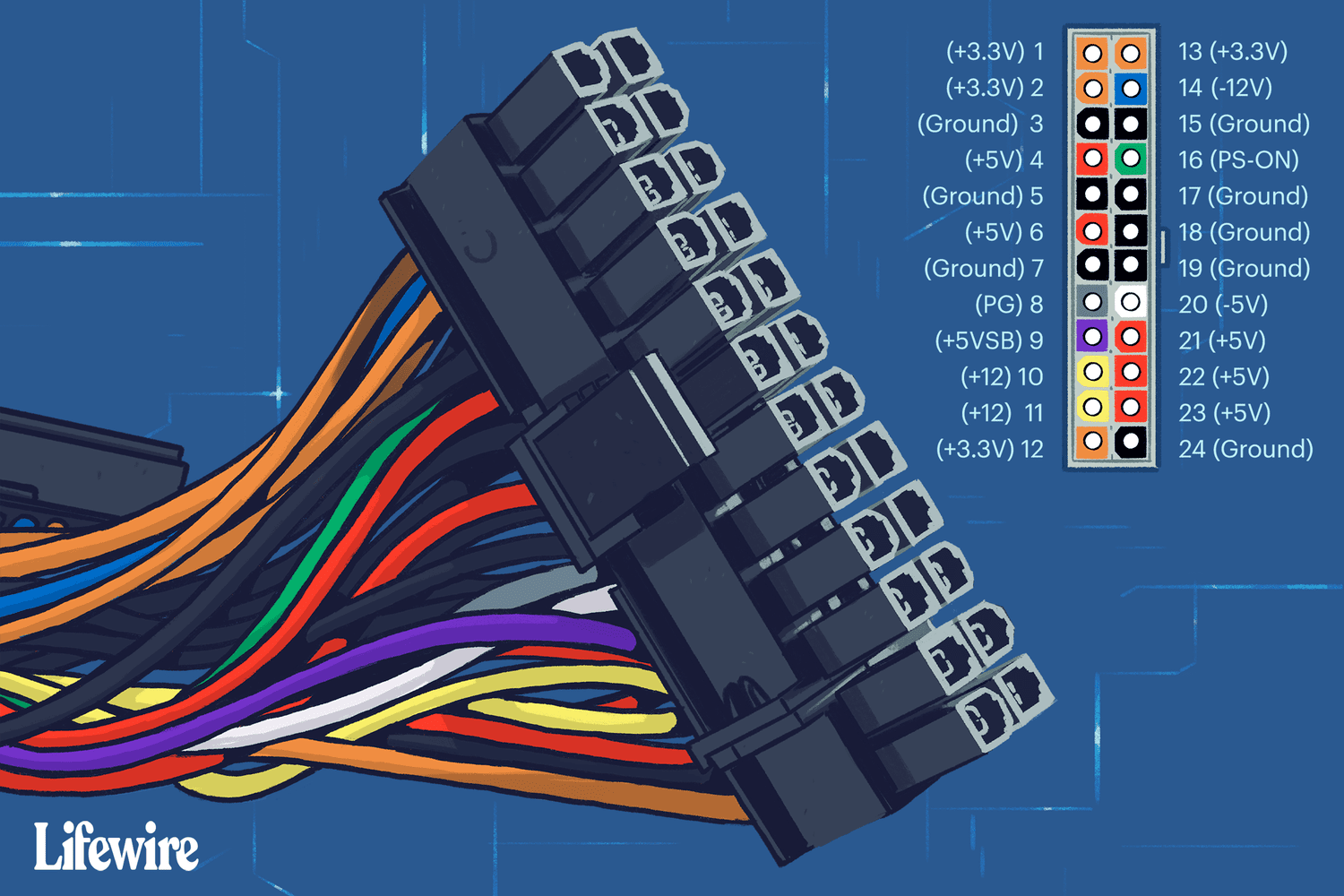
jonty@chaos.socialWhat is the most inappropriate connector with enough pins to support USB-C?
I suggest:
buherator
buheratorhttps://kaist-hacking.github.io/publication/yun-ksa/
eShard
eshard@infosec.exchangeOur journey with our #iOS emulator continues.
We show how we reached the home screen, enabled multitouch, unlocked network access, and started running real apps 👉 https://eshard.com/posts/emulating-ios-14-with-qemu-part2
Command injection, SQLi, and hardcoded creds in Infoblox NETMRI. tsk tsk
https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32814
https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32813
https://support.infoblox.com/s/article/Infoblox-NetMRI-is-vulnerable-to-CVE-2025-32815
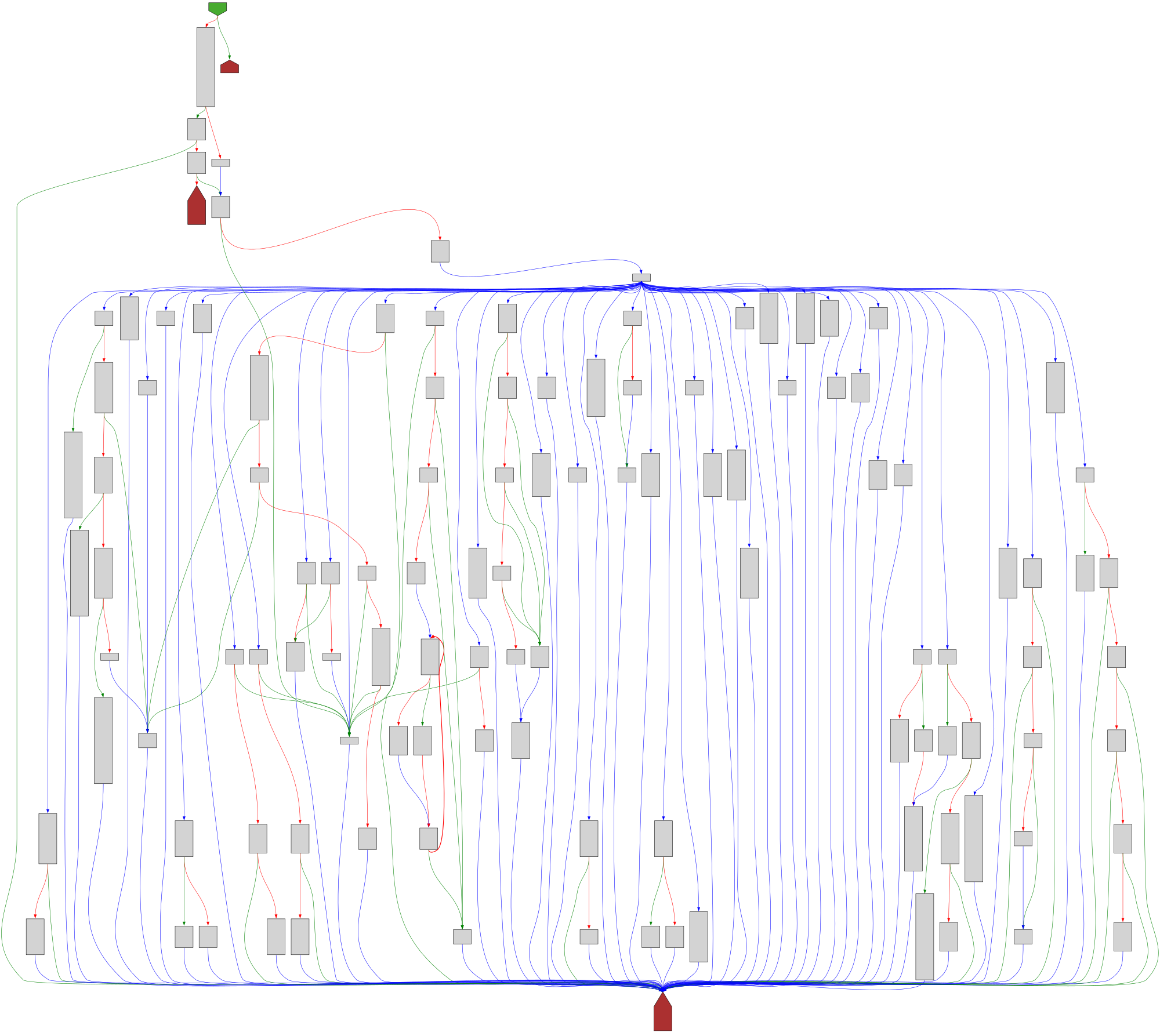
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00478ea0
ssl3_ctrl
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00478ea0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00478ea0.json&colors=light
The DFIR Report
TheDFIRReport@infosec.exchange🎯 THIS SATURDAY: DFIR Labs CTF 🎯
⏰ June 7 | 1630–2030 UTC
🔗 Register Now → https://dfirlabs.thedfirreport.com/ctf
🚀 DFIR Labs CTF is back!
💥 Only $9.99 to join
💥 Choose Elastic or Splunk
💥 Access a brand-new, unreleased case
💥 Top 5 get invited to join The DFIR Report team!
📣 Hear from past participants:
⭐ “Real case makes it different!”
🚀 “Great hands-on learning experience”
💯 “Excellent CTF, super responsive and realistic”
Don’t miss your chance to level up with real-world incident response challenges.
buherator
buheratorhttps://telex.hu/techtud/2025/06/03/hekkertamadas-paprika-csoport-erettsegi-adatbazis-masolas-oktatasi-hivatal
Wonder if perpetrators are in fact Hungarian (as the name suggests), or just using some LLM translator?
Alexandre Borges
alexandreborges@infosec.exchangeCisco IOS XE WLC Arbitrary File Upload Vulnerability (CVE-2025-20188) Analysis:
#cybersecurity #xxe #infosec #cve #vulnerability #threathunting #exploitation