Posts
3370Following
712Followers
1579Bart Groothuis
bartgroothuis@mastodon.onlineGermany’s largest telecommunication provider Deutsche Telekom is owned by Chinese hackers. And its managed IT service subsidiaries are too. No media reporting on it yet. Deutsche Telekom (addicted to cheap Huawei equipment) chose not to go public. Wake up! https://blog.eclecticiq.com/china-nexus-threat-actor-actively-exploiting-ivanti-endpoint-manager-mobile-cve-2025-4428-vulnerability
Attila Szasz
4ttil4sz1a@bird.makeupCVE-2025-0927 details here!
https://ssd-disclosure.com/ssd-advisory-linux-kernel-hfsplus-slab-out-of-bounds-write/
daniel:// stenberg://
bagder@mastodon.socialI talked AI slop with @joshbressers on Open Source Security:
https://opensourcesecurity.io/2025/2025-05-curl_vs_ai_with_daniel_stenberg/
Dan Luu
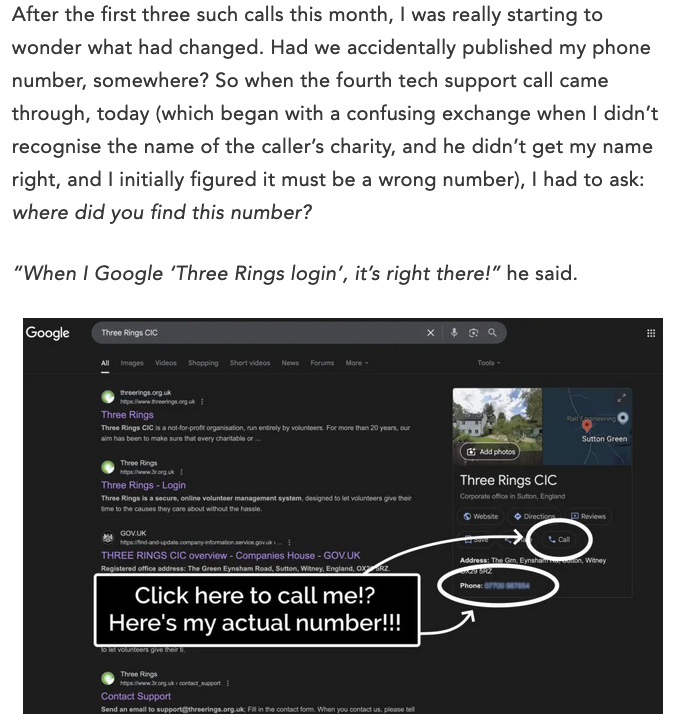
danluu@mastodon.socialInteresting story about Google publishing someone's phone number on searches for them when they gave the number to Google for account verification/security:
https://danq.me/2025/05/21/google-shared-my-phone-number/
Reminds me of the time a company I worked for (AFAIK) accidentally used phone numbers obtained the same way for ad targeting and got fined $150M
buherator
buheratorhttps://u1f383.github.io/linux/2025/05/25/dbus-and-polkit-introduction.html
With analysis of CVE-2025-23222 and CVE-2021-3560
buherator
buheratorhttps://horizon3.ai/attack-research/attack-blogs/cve-2025-32756-low-rise-jeans-are-back-and-so-are-buffer-overflows/
Graham Sutherland / Polynomial
gsuberland@chaos.socialMateusz Jurczyk from GP0 has been been writing a blog series on the implementation details of the Windows Registry, and there's a truly monumental amount of work on show here.
this one post alone is 24,000 words long, and covers a huge range of security issues discovered across the registry attack surface.
practically mandatory reading if you're doing Windows appsec assessments. really incredible stuff.
https://googleprojectzero.blogspot.com/2025/05/the-windows-registry-adventure-7-attack-surface.html
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Sad times, John Young of Cryptome is no longer with us:
buherator
buheratorhttps://www.incendium.rocks/posts/Automating-MS-RPC-Vulnerability-Research/
buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/05/the-windows-registry-adventure-7-attack-surface.html
buherator
buheratorhttps://github.blog/security/vulnerability-research/bypassing-mte-with-cve-2025-0072/
buherator
buheratorhttps://karmainsecurity.com/dont-call-that-protected-method-vbulletin-rce
buherator
buheratorhttps://labs.infoguard.ch/posts/attacking_edr_part4_fuzzing_defender_scanning_and_emulation_engine/
Great to see snapshot #fuzzing successfully applied to another AV product!
ZZ9 Plural Z Alpha
zz9official@mastodon.socialHappy #TowelDay hoopy froods everywhere!
We have five winners from our contest, and will be publishing their works on our site soon, along with details of our (members only) June competition, with an Curious King illustrated fine press edition of Hitchhiker's on offer!
Open Source Security mailing list
oss_security@bird.makeupCVE-2025-48708: ghostscript can embed plaintext password in encrypted PDFs https://www.openwall.com/lists/oss-security/2025/05/23/2
the full command-line input, including the plaintext password, is embedded at the beginning of the generated PDF file
why2025camp
why2025camp@chaos.socialHappy towel day! We hope you know where your towel is, as one who still knows where their towel is, is clearly someone to be reckoned with.
And we also hope you know you have less then 24 hours to fill in the WHY2025 CfP!
CFG Bot 🤖
cfgbot@mastodon.socialProject: facebook/react https://github.com/facebook/react
File: compiler/packages/babel-plugin-react-compiler/src/Optimization/OutlineJsx.ts:53 https://github.com/facebook/react/blob/c250b7d980864be49facf2306f06455e7f9e305d/compiler/packages/babel-plugin-react-compiler/src/Optimization/OutlineJsx.ts#L53
function outlineJsxImpl( fn: HIRFunction, outlinedFns: Array<HIRFunction>, ): void
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Ffacebook%2Freact%2Fblob%2Fc250b7d980864be49facf2306f06455e7f9e305d%2Fcompiler%2Fpackages%2Fbabel-plugin-react-compiler%2Fsrc%2FOptimization%2FOutlineJsx.ts%23L53&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Ffacebook%2Freact%2Fblob%2Fc250b7d980864be49facf2306f06455e7f9e305d%2Fcompiler%2Fpackages%2Fbabel-plugin-react-compiler%2Fsrc%2FOptimization%2FOutlineJsx.ts%23L53&colors=light
Alan Coopersmith
alanc@hachyderm.ioToday we've released #OracleSolaris 11.4.81, our quarterly feature update. The announcement is at https://blogs.oracle.com/solaris/post/announcing-oracle-solaris-114-sru81 and lists the new features and software upgrades included.
REverse_Tactics
reverse_tactics@bird.makeupSlides and video of our talk at @offensive_con are already online !
Thanks to @binary_gecko for the amazing event
https://www.reversetactics.com/publications/2025_conf_offensivecon_journeytofreedom/