Posts
3368Following
712Followers
1579buherator
buheratorhttps://www.incendium.rocks/posts/Automating-MS-RPC-Vulnerability-Research/
buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/05/the-windows-registry-adventure-7-attack-surface.html
buherator
buheratorhttps://github.blog/security/vulnerability-research/bypassing-mte-with-cve-2025-0072/
buherator
buheratorhttps://karmainsecurity.com/dont-call-that-protected-method-vbulletin-rce
buherator
buheratorhttps://labs.infoguard.ch/posts/attacking_edr_part4_fuzzing_defender_scanning_and_emulation_engine/
Great to see snapshot #fuzzing successfully applied to another AV product!
ZZ9 Plural Z Alpha
zz9official@mastodon.socialHappy #TowelDay hoopy froods everywhere!
We have five winners from our contest, and will be publishing their works on our site soon, along with details of our (members only) June competition, with an Curious King illustrated fine press edition of Hitchhiker's on offer!
Open Source Security mailing list
oss_security@bird.makeupCVE-2025-48708: ghostscript can embed plaintext password in encrypted PDFs https://www.openwall.com/lists/oss-security/2025/05/23/2
the full command-line input, including the plaintext password, is embedded at the beginning of the generated PDF file
why2025camp
why2025camp@chaos.socialHappy towel day! We hope you know where your towel is, as one who still knows where their towel is, is clearly someone to be reckoned with.
And we also hope you know you have less then 24 hours to fill in the WHY2025 CfP!
CFG Bot 🤖
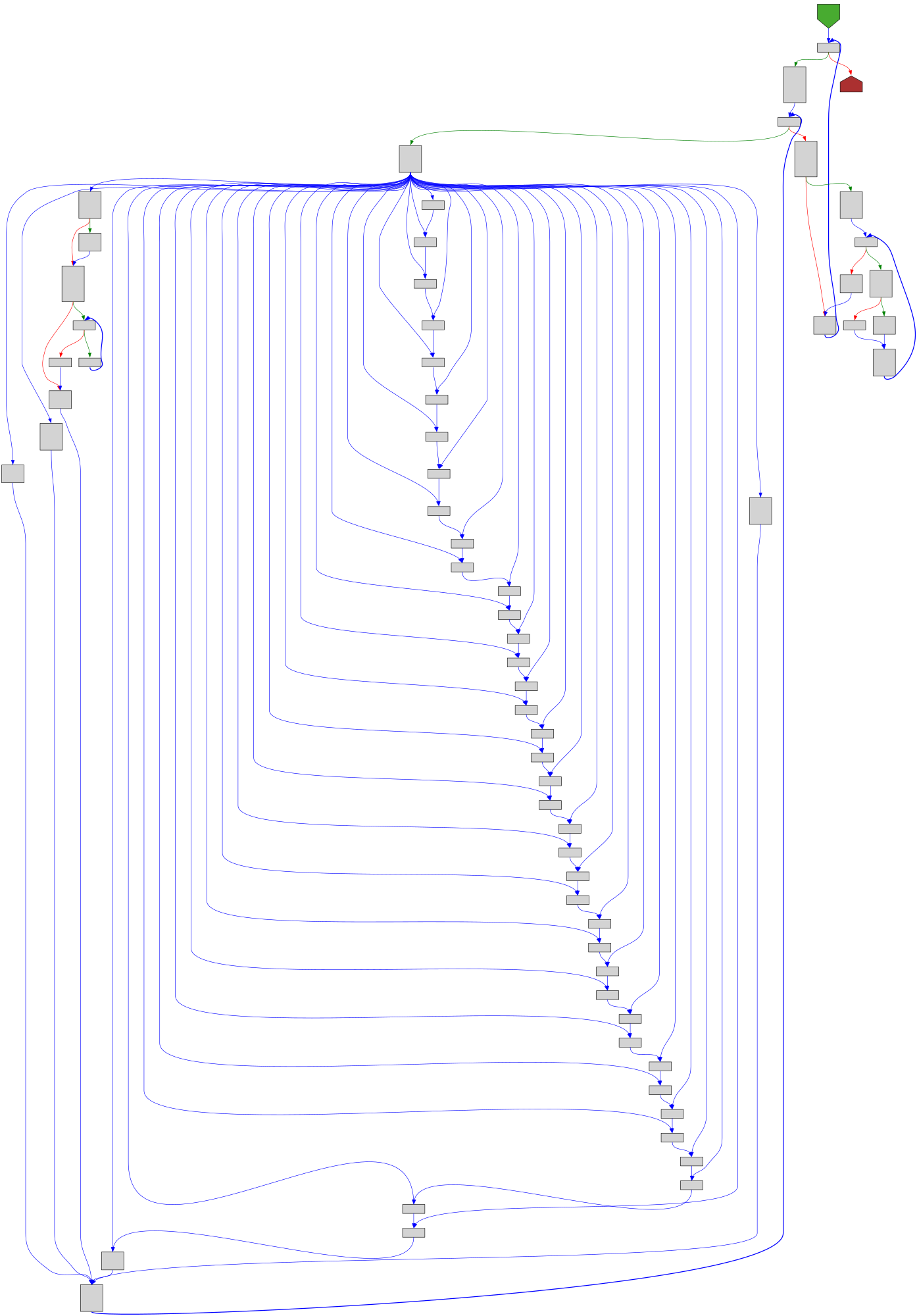
cfgbot@mastodon.socialProject: facebook/react https://github.com/facebook/react
File: compiler/packages/babel-plugin-react-compiler/src/Optimization/OutlineJsx.ts:53 https://github.com/facebook/react/blob/c250b7d980864be49facf2306f06455e7f9e305d/compiler/packages/babel-plugin-react-compiler/src/Optimization/OutlineJsx.ts#L53
function outlineJsxImpl( fn: HIRFunction, outlinedFns: Array<HIRFunction>, ): void
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Ffacebook%2Freact%2Fblob%2Fc250b7d980864be49facf2306f06455e7f9e305d%2Fcompiler%2Fpackages%2Fbabel-plugin-react-compiler%2Fsrc%2FOptimization%2FOutlineJsx.ts%23L53&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Ffacebook%2Freact%2Fblob%2Fc250b7d980864be49facf2306f06455e7f9e305d%2Fcompiler%2Fpackages%2Fbabel-plugin-react-compiler%2Fsrc%2FOptimization%2FOutlineJsx.ts%23L53&colors=light
Alan Coopersmith
alanc@hachyderm.ioToday we've released #OracleSolaris 11.4.81, our quarterly feature update. The announcement is at https://blogs.oracle.com/solaris/post/announcing-oracle-solaris-114-sru81 and lists the new features and software upgrades included.
REverse_Tactics
reverse_tactics@bird.makeupSlides and video of our talk at @offensive_con are already online !
Thanks to @binary_gecko for the amazing event
https://www.reversetactics.com/publications/2025_conf_offensivecon_journeytofreedom/
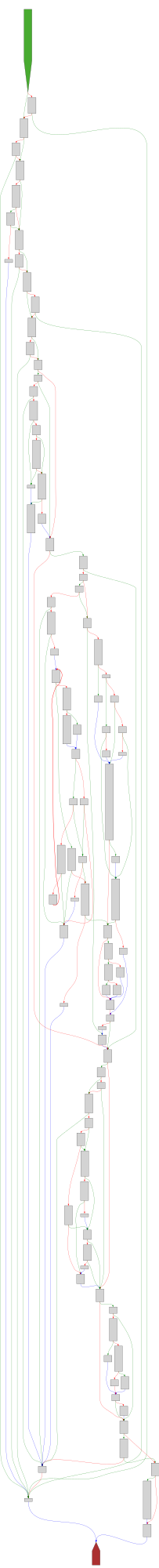
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0064d910
ossl_store_handle_load_result
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0064d910.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0064d910.json&colors=light
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://security.googleblog.com/2025/05/tracking-cost-of-quantum-factori.html - what's over the horizon for PQC
* https://www.gov.uk/government/publications/secure-by-design-problem-book/secure-by-design-problem-book - HMG problem book for Secure By Design
Standards:
* https://www.ncsc.gov.uk/blog-post/new-etsi-standard-protects-ai-systems-from-evolving-cyber-threats - NCSC work on new ETSI standard for AI security
Threats:
* https://ai-incidents.mitre.org/ - MITRE ATLAS' database of AI spillages, leaks and floods
* https://unit42.paloaltonetworks.com/threat-brief-sap-netweaver-cve-2025-31324/ - SAP oopsie turns bad
Detection:
* https://community.emergingthreats.net/t/come-sail-the-cves-part-1-data-acquisition/2750 - @da_667 talks detection engineering
* https://www.magonia.io/wiresnort/ - combining Wireshark and Snort
Bugs:
* https://www.akamai.com/blog/security-research/abusing-dmsa-for-privilege-escalation-in-active-directory - abusing service account delegation for privesc in AD
* https://astr.al/notes/2024-11-28_mdatp_privesc - when you can't even trust $argv[0] and processes called java.. a nice LPE in Defender for Linux
* https://sourceware.org/bugzilla/show_bug.cgi?id=32976 - ... or, it seems $LD_LIBRARY_PATH (what's old is new =))
* https://mastdatabase.co.uk/blog/2025/05/o2-expose-customer-location-call-4g/ - leaky VoLTE and wifi calling
* https://starlabs.sg/blog/2025/05-breaking-out-of-restricted-mode-xss-to-rce-in-visual-studio-code/ - XSS to RCE in VSCode
Exploitation:
* https://go.dev/blog/tob-crypto-audit - @trailofbits took a look at Go Crypto
Hard hacks:
* https://idevicecentral.com/tweaks/idevice-toolkit-ipa-download/ - getting JB like tweaks running on modern iOS
* https://www.sopl.us/blog/consumer-do-it-yourself-guide-to-identifying-your-keys - getting physical with your keys
Development:
* https://docs.oracle.com/cd/E37838_01/html/E61050/gnclc.html - Oracle's guide to secure C for Solaris (thanks @alanc)
* https://allan.reyes.sh/posts/keeping-secrets-out-of-logs/ - on keeping your secrets, well, secret
* https://netascode.cisco.com/ - automate your network
Hardening:
* https://lore.kernel.org/landlock/20250519.ceihohf6a3uT@digikod.net/ - Latest news on Landlock for Linux
* https://www.man7.org/linux/man-pages/man1/systemd-analyze.1.html - analyzing systemd for signs of sense
* https://blog.torproject.org/introducing-oniux-tor-isolation-using-linux-namespaces/ - another option to isolate your onions
Nerd:
* https://linuxexpert.org/from-licenses-to-liberation/ - the story of Linux, through a lens of innovation
* https://www.newscientist.com/article/2480221-chemists-discover-anti-spice-that-could-make-chilli-peppers-less-hot/ - did you know you could also make chillies hotter with salt?
Alec Muffett
alecmuffett@mastodon.socialI think that one of the reasons that I’m not worried about AGI is that I’m still waiting for the end of the world to be caused by Quantum Computing
https://alecmuffett.com/article/113401
#ItsTheEndOfTheWorldAsWeKnowItAndIFeelFine #QuantumComputing #ai2027
Programming Quotes
programming_quotes@mastodon.socialThese days, the problem isn't how to innovate; it's how to get society to adopt the good ideas that already exist.
— Douglas Engelbart
Simon Tatham
simontatham@hachyderm.ioTwo different approaches to debugging a software problem:
The Sudoku approach: stare at the limited set of clues you have, and think harder and harder about them until you find a way to deduce something useful.
The Minesweeper approach: don't even try to figure out the solution from only the clues you have right now. Instead, focus on finding a way to acquire another clue, and then using that to get another, and so on. Eventually you've collected so many clues that the answer is obvious.
Sometimes the Sudoku approach is necessary, because you've got all the clues you're ever going to get. But I think my new motto is "Never Sudoku a problem when you can Minesweeper it."
Gabe Schuyler
gabe_sky@infosec.exchangeAnnouncing: https://justaqrcode.com.
Tired of "free" QR code generators that are full of ads and trackers, that share your data, and that want to sell you something? Me too. Here's my act of resistance: I made a one-page site that works entirely in your browser to generate a simple QR code. And that's all it does. You can download the HTML page and run it locally, even. Read the source; nothing up my sleeves. Just a QR code.
My offer to you -- I will continue to pay for the domain name and web hosting for it, myself. If you find it valuable, you can pay it back by creating your own useful thing for the world and releasing it for free. Let's take back the friendly web, one vexingly-monetized utility at a time!
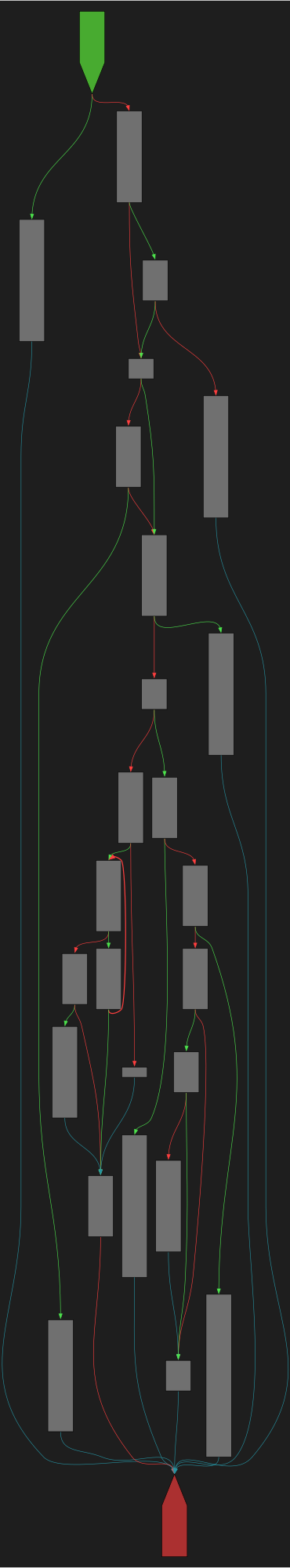
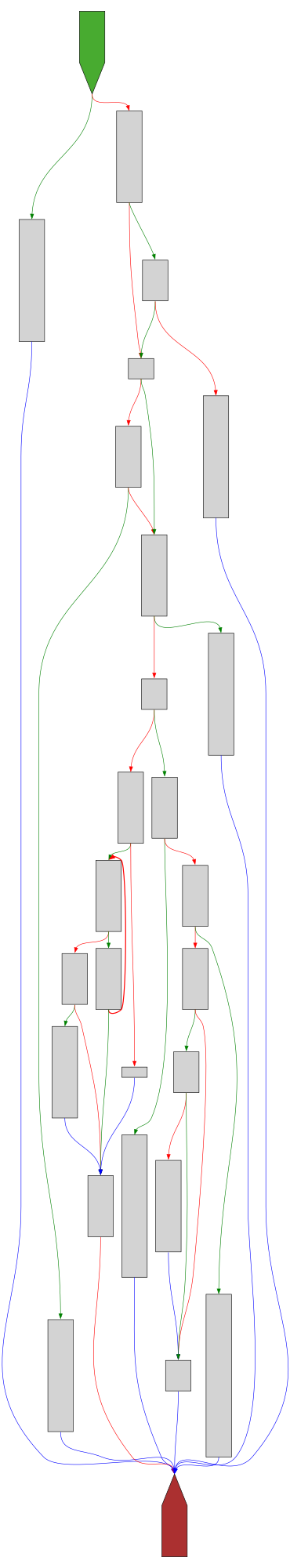
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00628bf0
PKCS7_decrypt
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00628bf0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00628bf0.json&colors=light