Posts
2515Following
640Followers
1438Ole André Vadla Ravnås
oleavr@fosstodon.orgFrida 17 is out 🎉
https://frida.re/news/2025/05/17/frida-17-0-0-released/
✧✦Catherine✦✧
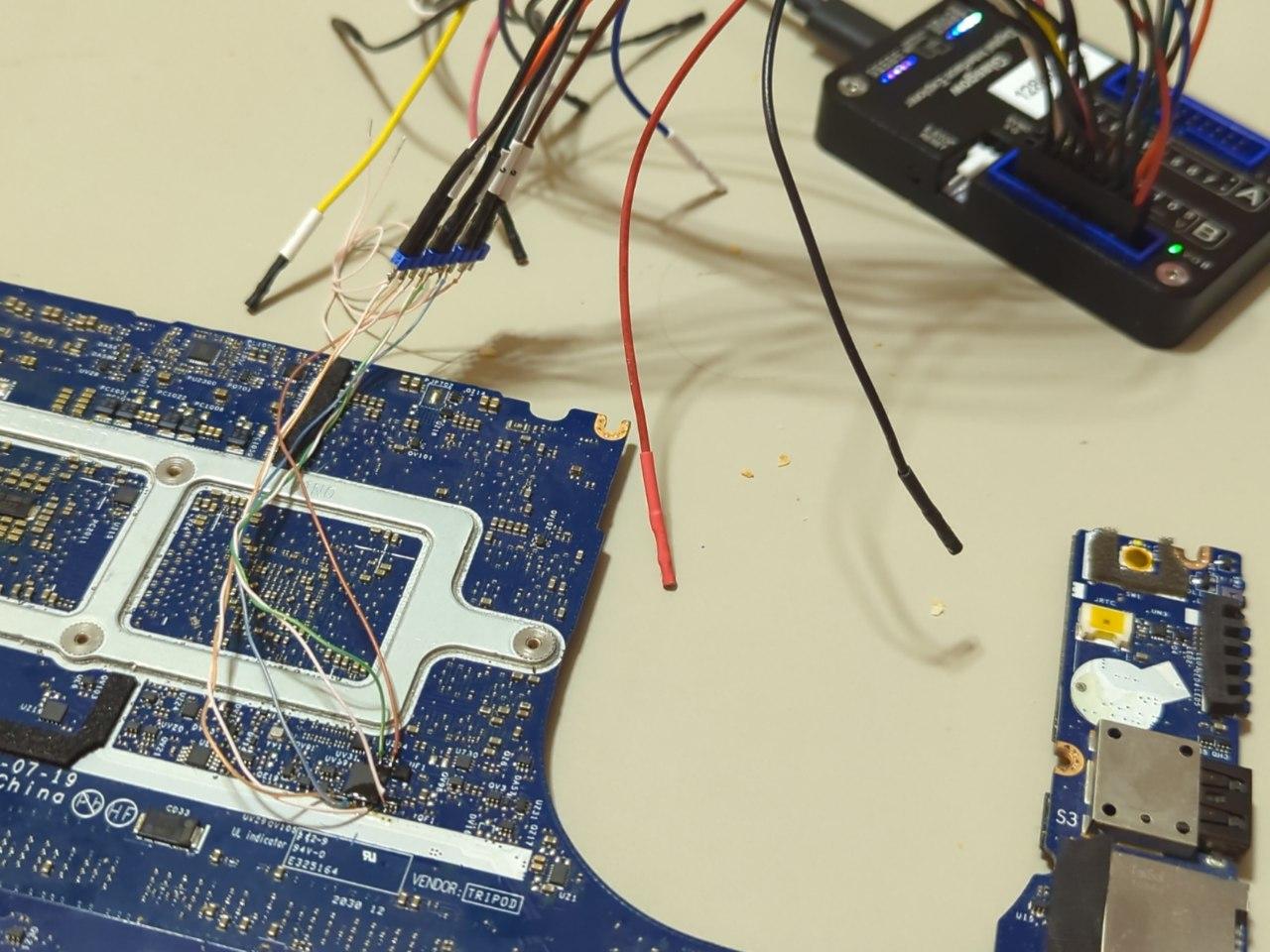
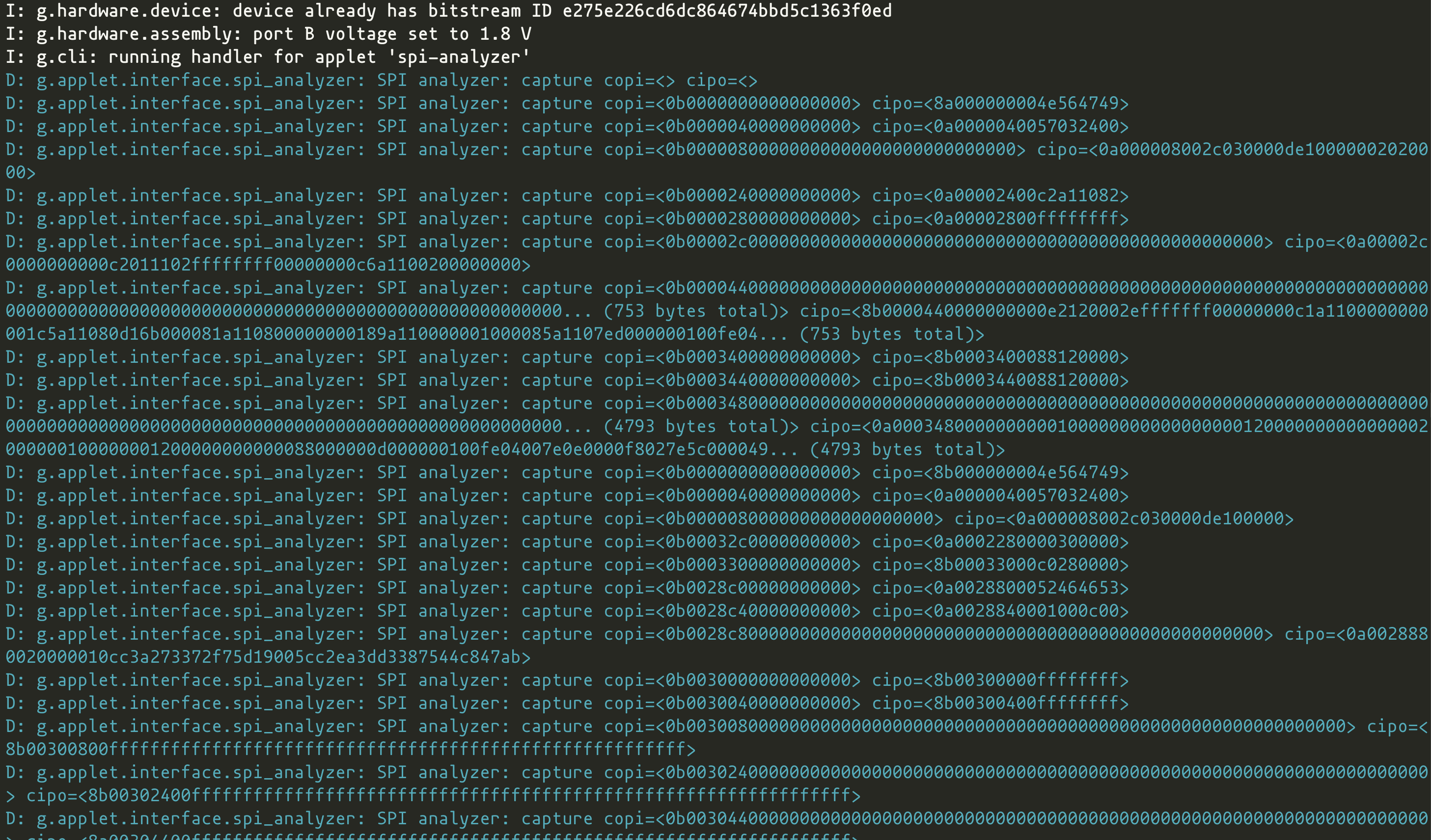
whitequark@mastodon.sociala motherboard from my now-previous laptop doesn't boot; the LED blink sequence decodes to "BIOS flash failure". first of all what the heck? that never happens (but the symptoms when it died were consistent with it happening)
anyway, it uses plain SPI, and #GlasgowInterfaceExplorer can now analyze SPI transactions very easily
let's find out
hackaday
hackaday@hackaday.socialEscaping US Tech Giants Leads European YouTuber to Open Source
https://hackaday.com/2025/05/17/escaping-us-tech-giants-leads-european-youtuber-to-open-source/
buherator
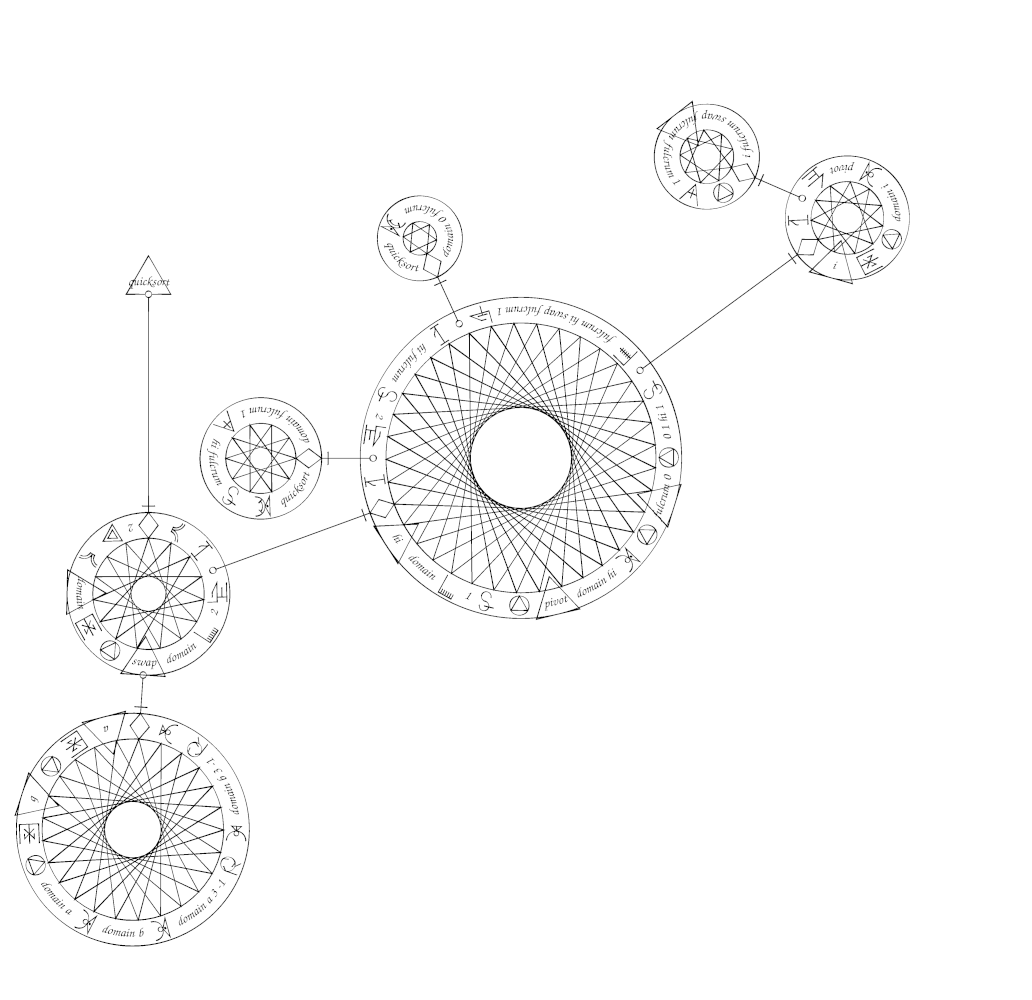
buheratorhttps://suberic.net/~dmm/projects/mystical/README.html
h/t @neauoire
Devine Lu Linvega
neauoire@merveilles.townA programming language that resembled magical circles.
docs: https://suberic.net/~dmm/projects/mystical/README.html
All sigils: https://suberic.net/~dmm/projects/mystical/docs/operators.html
by @yomikoma
Lorin Hochstein 
norootcause@hachyderm.io
Them: The real threat to reliability is all this complexity in our system!
Me: Wait, so those corrective actions that you proposed in the wake of that last incident, would they *reduce* complexity or *increase* it?
Them: …
Me: …
Trend Zero Day Initiative
thezdi@infosec.exchangePwn2Own Berlin 2025 comes to a close. We awarded $1,078,750 for 28 unique 0-days. Congrats to STAR Labs SG for winning Master of Pwn with $320,000. Thanks to @offensive_con for hosting, and thanks to all who participated. Can't wait to see you next year! #Pwn2Own #P2OBerlin
Open Source Security mailing list
oss_security@bird.makeupGLIBC-SA-2025-0002: CVE-2025-4802: glibc: elf: static setuid binary dlopen may incorrectly search LD_LIBRARY_PATH https://www.openwall.com/lists/oss-security/2025/05/17/2
Affects statically linked setuid binaries that call dlopen, including internally to glibc after setlocale or NSS functions such as getaddrinfo
buherator
buheratorhttps://cyberscoop.com/coinbase-cyberattack-extortion-counter-reward/
buherator
buheratorhttps://labs.watchtowr.com/expression-payloads-meet-mayhem-cve-2025-4427-and-cve-2025-4428/
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-qx2m-rcpc-v43v
buherator
buheratorAchievement unlocked: featured in exploits.club newsletter \o/
https://blog.exploits.club/exploits-club-weekly-newsletter-72-windows-on-windows-coreaudio-fuzzing-virtualbox-escapes-and-more/
Trend Zero Day Initiative
thezdi@infosec.exchangeWrapping up Day Two of #Pwn2Own Berlin 2025. We’ve awarded $695,000 for 20 unique 0-days, with one more day to go!
Jan Wildeboer 😷
jwildeboer@social.wildeboer.net
Dear #Letsencrypt, you helped secure millions and millions of servers, not just web servers. But your announcement at https://letsencrypt.org/2025/05/14/ending-tls-client-authentication/ about ending Ending TLS Client Authentication Certificate Support in 2026 because Google changes their requirements would result in your certificates being unusable for SMTP servers. You are literally risking an email collapse for many mailserver owners just to please Google? Please think again. Please.
Hanno Zulla
hzulla@infosec.exchangeThe cool thing about software development is that the computer is doing exactly what you tell it to do.
The cool thing about debugging is slowly learning what you actually told the computer to do.
Trend Zero Day Initiative
thezdi@infosec.exchangeConfirmed!! Dinh Ho Anh Khoa of Viettel Cyber Security combined an auth bypass and an insecure deserialization bug to exploit #Microsoft SharePoint. He earns $100,000 and 10 Master of Pwn points. #Pwn2Own #P2OBerlin
Peter Schaar
PWS_1@mastodon.social#Microsoft has blocked its services to the International Criminal Court by order of Donald #Trump. The #ICC prosecutor doesn’t have access to his #email. Source:AP
https://apnews.com/article/icc-trump-sanctions-karim-khan-court-a4b4c02751ab84c09718b1b95cbd5db3
Virus Bulletin
VirusBulletin@infosec.exchangeG DATA's Karsten Hahn details how software downloads for the printer company Procolored were infected with XRed backdoor for half a year. https://www.gdatasoftware.com/blog/2025/05/38200-printer-infected-software-downloads
Dr. Christopher Kunz
christopherkunz@chaos.socialCISA is changing the way they publizice alerts, including the KEV (known exploited vulnerabilities). These will no longer be shown on the "Alerts" overview, but must be subscribed to via GovAlert (or just scrape the JSON...).
The first vulnerability that is *not* being published as an alert is...drumroll... CVE-2025-47729. "The TeleMessage archiving backend through 2025-05-05 holds cleartext copies of messages from TM SGNL app users"
Isn't that a funny coincidence?