Posts
2512Following
641Followers
1439CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
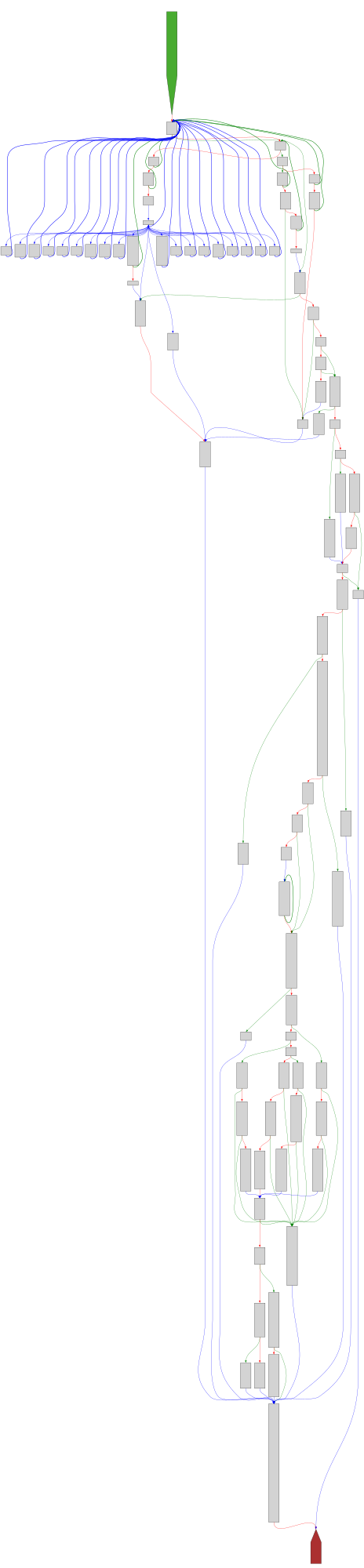
Address: 0043acc0
rsautl_main
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0043acc0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0043acc0.json&colors=light
buherator
buheratorhttps://karmainsecurity.com/KIS-2025-02
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialSleep deprivation is a form of torture.
Unless you are a parent, in which case it is a form of "children are a blessing, you wanted this, you're on your own, suck it up, good luck."
dragosr
dragosr@chaos.socialTime to update microcode on your Intel processors (gen >9)...
New speculative prediction bug lets you capture /etc/shadow with 99% reliability. They didn't make anything like it work on AMD or ARM... yet...
https://comsec.ethz.ch/research/microarch/branch-privilege-injection/
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-01247.html
https://github.com/intel/Intel-Linux-Processor-Microcode-Data-Files/releases/tag/microcode-20250512
chompie
chompie1337@haunted.computerMe and the homies are dropping browser exploits on the red team engagement 😎. Find out how to bypass WDAC + execute native shellcode using this one weird trick -- exploiting the V8 engine of a vulnerable trusted application.
https://www.ibm.com/think/x-force/operationalizing-browser-exploits-to-bypass-wdac
Taggart 
mttaggart@infosec.exchange
Holy wow, XSS to RCE in Restricted Mode in VSCode. What a find!
https://starlabs.sg/blog/2025/05-breaking-out-of-restricted-mode-xss-to-rce-in-visual-studio-code/
Trend Zero Day Initiative
thezdi@infosec.exchangeThe schedule for #Pwn2Own Berlin is now live! We have three days of exploitation set - including our first AI entries. https://www.zerodayinitiative.com/blog/2025/5/14/pwn2own-berlin-the-full-schedule #P2OBerlin
Peter Cohen
flargh@mastodon.socialdays like today I remember to do my breathing exercises and gently remind myself this is nothing an extinction level event cant fix
mahaloz
mahaloz@infosec.exchangeWhat does it mean to be a hacker? This semester, I taught a hacker history and culture class, which was a blast. In one assignment, my students paid tribute to the classic @phrack Pro-Phile -- a small bio on a famous hacker. Check out their pieces: https://cse194.mahaloz.re/prophiles.html
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@eupolicy.socialYes, hello! If you were following @bert_hubert@fosstodon.org you should have been redirected automatically to following this new account. And if not, if you are still interested in my ramblings, please follow this account manually. Can I ask for retoots so the people that might be interested see this news? Thanks!
TechnoTenshi 

technotenshi@infosec.exchange
Google quietly cut a key file access permission for Nextcloud’s Android app, breaking uploads for anything but media. The result: fewer features for a direct Drive competitor. Appeals were denied, while Google apps remain unaffected. Classic gatekeeping.
https://nextcloud.com/blog/nextcloud-android-file-upload-issue-google/
Open Source Security mailing list
oss_security@bird.makeupCVE-2024-28956: Xen Security Advisory 469 v2: x86: Indirect Target Selection https://www.openwall.com/lists/oss-security/2025/05/12/5
A bug in the hardware support for prediction-domain isolation. An attacker might be able to infer the contents of arbitrary host memory, including memory assigned to other guests.
buherator
buheratorhttps://bsky.app/profile/tannerofthenorth.bsky.social/post/3lp572utm5c2c
h/t @neurovagrant
#fromBsky
LaurieWired
lauriewired@bird.makeupWhat happens if a cosmic ray hits a voting machine?
In Belgium’s 2003 elections, a relatively unknown Communist Party candidate received 4096 extra votes…from a spontaneous bit inversion.
It was more votes than was mathematically possible at that polling station.
buherator
buheratorhttps://threadreaderapp.com/thread/1922015999118680495.html
buherator
buheratorhttps://www.politico.eu/article/viktor-orban-fidesz-party-hungary-russia-democracy-transparency-public-life-civil-society/
The darkest times of my life in #Hungary.
tiddy roosevelt
babe@glitterkitten.co.ukGood lord. Talk of the ruination of the web on here today I decided to see what it was like just straight up raw dogging my browsing habits for a little while. No ad blockers, no blocking cookie popups etc.
People actually USE this?!
buherator
buheratorhttps://blog.trailofbits.com/2025/05/14/the-cryptography-behind-passkeys/