Posts
3370Following
712Followers
1579buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/05/breaking-sound-barrier-part-i-fuzzing.html
Unnamed TNG skant beefcake
researchfairy@scholar.social"Wrong but plausible" is a feature and not a bug for LLMs if you're looking for a system to deploy where you can use it, say, to fine-tune insurance reimbursements to the exact dollar amount you wanted and have it produce the justifications needed to get there at an industrial scale
Nicolas Grégoire
agarri.fr@bsky.brid.gyXWiki has been compromised, and all personal wikis have been deleted. That includes mine, named XHE for "XML Hacking Encycopledia" 😢
a baby is making a sad face wh...
Binary Ninja
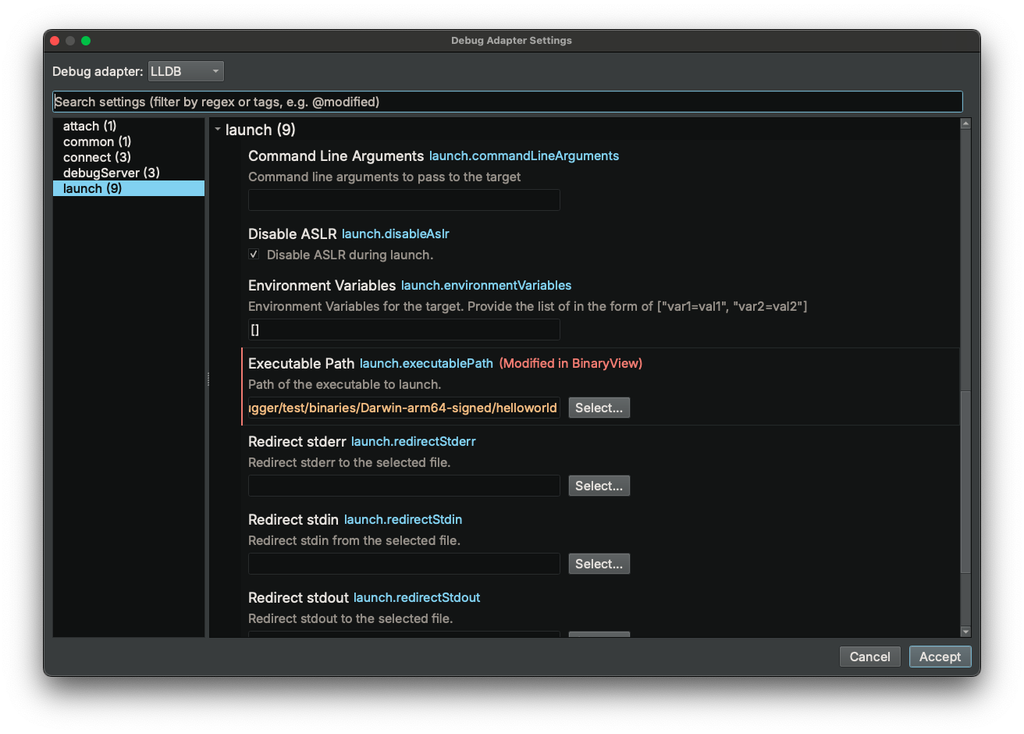
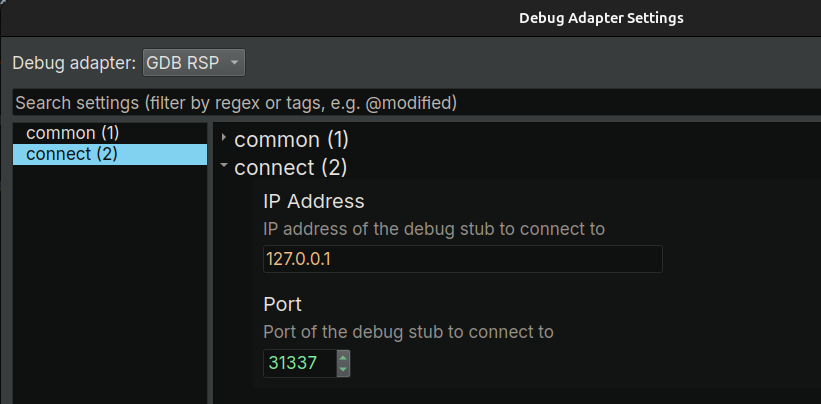
binaryninja@infosec.exchangeBinary Ninja 5.0 brings big updates to the debugger: a cleaner adapter settings UI, smarter analysis that won’t slow down your session, and new backends including rr and Corellium. Faster and more flexible debugging, whether local or remote! https://binary.ninja/2025/04/23/5.0-gallifrey.html#debugger
Jan Schaumann
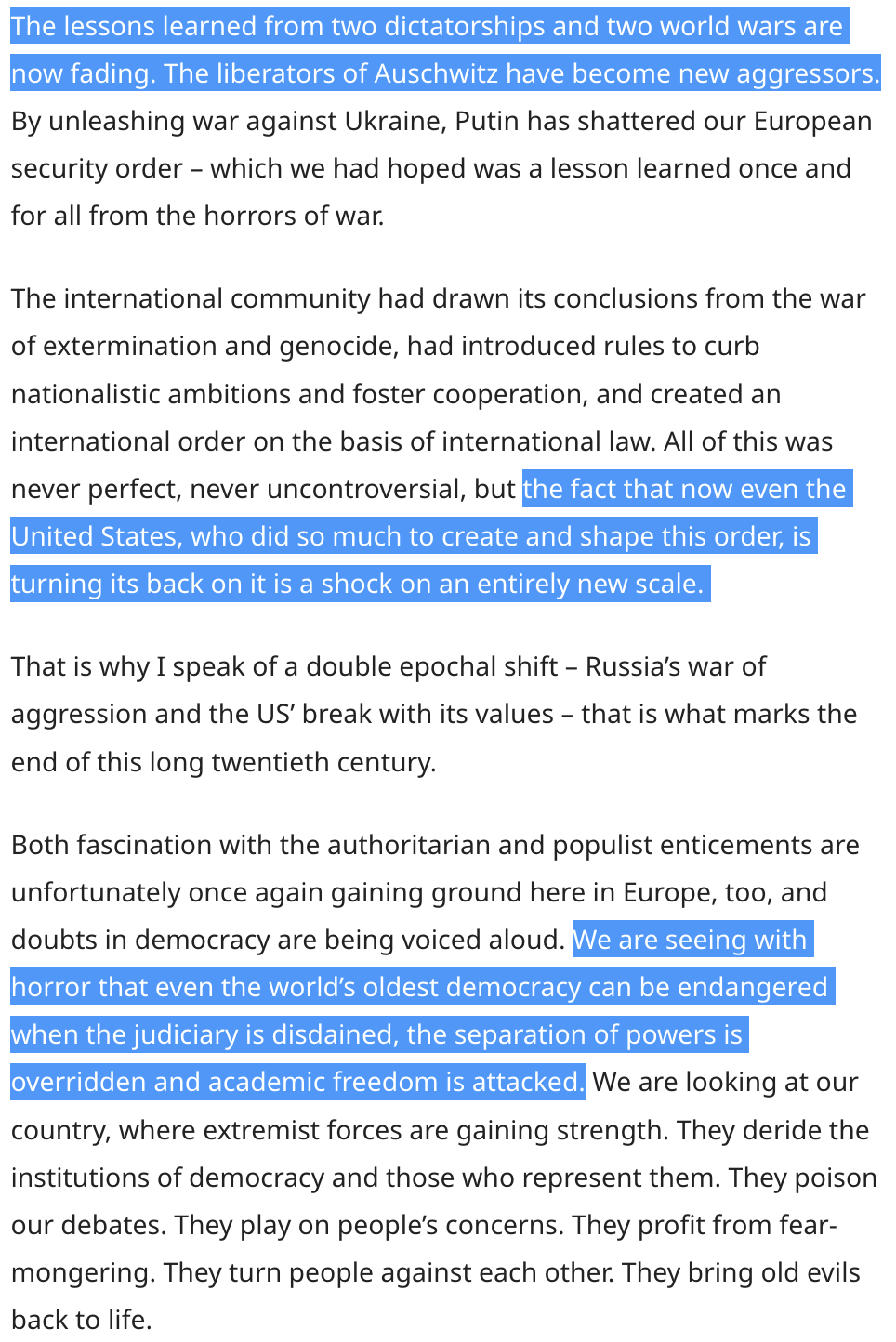
jschauma@mstdn.socialGerman President Steinmeier's speech commemorating the 80th anniversary of the end of World War II:
You want to read the whole thing, but the part below and the emphasis on the importance of learning from the past instead of describing it as a "cult of guilt" were powerful and eloquent. No words were minced, and we need more of that.
Tamas K Lengyel
tklengyel@discuss.systemsNow this looks like a pretty kick ass project: FUZZUER: Enabling Fuzzing of
UEFI Interfaces on EDK-2 https://www.ndss-symposium.org/wp-content/uploads/2025-400-paper.pdf and source at https://github.com/BreakingBoot/FuzzUEr
Tamas K Lengyel
tklengyel@discuss.systemsFinally a paper on malware fuzzing! PFUZZER: Practical, Sound, and Effective Multi-path Analysis of
Environment-sensitive Malware with Coverage-guided Fuzzing https://www.diag.uniroma1.it/~delia/papers/eurosp25-pfuzzer.pdf
buherator
buheratorFuzzing Windows Defender with loadlibrary in 2025
https://scrapco.de/blog/fuzzing-windows-defender-with-loadlibrary-in-2025.html
#Fuzzing #ReverseEngineering #Antivirus
kimapr
kimapr@ublog.kimapr.netI think it’s really funny that in windows the standard libraries serve to abstract away incompatibilities between the kernel of different windows releases while this funny thing:
- GLibc
in the lunix world does the exact opposite
Ivan Ožić Bebek
obivan@infosec.exchangeA practical NTLM relay attack using the MS-EVEN RPC protocol and antivirus-assisted coercion https://github.com/Thunter-HackTeam/EvilentCoerce
Yarden Shafir
yarden_shafir@bird.makeupFYI if you’re willing to link with ntdll or dynamically resolve it there’s a ton of APIs that return TEB/PEB or leave them in one of the registers.
(Don’t believe official return values. MSDN is a liar!)
Joxean Koret (@matalaz)
joxean@mastodon.socialToday 80 years ago Nazi Germany declared its unconditional surrender, ending the World War II.
buherator
buheratorhttps://blog.es3n1n.eu/posts/how-i-ruined-my-vacation/
Defender disabler tool:
https://github.com/es3n1n/defendnot
Mari0n
pinkflawd@mastodon.socialRecon training prices go up beginning of May! If Linux binary analysis and malware are down your alley, check out my 4-day training on the topic 🤓
https://recon.cx/2025/trainingLinuxMalwareReverseEngineering.html
buherator
buheratorhttps://www.crowdfense.com/cve-2024-11477-7zip-zstd-buffer-overflow
buherator
buheratorhttps://blog.exploits.club/exploits-club-weekly-newsletter-71-lots-of-linux-macos-oob-writes-enterprise-pre-auth-rces-and-more/
Project Zero Bot
p0botXNU VM_BEHAVIOR_ZERO_WIRED_PAGES behavior allows writing to read-only pages
https://project-zero.issues.chromium.org/issues/391518636
CVE-2025-24203
Lee Holmes 
Lee_Holmes@infosec.exchange
It makes me super uncomfortable that globbing in Bash can turn into code execution. The fact that the name of a file can change the behavior of ls is scary. This also works for other commands that you tend to glob with, such as rm.
sam4k
sam4k@infosec.exchangewith offensivecon around the corner, i figured id write another post on linux kernel exploitation techniques - this time i cover the world of page table exploitation! enjoy 🤓