Posts
3373Following
712Followers
1579eShard
eshard@infosec.exchangeThe full webinar recording is out. 🔴
Watch time travel debugging in action: https://youtu.be/tEzumvwjUzo
buherator
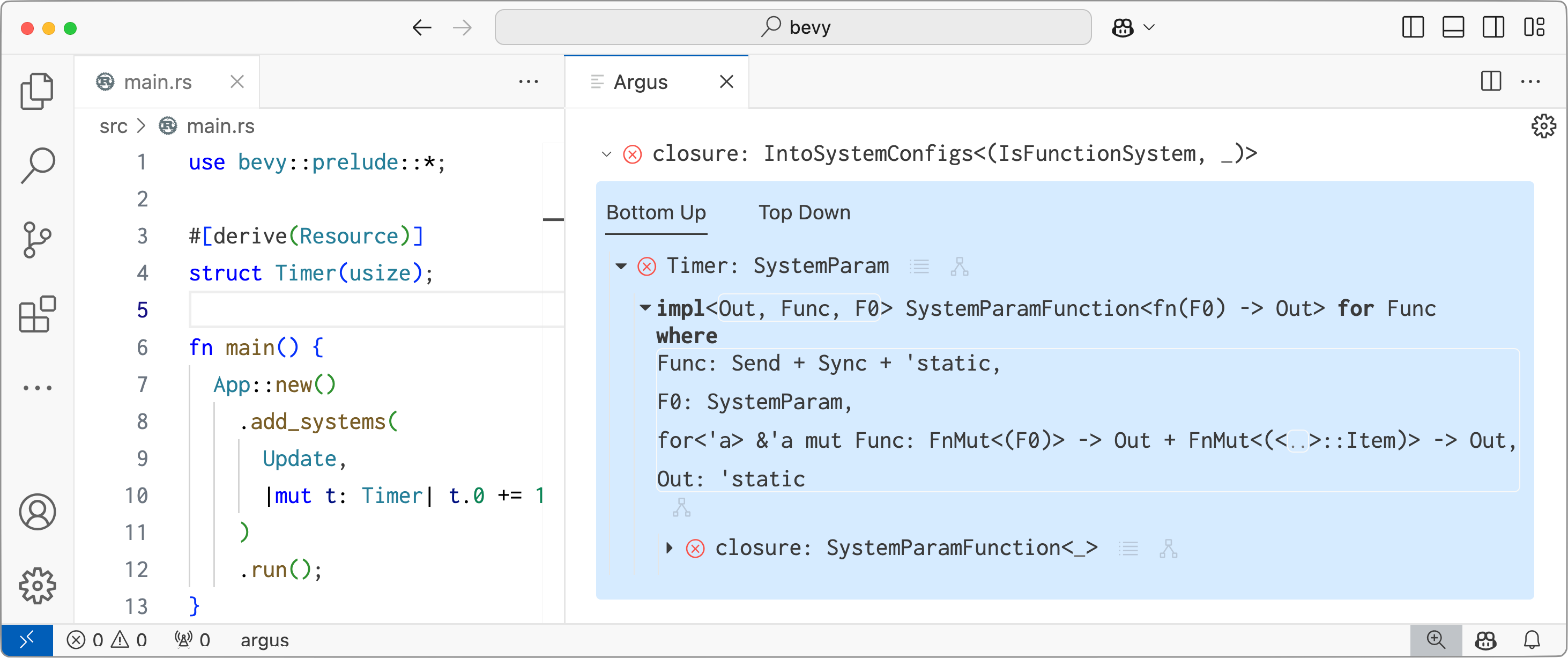
buherator- `pe_mofs_to_fofs_ex`
(not sure which meme template would fit this one)
⛧-440729 [sophie raven]
sophie@mastodon.catgirl.cloudShow content
going to take some weapons to the datacenter any day now
J-436215 "juno" ⚵
elsie@girlc.atbuherator
buheratorhttps://forms.gle/GdfVJDPnZHVz1jY67
On Google Forms of course /o\
HN Security
hnsec@infosec.exchangeHow was it like to attend the exclusive #ZeroDayQuest event? How did a Unix #hacker even qualify in the first place? How can you become one of the #Microsoft MVRs?
Our technical director @raptor answers these and other questions in his latest article:
https://security.humanativaspa.it/my-zero-day-quest-bluehat-podcast
Gammitin (Ben) 💾
Gammitin@mastodon.socialHappy birthday to Wolfenstein 3D, released on this day, 33 years ago on 5th May 1992!
The tech industry is a teenage industry. Rebelling against what it sees as old and uncool while desperately following fads and fashions as it tries to fit in with what everyone else is doing.
Will Crichton
tonofcrates@mastodon.socialIf you've ever struggled with trait/typeclass compiler errors, or if you're interested in better user interfaces for compiler diagnostics, check out our upcoming PLDI paper: "An Interactive Debugger for Rust Trait Errors"
Rust famously has good error messages. But we found that with the right interface, people become ~3x faster at identifying the root cause of a trait error. See our blog post, including a live demo in your browser:
https://cel.cs.brown.edu/blog/an-interactive-debugger-for-rust-trait-errors
Ionica Smeets
ionica@mathstodon.xyz“I started a spreadsheet, which is what middle-class professionals do when faced with systemic problems — we quantify things, as if converting human suffering into Excel cells might render it more manageable.” Via @gvwilson.
✧✦Catherine✦✧
whitequark@mastodon.socialdid you know that GDB includes a bytecode compiler? specifically, it has a private [edit: it's documented] bytecode format used between it and the GDB server, which the latter uses to implement conditional breakpoints with complex expressions and tracepoints
every time it hits a breakpoint/tracepoint it evaluates the bytecode, which has jumps and can read arbitrary target memory, and decides whether it really was hit or not
Insinuator
Insinuator@infosec.exchangeNew post: Full Disclosure: Multiple Rundeck Job Command Injections https://insinuator.net/2025/05/full-disclosure-multiple-rundeck-job-command-injections/
Alec Muffett
alecmuffett@mastodon.socialICYMI: “Every TWINSCAN EUV ships with ~45 million lines of code […] Bugfixes and features start out as *word documents* sent to a series of review boards…”
https://alecmuffett.com/article/113264
#SecurityByDesign #SoftwareEngineering #bugs
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
#Webmin: a critical security vulnerability discovered in a widely-used web-based system administration tool, allowing authenticated attackers to escalate privileges to root level and execute code.
Caused by CRLF injection: CVE-2025-2774 (CVSS 8.8)
👇
https://cybersecuritynews.com/webmin-vulnerability-escalate-privileges/
Project Zero Bot
p0botFirefox: JavaScript can run during XSLTProcessor transform, leading to use-after-free
https://project-zero.issues.chromium.org/issues/389079450
CVE-2025-3028
Programming Quotes
programming_quotes@mastodon.socialSoftware is like entropy. It is difficult to grasp, weighs nothing, and obeys the second law of thermodynamics; i.e. it always increases.
Soatok Dreamseeker
soatok@furry.engineerTech Companies Apparently Do Not Understand Why We Dislike AI
It's becoming increasingly apparent that one of the reasons why tech companies are so enthusiastic about shoving AI into every product and service is that they fundamentally do not understand why people dislike AI. I will elaborate. I was recently made aware of the Jetbrains developer ecosystem survey, which included a lot of questions about AI. After I answered some of them negatively (and possibly…
http://soatok.blog/2025/05/04/tech-companies-apparently-do-not-understand-why-we-dislike-ai/
Zhuowei Zhang
zhuowei@notnow.devWrote a wrapper for Linux’s HID descriptor parser so I can fuzz it with libFuzzer: https://github.com/worthdoingbadly/hid-parser-harness
I’m still trying to figure out the USB uninitialized memory issue from that Amnesty International report, so I made it abort when it sees a 0xbe byte (ASan fills uninitialized malloc’d buffers with this).