Posts
3373Following
712Followers
1579✧✦Catherine✦✧
whitequark@mastodon.socialdid you know that GDB includes a bytecode compiler? specifically, it has a private [edit: it's documented] bytecode format used between it and the GDB server, which the latter uses to implement conditional breakpoints with complex expressions and tracepoints
every time it hits a breakpoint/tracepoint it evaluates the bytecode, which has jumps and can read arbitrary target memory, and decides whether it really was hit or not
Insinuator
Insinuator@infosec.exchangeNew post: Full Disclosure: Multiple Rundeck Job Command Injections https://insinuator.net/2025/05/full-disclosure-multiple-rundeck-job-command-injections/
Alec Muffett
alecmuffett@mastodon.socialICYMI: “Every TWINSCAN EUV ships with ~45 million lines of code […] Bugfixes and features start out as *word documents* sent to a series of review boards…”
https://alecmuffett.com/article/113264
#SecurityByDesign #SoftwareEngineering #bugs
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
#Webmin: a critical security vulnerability discovered in a widely-used web-based system administration tool, allowing authenticated attackers to escalate privileges to root level and execute code.
Caused by CRLF injection: CVE-2025-2774 (CVSS 8.8)
👇
https://cybersecuritynews.com/webmin-vulnerability-escalate-privileges/
Project Zero Bot
p0botFirefox: JavaScript can run during XSLTProcessor transform, leading to use-after-free
https://project-zero.issues.chromium.org/issues/389079450
CVE-2025-3028
Programming Quotes
programming_quotes@mastodon.socialSoftware is like entropy. It is difficult to grasp, weighs nothing, and obeys the second law of thermodynamics; i.e. it always increases.
Soatok Dreamseeker
soatok@furry.engineerTech Companies Apparently Do Not Understand Why We Dislike AI
It's becoming increasingly apparent that one of the reasons why tech companies are so enthusiastic about shoving AI into every product and service is that they fundamentally do not understand why people dislike AI. I will elaborate. I was recently made aware of the Jetbrains developer ecosystem survey, which included a lot of questions about AI. After I answered some of them negatively (and possibly…
http://soatok.blog/2025/05/04/tech-companies-apparently-do-not-understand-why-we-dislike-ai/
Zhuowei Zhang
zhuowei@notnow.devWrote a wrapper for Linux’s HID descriptor parser so I can fuzz it with libFuzzer: https://github.com/worthdoingbadly/hid-parser-harness
I’m still trying to figure out the USB uninitialized memory issue from that Amnesty International report, so I made it abort when it sees a 0xbe byte (ASan fills uninitialized malloc’d buffers with this).
beSpacific
bespacific@newsie.social#TeleMessage, that app used by the #Trump administration to archive Signal messages, has been #hacked. The #hacker managed to get some users' #Signal group chats and messages too. This is a hugely significant #breach not just for those individual customers, but also for the U.S. government more widely. #natsec #nationalsecurity https://www.404media.co/the-signal-clone-the-trump-admin-uses-was-hacked/ #government #democracy #trump #hegseth
Misinformation-Superhighwayman
DamienWise@aus.socialMay the 5th Element be with you.
jonpalmisc
jonpalmisc@infosec.exchangeQuick note: https://arm.jonpalmisc.com/ has been updated to the latest version of the Arm spec. Any changes should be strictly improvements, but let me know if something seems off.
buherator
buheratorNCommander
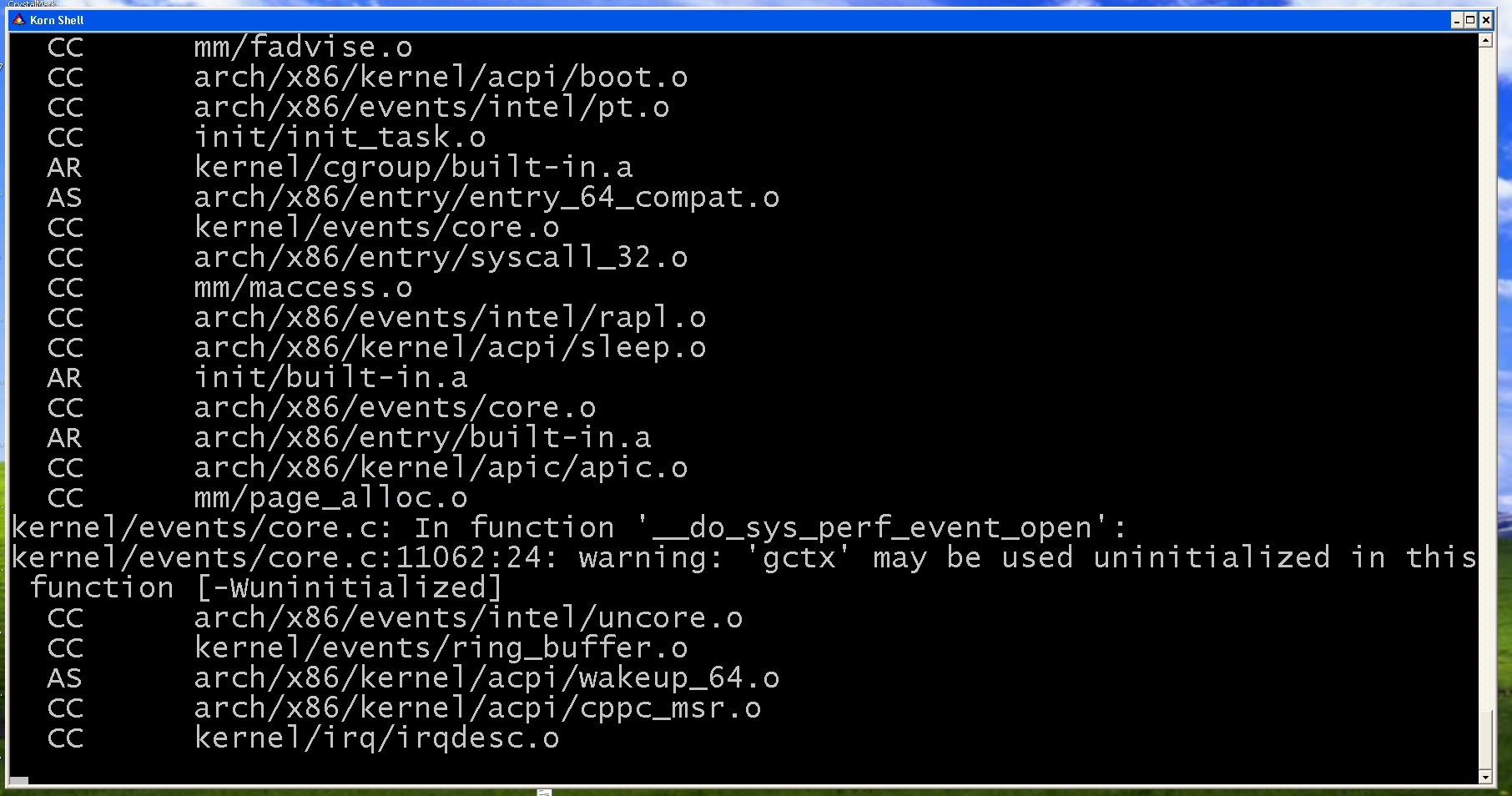
ncommander@social.restless.systemsWant to see something cursed?
It's the Linux kernel 4.19 building *natively* under Windows XP under Services for UNIX. The amount of effort to get this far was immense ...
EDIT: Follow the adventure at https://YouTube.com/c/NCommander
postcardware.net
postcardware@cyber.msSent from Utrecht, Netherlands on August 21, 1995. https://postcardware.net/?id=37-32
buherator
buheratorhttps://www.youtube.com/watch?v=jTfwpWj4eqA
Miss this band :(
#punk #music
CISA KEV Tracker
cisakevtracker@mastodon.socialCVE ID: CVE-2024-58136
Vendor: Yiiframework
Product: Yii
Date Added: 2025-05-02
Vulnerability: Yiiframework Yii Improper Protection of Alternate Path Vulnerability
Notes: This vulnerability affects a common open-source component, third-party library, or a protocol used by different products. For more information, please see: https://www.yiiframework.com/news/709/please-upgrade-to-yii-2-0-52 ; https://nvd.nist.gov/vuln/detail/CVE-2024-58136
CVE URL: https://nvd.nist.gov/vuln/detail/CVE-2024-58136
jvoisin
jvoisin@infosec.exchangeMaking Burp Suite snappy on Asahi Linux — https://dustri.org/b/making-burp-suite-snappy-on-asahi-linux.html