Posts
2555Following
630Followers
1409Graham Cluley
gcluley@mastodon.green21 million employee screenshots leaked in bossware breach blunder.
Daenney
ohno@dny.socialProof-of-work challenges have become the current hotness for defeating AI scrapers. I think it’s great we have these and that they’re getting deployed to great effect. But I’ve also seen a lot of people claim the “AI scrapers” problem is now solved and I’m sorry to tell you this but no it’s not.
The reason it’s solved right now is because most of these scrapers don’t execute JavaScript. But with enough people deploying PoW proxies, the economics around that change enough to make it worthwhile for AI companies to do so. AI companies have more money than you. Yes it’ll cost them, but that cost is worth it to them because otherwise they don’t have a business.
(Also Anubis and other solutions default to only triggering if the User-Agent header contains Mozilla so guess what! It’ll soon need to be enabled regardless of the value of that header because it’s trivial to circumvent. Then the cost goes up for the operator too as more and more users get affected.)
The JS needed for the PoW stuff isn’t complicated. A small JS interpreter can handle that. What mostly remains is then the cost of the hash. Right now most things use SHA256, for which we have CPU extensions and AVX instructions to speed this up. Constantly increasing the PoW rounds doesn’t solve this. Eventually the experience degrades too much for real users, whereas servers literally don’t care. Nobody is sitting there waiting for the output to be rendered. All they want is to get the content to train on.
PoW proxies are a stopgap, and a very useful one. But a stopgap nonetheless. We’re buying ourselves time. But we’re going to need more than this. Including legislation that outlaws some of this shit entirely.
AI is a technology, but the root of the problem we’re facing is a societal and political one. We cannot ignore those aspects and exclude them from a solution.
Trend Zero Day Initiative
thezdi@bird.makeupAll of the gear needed for #Pwn2Own Berlin is on its way. Next stop - Germany!
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgIn 15 minutes Europe will hopefully launch its next climate satellite. The launch can however only be watched via YouTube since we apparently can’t do that ourselves and have to put our government info next to the antivax promo. https://www.esa.int/ESA_Multimedia/ESA_Web_TV
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250428-00/?p=111121
Jesko Hüttenhain
rattle@infosec.exchangeFYSA; #BinaryRefinery has switched from pefile to LIEF:
https://github.com/binref/refinery/pull/84
It shouldn't change anything, but if it does, please let me know.
Lorenzo Stoakes
ljs@mastodonapp.ukI wrote a book on Linux Memory Management, published by @nostarch - it's a comprehensive 1300 page exploration of Linux 6.0's memory management code, depth-first, diving into the code and REALLY explaining how things work.
The idea is to avoid hand waving as much as possible and literally explore what the kernel _actually_ does.
It's full of diagrams and careful explanations of logic including a ton of stuff you just can't find anywhere else.
It's currently available in its entirety in draft form via early access when you pre-order.
It's available at https://nostarch.com/linux-memory-manager
:)
Tib3rius 
tib3rius@infosec.exchange
Thanks Forbes, I was confused what password spraying...sorry, "sparaying" attacks looked like. 🫠
Go hack more AI shit.
https://frycos.github.io/vulns4free/2025/04/28/mailessentials.html
buherator
buheratorShow content
https://risingnemesisrecords.bandcamp.com/track/a-new-god-of-wrath
Daring Fireball
daringfireball@mastodon.social★ Another Periodic Suggestion to Try, Just Try, Switching to Kagi for Search
https://daringfireball.net/2025/04/try_switching_to_kagi
Michał "rysiek" Woźniak · 🇺🇦
rysiek@mstdn.socialApparently #PerplexityAI CEO is annoyed that people are sharing that article where he is quoted saying that their browser will track everything users do to sell more ads.
> “That’s kind of one of the other reasons we wanted to build a browser, is we want to get data even outside the app to better understand you,” Srinivas said.
This is that article, in case you'd like to share it:
https://techcrunch.com/2025/04/24/perplexity-ceo-says-its-browser-will-track-everything-users-do-online-to-sell-hyper-personalized-ads/
Receipt:
https://xcancel.com/AravSrinivas/status/1915812398470205461#m
st1nger  🏴☠️
🏴☠️ 

st1nger@infosec.exchange
"In the coming day(s), pretty much every #Kali system out there will fail to update. [..] This is not only you, this is for everyone, and this is entirely our fault. We lost access to the signing key of the repository, so we had to create a new one," https://www.kali.org/blog/new-kali-archive-signing-key/
CISA KEV Tracker
cisakevtracker@mastodon.socialCVE ID: CVE-2025-1976
Vendor: Broadcom
Product: Brocade Fabric OS
Date Added: 2025-04-28
Vulnerability: Broadcom Brocade Fabric OS Code Injection Vulnerability
Notes: https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/25602 ; https://nvd.nist.gov/vuln/detail/CVE-2025-1976
CVE URL: https://nvd.nist.gov/vuln/detail/CVE-2025-1976
Linux Kernel Security
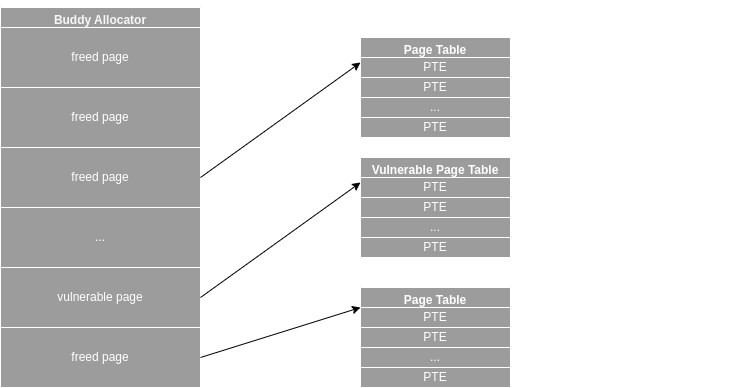
linkersec@infosec.exchangeExploiting CVE-2024-0582 via the Dirty Pagetable Method
Kuzey Arda Bulut posted an article about exploiting CVE-2024-0582 in io_uring using the Dirty Pagetable technique.
https://kuzey.rs/posts/Dirty_Page_Table/
This bug was previously reported by @jann and exploited by Oriol Castejón.
https://project-zero.issues.chromium.org/issues/42451653
https://blog.exodusintel.com/2024/03/27/mind-the-patch-gap-exploiting-an-io_uring-vulnerability-in-ubuntu/
buherator
buheratorclearbluejar
clearbluejar@infosec.exchangeNew #ghidriff release! v0.9.0
- Set custom analysis options
- Set custom base address (bootloaders, etc)
https://github.com/clearbluejar/ghidriff/releases/tag/v0.9.0
buherator
buheratorShow content
https://vulgardisplayofpurring.bandcamp.com/album/vulgar-display-of-purring-presents-new-york
This is a fun compilation!
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialI cannot stress this enough:
In a lot of traditions what we call fairy tales (or wonder tales) were for adults. Often told by grown men at the barracks or during work.
Which means uncensored fairy tale texts often include a whole lot of cussing. Because you'd yell "Sh**!" too if a devil chased you.
And this is how we get the scene where an evil king offers a hero money for his services and the hero flat out says "Your majesty, suck my d***"