Posts
2557Following
630Followers
1411buherator
buheratorShow content
https://risingnemesisrecords.bandcamp.com/track/a-new-god-of-wrath
Daring Fireball
daringfireball@mastodon.social★ Another Periodic Suggestion to Try, Just Try, Switching to Kagi for Search
https://daringfireball.net/2025/04/try_switching_to_kagi
Michał "rysiek" Woźniak · 🇺🇦
rysiek@mstdn.socialApparently #PerplexityAI CEO is annoyed that people are sharing that article where he is quoted saying that their browser will track everything users do to sell more ads.
> “That’s kind of one of the other reasons we wanted to build a browser, is we want to get data even outside the app to better understand you,” Srinivas said.
This is that article, in case you'd like to share it:
https://techcrunch.com/2025/04/24/perplexity-ceo-says-its-browser-will-track-everything-users-do-online-to-sell-hyper-personalized-ads/
Receipt:
https://xcancel.com/AravSrinivas/status/1915812398470205461#m
st1nger  🏴☠️
🏴☠️ 

st1nger@infosec.exchange
"In the coming day(s), pretty much every #Kali system out there will fail to update. [..] This is not only you, this is for everyone, and this is entirely our fault. We lost access to the signing key of the repository, so we had to create a new one," https://www.kali.org/blog/new-kali-archive-signing-key/
CISA KEV Tracker
cisakevtracker@mastodon.socialCVE ID: CVE-2025-1976
Vendor: Broadcom
Product: Brocade Fabric OS
Date Added: 2025-04-28
Vulnerability: Broadcom Brocade Fabric OS Code Injection Vulnerability
Notes: https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/25602 ; https://nvd.nist.gov/vuln/detail/CVE-2025-1976
CVE URL: https://nvd.nist.gov/vuln/detail/CVE-2025-1976
Linux Kernel Security
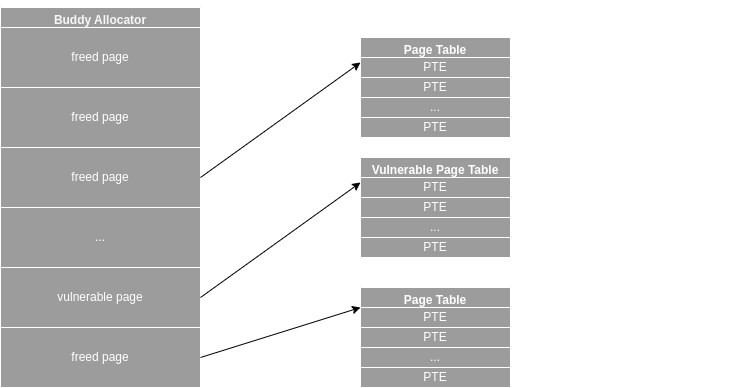
linkersec@infosec.exchangeExploiting CVE-2024-0582 via the Dirty Pagetable Method
Kuzey Arda Bulut posted an article about exploiting CVE-2024-0582 in io_uring using the Dirty Pagetable technique.
https://kuzey.rs/posts/Dirty_Page_Table/
This bug was previously reported by @jann and exploited by Oriol Castejón.
https://project-zero.issues.chromium.org/issues/42451653
https://blog.exodusintel.com/2024/03/27/mind-the-patch-gap-exploiting-an-io_uring-vulnerability-in-ubuntu/
buherator
buheratorclearbluejar
clearbluejar@infosec.exchangeNew #ghidriff release! v0.9.0
- Set custom analysis options
- Set custom base address (bootloaders, etc)
https://github.com/clearbluejar/ghidriff/releases/tag/v0.9.0
buherator
buheratorShow content
https://vulgardisplayofpurring.bandcamp.com/album/vulgar-display-of-purring-presents-new-york
This is a fun compilation!
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialI cannot stress this enough:
In a lot of traditions what we call fairy tales (or wonder tales) were for adults. Often told by grown men at the barracks or during work.
Which means uncensored fairy tale texts often include a whole lot of cussing. Because you'd yell "Sh**!" too if a devil chased you.
And this is how we get the scene where an evil king offers a hero money for his services and the hero flat out says "Your majesty, suck my d***"
The DFIR Report
TheDFIRReport@infosec.exchange🌟New report out today!🌟
Navigating Through The Fog
In December 2024, The DFIR Report's Threat Intel Group uncovered an open directory linked to a Fog ransomware affiliate, revealing their operational toolkit.
Key takeaways from our analysis:
➡️ Initial Access: Compromised SonicWall VPN credentials were used.
➡️ Toolkit: Included tools for reconnaissance, exploitation (Certipy, Zer0dump), credential theft (DonPAPI), persistence (AnyDesk automated via PowerShell), and C2 (Sliver, Proxychains tunneling).
➡️ Targets: Victims spanned technology, education, and logistics sectors across Europe, North America, and South America.
➡️ Persistence: AnyDesk RMM tool was leveraged for maintaining access.
➡️ Command & Control: Sliver C2 executables were hosted alongside Proxychains for traffic tunneling.
Read the full analysis here: https://thedfirreport.com/2025/04/28/navigating-through-the-fog/
Caitlin Condon
catc0n@infosec.exchangeLike others, Rapid7 MDR has observed in-the-wild exploitation of SAP NetWeaver Visual Composer CVE-2025-31324 in customer environments. Webshells being dropped with random 8-character names. Earliest confirmed EITW on our side currently is late March, but I'd expect that may change (i.e., move earlier). Manufacturing is overwhelmingly the most affected vertical, mostly in the U.S.
Romain THOMAS
rh0main@infosec.exchangeFuzzing Windows ARM64 binaries with a DBI and LLVM?
Here we go: https://www.romainthomas.fr/post/25-04-windows-arm64-qbdi-fuzzing/
Stacey Cornelius 🇨🇦
StaceyCornelius@zeroes.caRandom rant re: claiming your online space as a creator of any stripe.
Create connections with your people, not corporate platforms. As in:
"My online shop" *not* "My Etsy shop"
"My newsletter" *not* "My Substack" (or Ghost, etc)
I get that for some people, Substack is currently their only viable option. They do not need the marketing boost.
And I've seen so many times, for two decades now, "Oh look at the cute thing I found on Etsy!" with zero mention of the person who made it. Zero. Reinforce your name, not theirs.
Repetition = recognition. You bust your ass to build your thing. Make sure people remember you, not a corporate platform that could turn on a dime. You deserve better.
Rant over.
Kornel
kornel@mastodon.socialSIGBOIVK 2025 [PDF, p170]: https://sigbovik.org/2025/proceedings.pdf
`ccdoom` is a standards-compliant C23 C compiler that has "program-agnostic compilation model" and "advanced whole-program dead-code elimination" that always outputs doom.exe.
> ccdoom adopts a more user-centric approach to safety: the output contains significantly more monsters than the output of most C compilers, but the user is provided sufficient ammunition to defeat them.
Andreas Klopsch
hackingump1@infosec.exchangePresenting "Unveiling RIFT: Advanced Pattern Matching for Rust Libraries" at RECON Montreal 2025!
Sharing research on discovering Rust dependencies in compiled binaries.
See you there! 🚀
#RECON2025 #RustLang #ReverseEngineering
Phrack
phrack@haunted.computerRUMOURS are TRUE 🤷♀️
PHRACK will be releasing a SPECIAL #71.5 👉HARDCOVER👈
at https://www.offensivecon.org/
BERLIN ("The 𞅀-Day Edition").
Main #72 release THIS SUMMER at MULTIPLE conferences (main release at WHY2025). ❤️
Attack and Defense
attackanddefense@infosec.exchangeIf you've discovered a potential vulnerability in Firefox, please see our way to get rewarded for your work. We do not require exploits. Just a bug description is enough.
Of course, we reward and encourage sending us more details (PoC, detailed report, regression range, potential fix). But to qualify for a bug bounty, all you need is a bug.
Please check our bounty FAQ at https://www.mozilla.org/en-US/security/bug-bounty/faq/
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchangeIf you've discovered vulnerabilities in major browsers like Chrome, Safari, or Firefox, our program offers a fast, efficient way to get rewarded for your work. We focus exclusively on browsers with a large market share, ensuring your findings have real impact.
Our process is designed for efficiency—eliminating the usual delays and bureaucratic hurdles. You can submit vulnerabilities in minutes, receive detailed feedback within 72 hours, and be compensated with quick payouts within 15 days after validation.
We handle the full disclosure process, including vendor communications and paperwork, so you can focus on what matters: your research. Plus, you can maintain anonymity while receiving fair compensation for your contributions.
Check out the list of supported browsers and get started here: https://ssd-disclosure.com/product-index/