Posts
3180Following
705Followers
1561Rob Ricci
ricci@discuss.systemsWith bluesky (mostly) going down for a few hours today, I got to wondering about how decentralized the fediverse really is in terms of where its servers are hosted. I grabbed a server list from fedidb, with network information coming from ipinfo.io .
[EDIT: I did a better analysis on a dataset of 10x as many servers, see https://discuss.systems/@ricci/114400324446169152 ]
These stats are by the number of *servers* not the number of *users* (maybe I'll run those stats later).
fedidb currently tracks 2,650 servers of various types (Mastodon, pixelfed, lemmy, misskey, peertube, etc)
The fediverse is most vulnerable to disruptions at CloudFlare: 24% of Fediverse servers are behind it. Also note that this means that I don't have real data on where this 24% are located or hosted, since CloudFlare obscures this by design.
Beyond CloudFlare, the fediverse is not too concentrated on any one network. The most popular host, Hertzner, only hosts 14% of fediverse servers, and it falls off fast from there.
Here are the top networks where fediverse servers are hosted:
504 Cloudflare, Inc.
356 Hetzner Online GmbH
130 DigitalOcean, LLC
114 OVH SAS
56 netcup GmbH
55 Amazon.com, Inc.
55 Akamai Connected Cloud
36 Contabo GmbH
33 SAKURA Internet Inc.
32 The Constant Company, LLC
31 Xserver Inc.
28 SCALEWAY S.A.S.
24 Google LLC
23 Oracle Corporation
16 GMO Internet Group, Inc.
14 IONOS SE
14 FranTech Solutions
11 Hostinger International Limited
10 Nubes, LLC
Half of fediverse servers are on networks that host 50 or fewer servers - that's pretty good for resiliency.
There is even more diversity when it comes to BGP prefixes, which is good for resiliency: for example, the cloud providers that have multiple availability zones will generally have them on different prefixes, so this gets closer to giving us a picture of the specific bits of infrastructure the fediverse relies on.
The top BGP prefixes:
55 104.21.48.0/20
50 104.21.16.0/20
48 104.21.64.0/20
41 104.21.32.0/20
41 104.21.0.0/20
38 104.21.80.0/20
32 172.67.128.0/20
31 172.67.144.0/20
28 172.67.208.0/20
28 162.43.0.0/17
27 104.26.0.0/20
26 172.67.192.0/20
26 172.67.176.0/20
23 172.67.160.0/20
19 116.203.0.0/16
17 172.67.64.0/20
17 159.69.0.0/16
16 65.109.0.0/16
14 88.99.0.0/16
14 49.13.0.0/16
13 78.46.0.0/15
13 167.235.0.0/16
13 138.201.0.0/16
11 95.217.0.0/16
11 95.216.0.0/16
11 49.12.0.0/16
11 135.181.0.0/16
10 37.27.0.0/16
10 157.90.0.0/16
75% of fediverse servers are behind BGP prefixes that host 10 or fewer servers, meaning that the fediverse is *very* resilient to large network outages.
Top countries where fediverse servers are hosted:
871 United States
439 Germany
156 France
148 Japan
75 Finland
57 Canada
49 Netherlands
38 United Kingdom
26 Switzerland
26 South Korea
21 Spain
19 Sweden
18 Austria
17 Australia
15 Russia
12 Czech Republic
10 Singapore
10 Italy
And finally, a map of the locations of fediverse servers:
https://ipinfo.io/tools/map/91960023-e8c6-4bee-9b07-721f2c8febab
buherator
buheratorhttps://en.m.wikipedia.org/wiki/Razdan_(computer)
Phrack
phrack@haunted.computer🐣 CRACKME RESULTS are OUT! 💥
Congrats to rt_saber for being so quick.
Kudos to all those who hammered CloudFlare hard.
https://github.com/phrackzine/crackme/blob/main/easter-2025/teaser-challenge-solution.md
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Another header bypass, this time a Citrix NetScaler nasty:
HD Moore
hdm@infosec.exchangeA few quick notes on the Erlang OTP SSHd RCE (CVE-2025-32433):
1. Cisco confirmed that ConfD and NSO products are affected (ports 830, 2022, and 2024 versus 22)
2. Signatures looking for clear-text channel open and exec calls will miss exploits that deliver the same payloads after the key exchange.
3. If you find a machine in your environment and can't disable the service, running the exploit with the payload `ssh:stop().` will shut down the SSH service temporarily.
William R. Messmer
wmessmer@bird.makeupIf you update WinDbg today (1.2504.15001.0), you might notice another icon in the View tab of the ribbon, one called "Parallel Stacks". While incredibly useful in its own right, this isn't just a parallel stacks view. It's the introduction of graph visualization for extensions!
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Kinda want a DirBuster style list of headers at this point, so many times, we see new CVEs stemming from headers with magical properties.
✧✦Catherine✦✧
whitequark@mastodon.socialShow content
OH: see, if you slit your wrists, at least you accomplish something in the end. unlike doing a CTF
/r/netsec
_r_netsec@infosec.exchangeFire In The Hole, We’re Breaching The Vault - Commvault Remote Code Execution (CVE-2025-34028) - watchTowr Labs https://labs.watchtowr.com/fire-in-the-hole-were-breaching-the-vault-commvault-remote-code-execution-cve-2025-34028/
buherator
buheratorhttps://0xdeadc0de.xyz/blog/cve-2025-1731_cve-2025-1732
SSH tunnels FTW!
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
Two Use After Free (UAF) vulnerabilities were discovered within Chrome’s Browser process by one of our researchers at SSD Labs:
https://ssd-disclosure.com/ssd-advisory-miracleptr-sandbox/
daniel:// stenberg://
bagder@mastodon.socialHow the CNA thing is working out for #curl
https://daniel.haxx.se/blog/2025/04/24/how-the-cna-thing-is-working-out/
buherator
buheratorhttps://blog.ret2.io/2025/04/23/pwn2own-soho-2024-diskstation/
buherator
buherator- Some rich text + images hosted online for the event
- Subscription form to get updates
- Stats about expected attendance
- ??? (this is my first time)
Edit: I don't charge anything for the event, so percentage commission can work.
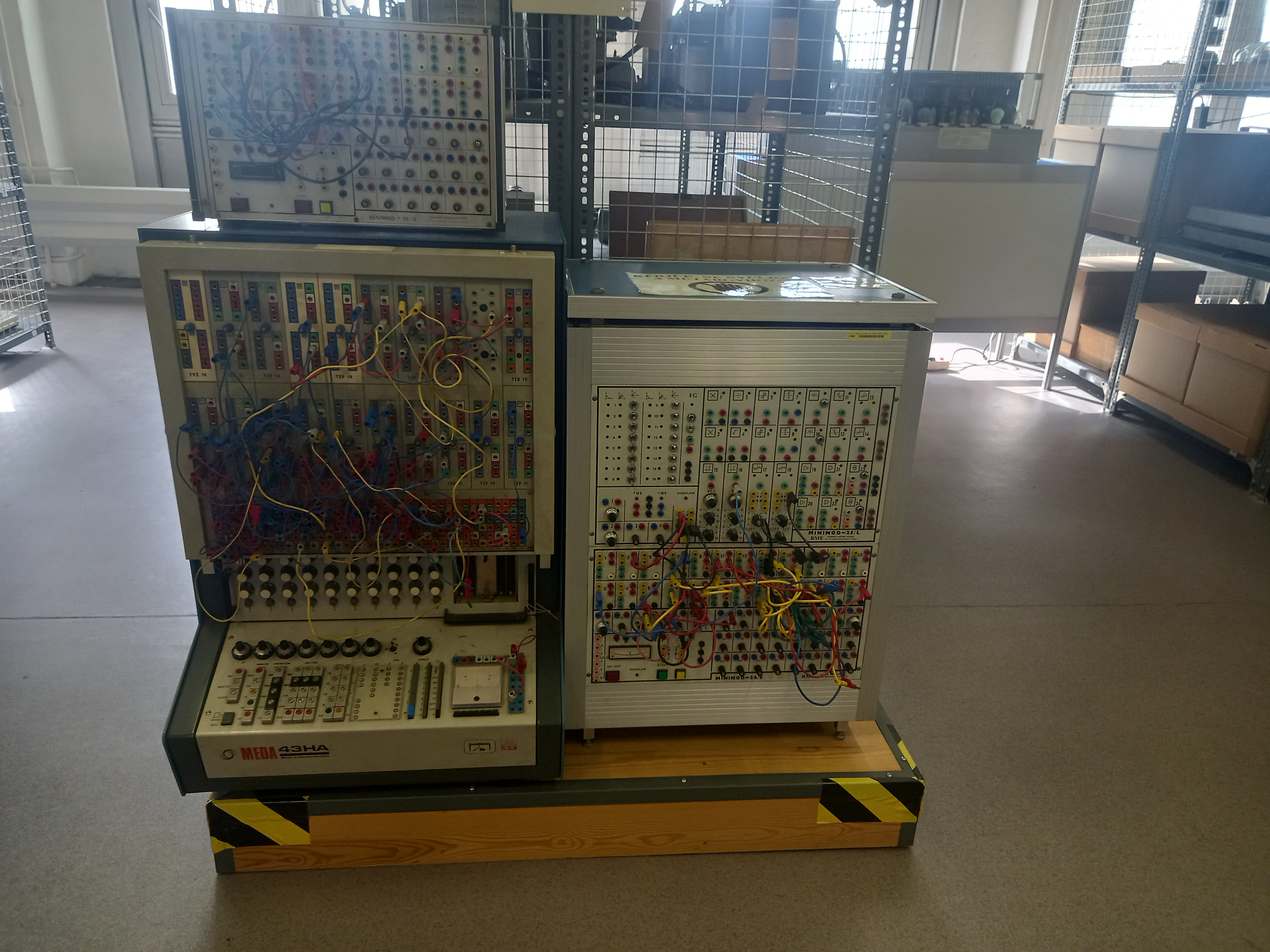
buherator
buheratorhttps://muzeuldecalculatoare.ro/2020/06/11/the-meda-43-analog-hybrid-computer/
Synacktiv
synacktiv@bird.makeupThe FastCGI library, mostly used in embedded equipment, was vulnerable for decades to an integer overflow over the IPC socket in 32-bits architecture. Check out how @shiropycatchown found it and exploited it for RCE!
https://www.synacktiv.com/en/publications/cve-2025-23016-exploiting-the-fastcgi-library
Mike Stone
mike@fosstodon.orgI know Chrome is the browser everybody loves to hate, but I think most would agree this would be very bad.
RE//verse Conference
REverseConf@infosec.exchangeIf you haven't seen it yet, make sure to check out another great RE//verse talk, Code reuse and attribution: best friends and worst enemies from Max 'Libra' Kersten (https://youtu.be/GPT1IksBkaI)