Posts
2573Following
630Followers
1418buherator
buheratorhttps://en.m.wikipedia.org/wiki/Razdan_(computer)
1dark1
1dark1@masto.hackers.townRemember the "You wouldn't steal a car" PSA? Turns out they pirated both the font AND the music. Exhibits:
font info: https://fontsinuse.com/uses/67480/piracy-it-s-a-crime-psa
pirated font embedded in this PDF: https://web.archive.org/web/20051223202935/http://www.piracyisacrime.com:80/press/pdfs/150605_8PP_brochure.pdf
and about the music: https://www.theransomnote.com/music/news/antipiracy-advert-music-was-stolen/
EDIT: more context re the composer, music, and royalties; the story is ofc more nuanced and apparently debunked: https://torrentfreak.com/sorry-the-you-wouldnt-steal-a-car-anti-piracy-ad-wasnt-pirated-170625/
#piracy #fonts #irony #hipocrisy #design #music #hashtag #download
Phrack
phrack@haunted.computer🐣 CRACKME RESULTS are OUT! 💥
Congrats to rt_saber for being so quick.
Kudos to all those who hammered CloudFlare hard.
https://github.com/phrackzine/crackme/blob/main/easter-2025/teaser-challenge-solution.md
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Another header bypass, this time a Citrix NetScaler nasty:
HD Moore
hdm@infosec.exchangeA few quick notes on the Erlang OTP SSHd RCE (CVE-2025-32433):
1. Cisco confirmed that ConfD and NSO products are affected (ports 830, 2022, and 2024 versus 22)
2. Signatures looking for clear-text channel open and exec calls will miss exploits that deliver the same payloads after the key exchange.
3. If you find a machine in your environment and can't disable the service, running the exploit with the payload `ssh:stop().` will shut down the SSH service temporarily.
William R. Messmer
wmessmer@bird.makeupIf you update WinDbg today (1.2504.15001.0), you might notice another icon in the View tab of the ribbon, one called "Parallel Stacks". While incredibly useful in its own right, this isn't just a parallel stacks view. It's the introduction of graph visualization for extensions!
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Kinda want a DirBuster style list of headers at this point, so many times, we see new CVEs stemming from headers with magical properties.
✧✦Catherine✦✧
whitequark@mastodon.socialShow content
OH: see, if you slit your wrists, at least you accomplish something in the end. unlike doing a CTF
/r/netsec
_r_netsec@infosec.exchangeFire In The Hole, We’re Breaching The Vault - Commvault Remote Code Execution (CVE-2025-34028) - watchTowr Labs https://labs.watchtowr.com/fire-in-the-hole-were-breaching-the-vault-commvault-remote-code-execution-cve-2025-34028/
buherator
buheratorhttps://0xdeadc0de.xyz/blog/cve-2025-1731_cve-2025-1732
SSH tunnels FTW!
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
Two Use After Free (UAF) vulnerabilities were discovered within Chrome’s Browser process by one of our researchers at SSD Labs:
https://ssd-disclosure.com/ssd-advisory-miracleptr-sandbox/
daniel:// stenberg://
bagder@mastodon.socialHow the CNA thing is working out for #curl
https://daniel.haxx.se/blog/2025/04/24/how-the-cna-thing-is-working-out/
buherator
buheratorhttps://blog.ret2.io/2025/04/23/pwn2own-soho-2024-diskstation/
buherator
buherator- Some rich text + images hosted online for the event
- Subscription form to get updates
- Stats about expected attendance
- ??? (this is my first time)
Edit: I don't charge anything for the event, so percentage commission can work.
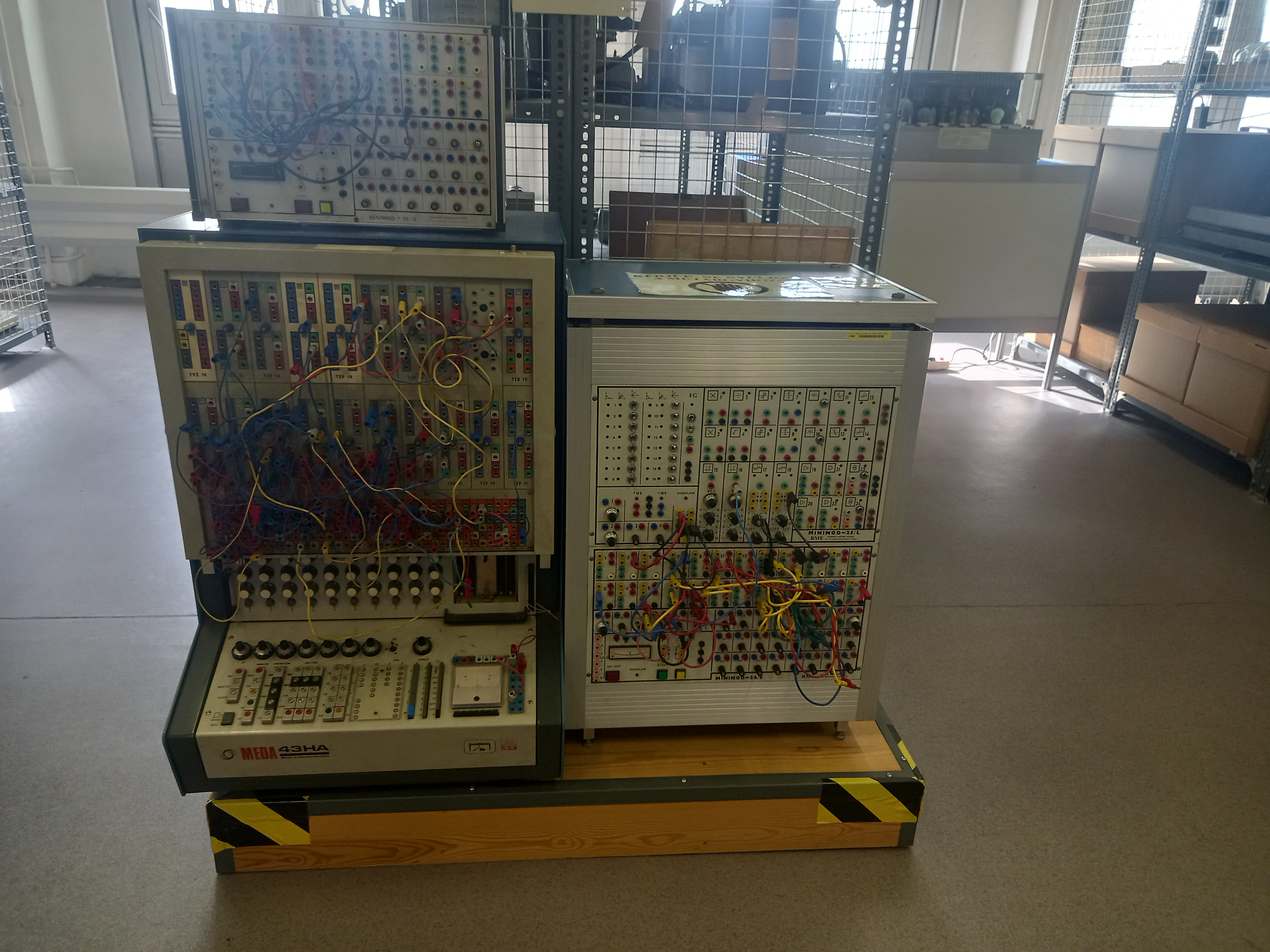
buherator
buheratorhttps://muzeuldecalculatoare.ro/2020/06/11/the-meda-43-analog-hybrid-computer/
Synacktiv
synacktiv@bird.makeupThe FastCGI library, mostly used in embedded equipment, was vulnerable for decades to an integer overflow over the IPC socket in 32-bits architecture. Check out how @shiropycatchown found it and exploited it for RCE!
https://www.synacktiv.com/en/publications/cve-2025-23016-exploiting-the-fastcgi-library
Mike Stone
mike@fosstodon.orgI know Chrome is the browser everybody loves to hate, but I think most would agree this would be very bad.
RE//verse Conference
REverseConf@infosec.exchangeIf you haven't seen it yet, make sure to check out another great RE//verse talk, Code reuse and attribution: best friends and worst enemies from Max 'Libra' Kersten (https://youtu.be/GPT1IksBkaI)
Alex Plaskett
alexjplaskett@bird.makeupRE//verse 2025 videos
https://www.youtube.com/playlist?list=PLBKkldXXZQhAW5QKjUQOUWaMAHAxDtgio