Posts
2558Following
630Followers
1411/r/netsec
_r_netsec@infosec.exchangeFire In The Hole, We’re Breaching The Vault - Commvault Remote Code Execution (CVE-2025-34028) - watchTowr Labs https://labs.watchtowr.com/fire-in-the-hole-were-breaching-the-vault-commvault-remote-code-execution-cve-2025-34028/
buherator
buheratorhttps://0xdeadc0de.xyz/blog/cve-2025-1731_cve-2025-1732
SSH tunnels FTW!
SSD Secure Disclosure
SSDSecureDisclosure@infosec.exchange🚨 New advisory was just published! 🚨
Two Use After Free (UAF) vulnerabilities were discovered within Chrome’s Browser process by one of our researchers at SSD Labs:
https://ssd-disclosure.com/ssd-advisory-miracleptr-sandbox/
daniel:// stenberg://
bagder@mastodon.socialHow the CNA thing is working out for #curl
https://daniel.haxx.se/blog/2025/04/24/how-the-cna-thing-is-working-out/
buherator
buheratorhttps://blog.ret2.io/2025/04/23/pwn2own-soho-2024-diskstation/
buherator
buherator- Some rich text + images hosted online for the event
- Subscription form to get updates
- Stats about expected attendance
- ??? (this is my first time)
Edit: I don't charge anything for the event, so percentage commission can work.
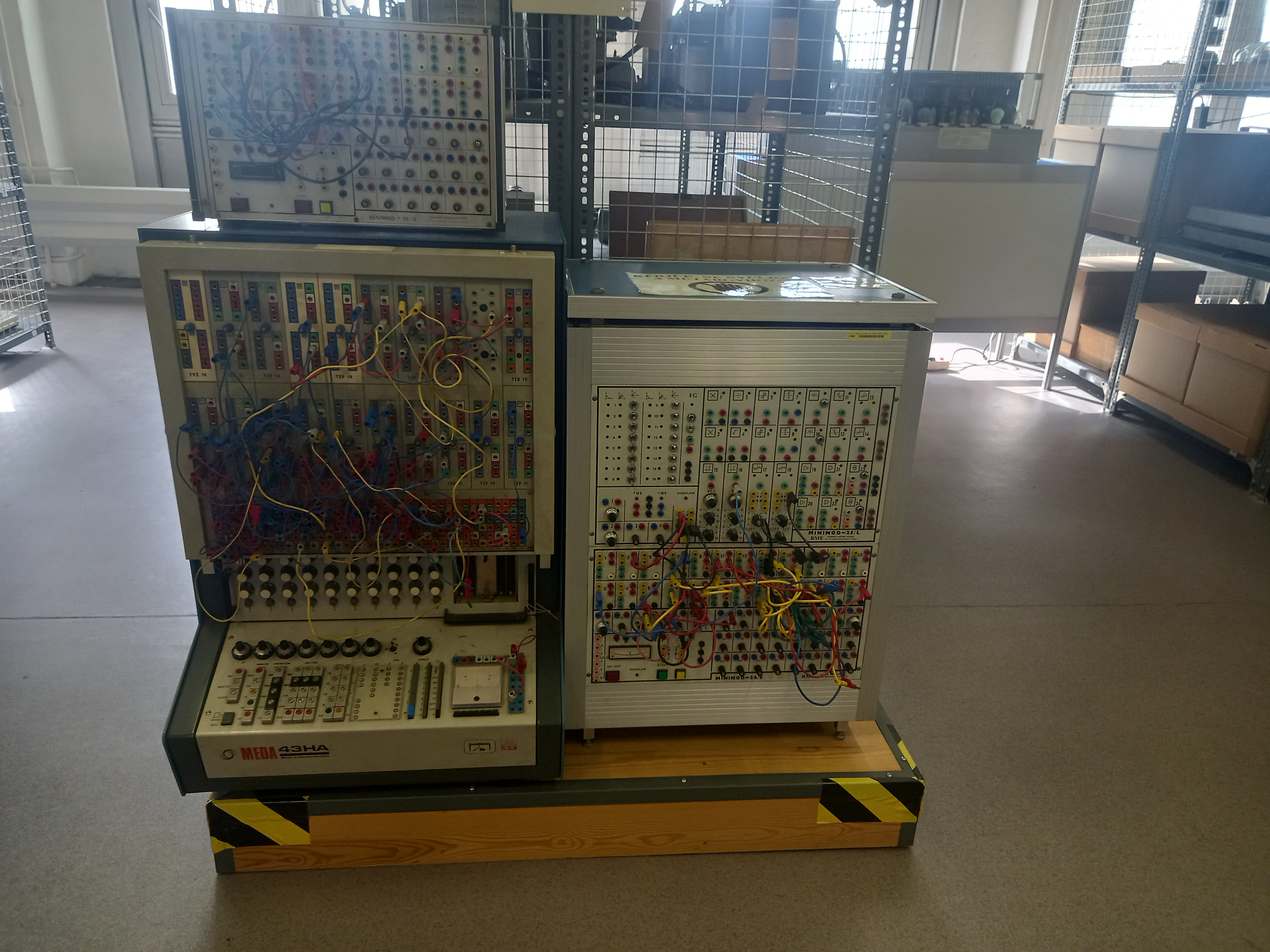
buherator
buheratorhttps://muzeuldecalculatoare.ro/2020/06/11/the-meda-43-analog-hybrid-computer/
Synacktiv
synacktiv@bird.makeupThe FastCGI library, mostly used in embedded equipment, was vulnerable for decades to an integer overflow over the IPC socket in 32-bits architecture. Check out how @shiropycatchown found it and exploited it for RCE!
https://www.synacktiv.com/en/publications/cve-2025-23016-exploiting-the-fastcgi-library
Mike Stone
mike@fosstodon.orgI know Chrome is the browser everybody loves to hate, but I think most would agree this would be very bad.
RE//verse Conference
REverseConf@infosec.exchangeIf you haven't seen it yet, make sure to check out another great RE//verse talk, Code reuse and attribution: best friends and worst enemies from Max 'Libra' Kersten (https://youtu.be/GPT1IksBkaI)
Alex Plaskett
alexjplaskett@bird.makeupRE//verse 2025 videos
https://www.youtube.com/playlist?list=PLBKkldXXZQhAW5QKjUQOUWaMAHAxDtgio
Ryan Castellucci 
ryanc@infosec.exchange
Coworker: ...and the IP address are compared with a string match.
Me: grinning manically
Coworker: Why are you looking at me like that?
Me: Open up a terminal and type ping 4.2.514 and hit enter.
Coworker: ...what's the fourth number?
Me: grin widens Just hit enter.
Coworker: WTF!?
testssl.sh 
testssl@infosec.exchange
testssl.sh 3.2.0 is finally out, see https://github.com/testssl/testssl.sh/releases/tag/v3.2.0 or just https://testssl.sh .
Changelog see https://github.com/testssl/testssl.sh/blob/3.2/CHANGELOG.md .
JA Westenberg
Daojoan@mastodon.socialGoogle is what happens when a system forgets why it was built but remembers how.
HN Security
hnsec@infosec.exchangeWe have identified some security vulnerabilities (CVE-2025-1731) in Zyxel USG FLEX H Series firewall appliances, that allow local users with access to a Linux OS shell to escalate privileges to root.
https://security.humanativaspa.it/local-privilege-escalation-on-zyxel-usg-flex-h-series-cve-2025-1731
#Zyxel #VulnerabilityResearch #CoordinatedDisclosure
Phrack
phrack@haunted.computer🐣 HAPPY EASTER FROM PHRACK 🐣
SPECIAL CrackMe Easter-2025 Challenge ONLINE NOW.
👉ZGlnICtzaG9ydCBlZ2c/Pz8/LnBocmFjay5vcmcgVFhU👈
Go find the EGG by solving the riddle :>
buherator
buheratorhttp://blog.quarkslab.com/auditing-moodles-core-hunting-for-logical-bugs.html
Kevin Beaumont
GossiTheDog@cyberplace.socialIf you heard about that hacking of the voices of traffic light crosswalks in the US recently, the root cause is the devices all had the password '1234' and an app to reprogram the devices was on the Apple app store.
https://www.theregister.com/2025/04/19/us_crosswalk_button_hacking/