Posts
3182Following
705Followers
1562
Tim (Wadhwa-)Brown 
timb_machine@infosec.exchange
Interesting links of the week:
Strategy:
* https://en.wikipedia.org/wiki/SIPOC - modelling systems with SIPOC
* https://www.thecvefoundation.org/ - the CVE foundation
* https://euvd.enisa.europa.eu/ - EU bug jail
* https://xntrik.wtf/aisa2024/ - @xntrik maps threats with https://threatcl.github.io/
* https://threatspec.org/ - the ThreatSpec
Threats:
* https://cloud.google.com/blog/topics/threat-intelligence/windows-rogue-remote-desktop-protocol - a novel phishing attack involving RDP
Detection:
* https://rulehound.com/rules - a single place to find interesting detection engineering ideas
Bugs:
* https://bugs.chromium.org/p/chromium/issues/detail?id=584535 - an 11 year old bug in every browser, still not dead!
Exploitation:
* https://silentsignal.github.io/BelowMI/ - memory management on System i courtesy of @buherator
* https://github.com/N1ckDunn/SOSLInjection/blob/main/SOSLInjection.pdf - Sal''esforce \o/
* https://github.com/N1ckDunn/DoubleFetch/blob/main/Double-FetchVulnerabilitiesInC.pdf - exploiting double fetch
Hard hacks:
* https://xairy.io/articles/thinkpad-xdci - emulating USB on a ThinkPad
* https://www.rtl-sdr.com/dragonos-lte-imsi-sniffing-using-the-lte-sniffer-tool-and-an-ettus-x310-sdr/ - build your own LTE sniffer
* https://blog.sesse.net/blog/tech/2025-04-05-10-57_cisco_2504_password_extraction.html - extracting passwords from Cisco WLC
* https://www.prizmlabs.io/post/remote-rootkits-uncovering-a-0-click-rce-in-the-supernote-nomad-e-ink-tablet - exploiting the Nomad e-ink tablet
Nerd:
* https://ukparliament.github.io/ontologies/meta/bots/ - UK parliamentary bots
* https://mwl.io/fiction/crime - Git drives people to murder
* https://changelog.complete.org/archives/10768-announcing-the-nncpnet-email-network - building a new mail protocol
Linux Kernel Security
linkersec@infosec.exchangeKernel-Hack-Drill: Environment For Developing Linux Kernel Exploits
Alexander Popov @a13xp0p0v published the slides from his talk at Zer0Con 2025. In this talk, he presented the kernel-hack-drill open-source project and showed how it helped him to exploit CVE-2024-50264 in the Linux kernel.
Slides: https://a13xp0p0v.github.io/img/Alexander_Popov-Kernel_Hack_Drill-Zer0Con.pdf
Project: https://github.com/a13xp0p0v/kernel-hack-drill
hrbrmstr 🇺🇦 🇬🇱 🇨🇦
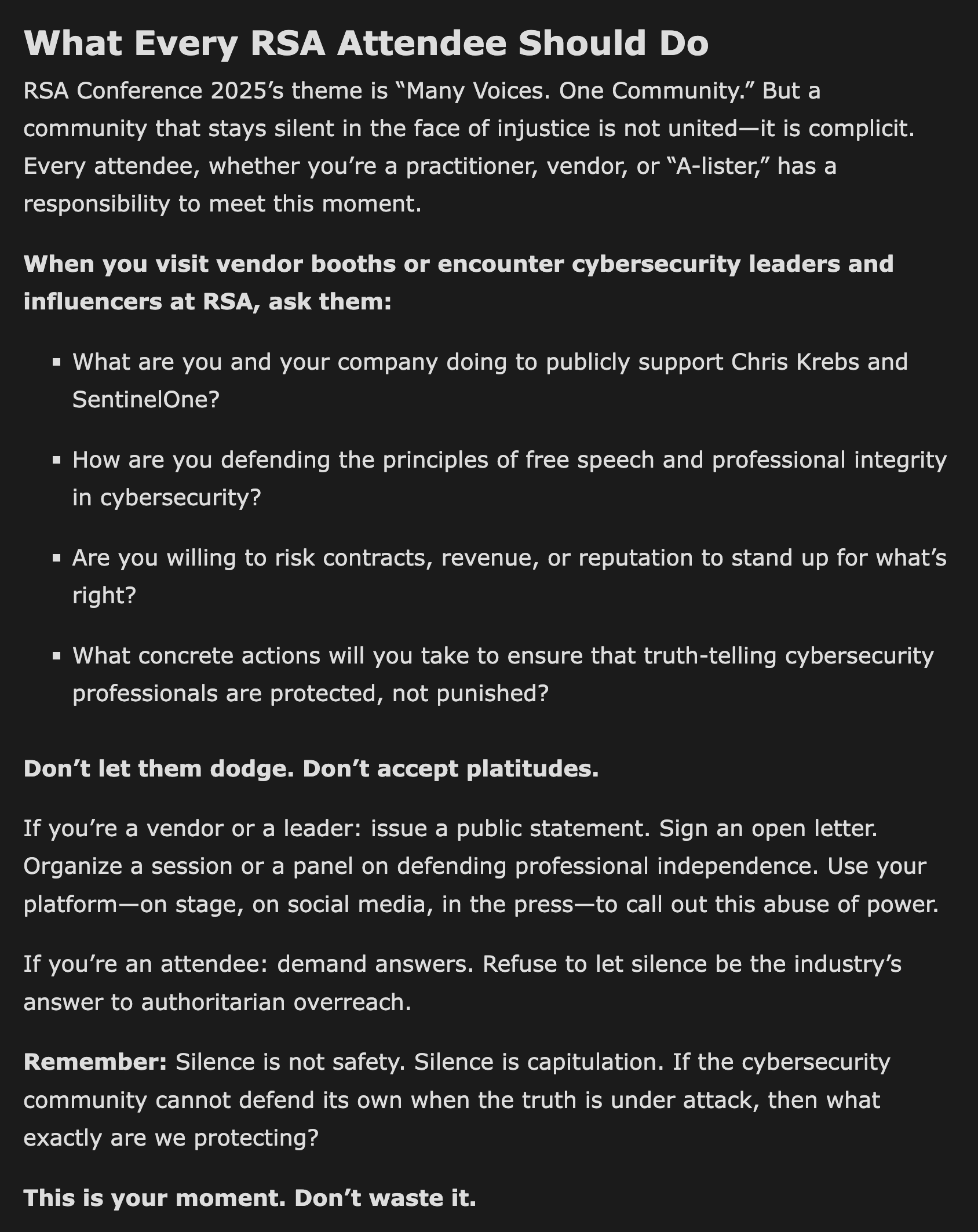
hrbrmstr@mastodon.socialDid a post on the personal blog (i.e., “the views expressed by me do not…blah blah”) — “Trump’s Retaliation Against Chris Krebs — and the Cybersecurity Industry’s Deafening Silence”.
Unlike most years, everyone attending RSA next week has a tangible, meaningful opportunity to make a difference.
Be better than the complicit cowards (humans & vendors) in our industry, speak up, & hold folks accountable.
Otherwise, “Many Voices. One Community” is just BS RSA marketing.
Prof. Emily M. Bender(she/her)
emilymbender@dair-community.social"Providers are pushed to spend less time caring for each patient as health systems move to reduce costs and increase revenue under the technological principle of maximal efficiency and output. But medicine was never intended to be another industrial complex."
This essay is beautiful and powerful.
alexanderkjall
alexanderkjall@mastodon.socialToday my #rust compiler told me "expected future, found a different future".
And I'm like: me too buddy, me too
buherator
buheratorhttps://ssd-disclosure.com/ssd-advisory-extract-double-free5-x-use-after-free7-x-8-x/
Can't find official identifiers for this, the GitHub advisory link is broken...
Jeff Atwood
codinghorror@infosec.exchangeMaybe you should build your own website https://neocities.org
Toby Kurien
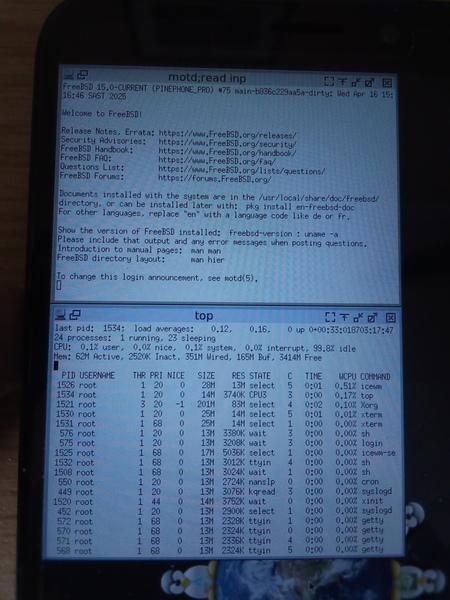
tobykurien@mastodon.socialI got #X11 running on the #PinephonePro under #FreeBSD ! Shown here running my favourite #icewm window manager. Super exciting! Now to get the touch screen working 😬
https://tobykurien.com/images/microblog/post-1744879274-0.jpg https://tobykurien.com/images/microblog/post-1744879274-1.jpg https://tobykurien.com/images/microblog/post-1744879274-2.jpg
HalvarFlake
HalvarFlake@mastodon.socialI never liked nu metal and I feel retrospectively justified by the fact that both Fred Durst and Kid Rock seem to be almost uniquely brain damaged even today.
CFG Bot 🤖
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/services/classifier.ts:1108 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/services/classifier.ts#L1108
function classifyTokenType(tokenKind: SyntaxKind, token?: Node): ClassificationType | undefined
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fservices%2Fclassifier.ts%23L1108&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fservices%2Fclassifier.ts%23L1108&colors=light
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250414-00/?p=111072
Oh, this is interesting (and a little scary)
tl;dr don’t use SSDs for long term, offline storage. The data degrades after as little as two years without the drives being powered up
buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/04/the-windows-registry-adventure-6-kernel.html
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
#CISA Warns of Credential Risks Tied to #Oracle Cloud Breach:
👇
https://securityonline.info/cisa-warns-of-credential-risks-tied-to-oracle-cloud-breach/
can't remember where I saw it but "Using AI in education is like using a forklift in the gym. The weights do not actually need to be moved from place to place. That is not the work. The work is what happens within you" is a solid quote
Mr. Bitterness
wdormann@infosec.exchangeGet your Apple updates folks.
https://support.apple.com/en-us/100100
CVE-2025-31200 and CVE-2025-31201 are being exploited ITW.
comex
comex@mas.toToday I learned something truly bizarre about Python.
What do you think this code does?
class C:
xs = [1]
ys = [1]
print([[None for y in ys] for x in xs])
Does it work and print [[None]]?
Or does it fail to access `xs` and `ys` because class scoping is weird?
Neither.
It successfully accesses `xs`, but then fails to access `ys`!
This is sort of documented (but not fully) under https://docs.python.org/3/reference/executionmodel.html#resolution-of-names.



 🏳️🌈🖖🏽
🏳️🌈🖖🏽