Posts
3368Following
712Followers
1580Jeff Atwood
codinghorror@infosec.exchangeMaybe you should build your own website https://neocities.org
Toby Kurien
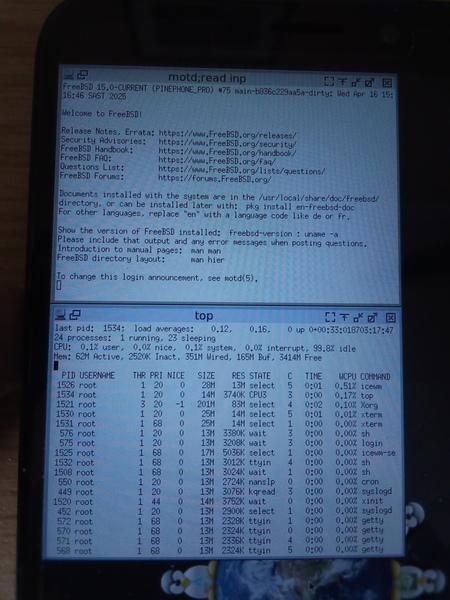
tobykurien@mastodon.socialI got #X11 running on the #PinephonePro under #FreeBSD ! Shown here running my favourite #icewm window manager. Super exciting! Now to get the touch screen working 😬
https://tobykurien.com/images/microblog/post-1744879274-0.jpg https://tobykurien.com/images/microblog/post-1744879274-1.jpg https://tobykurien.com/images/microblog/post-1744879274-2.jpg
HalvarFlake
HalvarFlake@mastodon.socialI never liked nu metal and I feel retrospectively justified by the fact that both Fred Durst and Kid Rock seem to be almost uniquely brain damaged even today.
CFG Bot 🤖
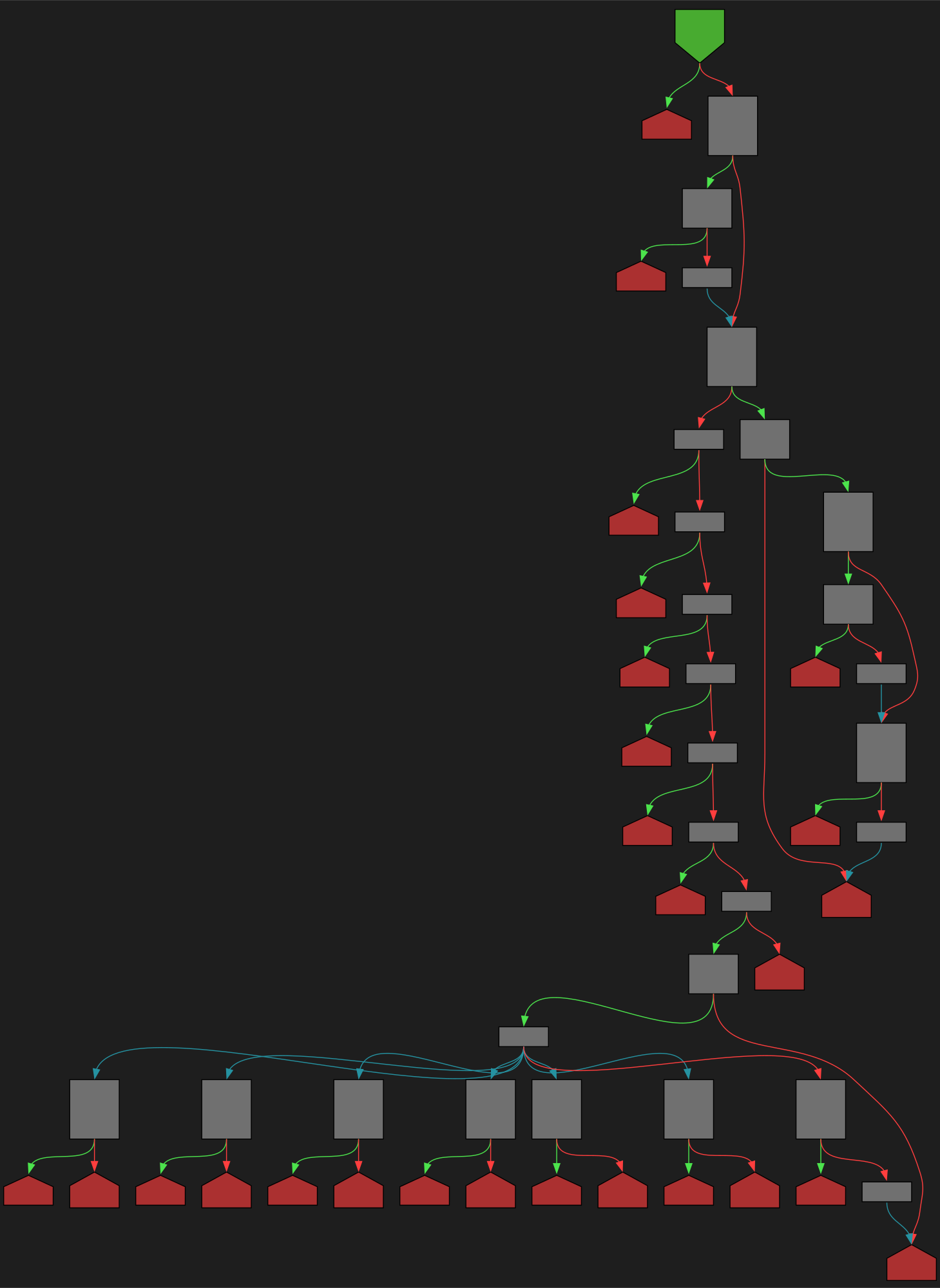
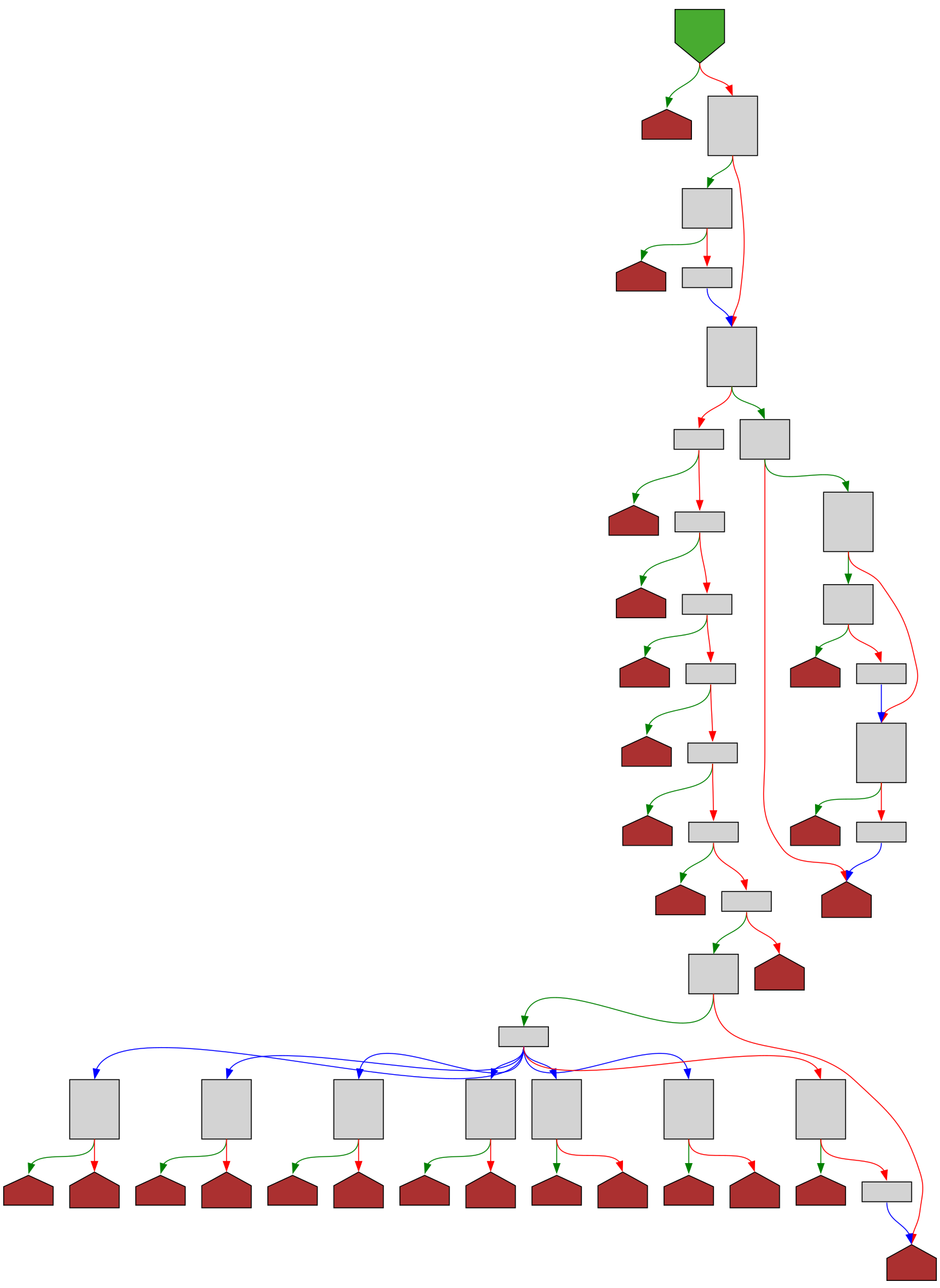
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/services/classifier.ts:1108 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/services/classifier.ts#L1108
function classifyTokenType(tokenKind: SyntaxKind, token?: Node): ClassificationType | undefined
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fservices%2Fclassifier.ts%23L1108&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fservices%2Fclassifier.ts%23L1108&colors=light
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250414-00/?p=111072
Oh, this is interesting (and a little scary)
tl;dr don’t use SSDs for long term, offline storage. The data degrades after as little as two years without the drives being powered up
buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/04/the-windows-registry-adventure-6-kernel.html
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
#CISA Warns of Credential Risks Tied to #Oracle Cloud Breach:
👇
https://securityonline.info/cisa-warns-of-credential-risks-tied-to-oracle-cloud-breach/
can't remember where I saw it but "Using AI in education is like using a forklift in the gym. The weights do not actually need to be moved from place to place. That is not the work. The work is what happens within you" is a solid quote
Mr. Bitterness
wdormann@infosec.exchangeGet your Apple updates folks.
https://support.apple.com/en-us/100100
CVE-2025-31200 and CVE-2025-31201 are being exploited ITW.
comex
comex@mas.toToday I learned something truly bizarre about Python.
What do you think this code does?
class C:
xs = [1]
ys = [1]
print([[None for y in ys] for x in xs])
Does it work and print [[None]]?
Or does it fail to access `xs` and `ys` because class scoping is weird?
Neither.
It successfully accesses `xs`, but then fails to access `ys`!
This is sort of documented (but not fully) under https://docs.python.org/3/reference/executionmodel.html#resolution-of-names.
Bonk Knob Records is very pleased to announce the release of "Not Bonk What I Call Wave: Remixes Vol 2"!
You can find it for streaming and download at all these fine places:
https://mirlo.space/bonk-knob-records/release/not-bonk
https://bonkwave.org/music/not-bonk-what-i-call-wave-remixes-vol2/
https://bonkknobrecords.bandcamp.com/album/not-bonk-what-i-call-wave-remixes-vol-2
https://bandwagon.fm/67fea099a706ef72dcec3978
Join us for the release party at 19:00 UTC / 20:00 BST / 21:00 CEST at https://party.bonkwave.org
buherator
buheratorhttps://github.com/erlang/otp/security/advisories/GHSA-37cp-fgq5-7wc2
Not much details and unfortunately I don't know much Erlang (yet), but this one seems pretty interesting!
CVE-2025-32433
Brett Cannon
brettcannon@fosstodon.orgThanks to @sbidoul , pip 25.1 will have a `pip lock` command that uses `pylock.toml`!
https://github.com/pypa/pip/pull/13213
pip-tools has started looking at if they can leverage it.
https://github.com/jazzband/pip-tools/issues/2124
pip-audit has support in 2.9.0 .
https://pypi.org/project/pip-audit/
@frostming has a PR for 'packaging' to add the required marker support (I assume for PDM support). It's getting really close to being merged.
https://github.com/pypa/packaging/pull/888
I'm a bit relieved there's uptake of pylock.toml already!
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.4 vs. iOS 18.4.1 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_4_22E240__vs_18_4_1_22E252/README.md
Adam Shostack 

adamshostack@infosec.exchange
The most important part of CVE is not the unique number, but the funding and expertise to run a credible program that assigns a unique number. The unique number was the center of what Dave Mann called a “concordance,” and I believe this is subtle but crucial: The value of CVE is not as a database, but as a stable way to cross-reference between databases and other tools. Dave and I have had many conversations about books having an ISBN, a UPC code, a Dewey number and a Library of Congress number. They serve different goals, and are managed by different groups.
I mention the books because assigning unique numbers in a stable way is harder than you'd expect.
0patch
0patch@infosec.exchangeMicropatches Released for URL File NTLM Hash Disclosure Vulnerability (Unknown CVE)
Alan Coopersmith
alanc@fosstodon.orgToday is Oracle's quarterly Critical Patch Update release day, so for #OracleSolaris we have released updates for 11.4 & 11.3, and patches for 10.
11.4: https://blogs.oracle.com/solaris/post/announcing-oracle-solaris-114-sru80
11.3: https://community.oracle.com/mosc/discussion/4583990/solaris-11-3-36-34-0-has-been-released-on-my-oracle-support
10: https://community.oracle.com/mosc/discussion/4584292/announcing-oracle-solaris-10-quarterly-patch-release-april-2025
For info on the security fixes in those releases, see the Oracle Systems Risk Matrix in the April 2025 CPU Bulletin at https://oracle.com/security-alerts/cpuapr2025.html#AppendixSUNS and the Oracle Solaris Third Party Bulletin for April 2025 at https://oracle.com/security-alerts/bulletinapr2025.html .
 🏳️🌈🖖🏽
🏳️🌈🖖🏽