Posts
3377Following
712Followers
1579Orhun Parmaksız 👾
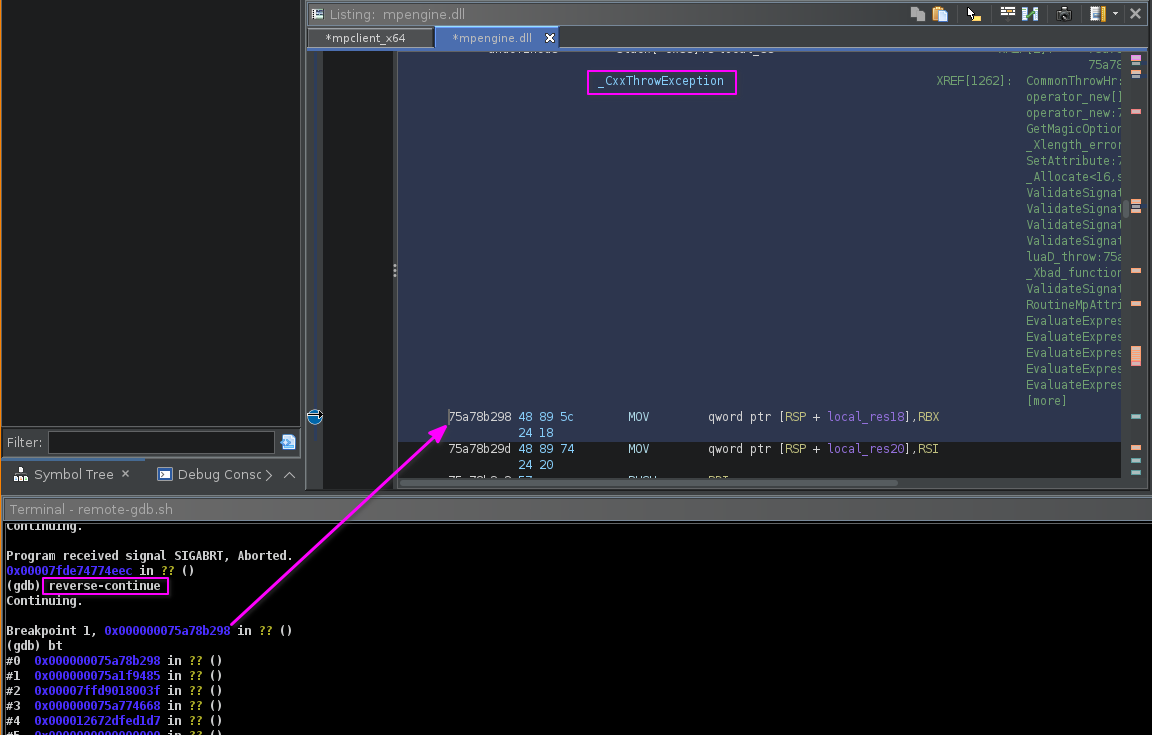
orhun@fosstodon.orgDebugging in the terminal isn't difficult anymore 🔥
🛠️ Meet **heretek** — A gdb TUI dashboard
🐛 Supports viewing stack, registers, instructions, hexdump & more!
🚀 Works with remote targets seamlessly (no gdbserver!)
🦀 Written in Rust & built with @ratatui_rs
⭐ GitHub: https://github.com/wcampbell0x2a/heretek
#rustlang #ratatui #tui #gdb #debugging #terminal #linux #commandline
/r/netsec
_r_netsec@infosec.exchangeShopware Unfixed SQL Injection in Security Plugin 6 https://www.redteam-pentesting.de/en/advisories/rt-sa-2025-001/
Doyensec
doyensec@infosec.exchangeRPGPGM
rpgpgm@mastodon.socialNew release #IBMi 7.6 is announced! This will be updated as I find more information.
#IBMi #rpgpgm #IBMChampion
https://www.rpgpgm.com/2025/04/version-76-announced.html
pancake 
pancake@infosec.exchange
Git turned 20 yesterday. I feel old. Again https://github.blog/open-source/git/git-turns-20-a-qa-with-linus-torvalds/
buherator
buheratorA deep dive into modern Windows Structured Exception Handler (SEH) [Nov. 2024.]
https://blog.elmo.sg/posts/structured-exception-handler-x64/
buherator
buheratorFun fact: you can attach to the gdbserver exposed by #rr and do #TimeTravelDebugging from #Ghidra :)
UX is similar to ret-sync.
CarveHerName
CarveHerName@mstdn.social#OnThisDay, 8 Apr 1959, Mary K Hawes initiates a project to create the first universal programming language for computers used by businesses and government. Grace Hopper led the team that then created COBOL. Some mainframes are still using it.
#WomenInHistory #OTD #History #WomensHistory #WomenInSTEM #Histodons
DEF CON
defcon@defcon.socialSpring has sprung. Birds are singing, flower buds are budding and the #DEFCON33 website is open for business. Bookmark https://defcon.org/html/defcon-33/dc-33-index.html for all the latest info on everything #DC33. August will be here before you know it and you’ll want to be in the loop as things develop.
Stay in touch, and we’ll see you at #defcon.
CFG Bot 🤖
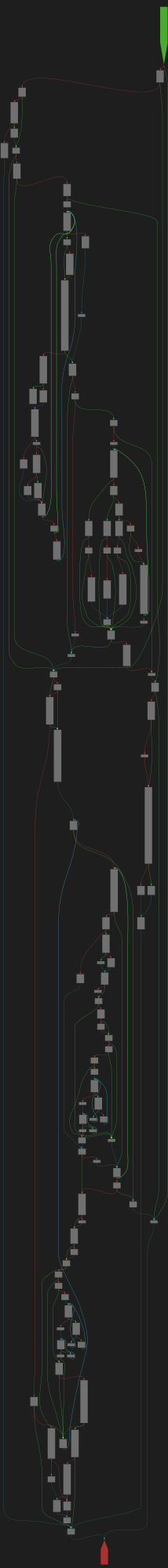
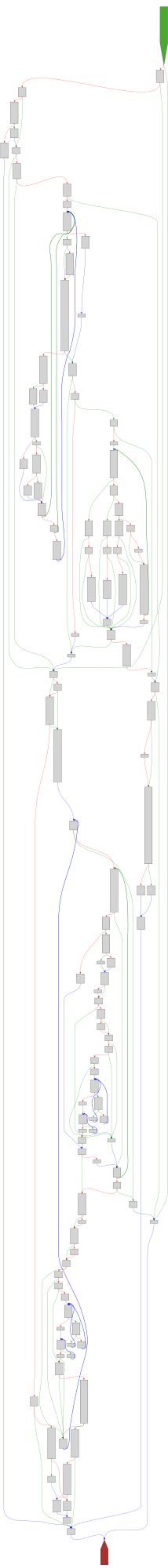
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1a737c
match
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1a737c.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1a737c.json&colors=light
buherator
buheratorApparently Bugcrowd was not pwned, they just try to roll out mandatory MFA:
https://www.bugcrowd.com/blog/bugcrowd-security-update-password-reset-and-mfa-requirement/
Scientists still struggle to come up with a way how this information could be included in the password reset mails they sent out, we’ll keep you updated about any breakthroughs!
h/t @raptor
buherator
buheratorhttps://cyberinsider.com/toddycat-hackers-exploit-eset-antivirus-flaw-to-bypass-windows-security/
Spoiler: version.dll strikes again...
Robin Green
fatlimey@mastodon.gamedev.placeInteresting talk on designing low-bit floating point number systems. Imagine you have 6-bits, using IEEE754 would you want to waste 6 of your codes for different NaNs? Do you really need two zeros? How about adding ±∞ or does saturating to ±FLT_MAX work for you use case? You can upconvert to Binary32 or Binary64 to do math operations, but which one gives you the better conversion when re-packing back down to 6-bits?
IEEE working group P3109 has the goods.
mei
mei@donotsta.recpresser
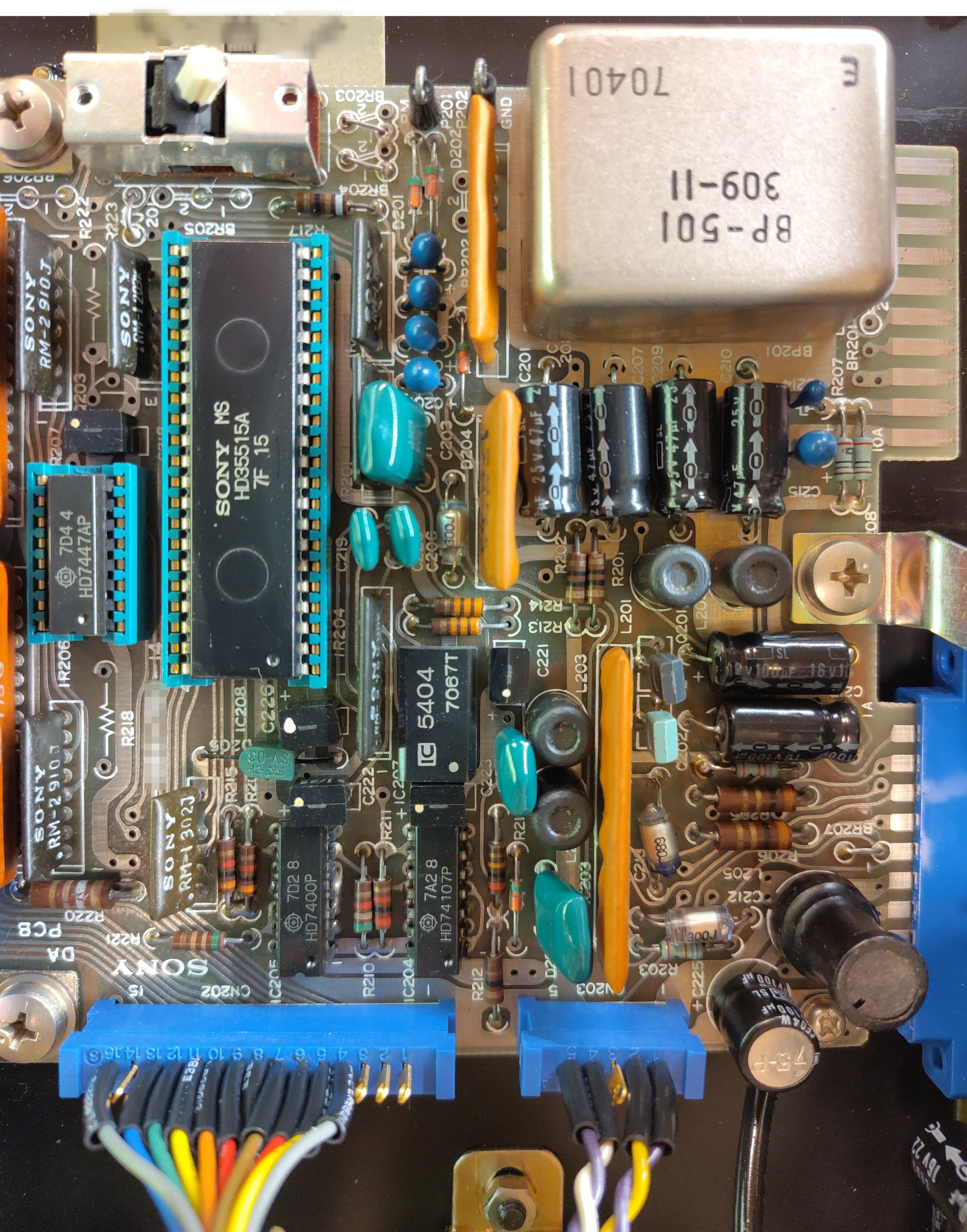
cccpresser@chaos.socialHere is another #NameThatWare challenge. While I know what the device does, I was not able to identify much of the components on the circuit board. Quite sure I could not solve this challenge myself.
So far I have not been able to identify
* the microcontroller
* the silver can on the top right
* any datecode
As always, please write down your deductions and guesses behind a CW to not spoil it for others.
Tim Blazytko
mr_phrazer@infosec.exchangeAt @recon , @nicolodev and I discuss the current state of MBA (de)obfuscation and their applications. We’ll also introduce a new #BinaryNinja plugin for simplifying MBAs in the decompiler.
Details: https://cfp.recon.cx/recon-2025/featured/
I'll also give a training: https://recon.cx/2025/trainingSoftwareDeobfuscationTechniques.html