Posts
3182Following
705Followers
1562mei
mei@donotsta.recpresser
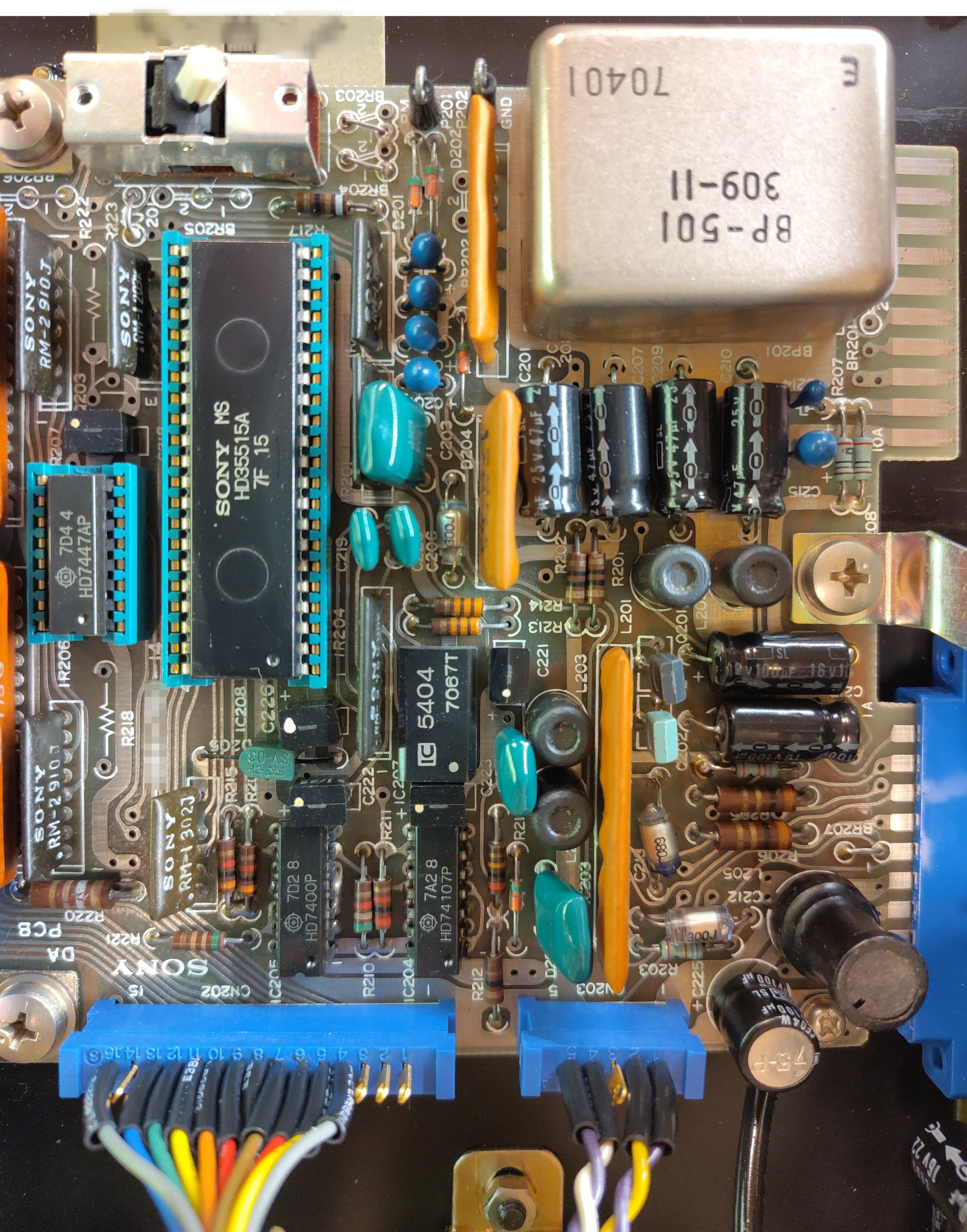
cccpresser@chaos.socialHere is another #NameThatWare challenge. While I know what the device does, I was not able to identify much of the components on the circuit board. Quite sure I could not solve this challenge myself.
So far I have not been able to identify
* the microcontroller
* the silver can on the top right
* any datecode
As always, please write down your deductions and guesses behind a CW to not spoil it for others.
Tim Blazytko
mr_phrazer@infosec.exchangeAt @recon , @nicolodev and I discuss the current state of MBA (de)obfuscation and their applications. We’ll also introduce a new #BinaryNinja plugin for simplifying MBAs in the decompiler.
Details: https://cfp.recon.cx/recon-2025/featured/
I'll also give a training: https://recon.cx/2025/trainingSoftwareDeobfuscationTechniques.html
buherator
buherator- Welcome to the #Bureaucracy! You owe us some money, but fear not, you can easily pay it with our very modern VPOS!
- Really? There’s no new items in my online mailbox you usually use.
- Oh we sent this request in a (non-certified) paper letter to the other side of the city.
- commuting Got the letter, what’s the URL for the VPOS?
- Oh we won’t tell you that…
- Nvm, I just googled it, what’s next?
- You have to choose the code that corresponds to your debt!
- Is the code in the letter you sent me?
- No, but we gave each code a title, multiple of which are very similar to what you want to pay for.
- googling OK, I found a page that matches the codes with account numbers and you did sent me the an account number so I think I found the right code!
- (mumbbling Damn it we have to get that page down!)
- So you actually sent me two letters with different sums, which one is correct?
- crickets
- I’ll just pay the bigger amount, just in case click pay Transaction rejected!
- Banks these days, huh?
- Let’s retry…
- You can’t just retry, the form you filled out is invalid now! But we can automatically create you a copy.
- This “copy” has a NULL where the original had some unique ID, are you sure this is right?
- We’re sure it’s fine…
- Alright, click pay
- UNRECOVERABLE ERROR
clownpertino - A simple macOS debugger detection trick.
Pretty sure someone using this one since it's so easy but I haven't seen it in the wild. Just some Monday lulz while the stock markets burn :P
Zack Whittaker
zackwhittaker@mastodon.socialNew, by me: Someone hacked into the Everest ransomware gang's dark web leak site and defaced it.
"Don't do crime CRIME IS BAD," Everest's site now reads.
https://techcrunch.com/2025/04/07/someone-hacked-everest-ransomware-gang-dark-web-leak-site
buherator
buheratorhttps://hackaday.com/2025/04/06/command-and-conquer-ported-to-the-pi-pico-2/
It may be Monday, but today is also National No Housework Day, National Beer Day and also International Beaver Day. Do with that information what you will. 
Zhuowei Zhang
zhuowei@notnow.devI wondered how OSS-Fuzz fuzzes Woff2 fonts with Brotli compression.
The answer seems to be… brute force.
https://issues.oss-fuzz.com/issues/42478986 shows a sample WOFF2 fuzzed font, and it contains a valid Brotli stream.
So oss-fuzz must be fuzzing raw WOFF2 fonts without a special mutator.
Yet it works: OSS-Fuzz coverage shows 93% coverage on the WOFF2 decoder:
It works, but the uncovered lines are the error lines… As if there’s not enough executions to actually hit the error cases…
looking at the execution coverage:
71.2k makes it to woff2_open_font 57.3k makes it to woff2_decompress 14.7k makes it to reconstruct_font 8.68k makes it to the end of woff2_open_font
eShard
eshard@infosec.exchangeWe emulated iOS 14 in QEMU.
This is how we did it: https://eshard.com/posts/emulating-ios-14-with-qemu
#reverseengineering #cybersecurity #iosdev #ios #apple #devops
aki-nyan
lethalbit@chaos.socialI look away for 5 minutes and Annie goes and makes herself home in the vacant spot in the rack,
Little baby
Slashdot 
slashdot@mastodon.cloud
Were Still More UK Postmasters Also Wrongly Prosecuted Over Accounting Bug? https://news.slashdot.org/story/25/04/06/0221239/were-still-more-uk-postmasters-also-wrongly-prosecuted-over-accounting-bug?utm_source=rss1.0mainlinkanon
hackaday
hackaday@hackaday.socialBen Eater vs. Microsoft BASIC
https://hackaday.com/2025/04/05/ben-eater-vs-microsoft-basic/
CFG Bot 🤖
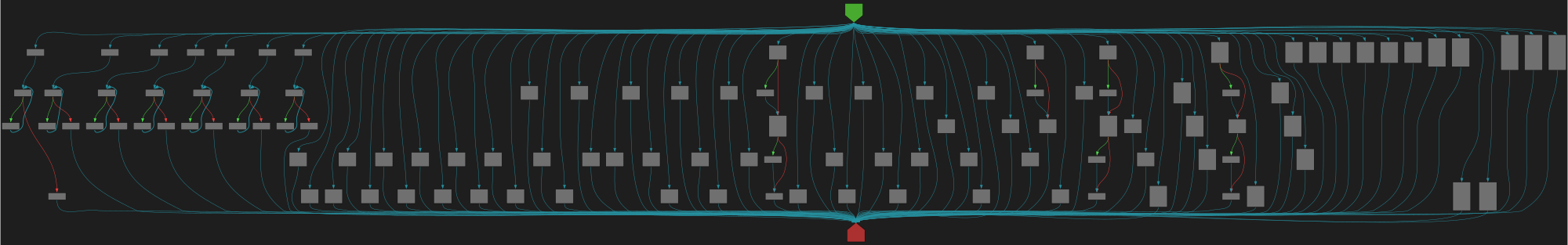
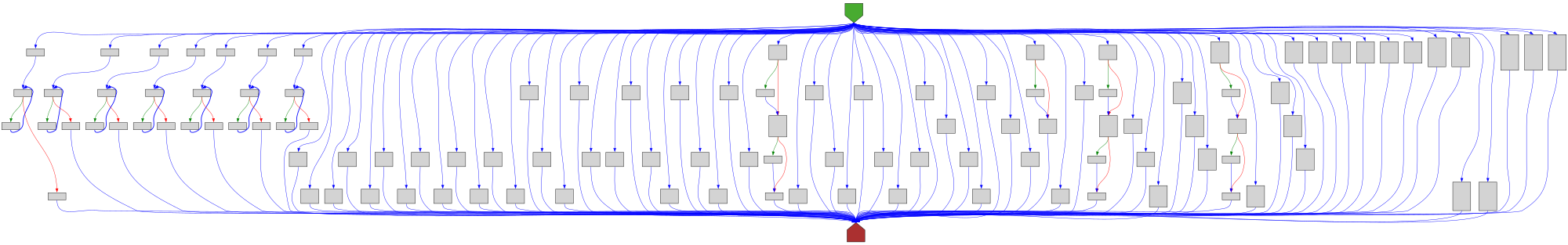
cfgbot@mastodon.socialProject: golang/go https://github.com/golang/go
File: src/cmd/fix/fix.go:54 https://github.com/golang/go/blob/refs/tags/go1.23.4/src/cmd/fix/fix.go#L54
func walkBeforeAfter(x any, before, after func(any))
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ffix%2Ffix.go%23L54&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fgolang%2Fgo%2Fblob%2Frefs%2Ftags%2Fgo1.23.4%2Fsrc%2Fcmd%2Ffix%2Ffix.go%23L54&colors=light
Craig Newmark
craignewmark@mastodon.socialBe like Ronin...
"Hero rat sets Guinness World Record for detecting landmines"
https://taskandpurpose.com/tech-tactics/ronin-landmines-rat-guinness-world-record/
via @TaskandPurpose
 radare
radare 
radareorg@infosec.exchange
Work in progress JNI helper plugin for #radare2 https://github.com/evilpan/jni_helper/tree/master/r2 #android #java #reverseengineering
buherator
buheratorhttps://gitlab.gnome.org/GNOME/yelp/-/issues/221
"Yelp, the GNOME user help application, allows help documents to execute
arbitrary JavaScript. A malicious help document may exfiltrate user files
to a remote server. A malicious website may download a help document
without user intervention, then trick the user into opening a ghelp URL
that references the help document. This notably requires the attacker to
guess the filesystem path of the downloaded help document."
And we just discussed old-school .HLP exploits the other day...
#EnoughEyeballs