Posts
3182Following
705Followers
1562CFG Bot 🤖
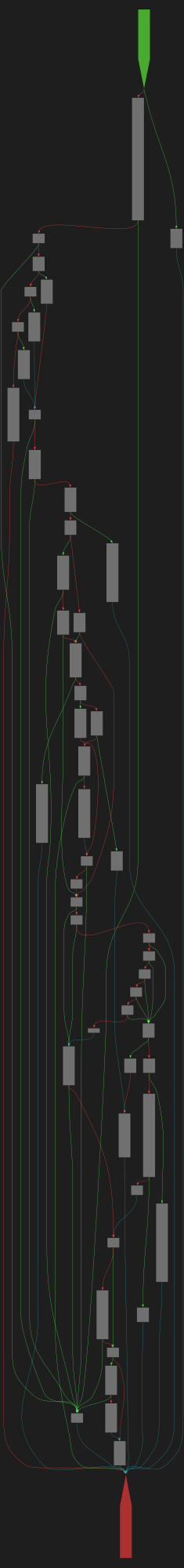
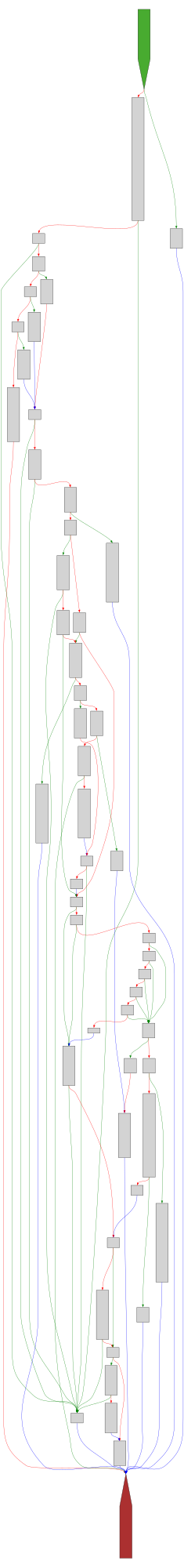
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 0063a0a0
rsa_ossl_private_encrypt
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0063a0a0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F0063a0a0.json&colors=light
Mr. Bitterness
wdormann@infosec.exchangeIvanti CVE-2025-22457 is being exploited ITW.
https://forums.ivanti.com/s/article/April-Security-Advisory-Ivanti-Connect-Secure-Policy-Secure-ZTA-Gateways-CVE-2025-22457
Per Mandiant:
We assess it is likely the threat actor studied the patch for the vulnerability in ICS 22.7R2.6 and uncovered through a complicated process, it was possible to exploit 22.7R2.5 and earlier to achieve remote code execution.
Gee, who could have imagined that attackers are looking at patches? 🤔
1) This apparently was silently fixed for ICS in 22.7R2.6, as the fix for this was released in February. Per Ivanti, the buffer overflow was considered a "product bug" at that time, as opposed to a vulnerability. Ivanti Policy Secure and ZTA gateways are expected to receive a patch in late April.
2) The advisory still conveys the magical thinking if if your device shows signs of compromise, then you should perform a "factory reset." This is magical in that the ICT won't catch a compromise nor will the "factory reset" reset to factory condition if the attacker is bothering to try.
While Mandiant also parrots the magical thinking of running the ICT tool, which I guess is the best advice if you're not going to throw the device in the trash since there isn't an official integrity checking tool that is sound, they do throw out a tidbit of:
... and conduct anomaly detection of client TLS certificates presented to the appliance.
Bets on whether CVE-2025-22457 is an overflow in the handling of a field in a client-provided certificate? 😂
/r/netsec
_r_netsec@infosec.exchangeSuspected China-Nexus Threat Actor Actively Exploiting Critical Ivanti Connect Secure Vulnerability (CVE-2025-22457) https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-exploiting-critical-ivanti-vulnerability/
exploits.club
exploitsclub@bird.makeup66 weeks in a row...whatchu know about it 📰 THE vuln research newsletter out NOW
MCPGhidra from @lauriewired
@u1f383 talks DirtyCOW
Mitigations galore with @standa_t and @slowerzs
XSS -> RCE with @chudypb and @watchtowrcyber
+ Jobs and MORE 👇
buherator
buheratorhttps://www.openwall.com/lists/oss-security/2025/04/03/1
"Our belief is that it's highly impractical to exploit on 64-bit systems
where xz was built with PIE (=> ASLR), but that on 32-bit systems,
especially without PIE, it may be doable."
buherator
buheratorhttps://www.youtube.com/watch?v=ce0bXORSMX4
/r/netsec
_r_netsec@infosec.exchangeFrida 16.7.0 is out w/ brand new APIs for observing the lifecycles of threads and modules, a profiler, multiple samplers for measuring cycles/time/etc., MemoryAccessMonitor providing access to thread ID and registers, and more 🎉 https://frida.re/news/2025/03/13/frida-16-7-0-released/
The Peter Pan of Nerdery™ 🇦🇺
dhry@mastodon.social#NotepadPlusPlus v8.7.9 released.
The author is totally my spirit animal.
#arm64 #windows #freeware
https://notepad-plus-plus.org/news/v879-we-are-with-ukraine/ https://notepad-plus-plus.org/news/v879-we-are-with-ukraine/
Edit: we is fedi-trending, guyzz! 🤗
buherator
buheratorhttps://projectblack.io/blog/zendto-nday-vulnerabilities/
#NoCVE
K. Ryabitsev-Prime 🍁
monsieuricon@social.kernel.orgWe'll be rolling it out on lore.kernel.org and git.kernel.org in the next week or so.
cts🌸
gf_256@bird.makeupIn 2020, I solved a gnarly reverse engineering challenge in PlaidCTF. Only 9 teams solved.
It's a huge pile of Typescript. Everything is named after a fish.
The catch? There's no code, only types. How do they perform computation using just the type system?
(Spoiler: Circuits!)
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.4 vs. iOS 18.5 beta 1 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_4_22E240__vs_18_5_22F5042g/README.md
Binary Ninja
binaryninja@infosec.exchangeWe've been teasing it for a while, but the full features of Firmware Ninja are officially available on dev and will be in the 5.0 release later this month! Doing reverse engineering of embedded firmware? Check out how FWN can make your life better:
Bastian Greshake Tzovaras
gedankenstuecke@scholar.socialHow can one engage in algorithmic sabotage to poison "AI" scrapers looking for images when one is running a static website? Thanks to @pengfold, I've implemented a quick and easy way for my own blog:
https://tzovar.as/algorithmic-sabotage-ii/
Also thanks to @rostro & @asrg for the pointers and discussion!
buherator
buheratorhttps://tandasat.github.io/blog/2025/04/02/sss.html
buherator
buheratorIts answer ("Tree-sitter grammars are used for syntax highlighting") was wrong, while pointed to the correct SO answer (pointing to Linguist) as a reference:
https://stackoverflow.com/questions/8886360/what-javascript-syntax-highlighter-does-github-use
Ryan Lee Sipes ⚡🦅
ryanleesipes@mastodon.socialIt's time to explain Thunderbird's relationship to Mozilla again.
Thunderbird is in its own legal entity - MZLA Technologies and is governed in part by a Community Council elected by and from our open source contributors.
Thunderbird is currently 100% donation-funded. We do not receive any money outside what our donors give us.
This is good for Thunderbird and makes us unique. Our whole structure only works to serve the interests of our users and contributor community.
hackaday
hackaday@hackaday.social70 DIY Synths on One Webpage
https://hackaday.com/2025/04/02/70-diy-synths-on-one-webpage/