Posts
2570Following
627Followers
1397buherator
buheratorSince the loader needed some debugging I ended up figuring out how to load the Linux-native mpclient into #Ghidra's debugger and use it to debug the PE module too:
https://github.com/v-p-b/loadlibrary/blob/x64_waffle/GHIDRA.md
This can spare an IDA license and performing dark arts with awk and gas...which is actually pretty badass, so if you want to keep doing that without IDA here's a Ghidra script too:
https://gist.github.com/v-p-b/c7d934234297158047b678f655c7d99f
buherator
buheratorhttps://exim.org/static/doc/security/CVE-2025-30232.txt
(was ZDI-CAN-26250)
buherator
buheratorhttps://bughunters.google.com/blog/6496960683835392/android-vrp-announces-autorepro-1-000-bonus-for-eligible-submissions
Daily Azure Shit
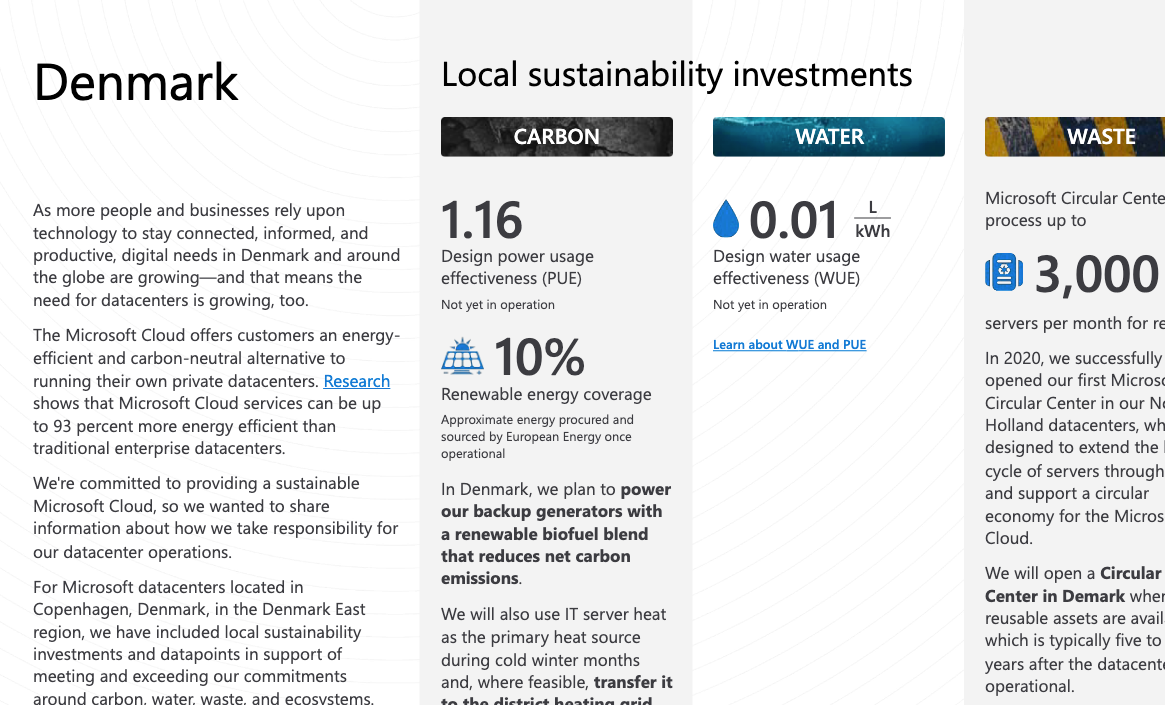
azureshit@mastodon.socialDay 421. Following up on the no longer available sustainability fact sheets of #Azure data centers from day 420, we have added those that we know of to the Internet Archive.
lizzy 

lizzy@social.vlhl.dev
"am i misunderstanding what the code is doing or is whoever wrote this really fucking stupid"
daniel:// stenberg://
bagder@mastodon.socialThe AI bots that desperately need OSS for code training, are now slowly killing OSS by overloading every site.
The curl website is now at 77TB/month, or 8GB every five minutes.
daniel:// stenberg://
bagder@mastodon.socialYou can help #curl by testing this final release candidate, rc3, before the real release happens next week:
abadidea
0xabad1dea@infosec.exchangean ominous I-am-under-NDA-coded warning to immediately uninstall atop has been posted by a reputable tech blogger. https://rachelbythebay.com/w/2025/03/25/atop/
buherator
buheratorhttps://binary.ninja/2025/03/25/default-browser-upcd.html
buherator
buheratorhttps://starlabs.sg/blog/2025/03-cimfs-crashing-in-memory-finding-system-kernel-edition/
M. J. Fromberger
creachadair@phire.place"Is that free as in beer, or free as in freedom?"
"It's free as in use-after."
Andrea Allievi
aall86@bird.makeuphttps://www.andrea-allievi.com/blog/a-minikvm-to-rule-all-machines-remotely/ Finally after hours and hours of assembling a YouTube video... MiniKvm 1.0 is there :-) Have fun and let me know if you find it useful...
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeWhen I was a student, I read a lot about how Silicon Valley companies were looking for 'problem solvers' rather than people with experience with specific technologies. At the time, this struck me as odd because problem solvers are not rare. Most people can solve a problem if you explain it to them. Indeed, the lesson from most of the formal verification classes was that a sufficiently detailed description of a problem is indistinguishable from a solution to that problem.
The real rare skill is working out which problems are the right ones to solve. Without that, you keep falling down dead-end rabbit holes and chasing local optima.
Everything I've seen in the last decade or so indicates what happens when problem solvers end up in senior leadership positions. You get companies that are great at solving completely the wrong problems.
This is outrageous. Where are the armed men who come in to take the spammers away? Where are they? This kind of behavior is never tolerated in Cascadia. You phish like that they put you in jail. Right away. No trial, no nothing. Cloudflare sites, we have a special jail for Cloudflare sites. You use QR codes: right to jail. You are domain squatting: right to jail, right away. Too many URL parameters: jail. Too few: jail. You are asking for gift cards, Monero, Bitcoin: you right to jail. You text a journalist? Believe it or not, jail. You receive a text, also jail. Send, receive. You use a hyphen in your domain name, believe it or not, jail, right away. We have the best users in the world because of jail.
Jonty Wareing
jonty@chaos.socialPlease remember that what you see on social media is what people choose to present, not an accurate representation of their life. Few people post about the horror.
Don't put off seeing friends because "they're having fun" or "they're busy" and "you'll see them later". You do not know that any of these things are true.
CFG Bot 🤖
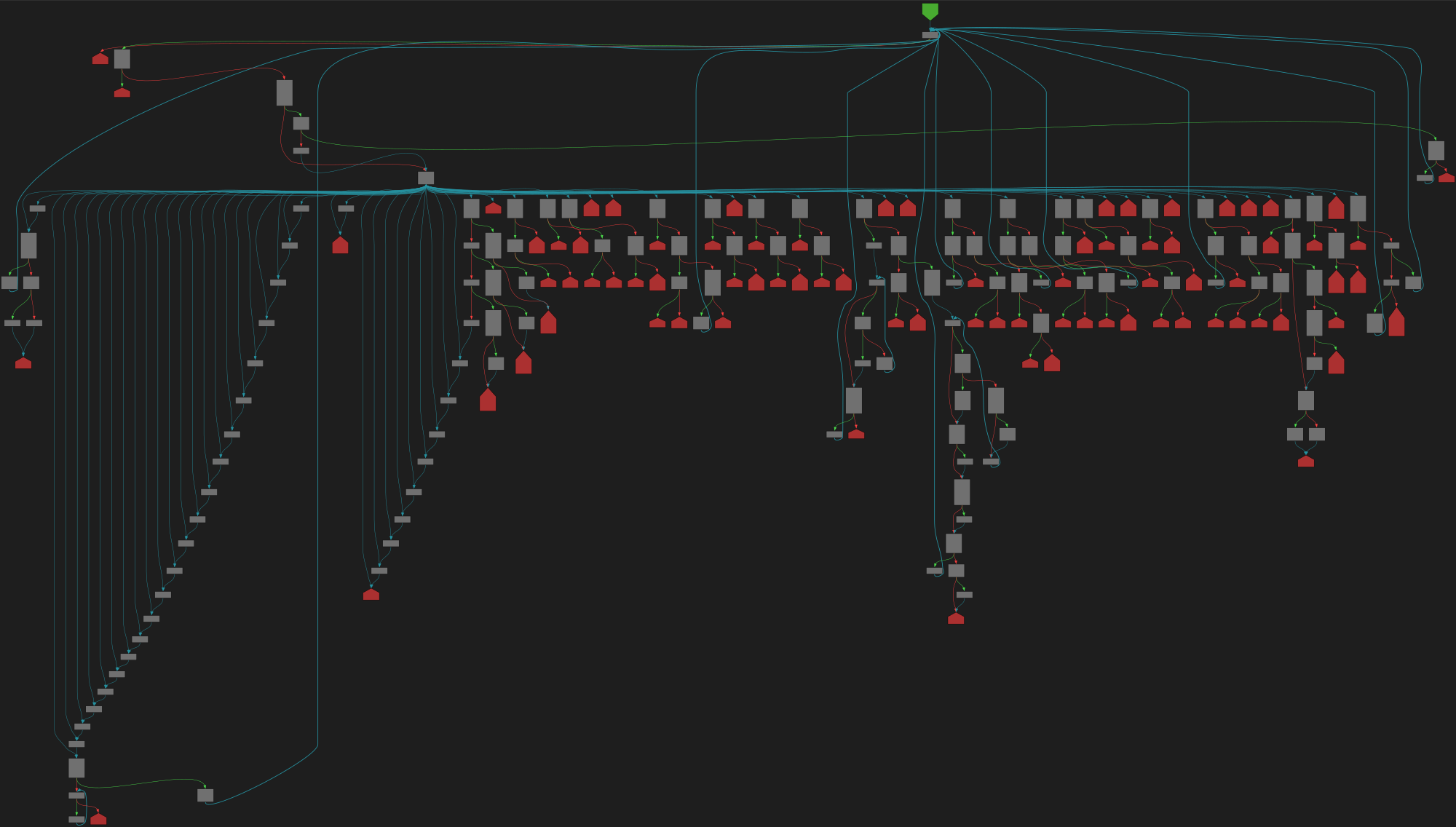
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/compiler/scanner.ts:1890 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/compiler/scanner.ts#L1890
function scan(): SyntaxKind
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Fscanner.ts%23L1890&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Fscanner.ts%23L1890&colors=light
Sonar Research
SonarResearch@infosec.exchange🦘🛜 Our second part of the “Diving Into JumpServer” series is live:
Read more on how an attacker who bypassed authentication can execute code and fully compromise the JumpServer instance and internal hosts:
Caitlin Condon
catc0n@infosec.exchangeI probably sound like a broken record at this point, but we're not sold yet on the world-ending nature of Next.js CVE-2025-29927.
The fact that the bug isn't known to have been successfully exploited in the wild despite the huge amount of media and industry attention it’s received sure feels like a reasonable early indicator that it's unlikely to be broadly exploitable (classic framework vuln), and may not have any easily identifiable remote attack vectors at all.
https://www.rapid7.com/blog/post/2025/03/25/etr-notable-vulnerabilities-in-next-js-cve-2025-29927/