Posts
3382Following
713Followers
1580rev.ng
revng@infosec.exchange🧟♂️ Finding dead bodies
A pad about find dead code using code coverage tools.
It was made by one of us for a talk at the rev.ng hour of some years ago.
More effort than required was put in the image but the results was undoubtedly great.
David Gerard
davidgerard@circumstances.runOpenAI asks US government for the moon on a stick (because CHINA)
https://pivot-to-ai.com/2025/03/14/openai-asks-the-us-government-for-the-moon-on-a-stick/ - text
https://www.youtube.com/watch?v=6VxrrCdMdL0 - video
HalvarFlake
HalvarFlake@mastodon.socialMy contempt for anyone involved with this drivel knows few limits. Conflating issues and fear mongering because a Chinese company dared to publish an actual open model:
And trying to talk about copyright after training in Libgen.
Hypocrisy, lies, grifting :-( - the level of despicable behavior is just out of this world.
wild how the media has fully given up on using the word “lie” as powerful people just bullshit constantly
it’s always “contradicted earlier statements” or “made claims that do not align with the facts” like girl just say they knowingly made shit up, we all see it
buherator
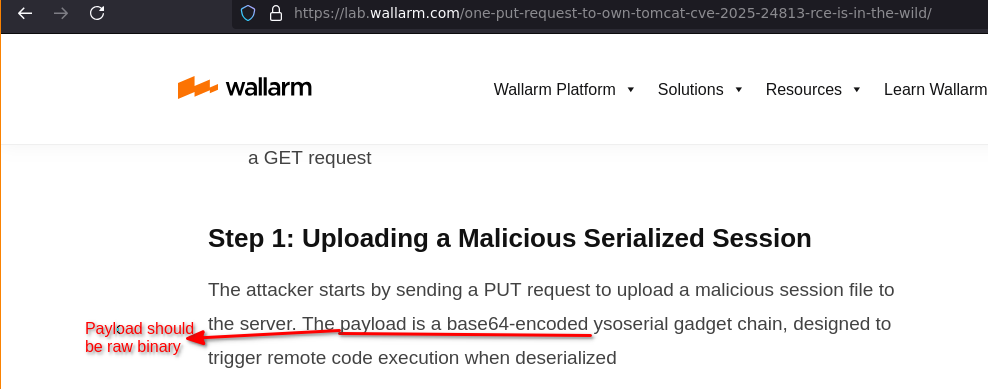
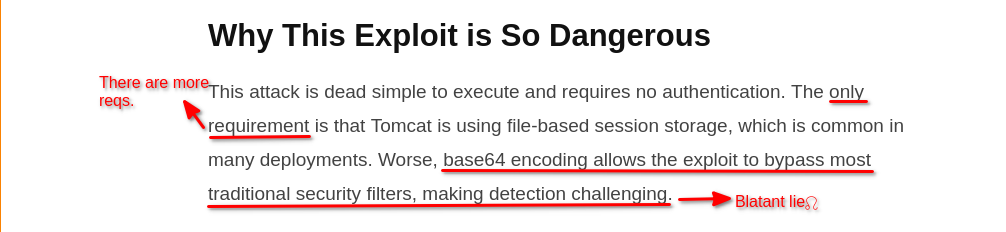
buheratorhttps://web.archive.org/web/20250314071219/https://lab.wallarm.com/one-put-request-to-own-tomcat-cve-2025-24813-rce-is-in-the-wild/
There is a PoC on GitHub too now - it improves my findings by directly invoking the session corresponding to the saved object so you don't have to wait for periodic refreshes:
https://github.com/iSee857/CVE-2025-24813-PoC/
This PoC will raise the EPSS score too.
Edit: Wallarm published an update showing that exploit traffic was detected before a PoC was public. Problem is my writeup&PoC was published well before their detection :P
Peter Stöckli
ulldma@infosec.exchangeIn this demonstration I show the impact of CVE-2025-25291/CVE-2025-25292, an authentication bypass in ruby-saml used by high profile OSS projects such as GitLab. My team coordinated with both the ruby-saml maintainer and GitLab to get this vulnerability fixed and patches are available at https://about.gitlab.com/releases/2025/03/12/patch-release-gitlab-17-9-2-released/
Jason Koebler
jasonkoebler@mastodon.socialthis is so so so wild, must read:
https://www.404media.co/super-nintendo-hardware-is-running-faster-as-it-ages/
drawio
drawio@hostux.social🚀 We’re working on a new user interface for http://draw.io! 🎨 Check out the details here 👉 https://github.com/jgraph/drawio/discussions/4953 — and let us know what you think! Your feedback will help shape the future of http://draw.io! 💡😊 #drawio #UI
DrWhax
drwhax@infosec.exchangeCool stuff for sale on Ebay! "1216428-301 Lockheed Martin Target ECM Combiner Circuit Card Assembly"
Mr. Bitterness
wdormann@infosec.exchangeI take it that there are no rules for being a CVE CNA?
Synology is a CNA.
They published a security advisory.
No CVE to be found.
Open Rights Group
openrightsgroup@social.openrightsgroup.org“There is significant public interest in knowing when and on what basis the UK government believes that it can compel a private company to undermine the privacy and security of its customers.”
ORG, Big Brother Watch and Index on Censorship call for the Tribunal into the UK government's secret order for Apple to break encryption to be held in public.
The case happens TOMORROW.
Read more ⬇️
#encryption #e2ee #privacy #security #ukpolitics #ukpol #cybersecurity #apple
buherator
buheratorhttps://bernsteinbear.com/blog/lattice-bitset/
"The Cinder JIT compiler does some cool stuff with how they represent types so I’m going to share it with you here. "
("Cinder is Meta's internal performance-oriented production version of CPython.")
/via exploits.club
buherator
buheratorhttps://www.euronews.com/2025/03/12/swedish-pirate-bay-backer-carl-lundstrom-dies-in-slovenia-plane-crash
CVE Program
CVE_Program@mastodon.socialWe value your opinion! Please respond to our:
“CVE Data Usage and Satisfaction Survey”
https://forms.office.com/g/hx168RPctg
The CVE Program is requesting feedback from:
* CVE consumers
* Defenders
#cve #vulnerability #vulnerabilitymanagement #cybersecurity
hugovangalen 🤖 🕹️ 😼
hvangalen@mastodon.nlThis weekend, talking to a guy who does IT at a Dutch bank.
Me: So everything runs on Azure or AWS these days?
He: Yes
Me: So they can see all the data.
He: No it's on separate servers, on EU soil. That was a thing before we decided to go ahead with this.
Me: So... They can see all the data.
He: No it's encrypted and threw some acronyms at me.
Me: So, you download the data, decrypt it, and work on it?
He: No that's done on the servers.
Me: So... They can see all the data.
buherator
buheratorhttps://www.hstoday.us/industry/people-on-the-move/alexei-bulazel-rejoins-national-security-council-in-senior-cyber-role/
Hey, this guy actually knows how stuff works!
https://i.blackhat.com/us-18/Thu-August-9/us-18-Bulazel-Windows-Offender-Reverse-Engineering-Windows-Defenders-Antivirus-Emulator.pdf
https://www.recon.cx/2018/brussels/resources/slides/RECON-BRX-2018-Reverse-Engineering-Windows-Defender-s-JavaScript-Engine.pdf
buherator
buheratorhttps://seclists.org/oss-sec/2025/q1/206
"This vulnerability may have been exploited in the wild."
"This commit fixes most of the issue - except `limit` is still signed short":
https://github.com/mozilla/gecko-dev/commit/026f6a947085020cd189dd9af3da00be433a44f8