Posts
3373Following
712Followers
1579CVE Program
CVE_Program@mastodon.socialWe value your opinion! Please respond to our:
“CVE Data Usage and Satisfaction Survey”
https://forms.office.com/g/hx168RPctg
The CVE Program is requesting feedback from:
* CVE consumers
* Defenders
#cve #vulnerability #vulnerabilitymanagement #cybersecurity
hugovangalen 🤖 🕹️ 😼
hvangalen@mastodon.nlThis weekend, talking to a guy who does IT at a Dutch bank.
Me: So everything runs on Azure or AWS these days?
He: Yes
Me: So they can see all the data.
He: No it's on separate servers, on EU soil. That was a thing before we decided to go ahead with this.
Me: So... They can see all the data.
He: No it's encrypted and threw some acronyms at me.
Me: So, you download the data, decrypt it, and work on it?
He: No that's done on the servers.
Me: So... They can see all the data.
buherator
buheratorhttps://www.hstoday.us/industry/people-on-the-move/alexei-bulazel-rejoins-national-security-council-in-senior-cyber-role/
Hey, this guy actually knows how stuff works!
https://i.blackhat.com/us-18/Thu-August-9/us-18-Bulazel-Windows-Offender-Reverse-Engineering-Windows-Defenders-Antivirus-Emulator.pdf
https://www.recon.cx/2018/brussels/resources/slides/RECON-BRX-2018-Reverse-Engineering-Windows-Defender-s-JavaScript-Engine.pdf
buherator
buheratorhttps://seclists.org/oss-sec/2025/q1/206
"This vulnerability may have been exploited in the wild."
"This commit fixes most of the issue - except `limit` is still signed short":
https://github.com/mozilla/gecko-dev/commit/026f6a947085020cd189dd9af3da00be433a44f8
Graham Sutherland / Polynomial
gsuberland@chaos.socialthe absolute state of infosec vulnerability marketing these days
on further analysis by folks who actually understand the tech it turns out the claimed backdoor isn't a backdoor at all, it isn't even really a security issue, and has been framed in a way that is both disingenuously overhyped and also pretty racist
bravo, folks, really advancing the field
buherator
buheratorhttps://github.blog/security/sign-in-as-anyone-bypassing-saml-sso-authentication-with-parser-differentials/
buherator
buheratorhttps://www.eff.org/deeplinks/2025/03/memoriam-mark-klein-att-whistleblower-about-nsa-mass-spying
#fromBsky
This is something that was occupying my time for some time already and I'm super happy that this research is finally released.
I believe this to be only a second reporting on malware targeting Juniper devices. Following Lumen Technologies blog from last month (but this one related to a different actor and different malware).
This blogs dives into specifics of Veriexec bypass vulnerability used by UNC3886, and details of 6 different backdoors found on Juniper MX devices.
UNC3886 is a very interesting actor that does not shy away from targeting less commonly known technologies like routers, edge devices or hypervisors.
More details here: https://cloud.google.com/blog/topics/threat-intelligence/china-nexus-espionage-targets-juniper-routers
Salearlyman
duk3luk3@cloudisland.nzI learned today that MySQL connections are crypto agility hell.
It has a concept of "secure" and "insecure" connections, opportunistic TLS, less opportunistic TLS, rsa based password encryption for transmitting a connection password securely over an insecure connection, and here's the kicker: an authentication cache that allows to authenticate over an insecure connection if you have first authenticated over a secure connection.
Paging @soatok ...
CFG Bot 🤖
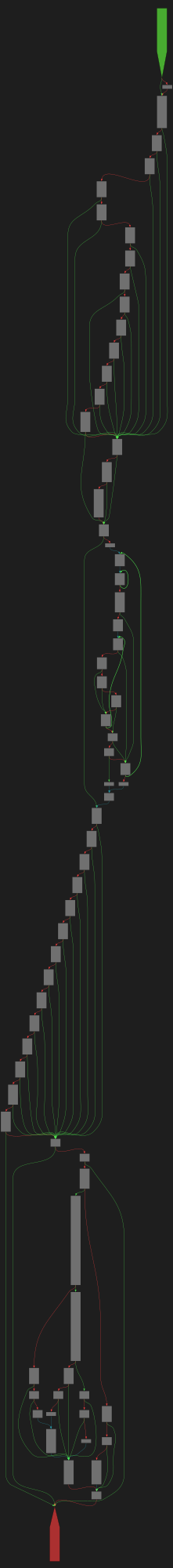
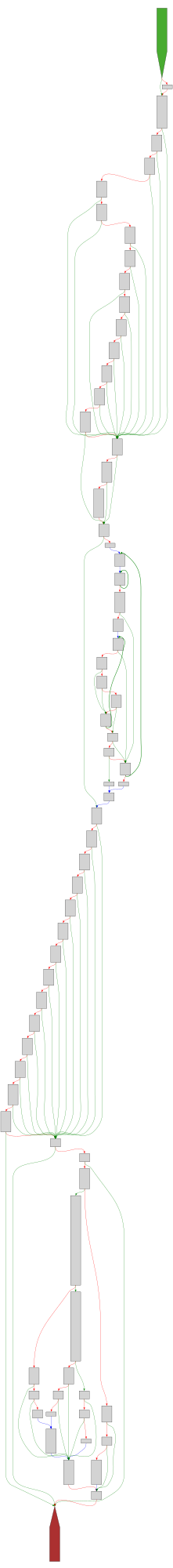
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a6ac088
get_resource_info
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a6ac088.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a6ac088.json&colors=light
Stefano Marinelli
stefano@bsd.cafeOne of the things I've been advocating for years - and where I want to raise my voice even louder - is the importance of owning your data. #OwnYourData
Over the past few days, I’ve come across two examples of how misinformation is causing immense damage, leading people to believe that there's no alternative but to hand over their data to big corporations, putting themselves entirely in their hands.
- A well-known lawyer, just before a meeting, warned about using Teams and its new "virtual assistant," which joins conferences before anyone else and transcribes everything. When I pointed out that it would be wise to use alternative tools (like Jitsi, for example, but there are others), he abruptly ended the conversation, saying, "We've lost this war. There's no alternative anymore."
That wasn’t the right moment for a detailed discussion, so I just noted that alternatives do exist - but if no one starts using them, and if we passively accept certain behaviors from certain companies, things will never improve for us.
- Just now, I received another one of those emails that hurt more in the heart than in the wallet: "Our e-commerce is taking off, so we’re moving it to Shopify to better manage our growth."
I replied, trying to explain that handing over a growing e-commerce business to a third-party company (right now, they have full access to their own server - meaning all their databases, data, etc., are under their control) means losing ownership of it. Prices could change at any moment, contract terms could shift negatively, and, worst case scenario, if Shopify itself faced issues (which seems impossible today, but think of giants like Kodak), they could lose everything. Of course, they’ll do what they think is best, but I feel obligated to warn them.
Luckily, others are making the opposite choice. But I keep wondering: since these big platforms aren’t exactly cheap, rather than "selling themselves" to them just for (potentially) fewer headaches, wouldn’t it be worth paying someone (not me, of course, but someone working exclusively for them) to handle these things - ensuring they retain full ownership of their business and their data?
#DataOwnership #Decentralization #BigTech #DataRights #MyDataMyChoice #TakeBackControl
buherator
buheratorMr. Bitterness
wdormann@infosec.exchangeMe to MSRC: Words clearly describing a vulnerability, with supporting screenshots of the commands I typed and the response that Windows gives.
MSRC: Can you please provide a video showing the behavior you are seeing?
Me: ...
I get that people doing grunt work have mostly-fixed workflows that they go through with common next steps.
But to request a video that now captures (beyond my already-submitted screenshots) the act of me typing, and the Windows response being painted on the screen adds what of value now?
Space Rogue
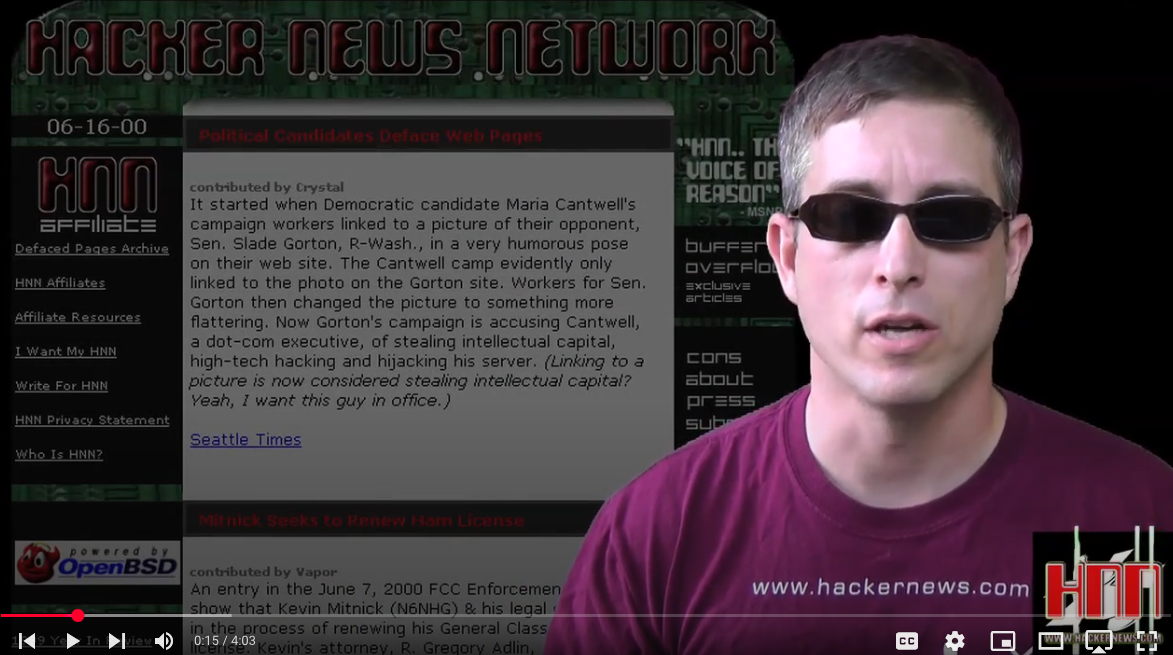
spacerog@mastodon.socialI should have done this a long time ago but people keep asking. I have assembled all of the clips of HNNCast on Youtube into one playlist. If you want to relive ~14yr old news items then this list is for you.
https://www.youtube.com/watch?v=UdKyDqU1p-4&list=PL-DjMTsCaYUwR3dZKdSb-fFMwLFBOvENb
Micah Lee
micahflee@infosec.exchangeHere's the second installment of my Paramilitary Leaks series. How you can set up your computer to read through the leaked militia chats yourself https://micahflee.com/step-by-step-guide-to-reading-the-leaked-militia-chats-yourself/
TIL Space Invaders had a tilt sensor. Good deep dive into the inner workings of the game.
https://www.computerarcheology.com/Arcade/SpaceInvaders/
#programming #retrocomputing #retrogaming #spaceinvaders #assemblylanguage #z80
Trail of Bits
trailofbits@infosec.exchangeIf you're fuzzing C/C++ code and need more customizability, our new Testing Handbook chapter shows you exactly how to set up and use LibAFL - both as a libFuzzer drop-in and as a Rust library.
https://appsec.guide/docs/fuzzing/c-cpp/libafl/
offensivecon
offensive_con@bird.makeupReminder to submit your proposals!
The CFP will close on the 2nd of April.
Robert C. Seacord (@rcs@hachyderm.io)
rcs@bird.makeupThere is a new official C language website maintained by the C Standards Committee https://www.c-language.org/
buherator
buheratorhttps://talosintelligence.com/vulnerability_reports/TALOS-2025-2136
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2135
https://talosintelligence.com/vulnerability_reports/TALOS-2025-2134
CVE-2025-27163 CVE-2025-27158 CVE-2025-27164
/via @talosvulns