Posts
3189Following
706Followers
1562Andrew Gallagher
andrewg@mastodon.ie‘The political press may not understand what’s happening (or may be too afraid to say it out loud), but those of us who’ve spent decades studying how technology and power interact? We see it and we can’t look away.
So, here’s the bottom line: when WaPo’s opinion pages are being gutted and tech CEOs are seeking pre-approval from authoritarians, the line between “tech coverage” and “saving democracy” has basically disappeared. It’s all the same thing.’
https://www.techdirt.com/2025/03/04/why-techdirt-is-now-a-democracy-blog-whether-we-like-it-or-not/
buherator
buheratorhttps://www.elttam.com/blog/rails-sqlite-gadget-rce/
buherator
buheratorhttps://old.reddit.com/r/netsec/comments/1j3tvof/case_study_traditional_cvss_scoring_missed_this/
RoundofThree
roundofthree@bird.makeupI've written a blog post on analysing and getting RCE on some of the bugs in the AIxCC Nginx challenge: https://roundofthree.github.io/posts/nginx-aixcc-pwn/
Siguza
siguza@infosec.spaceAny Apple engineer feel like debugging some hypervisor-related macOS kernel panic?
(Looks like failure by the guest to properly flush TLB panics the host, and seems easiest to repro on M2 Max?)
https://github.com/utmapp/UTM/issues/6919#issuecomment-2565338603
Graham Sutherland / Polynomial
gsuberland@chaos.socialwas not expecting to be writing a vulnerability report for Command & Conquer Generals: Zero Hour today but here we are
https://github.com/TheSuperHackers/GeneralsGameCode/issues/272
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00734fe0
ossl_cms_EncryptedContent_init_bio
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00734fe0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00734fe0.json&colors=light
Kevin Beaumont
GossiTheDog@cyberplace.social3 different VMware zero days, under active exploitation by ransomware groups
CVE-2025-22224, CVE-2025-22225, CVE-2025-22226
VMware ESXi
VMware Workstation Pro / Player (Workstation)
VMware Fusion
VMware Cloud Foundation
VMware Telco Cloud Platform
(Exploitation actually ESXi)
Mark Burnett
m8urnett@infosec.exchangeI need to do a blog post on this, but it seems like a lot of old tricks have been lost over the years. One thing I was thinking about is all the ways to obscure an executable name in command prompts. For example, and I'm not sure how many of them are documented, but all of these work:
Talos Vulnerability Reports
talosvulnsminiaudio ma_dr_flac__decode_samples__lpc out-of-bounds write vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2063
CVE-2024-41147
buherator
buheratorhttps://www.thezdi.com/blog/2025/3/3/cve-2024-43639
buherator
buheratorhttps://blog.doyensec.com/2025/03/04/exploitable-sshd.html
Mari0n
pinkflawd@mastodon.socialBlackHoodie will be back at @_ringzer0 Bootcamp on March 21st with a training about Compiler Internals for Security Engineers, brought to you by.. me 😊 Registration is open, please tell your friends and hacker family, alternatively Shares appreciated 😁 https://blackhoodie.re/Ringzer0_Bootstrap_2025/
Andrea Allievi
aall86@bird.makeupMy team designed and is maintaining Enclaves. Good article here :-)
Kim Zetter
kimzetter@infosec.exchangeTwo seemingly blockbuster stories published on Friday that reported that the Trump admin had ordered US Cyber Command and CISA to "stand down" on their work to detect and counter Russian cyber threats. But new info has come out to contradict the stories or qualify them. I dug into what we know and don't know. As always, if anyone has any additional information related to these stories, please contact me on Signal at KimZ.42.
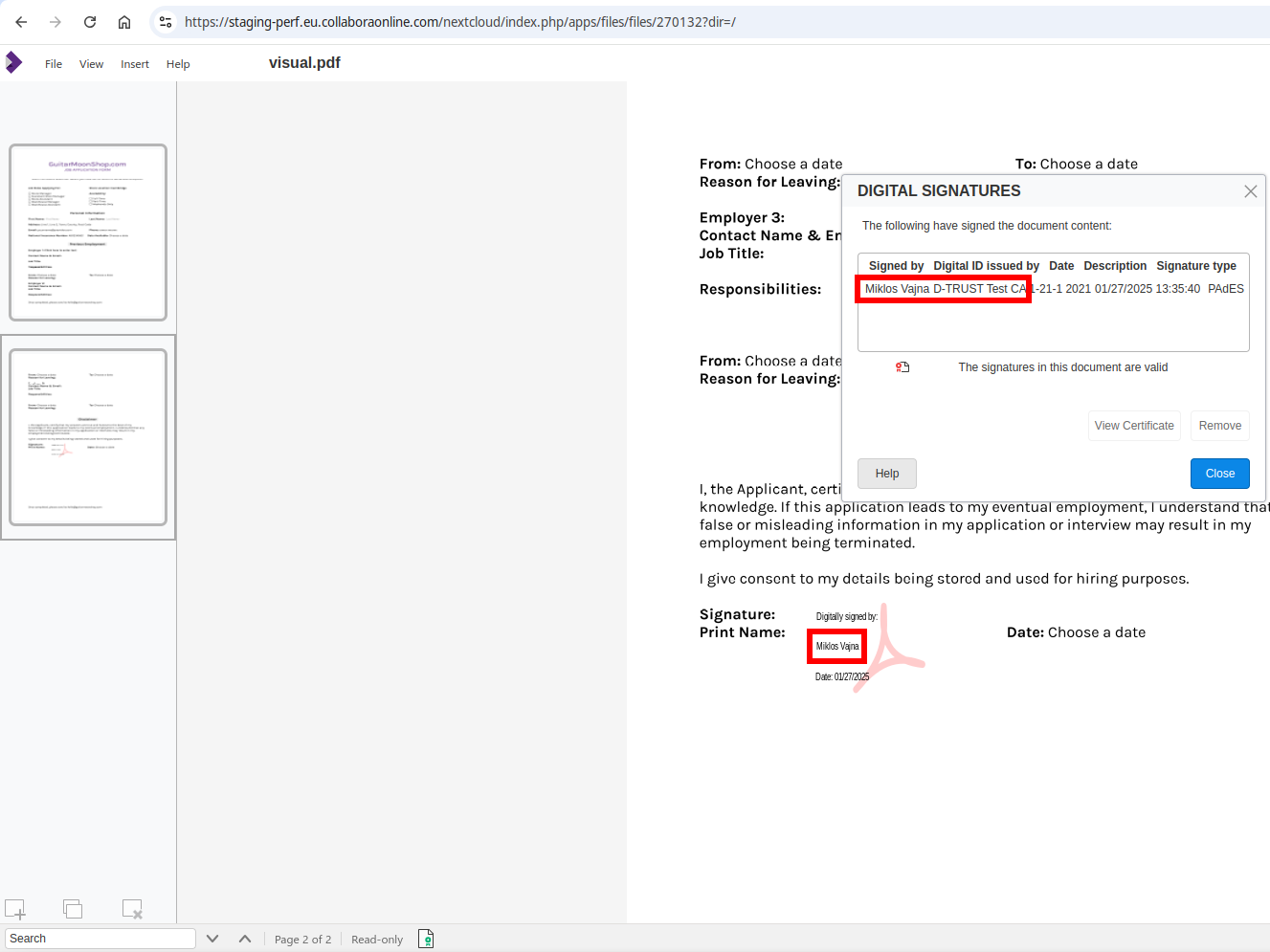
Miklos V
vmiklos@fosstodon.orgNew blog post: Electronic signing in Collabora Online https://vmiklos.hu/blog/cool-esign.html
buherator
buheratorhttps://www.youtube.com/watch?v=3yeb5gSLnjw
Thomas Cherryhomes
tschak@oldbytes.spaceCP/M Users: Looking for a copy of Avocet XASM85 for a resurrection project. #retrocomputing