Posts
3378Following
713Followers
1579Graham Sutherland / Polynomial
gsuberland@chaos.socialwas not expecting to be writing a vulnerability report for Command & Conquer Generals: Zero Hour today but here we are
https://github.com/TheSuperHackers/GeneralsGameCode/issues/272
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00734fe0
ossl_cms_EncryptedContent_init_bio
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00734fe0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00734fe0.json&colors=light
Kevin Beaumont
GossiTheDog@cyberplace.social3 different VMware zero days, under active exploitation by ransomware groups
CVE-2025-22224, CVE-2025-22225, CVE-2025-22226
VMware ESXi
VMware Workstation Pro / Player (Workstation)
VMware Fusion
VMware Cloud Foundation
VMware Telco Cloud Platform
(Exploitation actually ESXi)
Mark Burnett
m8urnett@infosec.exchangeI need to do a blog post on this, but it seems like a lot of old tricks have been lost over the years. One thing I was thinking about is all the ways to obscure an executable name in command prompts. For example, and I'm not sure how many of them are documented, but all of these work:
Talos Vulnerability Reports
talosvulnsminiaudio ma_dr_flac__decode_samples__lpc out-of-bounds write vulnerability
https://talosintelligence.com/vulnerability_reports/TALOS-2024-2063
CVE-2024-41147
buherator
buheratorhttps://www.thezdi.com/blog/2025/3/3/cve-2024-43639
buherator
buheratorhttps://blog.doyensec.com/2025/03/04/exploitable-sshd.html
Mari0n
pinkflawd@mastodon.socialBlackHoodie will be back at @_ringzer0 Bootcamp on March 21st with a training about Compiler Internals for Security Engineers, brought to you by.. me 😊 Registration is open, please tell your friends and hacker family, alternatively Shares appreciated 😁 https://blackhoodie.re/Ringzer0_Bootstrap_2025/
Andrea Allievi
aall86@bird.makeupMy team designed and is maintaining Enclaves. Good article here :-)
Kim Zetter
kimzetter@infosec.exchangeTwo seemingly blockbuster stories published on Friday that reported that the Trump admin had ordered US Cyber Command and CISA to "stand down" on their work to detect and counter Russian cyber threats. But new info has come out to contradict the stories or qualify them. I dug into what we know and don't know. As always, if anyone has any additional information related to these stories, please contact me on Signal at KimZ.42.
Miklos V
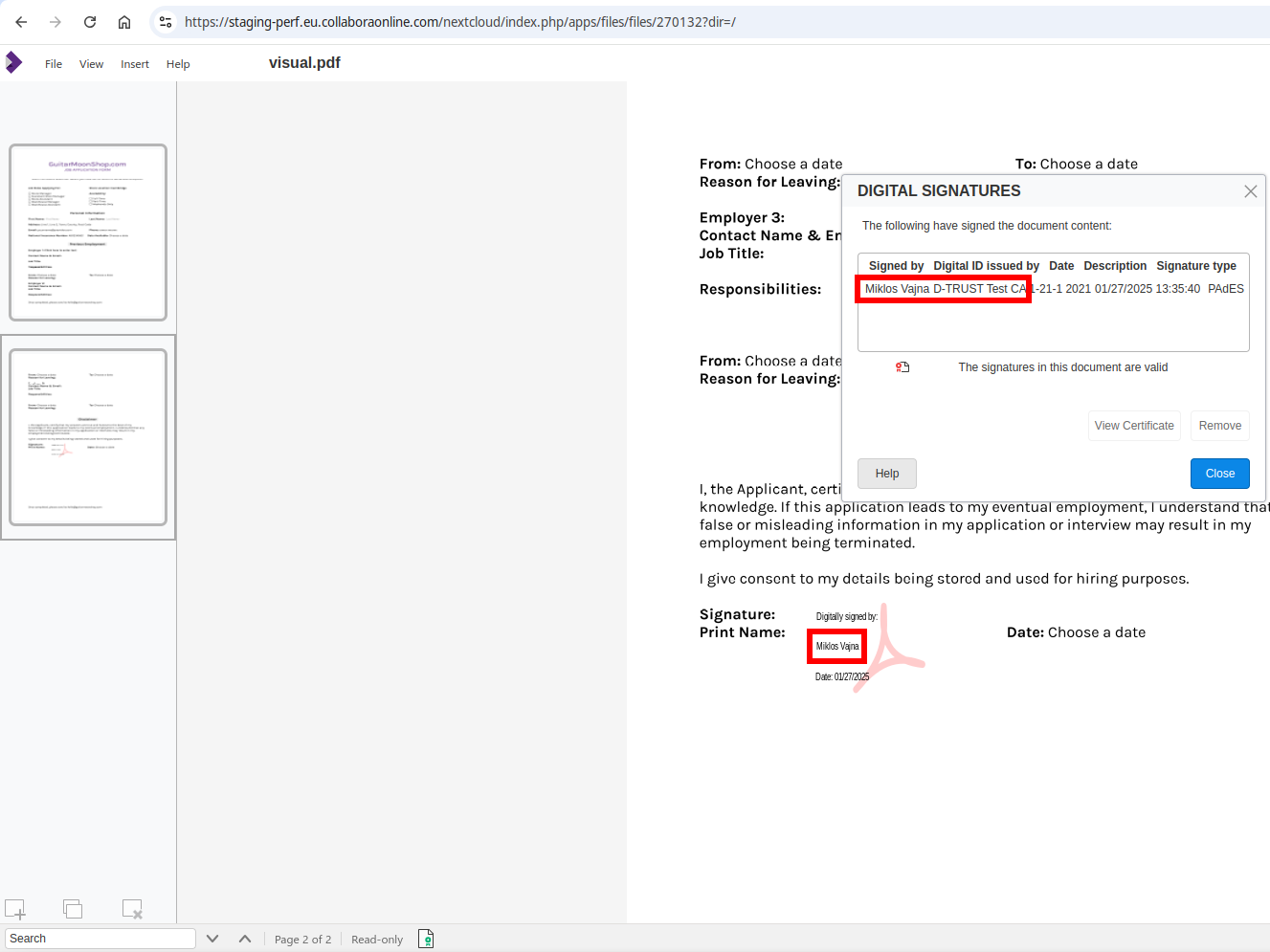
vmiklos@fosstodon.orgNew blog post: Electronic signing in Collabora Online https://vmiklos.hu/blog/cool-esign.html
buherator
buheratorhttps://www.youtube.com/watch?v=3yeb5gSLnjw
Thomas Cherryhomes
tschak@oldbytes.spaceCP/M Users: Looking for a copy of Avocet XASM85 for a resurrection project. #retrocomputing
Team KeePassXC
keepassxc@fosstodon.org🎉 KeePassXC 2.7.10 is out! 🥳
The most prominent changes in this release are the addition of a Proton Pass importer and (due to popular request) a new setting for changing the application font size. You can find the full list of changes on our website:
https://keepassxc.org/blog/2025-03-04-2.7.10-released/
eShard
eshard@infosec.exchange𝗝𝗼𝗶𝗻 𝗼𝘂𝗿 𝗹𝗶𝘃𝗲 𝘄𝗲𝗯𝗶𝗻𝗮𝗿 𝗼𝗻 𝗠𝗮𝗿𝗰𝗵 𝟲𝘁𝗵!
Discover how to eliminate debugging inefficiencies and accelerate vulnerability research with time travel analysis.
Register now 👇
https://www.linkedin.com/events/exploitingaroutervulnerabilityw7299810055170805761/
#cybersecurity #webinar #vulnerability #malware #reverseengineering
buherator
buheratorhttps://u1f383.github.io/linux/2025/03/04/enomem-in-linux-kernel.html
"In this article, I will explore the feasibility of precisely managing memory usage within the Linux kernel" CVE-2023-2236