Posts
3381Following
713Followers
1580Dare Obasanjo
carnage4life@mas.toThe SEC has ruled that meme coins aren’t securities since they “typically have limited or no use or functionality” and are “more akin to collectibles.”
These means getting rug pulled on a memecoin isn’t securities fraud. It’s more like overpaying for Beanie Babies.
https://www.cnbc.com/2025/02/27/sec-says-most-meme-coins-are-not-securities.html
Tony “Abolish ICE” Arcieri🌹🦀
bascule@mas.toGene Hackman’s Family Reveals What They Believe Caused His Death: Carbon Monoxide
Yet another reason to get rid of all the gas appliances in your home if you can: they’re dangerous!
buherator
buheratorbuherator
buheratorhttps://seclists.org/fulldisclosure/2025/Feb/19
- Firmware Downgrade (CVE-2024-39601)
- Firmware Update Decryption via Secure Element Oracle (CVE-2024-53832)
Royce Williams
tychotithonus@infosec.exchangeIf a government can issue a secret order to push a 'special' version of a mobile app just to a specific person (or set of people), how can this be mitigated?
How can app "rarity" be detected locally? (Antivirus and its descendants have a concept of a "well-known benign executable" vs one that has only been rarely seen.
Can a local app, or an OS feature, be used to compare local apps with a list of expected versions?
Can this be done independently of the OS (since the order could also subvert the rarity check)? (Even an independent app can be subverted if the only app store is the official one maintained by the same vendor.)
To detect unusual app versions, reproducible builds are necessary but not sufficient, unless the project is also FOSS -- because even if everyone gets the same APK, the app might receive different instructions from its server depending on unique metadata.
buherator
buheratorhttps://www.synacktiv.com/en/publications/taking-the-relaying-capabilities-of-multicast-poisoning-to-the-next-level-tricking
buherator
buheratorhttps://bughunters.google.com/blog/5850786553528320/a-deep-dive-into-js-trusted-types-violations
buherator
buheratorhttps://github.com/hyperlight-dev/hyperlight
It supports both Windows and Linux, utilizing Windows Hypervisor Platform on Windows, and either Microsoft Hypervisor (mshv) or KVM on Linux.
#hypervisor #virtualization
Zhuowei Zhang
zhuowei@notnow.dev“HKEY_CURRENT_USER. You will never find a more wretched hive of scum and villainy.”
Joxean Koret (@matalaz)
joxean@mastodon.socialAnybody knows how to demangle a string, not a symbol, in #Ghidra using Python?
buherator
buheratorhttps://u1f383.github.io/linux/2025/02/27/how-does-linux-direct-mapping-work.html
Glyph
glyph@mastodon.socialbeen reminded of this several times this week and not in a nice way
buherator
buheratorhttps://binary.ninja/2025/02/26/sidekick-in-action-finding-vulnerabilities-in-dnsmasq.html
Taggart
mttaggart@infosec.exchangeFirefox now has Terms of Use! This'll go over like a lead balloon.
You give Mozilla all rights necessary to operate Firefox, including processing data as we describe in the Firefox Privacy Notice, as well as acting on your behalf to help you navigate the internet. When you upload or input information through Firefox, you hereby grant us a nonexclusive, royalty-free, worldwide license to use that information to help you navigate, experience, and interact with online content as you indicate with your use of Firefox.
cpresser
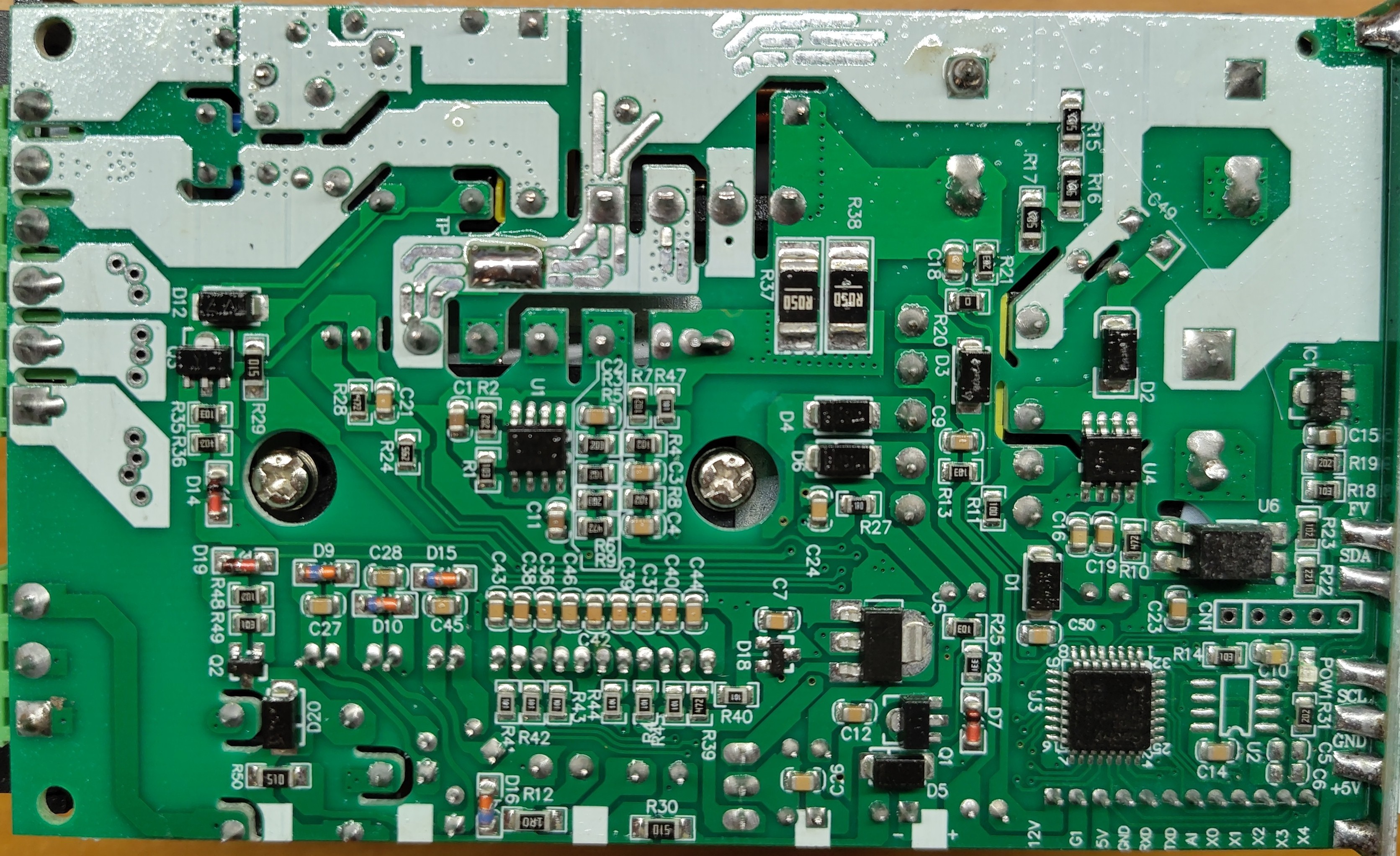
cccpresser@chaos.socialI got another #NameThatWare for you all. This time, lets try something new.
Its quite hard to make a challenge that is both accessible and challenging at the same time. So now, I will post multiple pictures. The first in this post is the 'hard' level. If you are not an expert, look at the 2nd picture that will be behind a CW. There is also a 3rd picture for easy-mode.
As always, try to write down you observations and deductions behind a CW to not spoil it for others.
Lorenzo Franceschi-Bicchierai
lorenzofb@infosec.exchangeNEW: Hacked crypto exchange Bybit is offering $140 million in bounties to anyone who can help locate and freeze the stolen ethereum.
Bybit also disclosed preliminary results of investigations, which reveal hackers breached a developer’s device at a wallet platform Safe Wallet.
Neodyme
neodyme@infosec.exchangeWrapping up our COM hijacking series! 🎉
In the final part, we discuss a custom IPC protocol, use a registry write to gain SYSTEM privileges, and explore Denial of Service attacks on security products. 💥💻
Don't miss it! https://neodyme.io/en/blog/com_hijacking_4/