Posts
2473Following
598Followers
1327CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 005b45b0
aes_gcm_ctrl
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F005b45b0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F005b45b0.json&colors=light
Michael Lucas 
mwl@io.mwl.io
ICYMI: I am now selling print books directly from my store. Buy print, get the ebook free.
Only Run Your Own Mail Server and Dear Abyss right now, but it's a start!
daniel:// stenberg://
bagder@mastodon.socialFor educational purposes we disclose this recent hackerone report on #curl claiming its sprintf() implementation is bad because it can be made to deref a bad pointer when you use it incorrectly. You know, exactly how all sprintf() implementation work - by design.
This is not the first time we had this "flaw" reported. (I did not check the "AI slop" checkbox on this one)
buherator
buheratorI could really use some climate change rn...
buherator
buherator- I couldn't get NET to work so far, neither with virtio nor e1000 vNIC's
- Windows 11 refuses to recognize serial ports too, even with virtio drivers. It'd have been royal to use WinDbg from Store but :(
- Windows Server 2022 does recognize COM ports (maybe drivers can be transplanted to 11?)
- COM ports can be connected from the Proxmox host using socat as described here:
https://forum.proxmox.com/threads/two-windows-guests-communicating-via-serial-console-comn.67588/
- You should of course disable Secure Boot - you can do that in the VM's BIOS under Device Manager / Secure Boot Config / Attempt Secure Boot
TBC
Virus Bulletin
VirusBulletin@infosec.exchangeGoogle Threat Intelligence Group (GTIG) has observed increasing efforts from several Russia state-aligned threat actors to compromise Signal Messenger accounts used by individuals of interest to Russian intelligence services. https://cloud.google.com/blog/topics/threat-intelligence/russia-targeting-signal-messenger
Ange
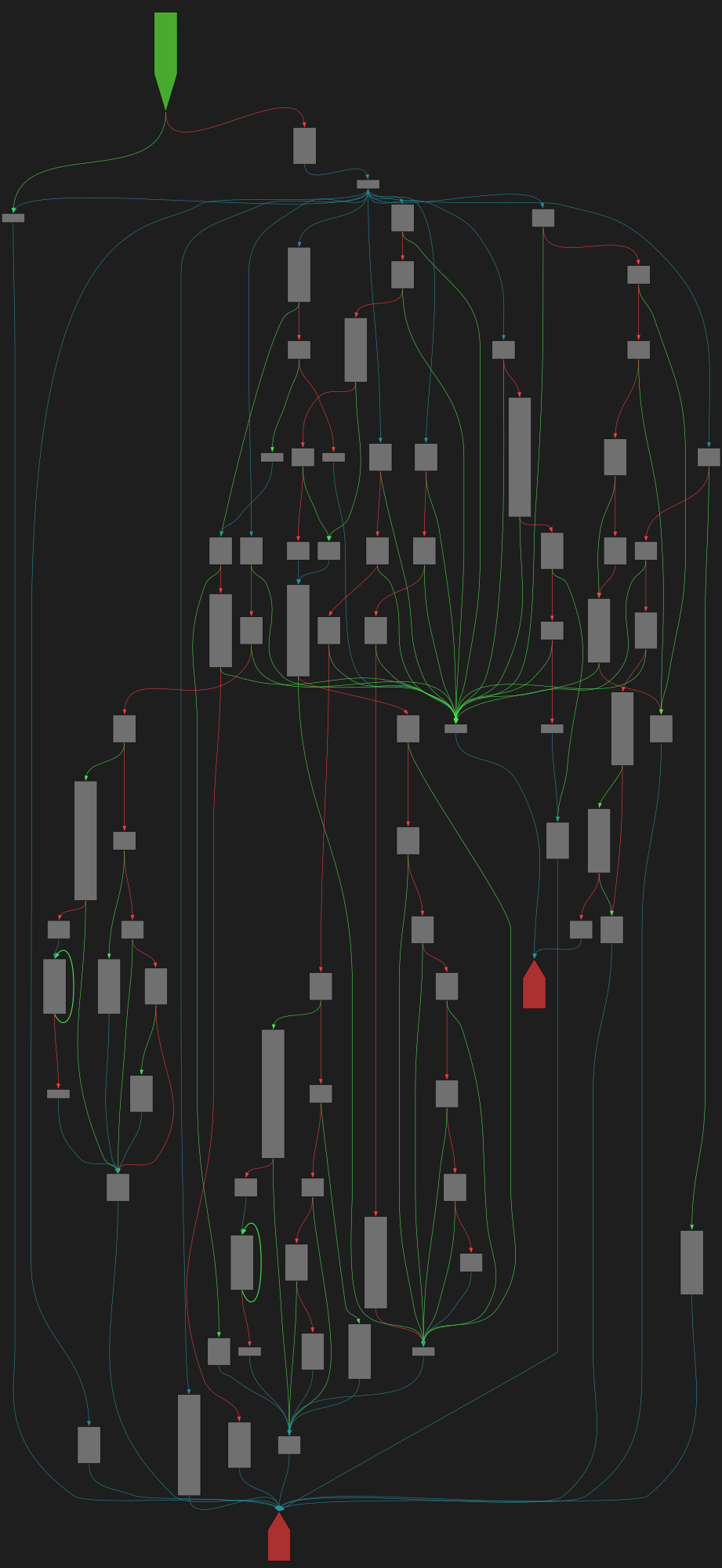
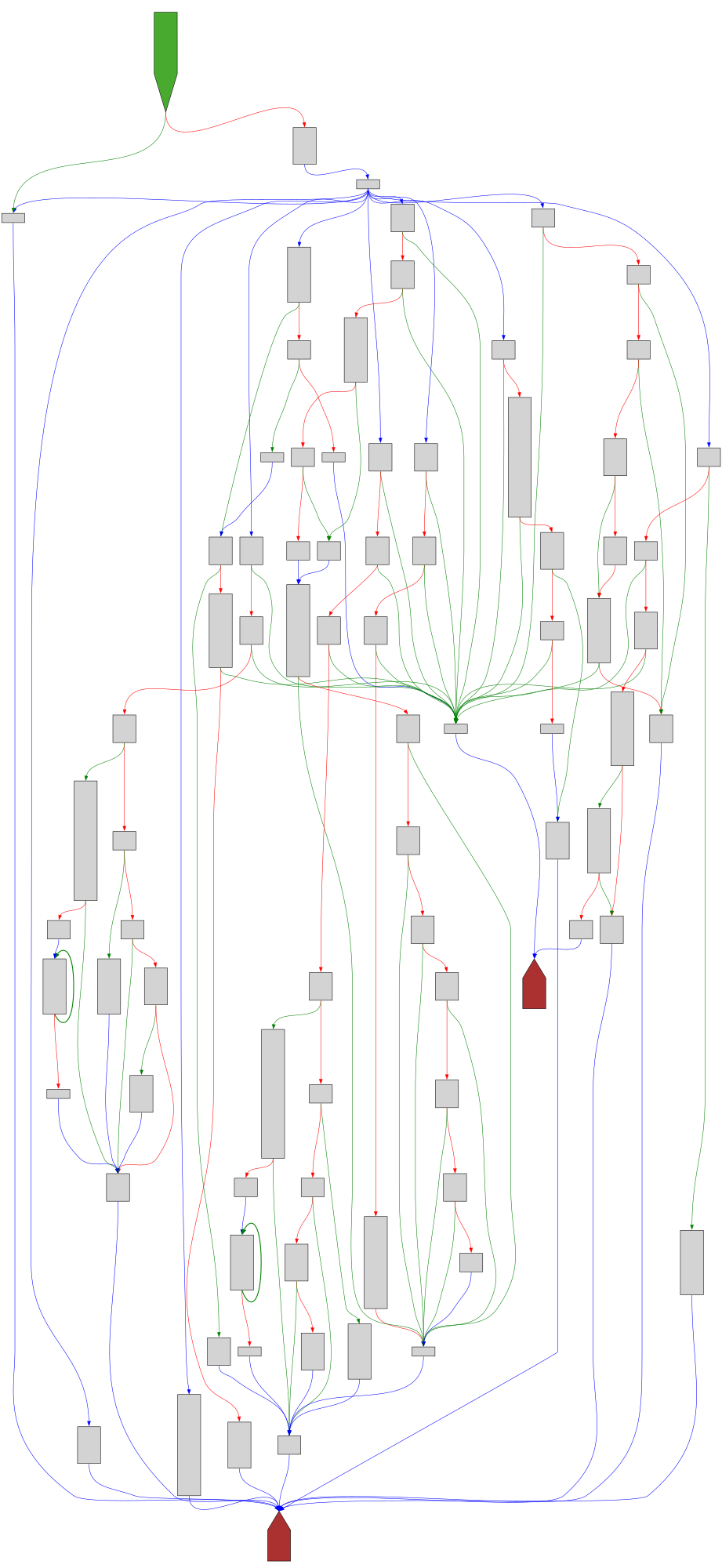
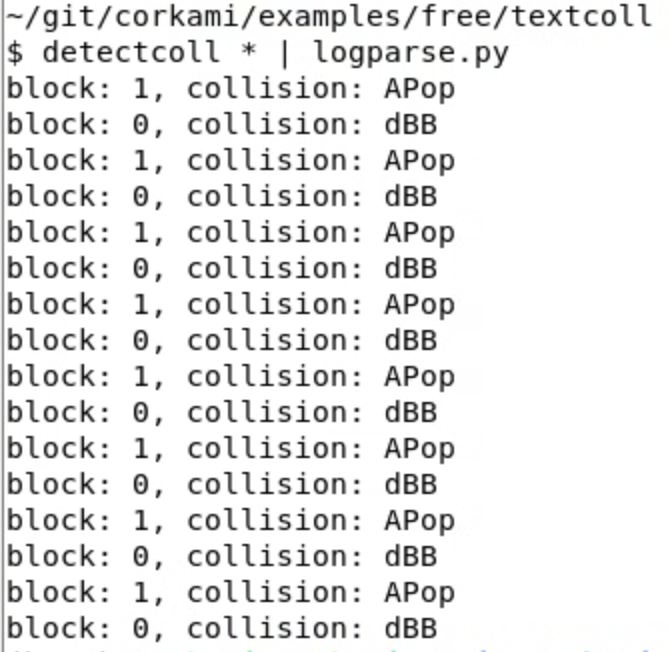
Ange@mastodon.socialI just pushed an update to logparse to detect the near-collision blocks (w/ no difference) of TextColl.
Thanks Marc!
https://github.com/corkami/collisions
Ange
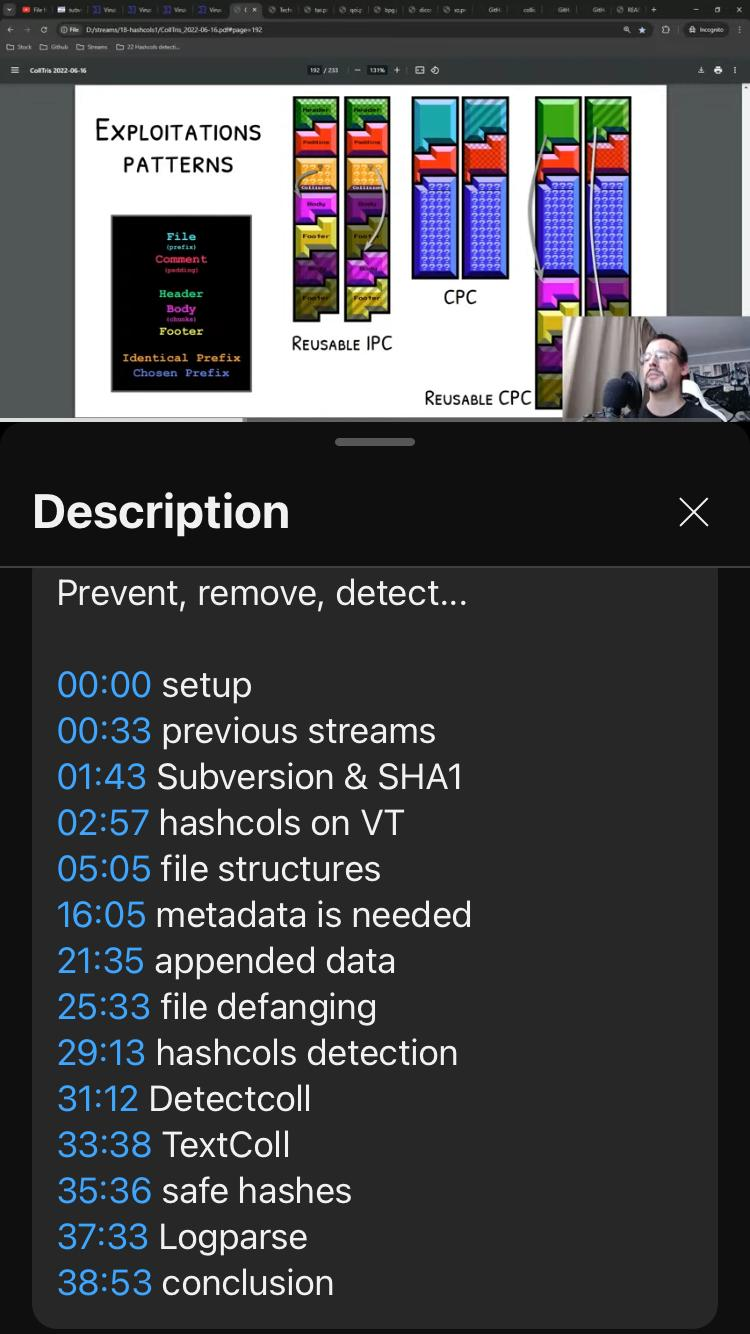
Ange@mastodon.socialThe livestream on multi-hashcolls is up.
Covering the hashcoll tag in VT, specific file format structures, defanging files, Stevens' DetectColl, safe hashes...
https://www.youtube.com/live/1D6C6z_25cE?si=GmDi17uII1xj7rUi&t=33
Dr. Zalka Csenge Virág
TarkabarkaHolgy@ohai.socialDo I have anyone here who reads #Chinese and can help me with a story?...
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-p5pg-x43v-mvqj
CVE-2024-12084 CVE-2024-12085 CVE-2024-12086 CVE-2024-12087 CVE-2024-12088
buherator
buheratorhttps://github.com/google/security-research/security/advisories/GHSA-73px-m3vw-mr35
CVE-2025-0110
Ars Technica
arstechnica@mastodon.socialValve releases full Team Fortress 2 game code to encourage new, free versions
Other Source games also get the Half-Life 2 anniversary update treatment.
https://arstechnica.com/gaming/2025/02/valve-releases-full-team-fortress-2-game-code-to-encourage-new-free-versions/?utm_brand=arstechnica&utm_social-type=owned&utm_source=mastodon&utm_medium=social
I guess technically it's grub_strcpy() but close enough.
https://bugzilla.redhat.com/show_bug.cgi?id=2346112
A flaw was found in grub2. During the network boot process, when trying to search for the configuration file, grub copies data from a user controlled environment variable into an internal buffer using the grub_strcpy() function. During this step, it fails to consider the environment variable length when allocating the internal buffer, resulting in an out-of-bounds write. If correctly exploited, this issue may result in remote code execution through the same network segment grub is searching for the boot information, which can be used to by-pass secure boot protections.
I missed that Chrome had a release yesterday for Desktop that fixed two sev:HIGH CVEs and a sev:MED :
https://chromereleases.googleblog.com/2025/02/stable-channel-update-for-desktop_18.html
And the Android one says it fixed the same vulns as the Desktop one:
https://chromereleases.googleblog.com/2025/02/chrome-for-android-update_01629155727.html
buherator
buheratorhackaday
hackaday@hackaday.socialBe Careful What You Ask For: Voice Control
https://hackaday.com/2025/02/19/be-careful-what-you-ask-for-voice-control/
Random reminder that you can follow Mastodon ( and maybe Fediverse in general? ) accounts by appending dot rss to their profile URL. For example, if you lacked good judgement and wanted to follow my feed via RSS, you would add https://infosec.exchange/@cR0w.rss to your RSS reader and it would pull posts into your reader. It's a fantastic feature for certain feeds. And, as was made more evident recently ( RIP 🐐 ) if an account autodeletes their posts or goes offline, you still have them in your RSS reader per its retention configuration.
With that, remember that anything you post can end up in someone's RSS reader ( or other scrapers / aggregators / etc. ) regardless of your profile hashtags and autodelete settings. Just something to keep in mind.
ς๏гєɭคภς0๔3г 
corelanc0d3r@infosec.exchange
🚀 Master heap exploitation with Corelan in Zagreb! Hands-on, real-world skills from the best. Limited spots—sign up now! 🔥
https://deep-conference.com/training-corelan-heap-exploit-development-masterclass-for-windows/