Posts
3368Following
712Followers
1580Taggart
mttaggart@infosec.exchangeHere's some nice empirical evidence to support what we all feel: insecure configuration and insecure defaults drive compromises more than software vulnerabilities. This paper argues that the Secure-By-Design initiative would be better served by focusing on the former.
https://www.documentcloud.org/documents/25524680-sbd-feb-2025-seymourwoods/
Techmeme
Techmeme@techhub.socialX appears to be blocking Signal's "Signal.me" links in DMs, posts, and profile pages, giving error messages and showing a warning page for users clicking them (Matt Binder/disruptionist)
https://www.disruptionist.com/p/elon-musks-x-blocks-links-to-signal
http://www.techmeme.com/250217/p8#a250217p8
Soatok Dreamseeker
soatok@furry.engineerReviewing the Cryptography Used by Signal
Last year, I urged furries to stop using Telegram because it doesn't actually provide them with any of the privacy guarantees they think it gives them. Instead of improving Telegram's cryptography to be actually secure, the CEO started spreading misleading bullshit about Signal®. Since then, I've been flooded with people asking me about various other encrypted messaging apps…
http://soatok.blog/2025/02/18/reviewing-the-cryptography-used-by-signal/
Wladimir Palant
WPalant@infosec.exchangeI have been introduced to the obscure Linux failure condition called “unbalanced btrfs filesystem.” That’s when you have more than 100 GiB free on your hard drive, yet the file system will refuse operations like renaming a file, claiming that you have no space left. Which comes out of the blue, without any kind of prior warning. And you first have to search past all the unhelpful articles explaining how to remove unused files, until you find that the issue is specific to the btrfs filesystem and with some luck can be cured by running some obscure commands (yet these commands also tend to refuse working because … 🥁🥁🥁 … you have no space left).
It’s 2025 and Linux still does that to people…
Sam Stepanyan  🐘
🐘
securestep9@infosec.exchange
#LibreOffice: patches two #vulnerabilities allowing arbitrary file writes & remote data extraction from environment variables & configuration files. CVE-2024-12425 & CVE-2024-12426 require no user interaction beyond opening a malicious document containing a malicious font or an image:
👇
https://securityonline.info/libreoffice-vulnerabilities-cve-2024-12425-cve-2024-12426-pocs-released-patch-asap/
buherator
buheratorCVE-2025-26465: MitM attack against OpenSSH's VerifyHostKeyDNS-enabled
client
CVE-2025-26466: DoS attack against OpenSSH's client and server
https://www.openwall.com/lists/oss-security/2025/02/18/1
Ange
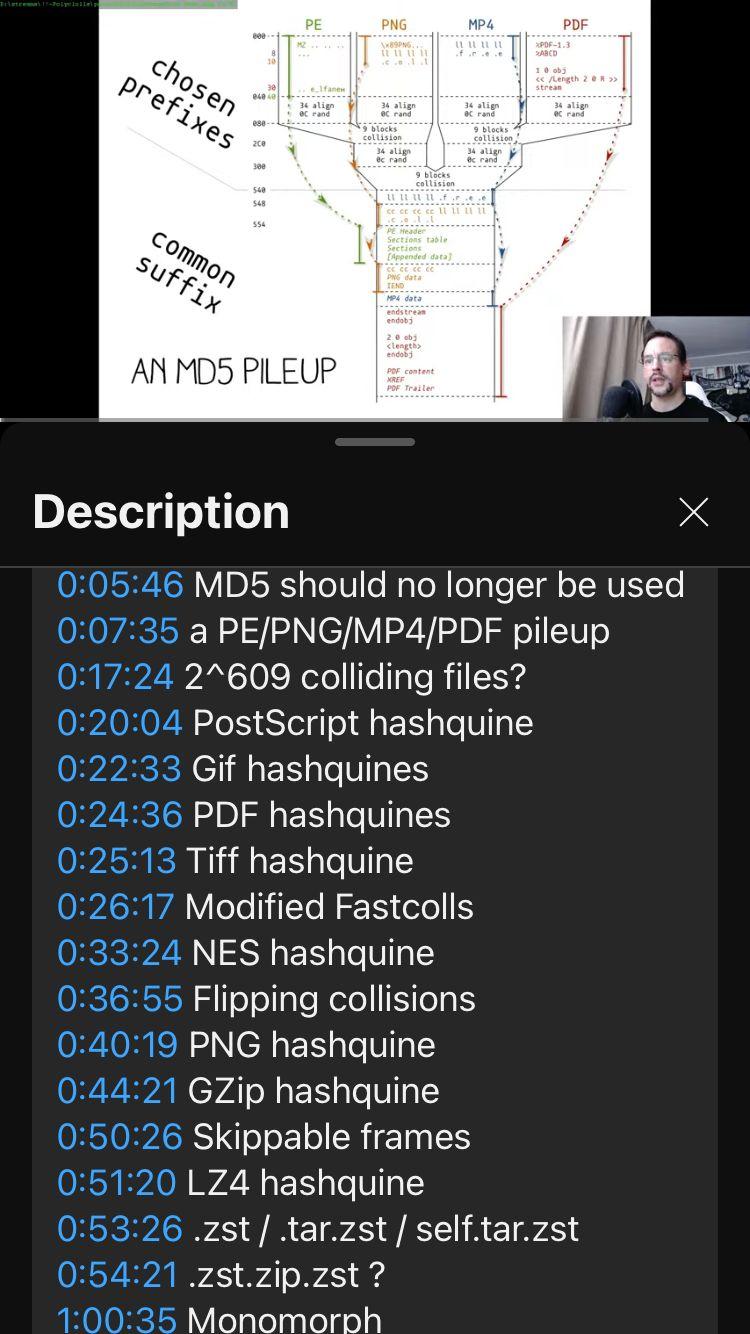
Ange@mastodon.socialThe livestream on multi-hashcolls is up!
Awesome that David joined and commented on his own hashquines!
https://www.youtube.com/live/-asJnf-S2Nk?si=DCACWGTQyFVOmN1a
Ange
Ange@mastodon.socialThe next livestream will be on mitigating hash collisions: preventing them at format design, filtering them out or detecting them.
https://www.youtube.com/live/A7EBbGv1B3U?si=G0zp4eRd0agKSzxY
Phrack Zine
phrack@bird.makeupHackers rejoice!
We are releasing the Phrack 71 PDF for you today!
Don't forget this year is Phrack's 40th anniversary release! Send in your contribution and be part of this historical issue!
The CFP is still open, you can find it and the PDF link at https://phrack.org
buherator
buherator#datavisualization
Molly White
molly0xfff@hachyderm.ioIt’s a shame to see Sci-Hub falling for web3 hype and adding a pumpfun memecoin ticker to their webpage. Blockchain-based DNS does not automatically mean “decentralized”, and 3DNS — the company behind .box — is based in the US and would be subject to US court orders.
Someone unaffiliated with Sci-Hub created the memecoin, claiming to be fundraising, but said only 20% of proceeds would go to Sci-Hub. Founder Alexandra Elbakyan herself condemned this.
buherator
buheratorhttps://github.com/dod-cyber-crime-center/Dragodis
#Ghidra #IDA #ReverseEngineering
daniel:// stenberg://
bagder@mastodon.socialWhat comes after world domination?
This is the abstract for my scheduled talk at foss-north 2025 in April. What do you think is next?
ς๏гєɭคภς0๔3г 
corelanc0d3r@infosec.exchange
New year, new skills, new exploits! 💻🎯
Corelan classes are coming your way! Learn Windows stack & heap exploitation from corelanc0d3r.
🔥 Hands-on labs, real-world scenarios & an elite alumni network. Spots fill up fast—register now! 👉 [https://www.corelan-training.com/index.php/training-schedules
Source of some unbearably loud snoring
algernon@come-from.mad-scientist.clubAs the next step in my quest to make it easier to poison AI crawlers, I present you: OCIocaine: a project where #DockerCompose meets #Caddy and #Iocaine, to poison AI crawlers for all your sites, automatically.
The idea here is to provide a docker compose file that starts up Caddy and Iocaine, configured so that Caddy will reverse proxy for any and all services on the same docker network, as long as they have a few labels that tell it to do so. In addition, a Caddyfile snippet will be available for all of these, which takes care of routing bad visitors to Iocaine.
And if that's not enough, the whole thing comes preconfigured with a wordlist (a list of English words), and traning data (the complete works of Shakespeare), and a list of known AI crawlers (courtesy of ai.robots.txt).
All you have to do is copy the sample configuration, create a network, start it up, and deploy labeled containers into the same network, and OCIocaine takes care of the rest.
Soatok Dreamseeker
soatok@furry.engineerWordPress 6.8 is due to switch their password hashing to bcrypt, and their application passwords to BLAKE2b.
Great news:
They disarmed the 72 char footgun with bcrypt in the way I recommended (HMAC, rather than just SHA2, to prevent hash shucking, and base64 to prevent NUL truncation).
buherator
buheratorhttps://www.itjungle.com/2025/02/17/acs-password-leaks-are-a-security-issue-on-ibm-i/
Our work featured in IT Jungle
BINARLY🔬
binarly_io@bird.makeup🚨Secure Boot relies on revocation lists (dbx) to block malicious bootloaders, but discrepancies between the @uefiforum & @microsoft lists create security gaps.
👉Call for a single and openly maintained revocation list -- a unified source of truth!
https://www.binarly.io/blog/from-trust-to-trouble-the-supply-chain-implications-of-a-broken-dbx