Posts
3393Following
713Followers
1581Trail of Bits
trailofbits@infosec.exchangeThanks to OSTIF!, in 2024, we assessed cURL's HTTP/3 components. We found two issues, enhanced fuzzing coverage, and provided testing and security recommendations.
cURL marked our 14th security assessment with OSTIF, with our first being in 2019. OSTIF's mission to secure critical open-source software has led to security improvements across projects on which we all depend.
Read their annual reports:
https://ostif.org/ostif-2024-annual-report/
https://ostif.org/2024-sovtech-audit-report/
p0pcycle
pamoutaf@infosec.exchangeBetter late than never, I just published a blogpost about my experience at @blackhoodie training, hexacon 2024. Again, big thanks to the organizers for putting together this training, it was really good! 😊
buherator
buheratorhttps://vault.fbi.gov/kevin-mitnick/kevin-mitnick-part-01-final/view
#frombsky
benjojo
benjojo@benjojo.co.ukSuper scummy for microsoft to auto upgrade (at the added cost of an extra £30 a year) people to a AI plan, and not offer a "actually I don't use any of that stuff" can I not pay that £30 a year?
And then only when you are at the cancel page, it's like "🥺 oh sorry do you want the old deal back? 🥺"
For anyone else, you don't even have to get that far into the cancel page for this. So it's easy to save £30 a year with this.
Programming Quotes
programming_quotes@mastodon.socialPerfection is achieved, not when there is nothing more to add, but when there is nothing left to take away.
— Antoine de Saint Exupry
quarkslab
quarkslab@infosec.exchangeUnrestrict the restricted mode for USB on iPhone. A first analysis @citizenlab #CVE-2025-24200 👉 https://blog.quarkslab.com/first-analysis-of-apples-usb-restricted-mode-bypass-cve-2025-24200.html
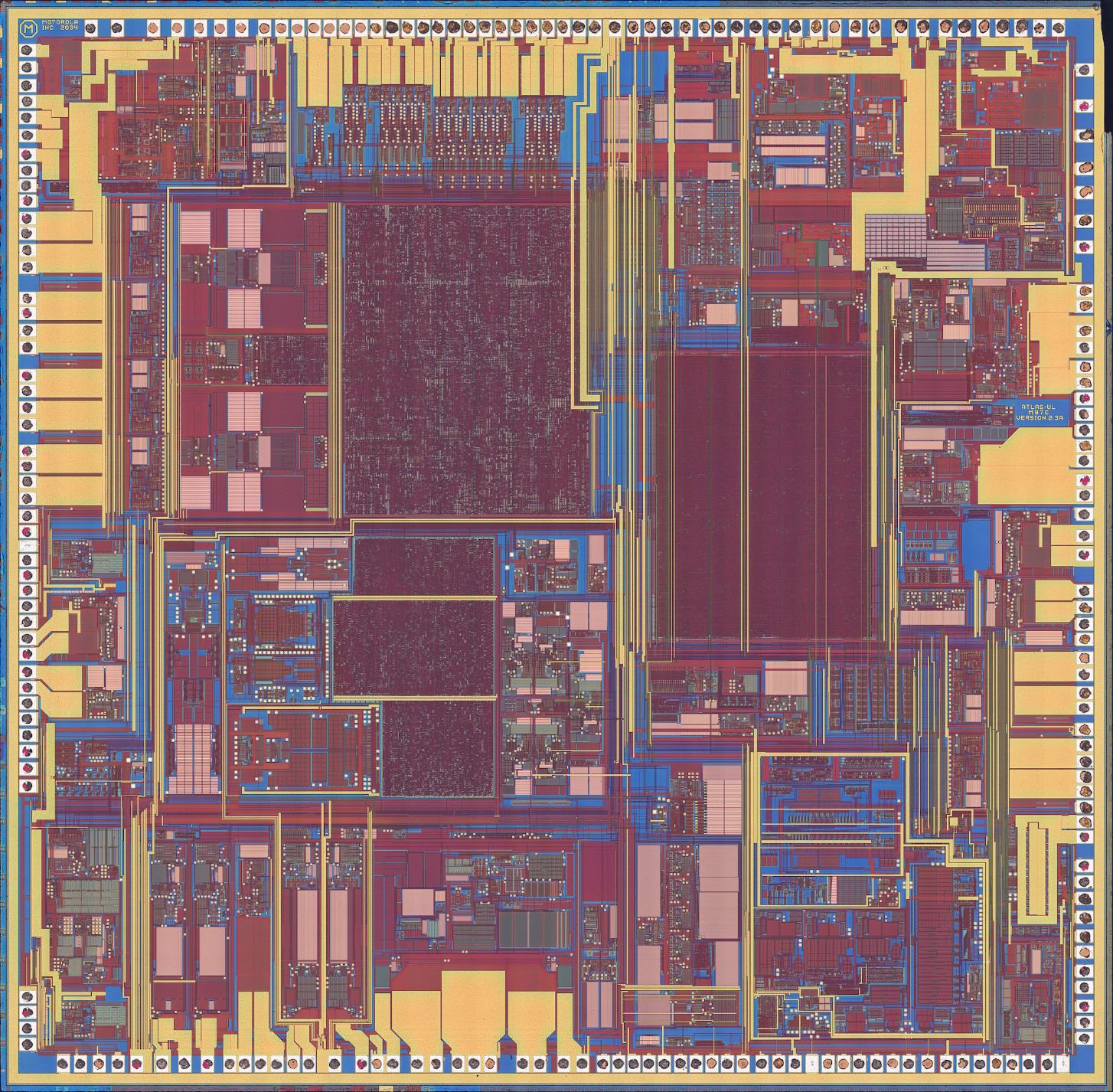
Happy #nakeddiefriday folks!
Today's specimen is p/n SC13890P23A by Motorola/Freescale. This came from an embedded cellular modem I tore out of [redacted]. The die is marked ATLAS-UL.
It is the most colourful die I have ever imaged. 
SiPron page: https://siliconpr0n.org/archive/doku.php?id=infosecdj:motorola:sc13890p23a
Preparing a talk on #programming an #AnalogComputer - using the wonderful #THAT from anabrid and my #Vectrex that has been modified to provide an additional #oscilloscope mode.
Frederik Braun �
freddy@security.plumbingReally cool blog post about permissions in browsers and how they work. https://albertofdr.github.io/web-security-class/browser/browser.permissions
buherator
buheratorhttps://blog.adafruit.com/2025/02/13/bent-broken-2025-worldwide-virtual-circuit-bending-festival/
Thibaultmol 🌈
thibaultmol@en.osm.townToday's @kagihq changelog is honestly kind of a massive deal for privacy stuff:
- Human readable privacy policy page
- Privacy pass (an open source, cryptographic verifiable way of doing searches through Kagi without them being able to see who you are)
- Official tor service
buherator
buheratorhttps://code-white.com/public-vulnerability-list/#unauthenticated-remote-code-execution-via-known-view-state-secret-in-fieldpie
This may be one of those leaked secrets MS warned about? No details unfortunately...
buherator
buheratorhttps://h0mbre.github.io/Patch_Gapping_Google_COS/
404 Media
404mediaco@mastodon.socialScoop: The databases powering doge. gov are insecure, and people outside the government have already pushed their own updates to the site to prove it:
https://www.404media.co/anyone-can-push-updates-to-the-doge-gov-website-2/
Brad Spengler
spendergrsec@bird.makeupNot sure why Google's kCTF isn't more widely known (other than by all the researchers making money from it). 44 unique successful exploits in a year against Linux kernels even running Google's out-of-tree "hardening" is a big story I'd say...
Anderson Nascimento
andersonc0d3@infosec.exchangeCVE-2025-26519: musl libc: input-controlled out-of-bounds write primitive in iconv()
Paragon Initiative Enterprises
paragon@phpc.socialAccelerating The Adoption of Post-Quantum Cryptography with PHP
https://paragonie.com/blog/2025/02/accelerating-adoption-post-quantum-cryptography
#PHP #crypto #cryptography #HPKE #KEMs #MLKEM #MLDSA #SLHDSA #postquantum #programming #webdev #MLS #rfc9180 #rfc9420
Kim Zetter
kimzetter@infosec.exchangeNew court documents shed light on what a 25-year-old DOGE worker named Marko Elez did inside Treasury payment systems, including which systems he accessed, security measures Treasury IT staff took to limit his access and activity, and whether he really did have the ability to change source code on production systems as previously reported. The new documents, signed affidavits filed in court by career executives at the Treasury department not political appointees, suggest that the situation inside the Treasury department is more nuanced than previously reported. Here's my story. If you find the piece valuable, please consider becoming a paid subscriber to my Zero Day publication, which is reader supported. https://www.zetter-zeroday.com/court-documents-shed-new-light-on-doge-access-and-activity-at-treasury-department/