Posts
2505Following
611Followers
1347MADWeb Workshop
madwebwork@infosec.exchangeThe #MADWeb '25 program is live!
We've got 9 full papers, 3 work-in-progress papers, and 2 exciting keynotes lined up. Huge thanks to all the authors and the program committee!
Check out the details and get ready for a great event! 🔥
🔗 https://madweb.work/#program
See you in San Diego!
buherator
buheratorbuherator
buheratorhttps://blog.0patch.com/2025/02/micropatches-released-for-microsoft.html
Baudouin Feildel
amdg2@diaspodon.frThanks @bagder for providing the Firefox ca bundle publicly in an accessible way here: https://curl.se/docs/caextract.html
Extra kudos for the appropriate curl command-line to automatically download the latest version!
clearbluejar
clearbluejar@infosec.exchangeJust released #ghidriff v0.8.0 - Ghidra 11.3 Support + PyGhidra 🔥👀
This release uses the latest PyGhidra now officially supported by Ghidra 🤓💪
https://github.com/clearbluejar/ghidriff/releases/tag/v0.8.0
🔋 included!
buherator
buheratorShow content
I mean how would you beat Schwarzenegger teaming up with Gremlins and the Cobra Commander (and others) to mutilate the clones of Steven Segal?
https://listenable-records.bandcamp.com/album/big-trouble
Recon
recon@infosec.exchangeRecon 2025 Have been Annonced! 20th year Anniversary https://recon.cx June 23-29.
Picard Tips
PicardTips@mas.toPicard management tip: It's okay not to know things. Practice saying "I don't know." Go ahead. Say it.
pty
pty@chaos.socialKennt ihr #wuppiefuzz ?
Ist ein coverage-guided REST-Fuzzer und Open-Source.
Bin heute darüber gestolpert und dacht das ist teilenswert.
Trend Zero Day Initiative
thezdi@infosec.exchangeOur blog site is having a moment, and @TheDustinChilds is stuck on a plane in DFW, but nothing stops Patch Tuesday. There's 2 Microsoft bugs being exploited in the wild and some things we've never seen before. Read all the details at https://www.zerodayinitiative.com/blog/2025/2/11/the-february-2025-security-update-review
buherator
buheratorhttps://talosintelligence.com/vulnerability_reports#disclosed
CVE-2024-0142, CVE-2024-0143, CVE-2024-0144, CVE-2024-0145
buherator
buheratorhttps://www.akamai.com/blog/security-research/2025-february-fortinet-critical-vulnerabilities
"We%27ll go through the processes of getting the firmware, decrypting, setting up a debugger, and finally looking for vulnerabilities." -> Mad respect!
Rust Weekly 🦀
rust_discussions@mastodon.socialA demonstration of writing a simple Windows driver in Rust
https://scorpiosoftware.net/2025/02/08/writing-a-simple-driver-in-rust/
Discussions: https://discu.eu/q/https://scorpiosoftware.net/2025/02/08/writing-a-simple-driver-in-rust/
quarkslab
quarkslab@infosec.exchangeGood tools are made of bugs: How to monitor your Steam Deck with one byte.
Finding and exploiting two vulnerabilities in AMD's UEFI firmware for fun and gaming.
A Christmas gift in February, brought to you by the incredible @pwissenlit 🫶
https://blog.quarkslab.com/being-overlord-on-the-steam-deck-with-1-byte.html
screaminggoat
screaminggoat@infosec.exchangeElecticIQ: Sandworm APT Targets Ukrainian Users with Trojanized Microsoft KMS Activation Tools in Cyber Espionage Campaigns
EclecticIQ analysts assess with high confidence that Sandworm (APT44), a threat actor supporting Russia's Main Intelligence Directorate (GRU), is actively conducting a cyber espionage campaign against Ukrainian Windows users. Likely ongoing since late 2023, following Russia's invasion of Ukraine, Sandworm leverages pirated Microsoft Key Management Service (KMS) activators and fake Windows updates to deliver a new version of BACKORDER, a loader previously associated with the group. BACKORDER ultimately deploys Dark Crystal RAT (DcRAT), enabling attackers to exfiltrate sensitive data and conduct cyber espionage.
Multiple pieces of evidence strongly link this campaign to Sandworm, also tracked by CERT-UA as UAC-0145, based on recurring use of ProtonMail accounts in WHOIS records, overlapping infrastructure, and consistent Tactics, Techniques and Procedures (TTPs). Additionally, the reuse of BACKORDER, DcRAT, and TOR network mechanisms, along with debug symbols referencing a Russian-language build environment, further reinforce confidence in Sandworm's involvement. Yara and Sigma rules, and Indicators of Compromise are listed.
#russia #sandworm #apt44 #gru #threatintel #IOC #yara #sigma #malwareanalysis #infosec #cybersecurity #cti #cyberthreatintelligence
CFG Bot 🤖
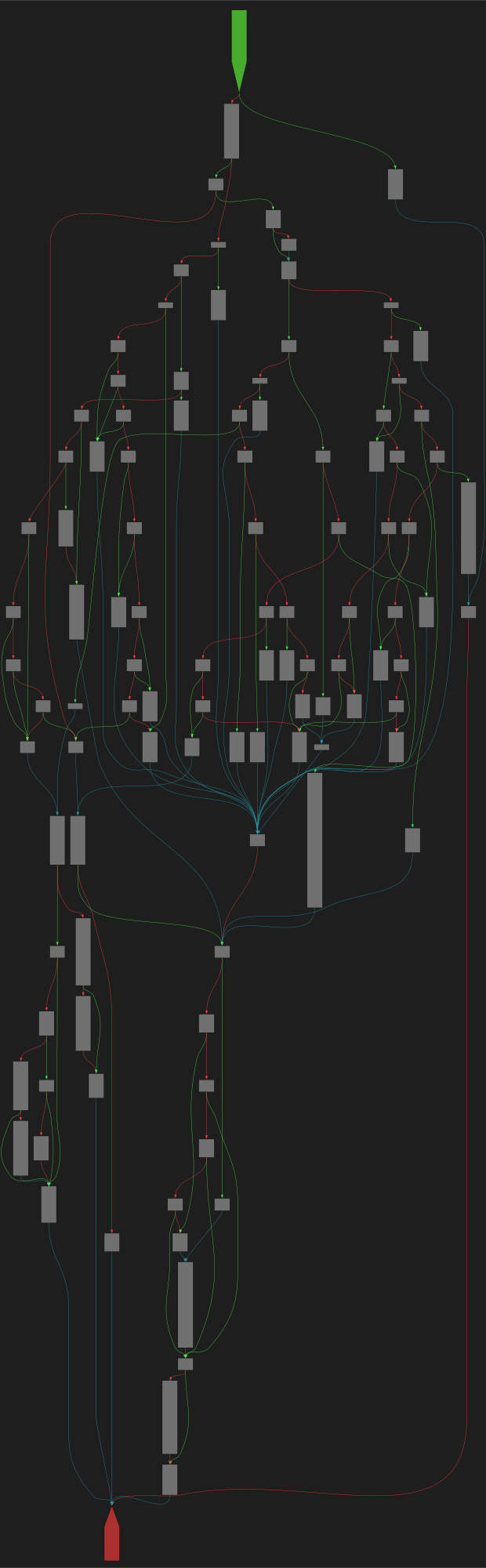
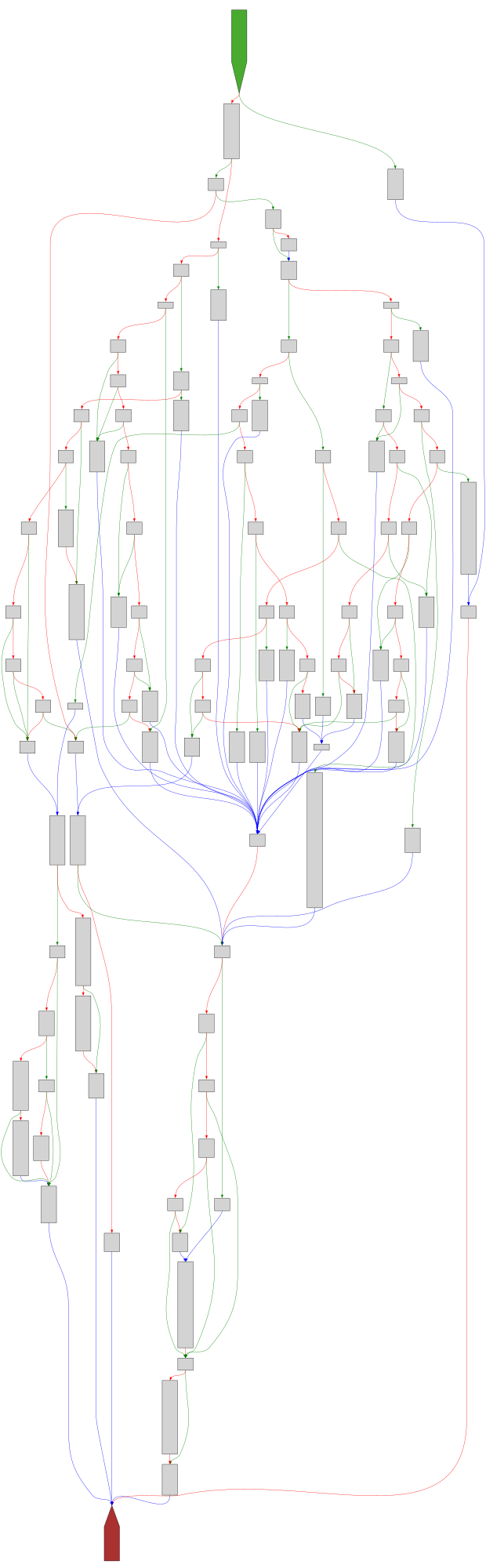
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a785720
getBasicDataType
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a785720.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a785720.json&colors=light
Will Dormann
wdormann@infosec.exchangeApparently Google is just shitty.
No duress signal or anything here. Just trying to fit in by being shitty. 🤦♂️