Posts
3394Following
713Followers
1581Anja Kreysing
anja@sonomu.clubfor a reason:
https://european-alternatives.eu
@european_alternatives
buherator
buheratorShow content
https://www.youtube.com/watch?v=WX656XCml9Q
This one deserves more views!
buherator
buheratorAs you can see, debugging #Ghidra works like a charm in IDEA, and the configuration is 15 lines of XML without hardcoded paths*:
https://github.com/radareorg/ghidra-r2web/blob/master/GhidraR2Web/.idea/runConfigurations/RunGhidra.xml
* You have to set a single Path Variable in your IDEA instance to specify the location of your Ghidra installation
Ange
Ange@mastodon.socialIn the next livestream tonight, we’ll hexplore more advanced hash collisions tricks.
https://www.youtube.com/live/fCNx2cO0Q98?si=xln4a4n_5BJ9wR5c
NOELREPORTS 🇪🇺 🇺🇦
noelreports@mstdn.socialThe moment Estonia disconnected its power grid from Russia has been shared online. A historic step toward energy independence.
Golang Weekly
golang_discussions@mastodon.socialWhy is Carbon being developed when Google already has Go
https://builtin.com/software-engineering-perspectives/google-carbon
Discussions: https://discu.eu/q/https://builtin.com/software-engineering-perspectives/google-carbon
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a8f937c
_update_driver_config_for_pmu_counters
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a8f937c.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a8f937c.json&colors=light
Alex Plaskett
alexjplaskett@bird.makeupThe Path of a Packet Through the Linux Kernel
https://www.net.in.tum.de/fileadmin/TUM/NET/NET-2024-04-1/NET-2024-04-1_16.pdf
kxxt
kxxt@mastodon.socialNew Blog Post: Fully Dynamically Linked Rust Binary: An Experiment
https://www.kxxt.dev/blog/fully-dynamically-linked-rust-binary/
BrianKrebs
briankrebs@infosec.exchangeWired has been killing it lately on covering what may well be the biggest security breach this country has ever seen. They obtained an email sent by an intelligence team within the U.S. Treasury Department that referred to Musk's actions to unilaterally slash and burn government agencies as "the single greatest insider threat risk" they have ever faced.
"There is ongoing litigation, congressional legislation, and widespread protests relating to DOGE’s access to Treasury and the Bureau of the Fiscal Service,” the email reads, per the tech-focused outlet. "If DOGE members have any access to payment systems, we recommend suspending that access immediately and conducting a comprehensive review of all actions they may have taken on these systems."
"There is reporting at other federal agencies indicating that DOGE members have performed unauthorized changes and locked civil servants out of the sensitive systems they gained access to,” the ‘Recommendations’ portion of the email continues. “We further recommend that DOGE members be placed under insider threat monitoring and alerting after their access to payment systems is revoked. Continued access to any payment systems by DOGE members, even “read only,” likely poses the single greatest insider threat risk the Bureau of the Fiscal Service has ever faced.”
https://www.wired.com/story/treasury-bfs-doge-insider-threat
Meanwhile, The Washington Post reports the warning came from a Treasury threat center run by the govt contractor Booz Allen Hamilton. The Post reports that late Friday, Booz Allen said it had “removed” a subcontractor who wrote the warning and would seek to retract or amend it. “The draft report was prepared by a subcontractor to Booz Allen and contained unauthorized personal opinions that are not factual or consistent with our standards,” company spokesperson Jessica Klenk said. Booz Allen won more than $1 billion in multiyear U.S. government contracts last year.
https://www.washingtonpost.com/national-security/2025/02/07/doge-treasury-payments-system-warning/
buherator
buheratorhttps://github.com/microsoft/vscode-java-debug/issues/722
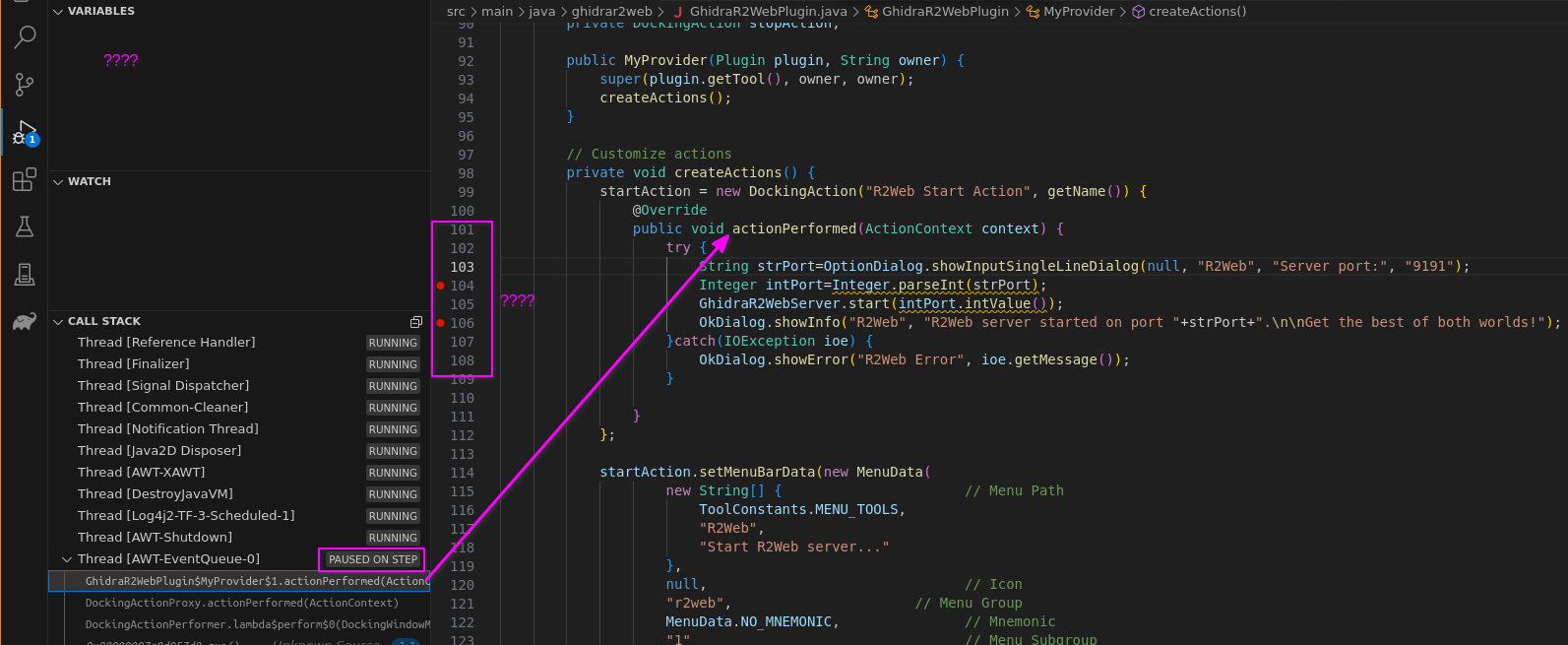
I also have to manually dig up the paused thread, there I can find the locals but still don't have visual indication about where exactly my code is paused...
Ian Smith
katachora@hachyderm.ioHow much of the time/energy/money in tech is consumed solving problems that are created by the business plan?
Example: I'm reading an article on performance monitoring for Web and I can't stop my brain from saying outrageous shit like, "If you didn't ship metric tons of javascript and only used HTML and CSS then you wouldn't need to run all this expensive infrastructure to tell you that your app performs like shit." Which is not what anyone, anywhere, seems to want to hear.
Truth being unhelpful is also unhelpful.
buherator
buherator- Copying .vscode/ template directory to the original (Eclipse-based) repo
- Fill in the path of my Ghidra installation in build.gradle (this can be pbbly done more elegantly by setting the env)
- Renaming the .classpath file produced by Eclipse, as it confuses VSCode
- Manually loading the plugin from Code Browser's File/Configure menu
The debugging experince is unfortunately shit so far, I can't even see which breakpoint is hit - I'll keep on reading VSCode tutorials...
buherator
buherator1) You'll need the Extension Pack for Java (from MS, not Oracle's crap!)
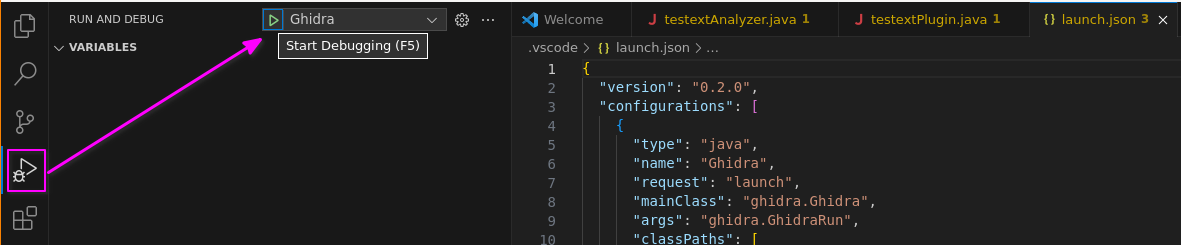
2) Ghidra launch configurations are available under the "bug with play button" sidebar icon
+1) Directory/workspace names are not necessarily valid Java package names, but Ghidra generates the code and the fs structure anyway
Now I'm trying to figure out why the sample code is not actually loaded to Ghidra when debugging...
buherator
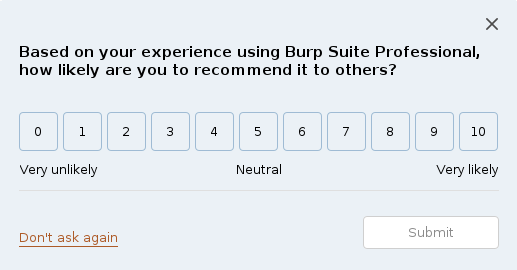
buheratorThis supposed to be a professional tool (that users pay for btw) not a fucking marketing platform.
/cc @albinowax
Jeff Moss
thedarktangent@defcon.socialToday was my last day at ONCD. I turned in my White House pass, laptop and phone.
I was explaining why I was resigning, while they were explaining the Special Governmental Employee (SGE) program was being eliminated. We both got to the same result. No hard feelings, I wish the best for ONCD and Cyber, there are a lot of important and pressing challenges ahead.
On the way out I watched movers empty out the Pandemic Readiness office. 😦 I went for drinks with friends.
You remember #Apple scanning all images on your #mobile device?
If you have an #Android #phone, a new app that doesn't appear in your menu has been automatically and silently installed (or soon will be) by #Google. It is called #AndroidSystemSafetyCore and does exactly the same - scan all images on your device as well as all incoming ones (via messaging). The new spin is that it does so "to protect your #privacy".
You can uninstall this app safely via System -> Apps.
https://developers.google.com/android/binary_transparency/google1p/overview