Posts
2476Following
654Followers
1479kxxt
kxxt@mastodon.socialNew Blog Post: Fully Dynamically Linked Rust Binary: An Experiment
https://www.kxxt.dev/blog/fully-dynamically-linked-rust-binary/
BrianKrebs
briankrebs@infosec.exchangeWired has been killing it lately on covering what may well be the biggest security breach this country has ever seen. They obtained an email sent by an intelligence team within the U.S. Treasury Department that referred to Musk's actions to unilaterally slash and burn government agencies as "the single greatest insider threat risk" they have ever faced.
"There is ongoing litigation, congressional legislation, and widespread protests relating to DOGE’s access to Treasury and the Bureau of the Fiscal Service,” the email reads, per the tech-focused outlet. "If DOGE members have any access to payment systems, we recommend suspending that access immediately and conducting a comprehensive review of all actions they may have taken on these systems."
"There is reporting at other federal agencies indicating that DOGE members have performed unauthorized changes and locked civil servants out of the sensitive systems they gained access to,” the ‘Recommendations’ portion of the email continues. “We further recommend that DOGE members be placed under insider threat monitoring and alerting after their access to payment systems is revoked. Continued access to any payment systems by DOGE members, even “read only,” likely poses the single greatest insider threat risk the Bureau of the Fiscal Service has ever faced.”
https://www.wired.com/story/treasury-bfs-doge-insider-threat
Meanwhile, The Washington Post reports the warning came from a Treasury threat center run by the govt contractor Booz Allen Hamilton. The Post reports that late Friday, Booz Allen said it had “removed” a subcontractor who wrote the warning and would seek to retract or amend it. “The draft report was prepared by a subcontractor to Booz Allen and contained unauthorized personal opinions that are not factual or consistent with our standards,” company spokesperson Jessica Klenk said. Booz Allen won more than $1 billion in multiyear U.S. government contracts last year.
https://www.washingtonpost.com/national-security/2025/02/07/doge-treasury-payments-system-warning/
buherator
buheratorhttps://github.com/microsoft/vscode-java-debug/issues/722
I also have to manually dig up the paused thread, there I can find the locals but still don't have visual indication about where exactly my code is paused...
Ian Smith
katachora@hachyderm.ioHow much of the time/energy/money in tech is consumed solving problems that are created by the business plan?
Example: I'm reading an article on performance monitoring for Web and I can't stop my brain from saying outrageous shit like, "If you didn't ship metric tons of javascript and only used HTML and CSS then you wouldn't need to run all this expensive infrastructure to tell you that your app performs like shit." Which is not what anyone, anywhere, seems to want to hear.
Truth being unhelpful is also unhelpful.
buherator
buherator- Copying .vscode/ template directory to the original (Eclipse-based) repo
- Fill in the path of my Ghidra installation in build.gradle (this can be pbbly done more elegantly by setting the env)
- Renaming the .classpath file produced by Eclipse, as it confuses VSCode
- Manually loading the plugin from Code Browser's File/Configure menu
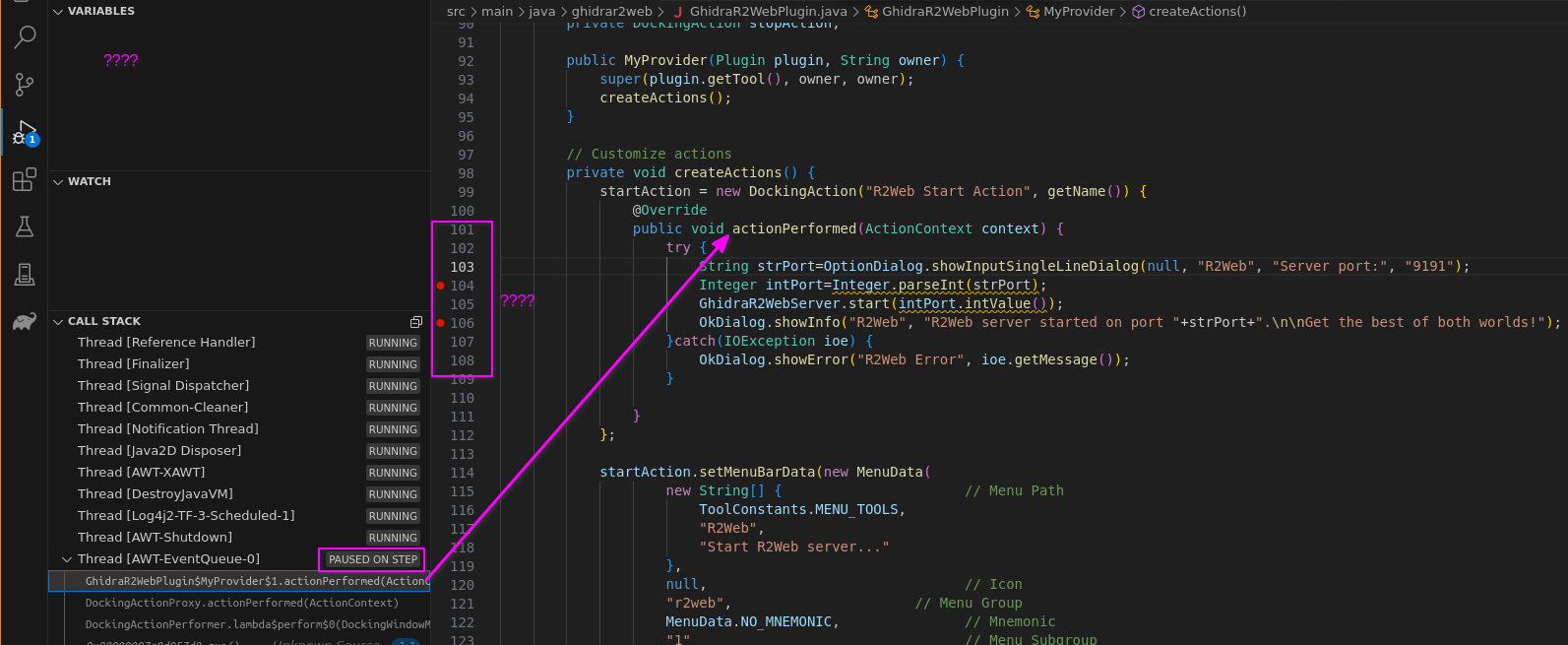
The debugging experince is unfortunately shit so far, I can't even see which breakpoint is hit - I'll keep on reading VSCode tutorials...
buherator
buherator1) You'll need the Extension Pack for Java (from MS, not Oracle's crap!)
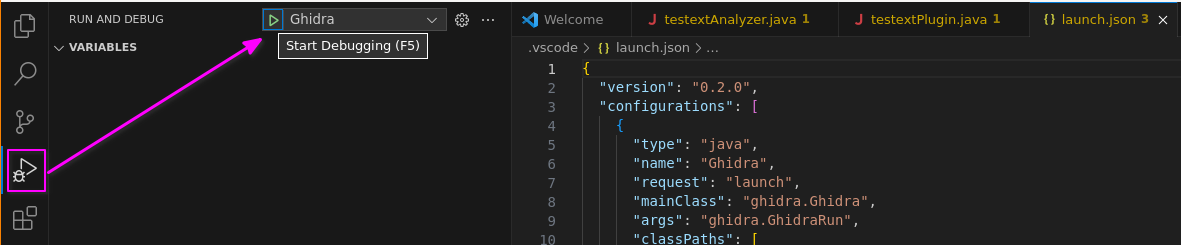
2) Ghidra launch configurations are available under the "bug with play button" sidebar icon
+1) Directory/workspace names are not necessarily valid Java package names, but Ghidra generates the code and the fs structure anyway
Now I'm trying to figure out why the sample code is not actually loaded to Ghidra when debugging...
buherator
buheratorThis supposed to be a professional tool (that users pay for btw) not a fucking marketing platform.
/cc @albinowax
Jeff Moss
thedarktangent@defcon.socialToday was my last day at ONCD. I turned in my White House pass, laptop and phone.
I was explaining why I was resigning, while they were explaining the Special Governmental Employee (SGE) program was being eliminated. We both got to the same result. No hard feelings, I wish the best for ONCD and Cyber, there are a lot of important and pressing challenges ahead.
On the way out I watched movers empty out the Pandemic Readiness office. 😦 I went for drinks with friends.
You remember #Apple scanning all images on your #mobile device?
If you have an #Android #phone, a new app that doesn't appear in your menu has been automatically and silently installed (or soon will be) by #Google. It is called #AndroidSystemSafetyCore and does exactly the same - scan all images on your device as well as all incoming ones (via messaging). The new spin is that it does so "to protect your #privacy".
You can uninstall this app safely via System -> Apps.
https://developers.google.com/android/binary_transparency/google1p/overview
If you are using Signal, and you are doing something the government considers illegal, the way they are going to read your messages about it is they will arrest the person you sent the messages *to*, and make your counterparty show them the logs. We know this because this technique came up again and again in, for example, the Jan. 6 court filings.
There may, hypothetically, be other Signal exploits available to a government, but this is the one they will use, because it works.
Valentin Gosu
valenting@fosstodon.orgI just published a blog post about getaddrinfo and all the other weird DNS APIs that we use in Firefox to resolve HTTPS records.
https://valentin.gosu.se/blog/2025/02/getaddrinfo-sucks-everything-else-is-much-worse
All this was part of the talk I gave at FOSDEM last weekend.
modzero
modzero@infosec.exchangeROPing our way to “Yay, RCE” - and a lesson in the importance of a good nights sleep!
From vulnerability to exploit - follow our Colleague Michaels journey of developing an ARM ROP chain to exploit a buffer overflow in uc-http
Via Return-Oriented Programming chain small code snippets, or gadgets, already present in a program’s memory can be leveraged
By chaining these gadgets together, they can execute arbitrary code without injecting anything new
Dive into the process of reverse engineering, gadget hunting, and crafting a working exploit.
Learn all about it in Michaels full report.
buherator
buheratorhttps://blog.0patch.com/2025/02/micropatches-released-for-windows-ole.html
daniel:// stenberg://
bagder@mastodon.socialDaniel weekly February 7, 2025
https://lists.haxx.se/pipermail/daniel/2025-February/000099.html
old security, ssh security, BBC, URLs from file, you can help, curl up CVE-2024-7264, EOSAwards, Workshop, FOSDEM, 1337, release, regressions, release candidates, codeql, no goods
Enfys J. Book [they/them]
EnfysBook@kind.socialIf you use Signal, Discord, or any other messaging app and you DON'T want Google or Apple monitoring/reading/learning from your messages, follow these steps.
Android:
1. Open Google app
2. Tap your profile photo
3. Settings
4. Google Assistant
5. "Your Apps"
6. Choose the app (e.g., Signal)
7. Toggle "Let your assistant learn from this app" off
iPhone:
1. Settings
2. Apps
3. Choose the app (e.g., Signal)
4. Toggle Apple intelligence or Siri settings to off (“learn from this app”)
/r/netsec
_r_netsec@infosec.exchangeWindows Telephony Services: 2025 Patch Diffing & Analysis https://blog.securelayer7.net/windows-telephony-services-2025-patch-diffing-and-analysis-pt-1/