Posts
3368Following
712Followers
1580Paragon Initiative Enterprises
paragon@phpc.socialNew from our team: A PHP implementation of RFC 9180 (HPKE - Hybrid Public-Key Encryption):
https://github.com/paragonie/hpke-php
This should serve as building block for more secure protocols (i.e., RFC 9420 a.k.a. Messaging Layer Security)/
This would, in turn, enable PHP developers to write software that communicates with MLS-compatible end-to-end encrypted messaging services.
screaminggoat
screaminggoat@infosec.exchangeGoogle Android zero-day: Android Security Bulletin February 2025
46 CVEs in Framework (1 critical, 45 high severity) cc: @buherator
Note: There are indications that CVE-2024-53104 may be under limited, targeted exploitation.
#CVE_2024_53104 #android #google #vulnerability #zeroday #eitw #activeexploitation #infosec #cybersecurity
Nspace
nspace@infosec.exchangeOur newest research project is finally public! We can load malicious microcode on Zen1-Zen4 CPUs!
https://github.com/google/security-research/security/advisories/GHSA-4xq7-4mgh-gp6w
screaminggoat
screaminggoat@infosec.exchangeQualcomm: February 2025 Security Bulletin
Qualcomm has 7 propriety vulnerabilities (1 critical, 5 high, 1 medium severity) and 17 open source vulnerabilities (1 critical, 9 high, 7 medium). That critical vulnerability CVE-2024-49837 (7.8 high) is Improper Validation of Array Index in Automotive OS Platform QNX. No mention of exploitation. h/t @cR0w
#qualcomm #patchtuesday #vulnerability #infosec #cybersecurity
buherator
buheratorhttps://connormcgarr.github.io/km-shadow-stacks/
CFG Bot 🤖
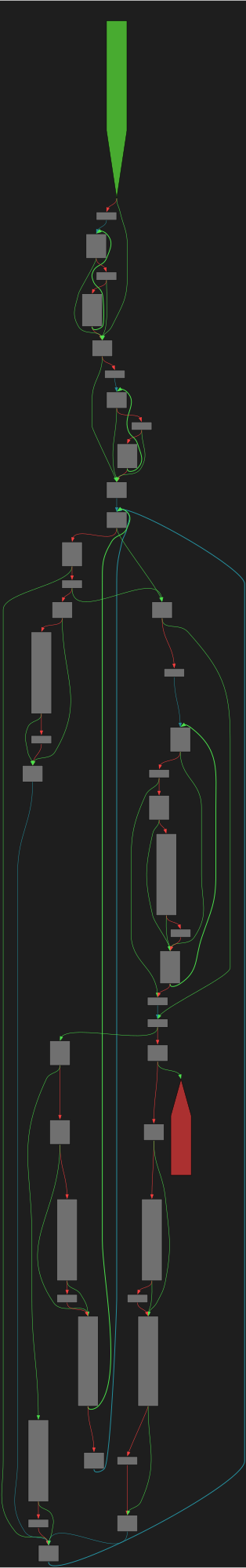
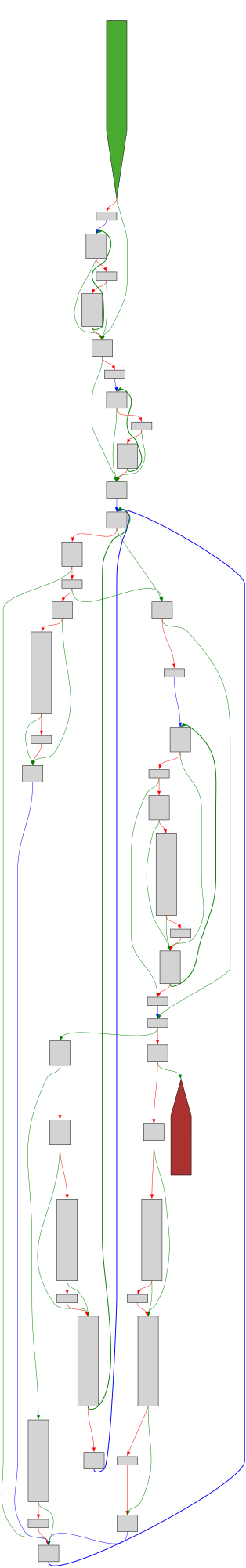
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75aa68af0
_Partition_by_median_guess_unchecked<interval<unsigned___int64>_*,`dexscan_scanfile'::__l183::compare_intervals>
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75aa68af0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75aa68af0.json&colors=light
Ken Shirriff
kenshirriff@oldbytes.spaceWhat is the origin of the word "mainframe"? Digging through archives, I traced it back to 1953. The IBM 701 computer was built from "frames": power frames, a storage frame, a drum frame, and the main frame. This 1953 drawing from the Installation Manual shows the dimensions of the "main frame". 1/n
buherator
buheratorhttps://jprx.io/cve-2025-24118/
buherator
buheratorhttps://starlabs.sg/blog/2025/12-mali-cious-intent-exploiting-gpu-vulnerabilities-cve-2022-22706/
pancake 
pancake@infosec.exchange
“For Sale: Binaries Compiled From Hand-Crafted Artisanal Code”
Darryl Pogue
dpogue@mastodon.socialSo Apple has open-sourced the XCBuild system used internally by Xcode as Swift-Build: https://github.com/swiftlang/swift-build
Based on their previously open-source llbuild project.
It includes support for Windows and Linux (using clang-cl on Windows), but does not currently seem to have a way to make use of it outside of Swift package manager or Xcode.
buherator
buheratorhttps://www.ophionsecurity.com/post/cisco-webex-connect-vulnerability-unauthenticated-access-to-all-chats
buherator
buheratorhttps://googleprojectzero.blogspot.com/2025/01/windows-exploitation-tricks-trapping.html
SiMpS0N
simpson@mastodon.socialCheers to 11 years of AppSec Ezine! 🎉 Huge thanks to the security community for sharing and the supporters who made this journey possible. Here's to another year of knowledge-sharing! 🚀
572nd Edition: https://pathonproject.com/zb/?871f09331bbd8d13#6ahftCLH0VYSLjlk8M+FtRW8EibTcKL+J5qO7xUUPpk=
buherator
buheratorhttps://techcommunity.microsoft.com/blog/windows-itpro-blog/understanding-the-microsoft-pluton-security-processor/4370413
James Forshaw 
tiraniddo@infosec.exchange
The second blog is about an interesting bug class in COM servers that implement IDispatch, which allows you to potentially create other objects in the process. For example every OOP COM server with IDispatch allows you to create a STDFONT object which isn’t really designed to be safely used cross process. To demo its usefulness I then use the trick to get code injection in a Windows-PPL process from where you could open protected LSASS etc. https://googleprojectzero.blogspot.com/2025/01/windows-bug-class-accessing-trapped-com.html
clearbluejar
clearbluejar@infosec.exchangeCVE-2025-21325 - 2025-Jan - ARM64 - Windows Secure Kernel Mode Elevation of Privilege
#ghidriff full diff 👀 https://gist.github.com/clearbluejar/318abe5d072eef55b9ea7c23a591726e
Incorrect permission assignment? 🧐 https://gist.github.com/clearbluejar/318abe5d072eef55b9ea7c23a591726e#skmicommitpte-diff