Posts
2475Following
655Followers
1478Jeff Atwood
codinghorror@infosec.exchangeThe history of the RAND Corporation is fascinating. And it isn't even a corporation! https://en.wikipedia.org/wiki/RAND_Corporation
Trail of Bits
trailofbits@infosec.exchangeNow accepting applications for our 2025 summer internship program!
Available tracks & examples:
AI/ML Security: Develop safety frameworks, conduct risk assessments
Application Security: Exploit kernel vulnerabilities, conduct code reviews, develop anti-DRM solutions
Blockchain: Enhance Slither/Echidna, shadow professional security audits
Cryptography: Build next-gen cryptanalysis tools, contribute to academic research
Operations: Drive strategic initiatives alongside our CEO
Details:
Duration: June - August 2025
Location: NYC or Remote
Direct mentorship from industry experts
Apply now: https://apply.workable.com/trailofbits/j/7476E8C7DC/
mahaloz
mahaloz@infosec.exchange2024 was a significant year for decompilation, constituting a possible resurgence in the field. Major talks, the thirty-year anniversary of research, movements in AI, and an all-time high for top publications in decompilation.
Join me for a retrospective:
https://mahaloz.re/dec-progress-2024
Allele Security Intelligence
allelesecurity@infosec.exchangeUse-after-free vulnerability in the CAN BCM subsystem of the Red Hat Enterprise Linux 9 and CentOS Stream 9 kernels
In recent months, our research team reported a use-after-free vulnerability in the Red Hat Enterprise Linux 9 and CentOS Stream 9 kernels. The vulnerability also affects Red Hat Enterprise Linux 9-derived distributions, such as Alma Linux 9 and Rocky Linux 9. Exploitation of the vulnerability could lead to denial of service, information disclosure, and bypass of security mitigations. The vulnerability is registered with the identifier CVE-2023-52922.
Even though the vulnerability was public and patched over a year ago in the upstream and stable branches of the Linux kernels, the kernels used by Red Hat Enterprise Linux 9, its derivatives, and CentOS Stream 9 remain vulnerable, exposing users and organizations. This delay in patching public vulnerabilities is part of the Linux ecosystem. Vulnerabilities are not patched in Linux distributions even after they become public and patched in the stable and upstream branches of the Linux kernel.
To mitigate the vulnerability while there's no update fixing it, the CAN BCM module could be removed and denied loading unless the system needs it. It is just one of several vulnerabilities not patched in widely used Linux distributions. If you need security beyond the Linux distributions you depend on can offer, we can help you. This finding results from our ongoing research into the security of Linux distributions. Allele Security Intelligence is an expert in this field.
Check out our website and contact us to learn more: https://allelesecurity.com.
Check out more details about the vulnerability here: https://access.redhat.com/security/cve/cve-2023-52922
We will publish a blog post analyzing the vulnerability.
Ivan Ožić Bebek
obivan@infosec.exchangeActive Directory Domain Services Elevation of Privilege Vulnerability (CVE-2025-21293) https://birkep.github.io/posts/Windows-LPE/
spaf
spaf@mstdn.socialOld Soviet joke repurposed for 2025:
Several times daily, a woman opens a news website, glances at the screen, then closes it.
Her spouse, curious, asks what she's doing.
The woman explains she's looking for death notices.
The spouse says that the website only has headlines, not obituaries.
The woman replies, "Oh, the obituaries I'm praying for will be headlines."
Neodyme
neodyme@infosec.exchange🔎Part 2 of our COM hijacking series is live!
This time, we discuss a vulnerability in AVG Internet Security, where we bypass an allow-list, disable self-protection, and exploit an update mechanism to escalate privileges to SYSTEM 🚀💻
https://neodyme.io/en/blog/com_hijacking_2/
Jim Blimey
jimblimey@retrochat.onlineA very happy birthday to the Sinclair ZX80 released on this day in 1980!
Ollie Whitehouse
ollie_whitehouse@infosec.exchangeWe have released a new NCSC research paper which aims to reduce the presence of 'unforgivable' vulnerabilities - in it we present a method to assess 'forgivable' vs 'unforgivable' vulnerabilities'.
https://www.ncsc.gov.uk/blog-post/eradicating-trivial-vulnerabilities-at-scale
Jan Lehnardt 
janl@narrativ.es
“Nobody asked for NFTs or the fucking Metaverse. Nobody asked for lying chatbots instead of getting to reach an actual support person that could solve your problems.”
And:“…people are challenging the notion that we all have to do AI now. Because we don’t. It’s a choice. A choice that mostly benefits monopolists.”
— @tante in https://tante.cc/2025/01/28/quoted-in-ars-technicas-article-on-tarpits-for-ai-crawlers/
buherator
buheratorCassandrich
dalias@hachyderm.ioI thought the sole gift of DeepSeek would be blowing the charade of massive compute requirements for parlor tricks, but now it looks like the allegations of "intellectual property theft" are also going to blow open the story of massive copyright infringement by OpenAI, Google, etc. 🤣 🍿 🍿 🍿
buherator
buheratorhttps://hsbp.org/tiki-calendar_edit_item.php?viewcalitemId=1939
#cryptography
Doyensec
doyensec@infosec.exchangeFollowing our attempts to contact the casdoor maintainers, we're releasing an advisory regarding their software. This vulnerability allows attackers to exfiltrate data from the identity provider (IdP) or obtain access over SCIM. Details here:
https://doyensec.com/resources/Doyensec_Advisory_UnauthenticatedSCIM-CasdoorIdP.pdf
CFG Bot 🤖
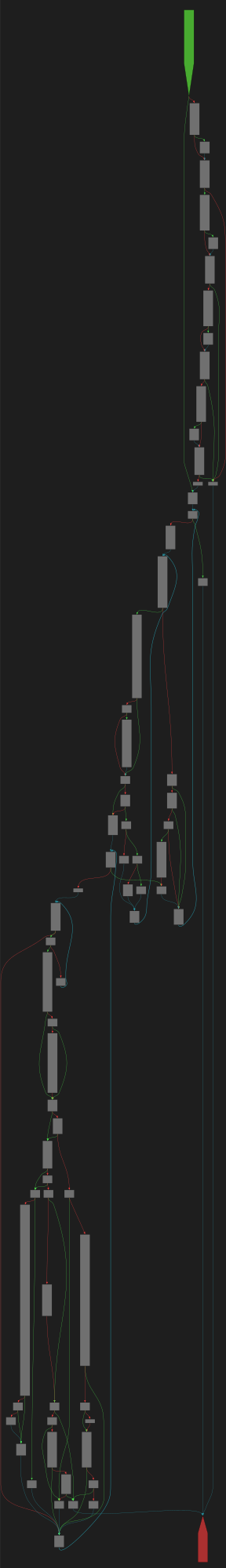
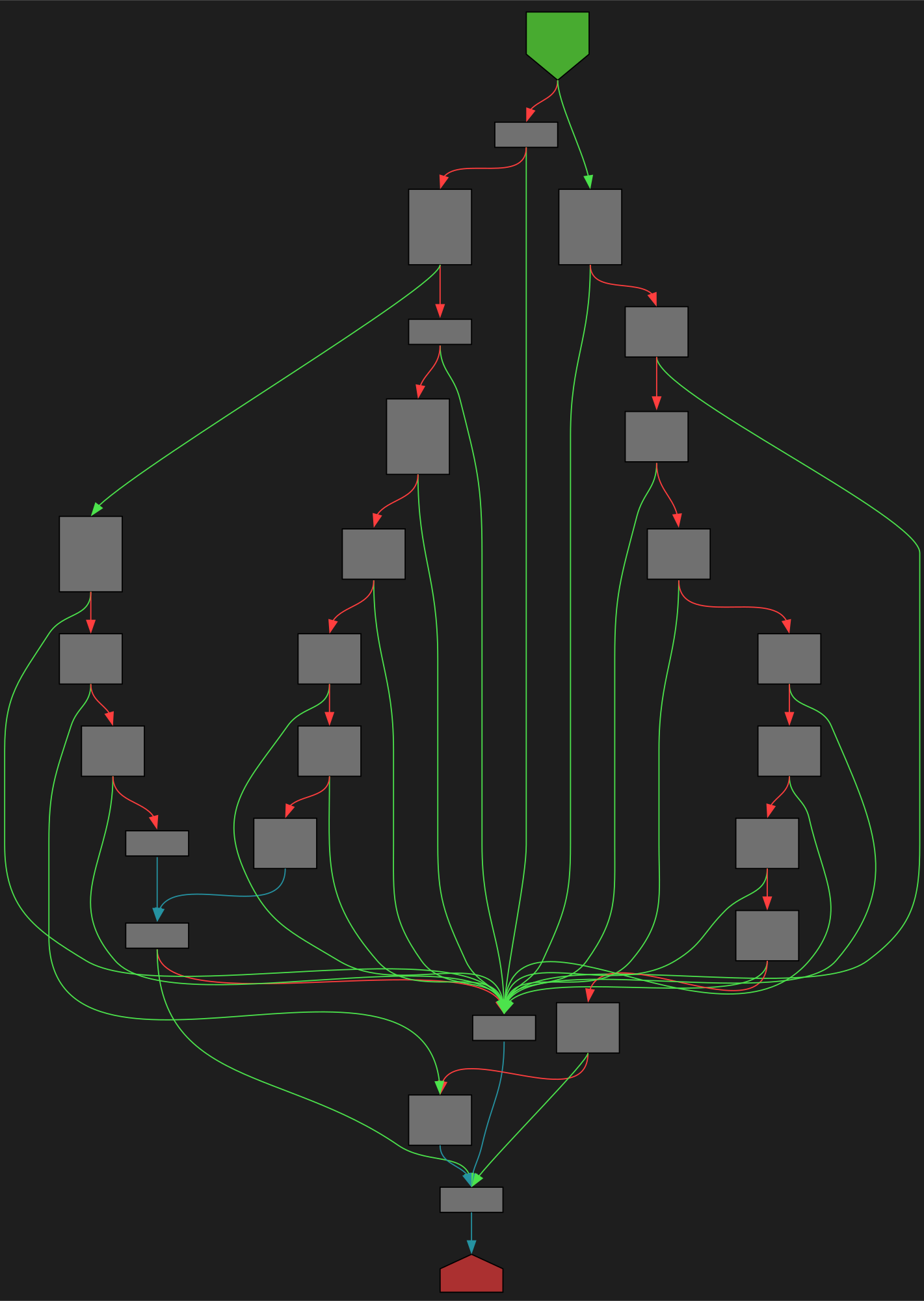
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1c7154
Lookup<struct_PeEmuHashProvider>
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1c7154.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1c7154.json&colors=light
buherator
buheratorhttps://mahaloz.re/dec-progress-2024
/by @mahaloz
Sass, David
sassdawe@infosec.exchangeSo, is anyone sueing #Microsoft in the #EuropeanUnion already because they are forcing #Copilot on their customers just like how they did with #MicrosoftTeams but this time they are also INCREASING THE PRICE AS WELL?
If not, then why not?!
CFG Bot 🤖
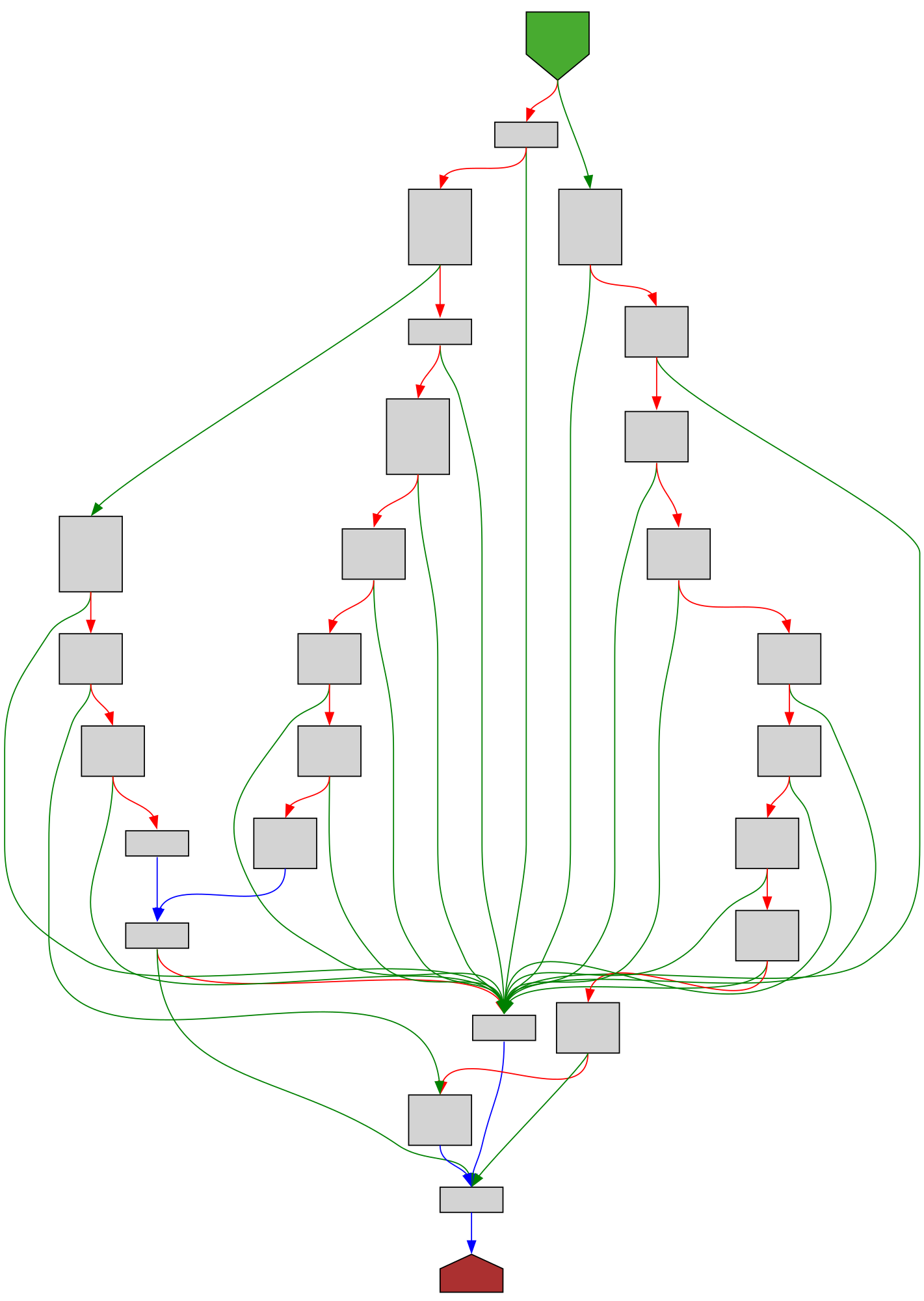
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a778a60
__acrt_MultiByteToWideChar
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a778a60.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a778a60.json&colors=light
buherator
buheratorShow content
https://abortedmetal.bandcamp.com/track/the-pain-will-be-exquisite