Posts
3368Following
712Followers
1580Jim Blimey
jimblimey@retrochat.onlineA very happy birthday to the Sinclair ZX80 released on this day in 1980!
Ollie Whitehouse
ollie_whitehouse@infosec.exchangeWe have released a new NCSC research paper which aims to reduce the presence of 'unforgivable' vulnerabilities - in it we present a method to assess 'forgivable' vs 'unforgivable' vulnerabilities'.
https://www.ncsc.gov.uk/blog-post/eradicating-trivial-vulnerabilities-at-scale
Jan Lehnardt 
janl@narrativ.es
“Nobody asked for NFTs or the fucking Metaverse. Nobody asked for lying chatbots instead of getting to reach an actual support person that could solve your problems.”
And:“…people are challenging the notion that we all have to do AI now. Because we don’t. It’s a choice. A choice that mostly benefits monopolists.”
— @tante in https://tante.cc/2025/01/28/quoted-in-ars-technicas-article-on-tarpits-for-ai-crawlers/
buherator
buheratorCassandrich
dalias@hachyderm.ioI thought the sole gift of DeepSeek would be blowing the charade of massive compute requirements for parlor tricks, but now it looks like the allegations of "intellectual property theft" are also going to blow open the story of massive copyright infringement by OpenAI, Google, etc. 🤣 🍿 🍿 🍿
buherator
buheratorhttps://hsbp.org/tiki-calendar_edit_item.php?viewcalitemId=1939
#cryptography
Doyensec
doyensec@infosec.exchangeFollowing our attempts to contact the casdoor maintainers, we're releasing an advisory regarding their software. This vulnerability allows attackers to exfiltrate data from the identity provider (IdP) or obtain access over SCIM. Details here:
https://doyensec.com/resources/Doyensec_Advisory_UnauthenticatedSCIM-CasdoorIdP.pdf
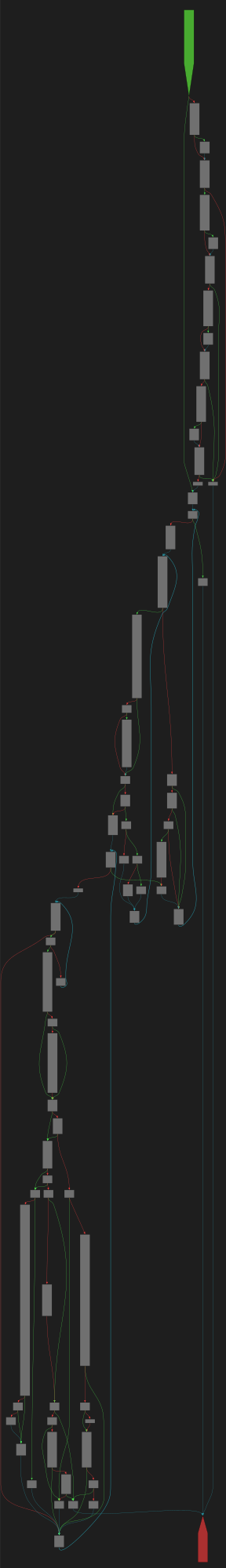
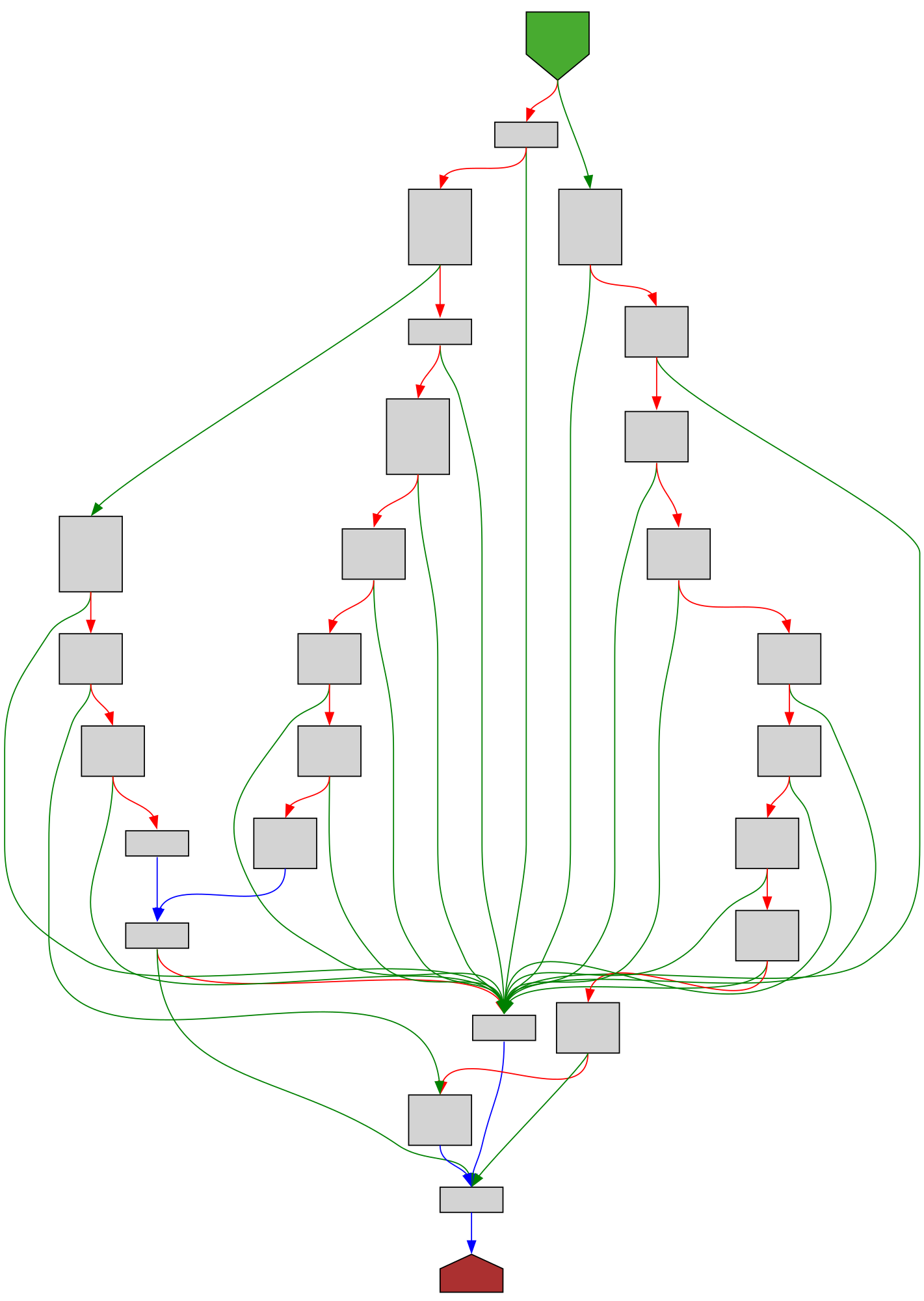
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1c7154
Lookup<struct_PeEmuHashProvider>
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1c7154.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1c7154.json&colors=light
buherator
buheratorhttps://mahaloz.re/dec-progress-2024
/by @mahaloz
Sass, David
sassdawe@infosec.exchangeSo, is anyone sueing #Microsoft in the #EuropeanUnion already because they are forcing #Copilot on their customers just like how they did with #MicrosoftTeams but this time they are also INCREASING THE PRICE AS WELL?
If not, then why not?!
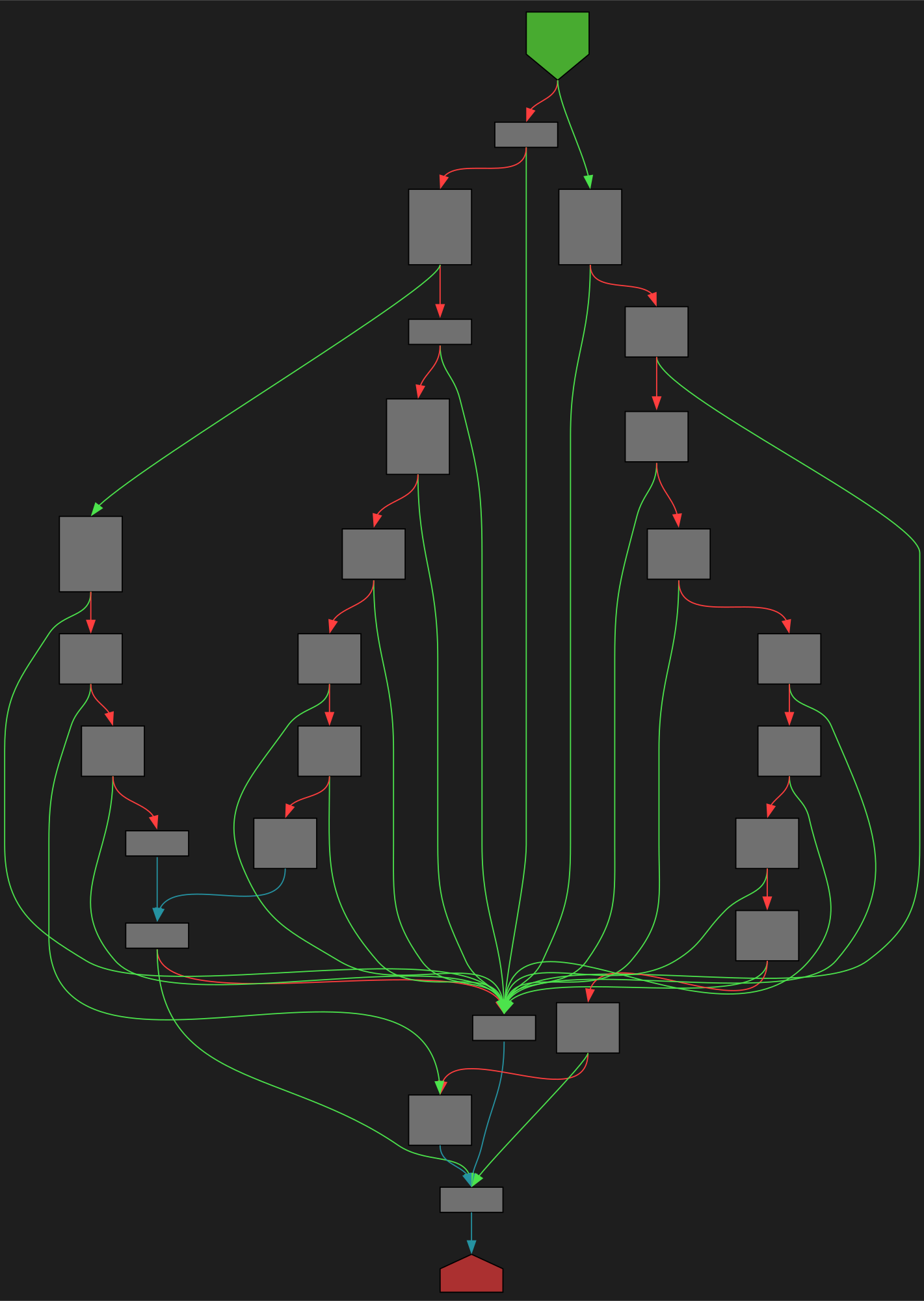
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a778a60
__acrt_MultiByteToWideChar
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a778a60.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a778a60.json&colors=light
buherator
buheratorShow content
https://abortedmetal.bandcamp.com/track/the-pain-will-be-exquisite
Paragon Initiative Enterprises
paragon@phpc.socialVersion 3.4.0 of the PHP implementation of PASETO has been released!
https://github.com/paragonie/paseto/releases/tag/v3.4.0
Includes PHP 8.4 compatibility and removes internal use of strtok(), which we don't consider a safe function for handling secret keys.
(We pulled 3.3.0 which was an accidental tag of an earlier commit in the master branch.)
buherator
buheratorShow content
https://valeofpnath.bandcamp.com/album/between-the-worlds-of-life-and-death
In light of US tech oligarchy setting its sights on Wikimedia Foundation, a historical detail I did not know before: #Wikipedia became the non-profit it is today partly as the result of a labour strike of Spanish Wikipedia editors who disagreed with the proposed inclusion of advertisements. Initially, it was not clear what revenue model Wikipedia would get, and Wales moved towards a for-profit model already a year after launch. However, rather than working for free, so Jimmy Wales could profit from their labour via advertising, Spanish contributors forked Spanish Wikipedia as the Encyclopedia Libre Universal. Under the threat of losing the editorial community of such a large language, Wales conceded and set up the non-profit.
That is to say, however imperfect they are, all the digital commons we have are the result of ongoing struggle and hard work to keep them as commons.
Via Las Redes Son Nuestras (https://www.consonni.org/es/publicaciones/las-redes-son-nuestras) by @teclista
HN Security
hnsec@infosec.exchangeAfter releasing his PoC for CVE-2024-49138, @ale98 is back with two new articles that provide background on #Windows #CLFS, analyze two distinct #vulnerabilities patched by Microsoft’s KB5048685, and describe how to #exploit them.
https://security.humanativaspa.it/cve-2024-49138-windows-clfs-heap-based-buffer-overflow-analysis-part-1
https://security.humanativaspa.it/cve-2024-49138-windows-clfs-heap-based-buffer-overflow-analysis-part-2
Taggart
mttaggart@infosec.exchangeWell, here's the cyberpunk part of the dystopia. Congrats Linux users, you're all criminals now.
Starting on January 19, 2025 Facebook's internal policy makers decided that Linux is malware and labelled groups associated with Linux as being "cybersecurity threats". Any posts mentioning DistroWatch and multiple groups associated with Linux and Linux discussions have either been shut down or had many of their posts removed.
https://distrowatch.com/weekly-mobile.php?issue=20250127#sitenews
buherator
buheratordaniel:// stenberg://
bagder@mastodon.socialVia another "crazy security scanner" report, I learn that #libcurl is installed in a #Microsoft Office and/or Teams install on Windows? According to the reddit post, in a normal install.
Does anyone know more?
The reddit page mentioning this: https://www.reddit.com/r/sysadmin/comments/1hx9eib/libcurl_vulnerability_in_office_and_teams/?sort=new
The libcurl mailing list post: