Posts
3368Following
712Followers
1579buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250123-00/?p=110800
Full system instrumentation ftw :)
Soatok Dreamseeker
soatok@furry.engineerEvery once in a while I have a really stupid idea, and then I sit down to write out what it would look like, and immediately spot a flaw in it that renders the whole thing insecure.
One of these days, one of my bad ideas is going to look back at me as someone else's implementation, deployed to production.
/r/netsec
_r_netsec@infosec.exchangeWinVisor: A proof-of-concept hypervisor-based emulator for Windows x64 binaries https://www.elastic.co/security-labs/winvisor-hypervisor-based-emulator
The Shadowserver Foundation
shadowserver@infosec.exchangeWe are sharing backdoored Ivanti Connect Secure devices that *may* have been compromised as part of a CVE-2025-0282 exploitation campaign (but also we believe may include older or other activity).
379 new backdoored instances found on 2025-01-22:
https://dashboard.shadowserver.org/statistics/combined/tree/?day=2025-01-22&source=compromised_website&source=compromised_website6&tag=cve-2025-0282%2B&geo=all&data_set=count&scale=log
Data shared daily in our Compromised Website report https://www.shadowserver.org/what-we-do/network-reporting/compromised-website-report/ tagged 'backdoor;ivanti-connect-secure'
Make sure to investigate your Ivanti Connect Secure instance if you receive an alert from us! @cisacyber mitigation advice is a good start https://www.cisa.gov/cisa-mitigation-instructions-cve-2025-0282
Thank you to @certfi for the insights and detection methods!
bert hubert 🇺🇦🇪🇺🇺🇦
bert_hubert@fosstodon.orgYesterday a user told me they couldn't log in to my parliamentary monitoring site. On investigating, I found that Microsoft email security was logging in on behalf of my user by executing a POST. This broke the single-use sign-on link. Executing POSTs is usually considered unacceptable, and in this way Microsoft again transgresses an important norm. Here's how to deal with the specific POST problem & what might be done about these transgressions in general:
https://berthub.eu/articles/posts/shifting-cyber-norms-microsoft-post/
Daniel Chateau  (シャトー・ダニエル)
(シャトー・ダニエル)
djchateau@infosec.exchange
Shitposting is valid pentesting apparently.
https://www.reddit.com/r/csMajors/comments/1i7v7hg/my_teams_intern_just_found_a_critical_bug_by/
hackaday
hackaday@hackaday.socialShellcode over MIDI? Bad Apple on a PSR-E433, Kinda
https://hackaday.com/2025/01/23/shellcode-over-midi-bad-apple-on-a-psr-e433-kinda/
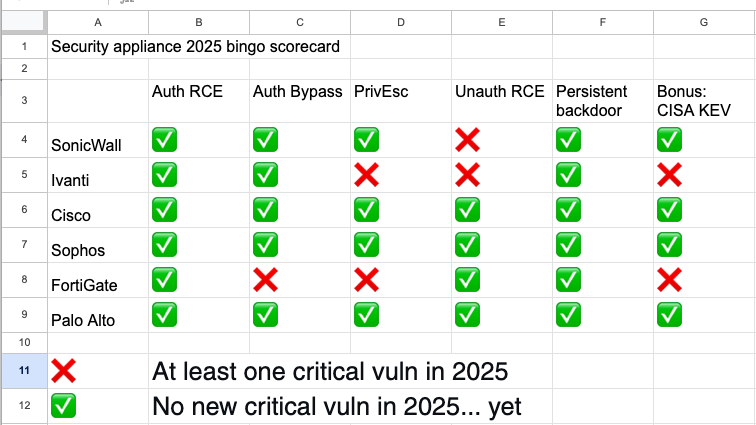
Dr. Christopher Kunz
christopherkunz@chaos.social...and here we go: Next entry in our bingo card is CVE-2025-23006 in SonicWall SMA1000.
Thanks, everyone, and remember: Current version lives at https://cku.gt/appbingo25
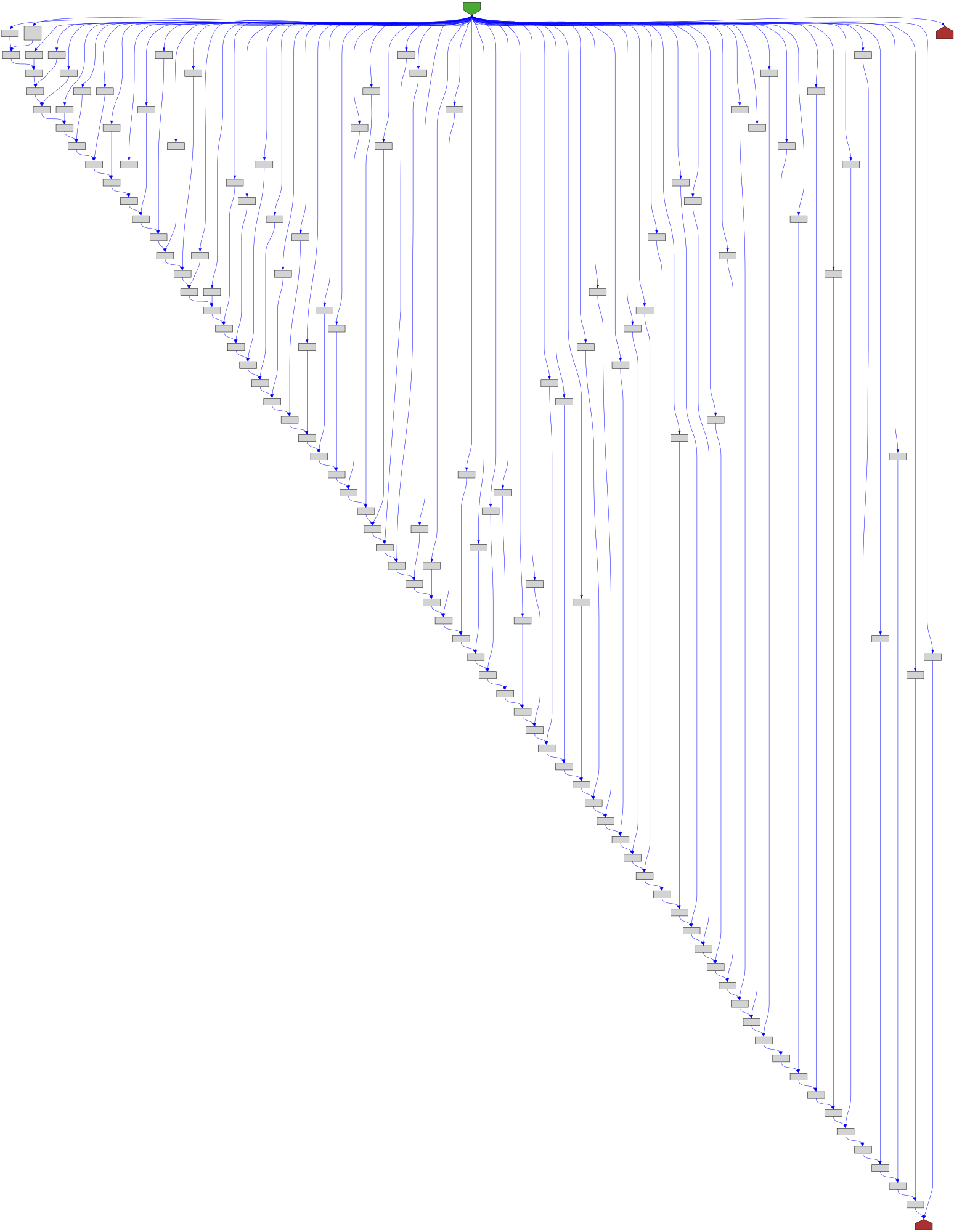
CFG Bot 🤖
cfgbot@mastodon.socialProject: microsoft/TypeScript https://github.com/microsoft/TypeScript
File: src/compiler/utilities.ts:4463 https://github.com/microsoft/TypeScript/blob/cbac1ddfc73ca3b9d8741c1b51b74663a0f24695/src/compiler/utilities.ts#L4463
function canHaveJSDoc(node: Node): node is HasJSDoc
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Futilities.ts%23L4463&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?github=https%3A%2F%2Fgithub.com%2Fmicrosoft%2FTypeScript%2Fblob%2Fcbac1ddfc73ca3b9d8741c1b51b74663a0f24695%2Fsrc%2Fcompiler%2Futilities.ts%23L4463&colors=light
screaminggoat
screaminggoat@infosec.exchangeSonicWall exploited zero-day: SMA1000 Pre-Authentication Remote Command Execution Vulnerability
CVE-2025-23006 (9.8 critical) Pre-authentication deserialization of untrusted data vulnerability has been identified in the SMA1000 Appliance Management Console (AMC) and Central Management Console (CMC), which in specific conditions could potentially enable a remote unauthenticated attacker to execute arbitrary OS commands.
IMPORTANT: SonicWall PSIRT has been notified of possible active exploitation of the referenced vulnerability by threat actors
cc: @goatyell @cR0w @GossiTheDog @briankrebs
#zeroday #CVE_2025_23006 #sonicwall #vulnerability #CVE #infosec #cybersecurity #eitw #activeexploitation
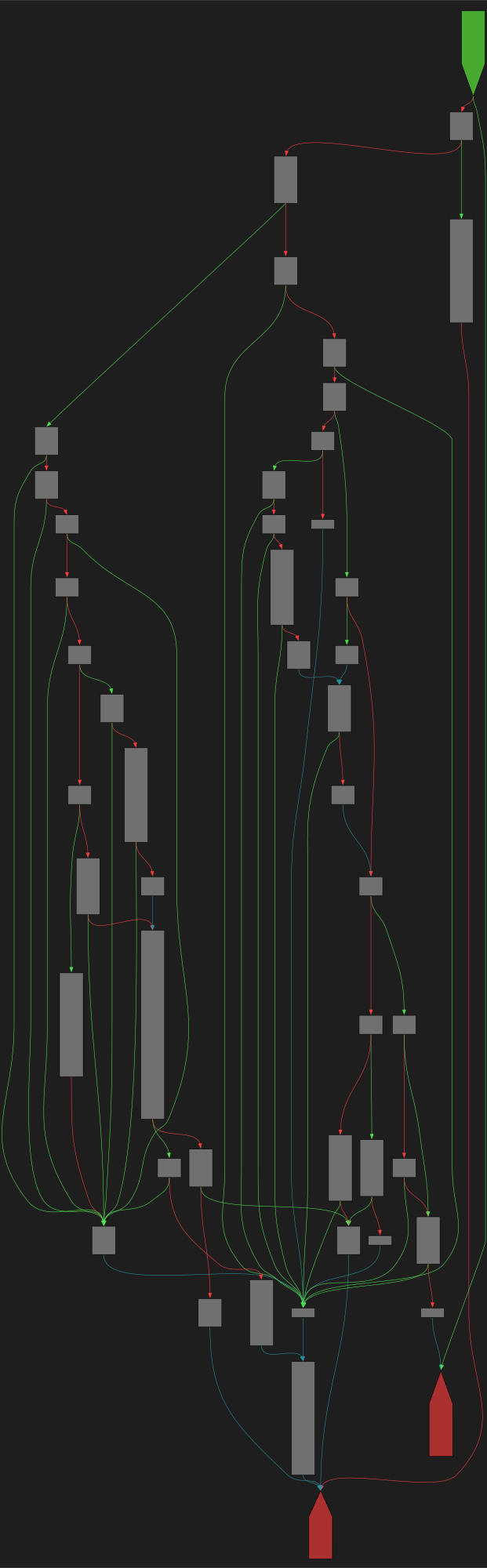
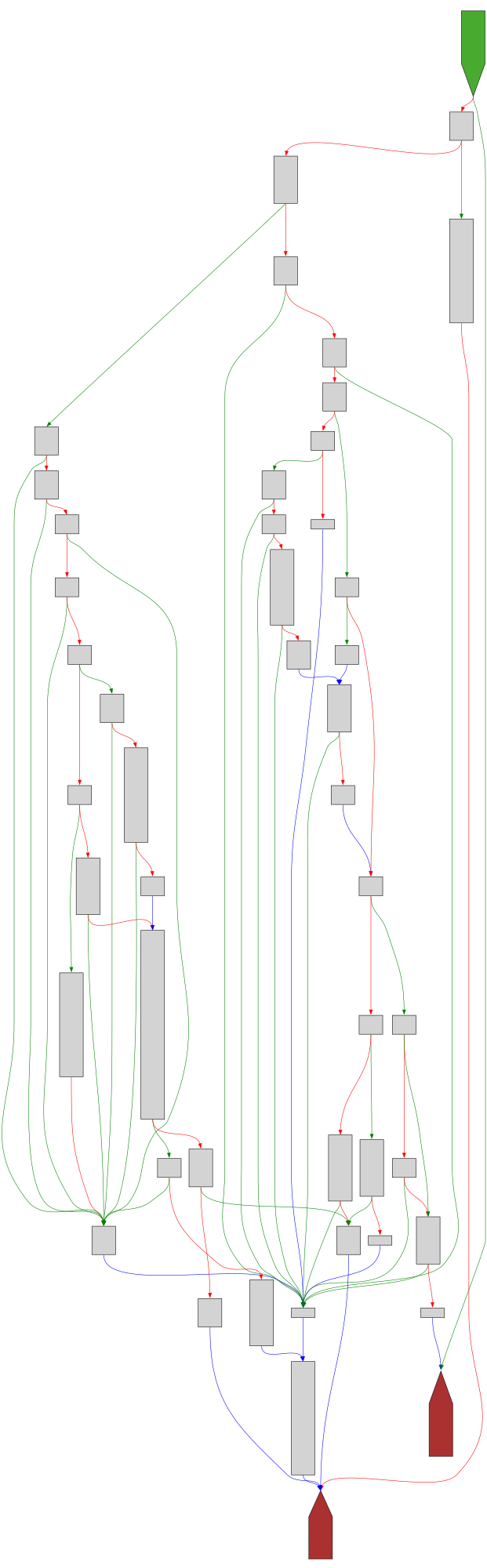
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 007060c0
ossl_gcm_stream_update
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F007060c0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F007060c0.json&colors=light
screaminggoat
screaminggoat@infosec.exchangeGoogle Chrome security advisory: Stable Channel Update for Desktop
New version 132.0.6834.110/111 for Windows, Mac and 132.0.6834.110 for Linux includes 3 security fixes, 2 were externally reported. CVE-2025-0611 (high severity) Object corruption in V8 and CVE-2025-0612 (high) Out of bounds memory access in V8. No mention of exploitation.
#google #chrome #chromium #vulnerability #cve #infosec #cybersecurity
comex
comex@mas.to“Clang will now more aggressively use undefined behavior on pointer addition overflow for optimization purposes.” https://github.com/llvm/llvm-project/commit/c2979c58d49b
A whole lot of non-exploitable bugs may become exploitable pretty soon.
Bob Young
fifonetworks@infosec.exchangeMicrosoft is getting ready to do away with MFA for its web-based products. No, this is not clickbait.
Beginning in February, if you log in to a web-based service, Microsoft will keep you logged in by default. Go ahead and close the browser window, it doesn’t matter. You’re still logged in, unless you deliberately log out. Think about hotel computers, library computers. Think about women in an abusive relationship.
It’s no longer MFA if Microsoft reduces authentication to device authentication. They won’t be requiring proof of identity of the person in front of the screen.
If you sign in to a Microsoft web-based app on a computer that is ACCESSED BY OTHER PEOPLE, you are at risk.
ACTION STEP
Even though Microsoft is placing the notification at the top of the screen right now, there are people you know who won’t understand what it means. There are people who won’t even notice the message. Make sure your friends and family know how to explicitly sign out after every session on a shared computer.
One last note: Microsoft says that instead of logging out you can use private browsing (for example, Google’s incognito mode). I don’t recommend this option, because sometimes software doesn’t behave quite like the coder thinks it will. For the most reliable security, log out.
Taggart
mttaggart@infosec.exchangeHere's a video overview of Venture, the cross-platform Windows Event Viewer. Version 0.2.0 now has the ability to join multiple .evtx files into a single view!
https://www.youtube.com/watch?v=LSobpAWwNV8
Grab Venture here: https://github.com/mttaggart/venture/releases/
"CrowdStrike, Fortinet Get Price Target Hikes Amid Booming Cybersecurity Market"
Clearly the Clownstrike "incident" doom is already behind, and Fortinet product security is irrelevant to stock price :X