Posts
3119Following
708Followers
1551BleepingComputer
BleepingComputer@infosec.exchangeSouth Korean VPN provider IPany was breached in a supply chain attack by the "PlushDaemon" China-aligned hacking group, who compromised the company's VPN installer to deploy the custom 'SlowStepper' malware.
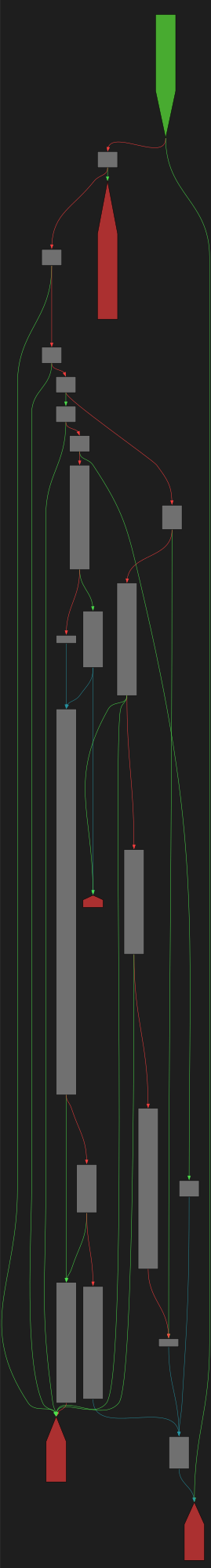
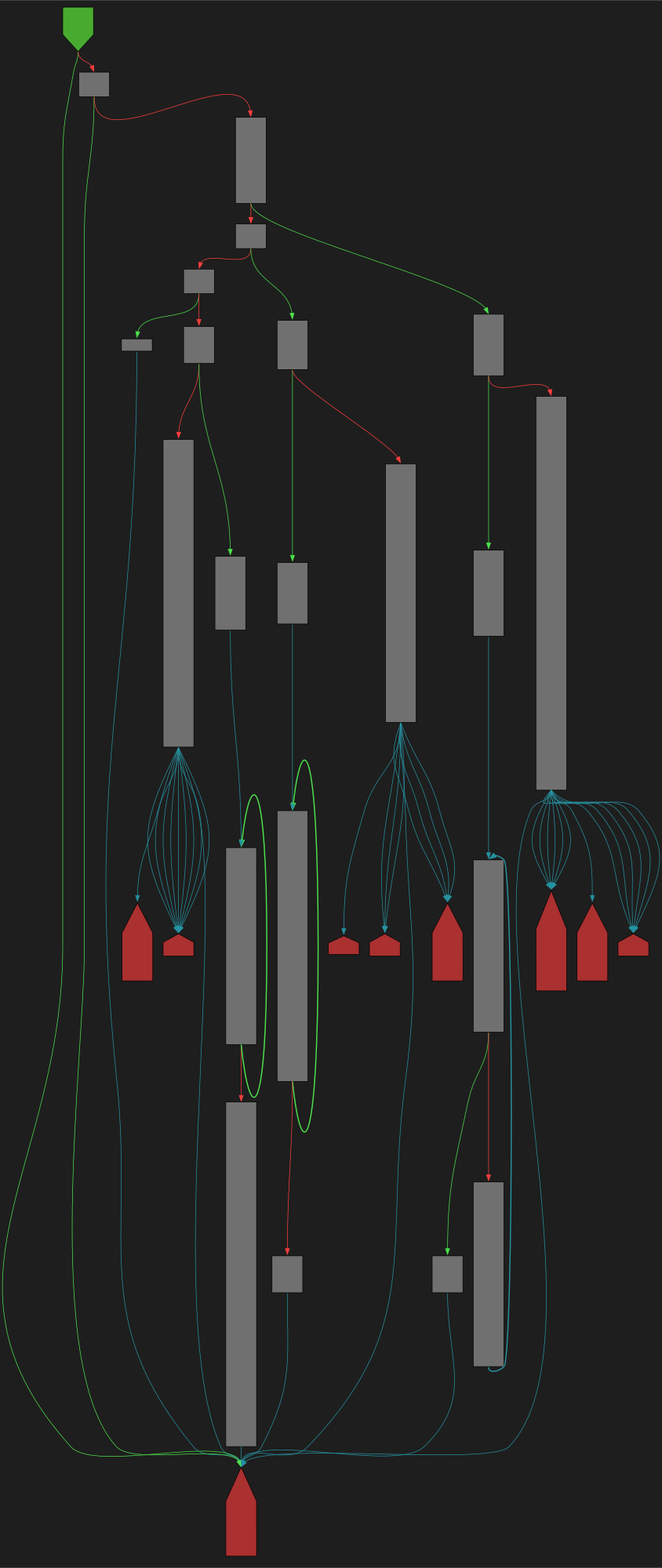
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 006a55e0
tdes_wrap_cipher
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F006a55e0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F006a55e0.json&colors=light
buherator
buheratorhttps://www.drawio.com/about
These people are pretty cool!
buherator
buheratorI'll reshare the original instead: https://blog.silentsignal.eu/2025/01/21/ibm-acs-password-dump/
(If you want to pull your hair out: https://cybersecuritynews[.]com/ibm-i-access-client-vulnerability-exposed/)
Anderson Nascimento
andersonc0d3@infosec.exchangeCVE-2025-0395: Buffer overflow in the GNU C Library's assert()
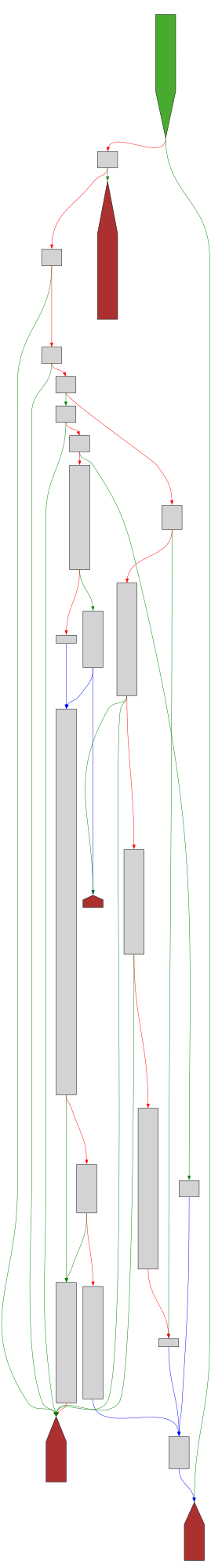
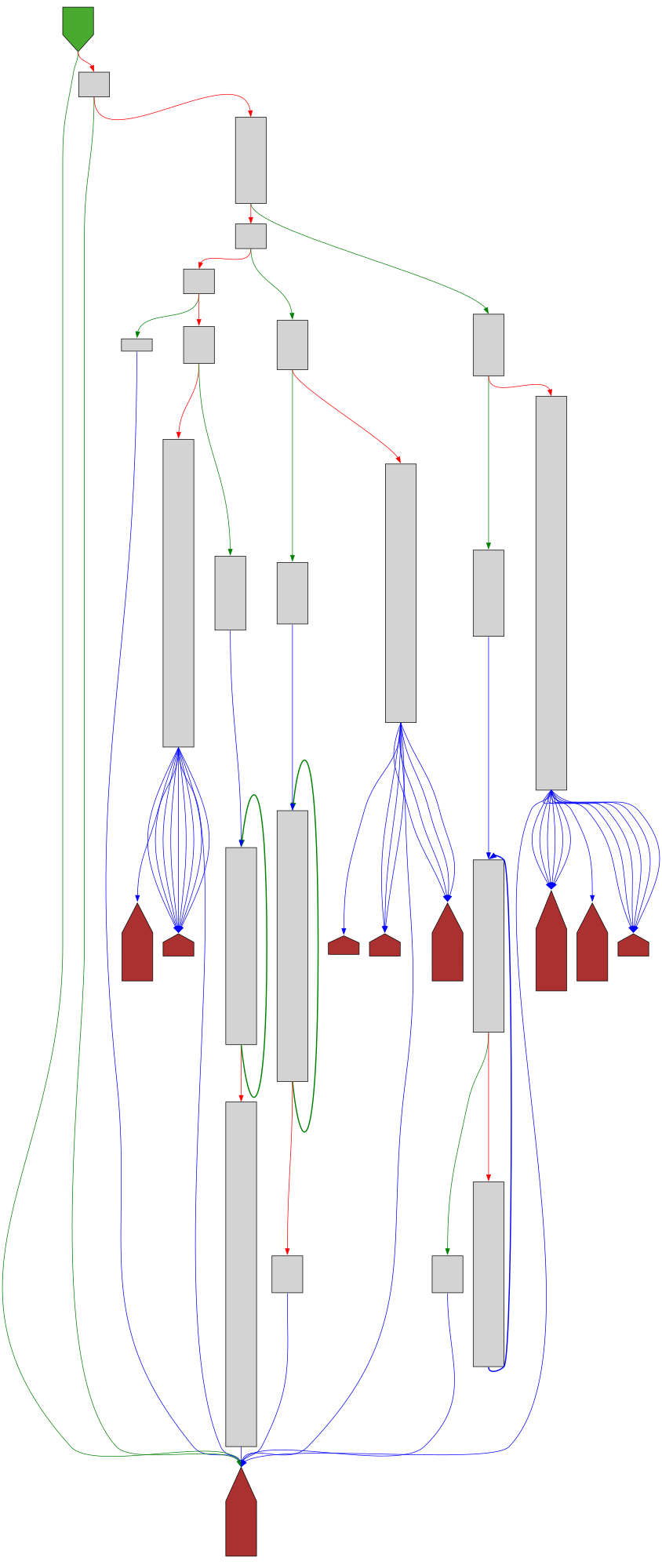
CFG Bot 🤖
cfgbot@mastodon.socialProject: mpengine-x64-pdb 1.1.24090.11
File: mpengine.dll
Address: 75a1ff7cc
GetTrackingContextFromBase64String
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1ff7cc.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fmpengine-x64-pdb%2F75a1ff7cc.json&colors=light
screaminggoat
screaminggoat@infosec.exchangeOracle: Oracle Critical Patch Update Advisory - January 2025
It's a pain in the butt to read, but there's 300+ vulnerabilities and coupled with the Oracle VP of Security Assurance's blog post January 2025 Critical Patch Update Released, there's likely no mention of exploitation.
See related The Hacker News reporting: Oracle Releases January 2025 Patch to Address 318 Flaws Across Major Products
#oracle #vulnerability #PatchTuesday #cve #infosec #cybersecurity
Ange
Ange@mastodon.socialWhat I call file format hexploring:
Read the specs, read parsers, craft pocs by hand if possible, explore the history and the features timeline, understand abuses, analyse at a low level…
Techmeme
Techmeme@techhub.socialThe Trump administration removed all advisory committee members within the DHS, including those in CISA and CSRB, which was investigating Salt Typhoon (Becky Bracken/Dark Reading)
https://www.darkreading.com/threat-intelligence/trump-fires-cyber-safety-board-salt-typhoon-hackers
http://www.techmeme.com/250122/p3#a250122p3
Trend Zero Day Initiative
thezdi@infosec.exchangeWell that's awkward. @EQSTLab used a OS command injection bug, but it was one used last year. Alpine chose not to patch it since "in accordance with ISO21434...the vulnerability is classified as 'Sharing the Risk'." Yikes. The @EQSTLab team earns $5,000 and 1 Master of Pwn point.
hackaday
hackaday@hackaday.socialGoing Minimal: 64×4, The Fun in Functional Computing
https://hackaday.com/2025/01/22/going-minimal-64x4-the-fun-in-functional-computing/
Andy Greenberg
agreenberg@infosec.exchangeTrump pardons Ross Ulbricht after eleven years in prison. An incredible twist in the never-ending Silk Road saga.
https://www.wired.com/story/trump-frees-silk-road-creator-ross-ulbricht-after-11-years-in-prison/
Michał "rysiek" Woźniak · 🇺🇦
rysiek@mstdn.socialThere's a "Signal deanonymized" thing going around:
https://gist.github.com/hackermondev/45a3cdfa52246f1d1201c1e8cdef6117
Stay calm. Deep breaths.
👉 while this is a real consideration, the only thing the attacker gets from this is a very rough (kilometers or tens of kilometers radius) location
👉 other communication platforms that use any kind of caching CDN to deliver attachments are just as vulnerable
👉 you almost certainly should continue to use Signal, unless you specifically know that this is a big problem for you.
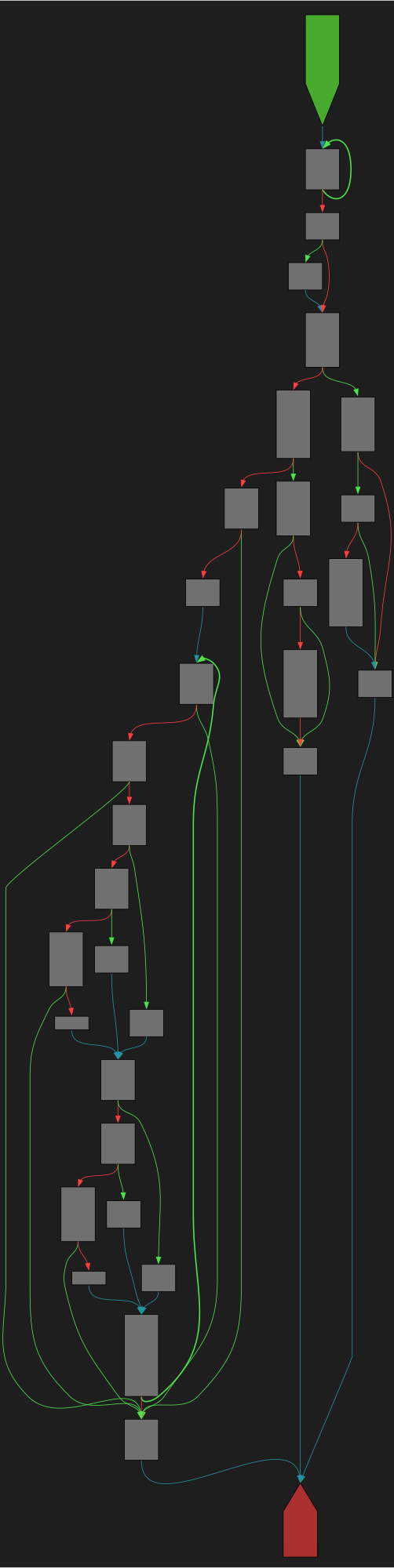
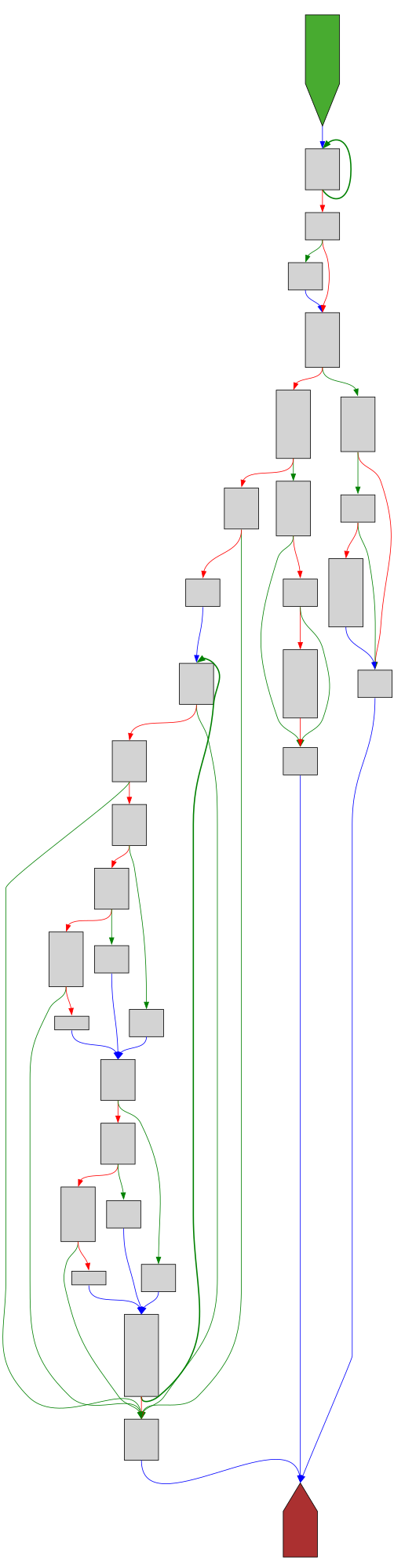
CFG Bot 🤖
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00714db0
aesni_set_encrypt_key
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00714db0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00714db0.json&colors=light
buherator
buheratorhttps://seclists.org/oss-sec/2025/q1/45
"It looks like an OEM leaked the patch for a major upcoming CPU vulnerability"
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250121-00/?p=110788
Trend Zero Day Initiative
thezdi@infosec.exchangeWell that's a first. @ScepticCtf, @diff_fusion), & @SeTcbPrivilege of fuzzware.io used a power drill to gain access to a port and exploit the Autel MaxiCharger. They head off to explain their work - except for the drill - we understand that part. #P2OAuto