Posts
3202Following
706Followers
1563TrendAI Zero Day Initiative
thezdi@infosec.exchangeWell that's awkward. @EQSTLab used a OS command injection bug, but it was one used last year. Alpine chose not to patch it since "in accordance with ISO21434...the vulnerability is classified as 'Sharing the Risk'." Yikes. The @EQSTLab team earns $5,000 and 1 Master of Pwn point.
hackaday
hackaday@hackaday.socialGoing Minimal: 64×4, The Fun in Functional Computing
https://hackaday.com/2025/01/22/going-minimal-64x4-the-fun-in-functional-computing/
Andy Greenberg
agreenberg@infosec.exchangeTrump pardons Ross Ulbricht after eleven years in prison. An incredible twist in the never-ending Silk Road saga.
https://www.wired.com/story/trump-frees-silk-road-creator-ross-ulbricht-after-11-years-in-prison/
Michał "rysiek" Woźniak · 🇺🇦
rysiek@mstdn.socialThere's a "Signal deanonymized" thing going around:
https://gist.github.com/hackermondev/45a3cdfa52246f1d1201c1e8cdef6117
Stay calm. Deep breaths.
👉 while this is a real consideration, the only thing the attacker gets from this is a very rough (kilometers or tens of kilometers radius) location
👉 other communication platforms that use any kind of caching CDN to deliver attachments are just as vulnerable
👉 you almost certainly should continue to use Signal, unless you specifically know that this is a big problem for you.
CFG Bot 🤖
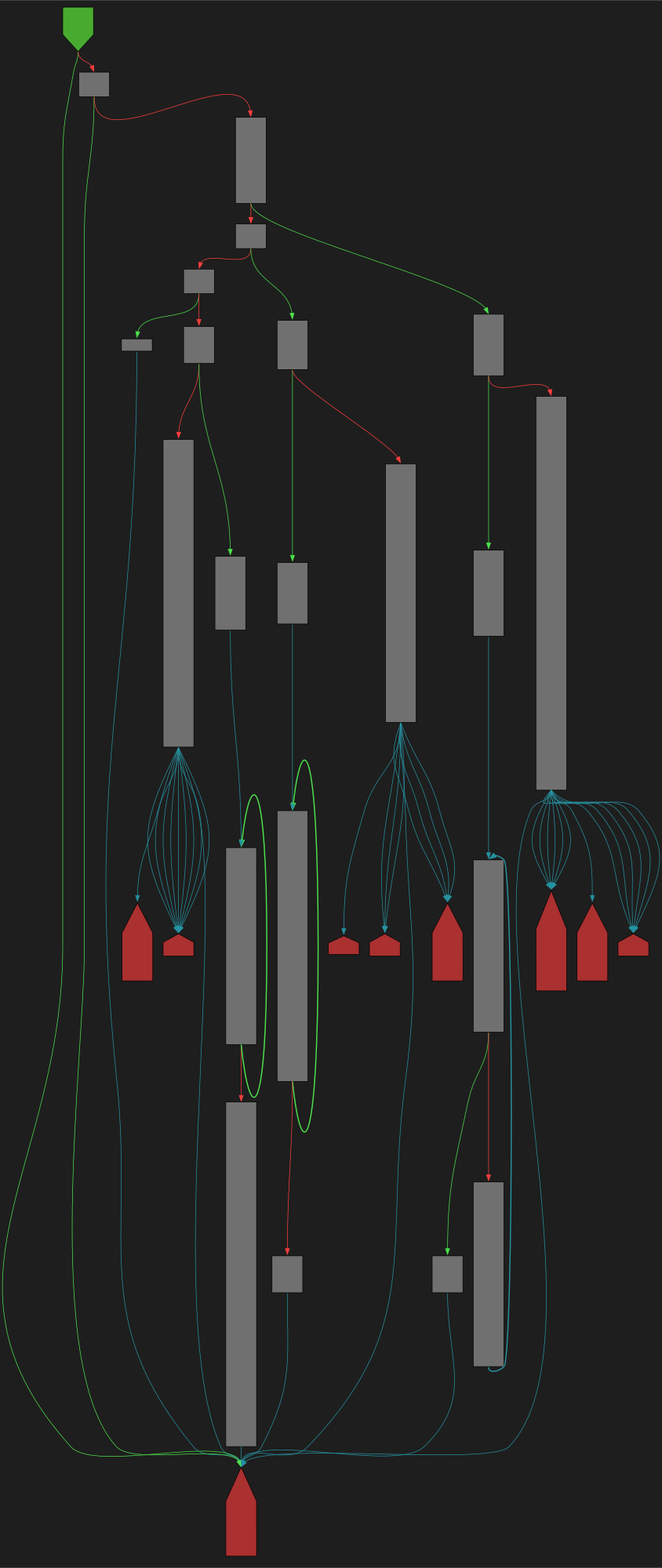
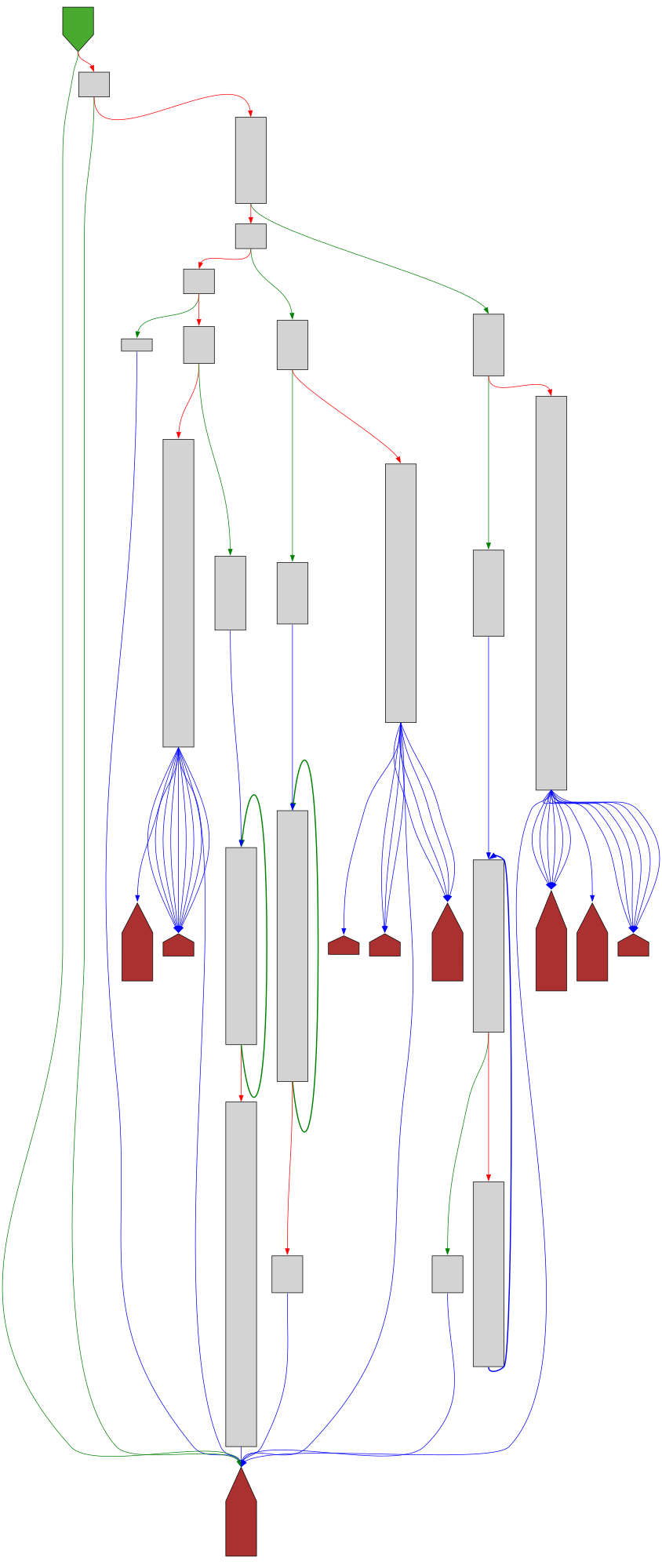
cfgbot@mastodon.socialProject: openssl-static-gcc-dwarf 3.4.0
File: openssl
Address: 00714db0
aesni_set_encrypt_key
SVG:
dark https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00714db0.json&colors=dark
light https://tmr232.github.io/function-graph-overview/render/?graph=https%3A%2F%2Fraw.githubusercontent.com%2Fv-p-b%2Fghidra-function-graph-datasets%2Frefs%2Fheads%2Fmain%2F%2Fopenssl-static-gcc-dwarf%2F00714db0.json&colors=light
buherator
buheratorhttps://seclists.org/oss-sec/2025/q1/45
"It looks like an OEM leaked the patch for a major upcoming CPU vulnerability"
buherator
buheratorhttps://devblogs.microsoft.com/oldnewthing/20250121-00/?p=110788
TrendAI Zero Day Initiative
thezdi@infosec.exchangeWell that's a first. @ScepticCtf, @diff_fusion), & @SeTcbPrivilege of fuzzware.io used a power drill to gain access to a port and exploit the Autel MaxiCharger. They head off to explain their work - except for the drill - we understand that part. #P2OAuto
K. Reid Wightman  🌻
🌻 

reverseics@infosec.exchange
Just upped my donation to my server (if you're on infosec.exchange, here's where to donate, straight from the llama's mouth: https://infosec.exchange/@jerry/109581969726975197 ).
If you're on some other server, find out who runs it, find out if they need financial support to help run it, and donate some money if you can. Servers don't grow on trees. Etc.
blacktop
blacktop@mastodon.socialHigh level diff of iOS 18.3 beta 3 vs. iOS 18.3 RC 🎉
https://github.com/blacktop/ipsw-diffs/blob/main/18_3_22D5055b__vs_18_3_22D60/README.md
RE//verse Conference
REverseConf@infosec.exchangeStruggling to reverse Rust binaries? Cindy Xiao @cdxiao breaks down the Rust type system and shares practical techniques to reconstruct Rust structures. Learn how to tackle Rust malware & analyze binaries like a pro. #REverse2025 #ReverseEngineering #Rust #Malware
Charlie Stross
cstross@wandering.shopPSA FOR AUTHORS: some dipshit put a pirate edition of my latest book on Apple Books with a "50% OFF" medallion on the cover illo. They used an obscure unicode glyph in the author name so that searches for "Charles Stross" find it but the bookstore won't merge it.
Where there's one there'll be others!
My publisher's piracy team is handling it.
If you have a book that came out this year, beware! It's a relative of the IDN homograph attack only targeting ebook stores:
The Meteoriks
meteoriks@icosahedron.websiteCALLING ALL #demoscene MUSICIANS!
Our jury for Best Soundtrack could urgently use one or two more jurors - are you able to help out?
We reactivated our application form just for you! Thank you humbly, everyone!
Trammell Hudson
th@v.stIt looks like oil paintings on wikipedia are being infected by phone camera software that automatically "fixes" skin textures.
Carly Page
carlypage@mastodon.socialHPE has confirmed it's investigating a data breach after a well-known hacker claimed to have stolen sensitive information from the company https://techcrunch.com/2025/01/21/hpe-investigating-security-breach-after-hacker-claims-theft-of-sensitive-data/
buherator
buheratorscreaminggoat
screaminggoat@infosec.exchangeJetBrains security advisory: TeamCity 2024.12.1 Bug Fix Is Now Available
It's time for security theater as JetBrains announces a TeamCity update but refuses to tell us what vulnerabilities actually got fixed. 🤡 There are no release notes for 2024.12.1 at the time of this toot.
There is no dropdown option for TeamCity 2024.12.1 in Fixed security issues page. A CVE of "TeamCity" doesn't show any new CVEs since December 2024. On average, they update their security bulletin with CVEs 4-30 days after announcing security updates.
#jetbrains #teamcity #cve #vulnerability #infosec #cybersecurity
David Chisnall (*Now with 50% more sarcasm!*)
david_chisnall@infosec.exchangeAny #Wikipedia editors around who can help? We are trying to get the article on #CHERI added. It's so far been rejected three times:
First, it did not have enough independent citations. We added a lot to news articles about CHERI.
Second, it was insufficiently detailed and lacking context. We added a timeline of development, a load of cross references, and a simple introduction.
It was then rejected again because it lacks an explanation that a 15-year-old could understand. This is true of 90% of science-related articles on Wikipedia, so I'm not sure how we fix it. An explanation at that level is something I can write (I have done for the #CHERIoT book!) but it would then make the page 3-4 times as long and not suitable for an encyclopaedia (I've previously seen pages rejected because Wikipedia is not the right place for tutorials).
I don't understand the standards for Wikipedia and I really need some guidance for how to resolve and progress this.